Documenting all the places
personal data goes.
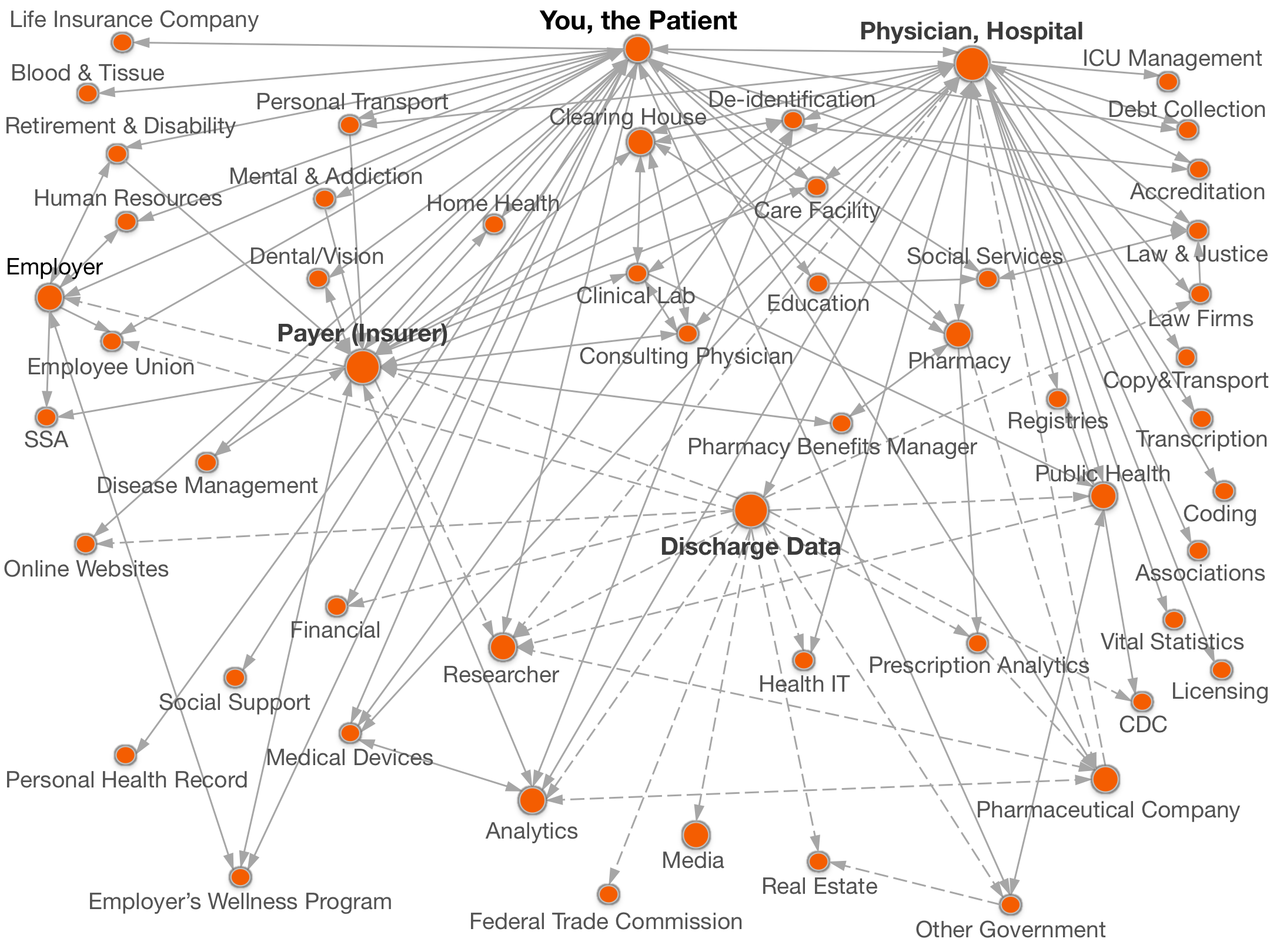
Legend:  with your name,
with your name, without your name.
without your name.
Click on a circle above for names of organizations and details of data shared.
Health payers receive information from you, the patient, statewide discharge data holders, pharmacy benefits managers, employer wellness programs, disease management organizations, de-identification companies and analytics firms and exchange information with researchers.
In general, Health Payers receive detailed medical bills from physicians, hospitals, and clinical laboratories. Bills typically include your name, address, policy number, date of birth, diagnoses, and procedures. Often providers submit bills to insurance companies through clearing houses.
Additionally, a Benefits Manager may play the role of a payer for self-insured employers.
There are many types of insurers:
A common payer is a health insurance company offers insurance against the risk of your personally incurring major medical expenses. By estimating the overall risk of health expenses among a targeted group, the insurance company pays your medical bills and you pay monthly premiums. Often your employer contributes significantly to your monthly premiums and feedback to the employer from the insurance company should be aggregate information that does not include your name. When your employer and your health payer are the same, they are called a Self-Insured Employer.
In comparison, a managed care organization aims to lower healthcare costs by re-organizing and negotiating arrangements directly with physicians. A common variation is Health Maintenance Organizations, which require members to select a primary physician as a doctor who acts as a gate keeper to recommend and approve medical services. Another variation is a Preferred Provider Organization is an organization of physicians, hospitals, and other health care providers who work with an insurer to provide health care at reduced rates.
The largest payer is Medicare, which is a federal program for senior citizens. Medicaid assists at the state level.
Examples
OptumInsight (Ingenix), a division of Minnetonka, Minn.-based UnitedHealth Group Inc., the biggest private U.S. health insurer, owns one of the deepest pools of health data on the planet. Its patient profiles link records from health plans, lab tests, hospital claims, pharmacies and physicians, even demographic information on patients' race, income and net worth. Sales were $2.88 billion last year. OptumInsight purchases statewide personal hospital discharge data from at least 10 states: CA, FL, IL, MD, MA, NJ, NY, PA, TX, WA [source]. The purchased data does not contain the person's name, but it is possible to match some people by name [source]. | Aetna of Connecticut had a data breach in 2010, in Connecticut. A number of insured customers were affected by an unauthorized access or accidental disclosure of personal information in September. [source]. | |
Ingenix (OptumInsight), a division of Minnetonka, Minn.-based UnitedHealth Group Inc., the biggest private U.S. health insurer, owns one of the deepest pools of health data on the planet. Its patient profiles link records from health plans, lab tests, hospital claims, pharmacies and physicians, even demographic information on patients' race, income and net worth. Sales were $2.88 billion last year. They purchase statewide personal hospital discharge data from at least 10 states: CA, FL, IL, MD, MA, NJ, NY, PA, TX, WA [source]. The purchased data does not contain the person's name, but it is possible to match some people by name [source]. | Aetna, Nationwide, WellPoint Group Health Plans, Humana Medicare, Mutual of Omaha Insurance Company, Anthem Blue Cross Blue Shield via Concentra Preferred Systems had a data breach in 2006, in Ohio. A lockbox holding personal information of health insurance customers was stolen Oct. 26. Thieves broke into an office building occupied by insurance company vendor, concentra Preferred Systems. The lockbox contained computer backup tapes of medical claim data for Aetna and other Concentra health plan clients. Exposed data includes member names, hospital codes, and either sSNs or Aetna member ID numbers. SSNs of 750 medical professionals were also exposed. Officials downplay the risk by stating that the tapes cannot be used on a standard PC. UPDATE (12/23/06): The lockbox also contained tapes with personal information of 42,000 NY employees insured by Group Health Insurance Inc.) uPDATE(1/24/07): Personal data of 28,279 Nationwides Ohio customers were also compromised. 2/11/10 Total changes to 396,279 to reflect final total of records breached in all of the affected companies. (396279 records involved) [source]. | |
Acs Government Healthcare purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Affinity Health Plan had a data breach in 2010, in New York. Affinity Health Plan, a New York managed care service, is notifying more than 400,000 current and former customers employees that their personal data might have been leaked through the loss of an unerased digital copier hard drive. Some personal records were found on the hard drive of a copier found in a New Jersey warehouse. The copier had previously been leased by Affinity and was then returned to the leasing company. Affinity Health Plan says it has not had a chance to review the data found on the copier. The figure of 409,262 notifications includes former and current employees, providers, applicants for jobs, members, and applicants for coverage. (409,262 records involved) [source]. | |
Aetna purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | American Association of Retired Persons, AARP Insurance had a data breach in 2010, in District Of Columbia. A client received another clients information in an insurance policy letter. He attempted to trace the mistake and notified the organization that underwrites AARPs life insurance program, New York Life Insurance. It is unknown how this error occurred and client names, phone numbers, policy numbers, check account information and dates of birth could have been exposed. [source]. | |
AHCA purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | American Fidelity Assurance Company had a data breach in 2010, in Oklahoma. Storage containers with Social Security numbers, names, dates of birth and other information were left on a curb in Edmond, Oklahoma. A couple went to the local news after having stored the hundreds of documents for a few years. The insurance papers are from 2003 and 2004 and have information on employees of multiple companies. [source]. | |
America Health Insurance Plans Center For Policy And Research purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | American International Group (AIG), Indiana Office of Medical Excess, LLC had a data breach in 2006, in New York. The computer server was stolen on March 31 containing personal information including names, social Security numbers, birth dates, and some medical and disability information. UPDATE(1/12/2010) A 28-year-old Indianapolis man was sentenced today to two years in state prison for trying to extort $208,00 from an insurance company after stealing a computer server. In March 2006, the man burglarized the indianapolis office of AIG Medical Excess, threatening to release clients personal data on the Internet. The server contained the names of more than 900,000 insured persons, as well as their personal identifying information, and confidential medical information and e-mail communications. At the time of the burglary, the man was an employee of a private security firm that provided security services to the insurance company. On July 23, 2008, Stewart delivered a package to the insurance company. The package included a letter stating that he possessed the stolen server and its confidential data. He asked for $1,000 a week for four years, but the FBI and others intervened. The indiana State Police, the Indiana Department of Natural Resources, indianapolis Metropolitan Police Department, and Attorney General also were part of the investigation. (930,000 records involved) [source]. | |
Anthem BC/BS of Maine purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Ameritas Life Insurance Corp. had a data breach in 2012, in Nebraska. A laptop was stolen or discovered stolen sometime around March 21, 2012. It contained the sensitive health information of 3,000 people. The incident was posted on the HHS website on June 8.UPDATE(08/03/2012): An official notice states that an employee notified Ameritas that their laptop and other items were stolen from their car on March 21. The laptop contained information used to provide group dental and vision quotes, as well as individual member enrollment information for employer-sponsored group health plans. The laptop was password protected but not encrypted. Names, Social Security numbers, addresses, dates of birth, and places of employment may have been exposed. (3,000 records involved) [source]. | |
Anthem Blue Cross/ Wellpoint Inc purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Anthem Blue Cross had a data breach in 2011, in California. Letters soliciting dental and vision coverage were mailed to current Anthem customers. A priority code composed of the customers Social Security number and two extra digits was printed on the outside of each envelope. One customer noticed the error and contacted the media. Anthem admits that an error occurred, but did not reveal the cause. Anthem is working to prevent this type of breach from happening again and was in the process of notifying customers of the error as of May 12.UPDATE(10/01/2012): Anthem experienced the marketing mailer error on April 27, 2011. The State of California settled with Anthem in September of 2012. Anthem agreed to pay $150,000 and to make significant improvements to its data security procedures to prevent future errors of a similar type.. (31,125 records involved) [source]. | |
Av Med Health Plans purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Anthem Blue Cross, WellPoint had a data breach in 2010, in California. More than 200,000 Anthem Blue Cross customers this week received letters informing them that their personal information might have been accessed during a security breach of the companys website. Only customers who had pending insurance applications in the system are being contacted because information was viewed through an on-line tool that allows users to track the status of their application. Social Security and credit card numbers were potentially viewed. Anthem Blue Cross merged with WellPoint in 2004.UPDATE (6/29/2010): Around 470,000 customers in 10 states were notified of the breach. The original story states that only applicants were affected, but existing customers also received notification of a possible breach of their information.UPDATE (7/12/2010): 20,000 Louisville, Kentucky residents received notification that a security mistake online resulted in the exposure of their Social Security numbers and financial information. It is unclear whether these residents are included in the original 470,000 customers. Only customers who were self insured were affected. WellPoint is claiming that this and other recent breaches were committed by an attorney or attorneys attempting to gain information for a lawsuit against WellPoint.UPDATE (9/17/2010): An Anthem applicant whose information was exposed by the breach filed a lawsuit against Anthem at the Los Angeles County Superior Court. The lawsuit claims that the breach exposed applicants and clients to identity theft. An applicant behind the lawsuit is seeking class action status.UPDATE (10/29/2010): The office of the Attorney General of Indiana is suing WellPoint Inc. because of the companys delay in notifying customers of the breach. WellPoint is accused of violating an Indiana law that requires businesses to provide notification of breaches in a timely manner and faces $300,000 in fines. State officials believe WellPoint was aware of the exposure in late February, but waited until June to notify customers.UPDATE(7/5/2011): WellPoint Inc. will pay Indiana a $100,000 settlement for violating a 2009 data breach notification law. Customer data was accessible between October 23, 2009 and March 8, 2010. One or more consumers informed WellPoint of the problem on February 22, 2010 and again on March 8, 2010. WellPoint began notifying consumers on June 18, 2010. (470,000 records involved) [source]. | |
Blue Cross & Blue Shield Of Florida purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | AvMed Health Plans had a data breach in 2010, in Florida. AvMed Health Plans announced that personal information of some current and former subscribers may have been compromised by the theft of two company laptops from its corporate offices in Gainesville. The information included names, addresses, phone numbers, Social Security numbers and protected health information. The theft was immediately reported to local authorities but attempts to locate the laptops have been unsuccessful. AvMed determined that the data on one of the laptops may not have been protected properly, and approximately 80,000 of AvMeds current subscribers and their dependents may be affected. An additional approximate 128,000 former subscribers and their dependents, dating back to April 2003, may also have been affected.UPDATE (06/03/2010): The theft of the laptops compromised the identity data of 860,000 more Avmed members than originally thought. The total now nears 1.1 million.UPDATE (11/17/2010): Five AvMed Health Plans customers filed a class-action lawsuit against the health insurer on behalf of the 1.2 million people who were affected by the breach. At least two of them believe that their personal information was misused as a result of this particular breach.UPDATE (09/24/2012): An appeals court ruled that the plaintiffs were explicitly able to prove a link between the breach and ID theft they incurred. The case had been thrown out by a lower court in August 2011, but the appeal ruling may allow victims of identity theft to make it easier to prove that the identity theft was caused by a data breach. (1,220,000 records involved) [source]. | |
California Medical Assistance Commission purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Ayuda Medical Case Management had a data breach in 2012, in Texas. Thousands of patient records were found in an unsecured trash can. They contained names, Social Security numbers, addresses, phone numbers, medical conditions, and treatment information. The boxes of medical records were traced to Ayuda, whose owner claimed to have been doing little or no business after losing a state contract in September. The boxes were auctioned off after the owner failed to pay the rental fee on a storage unit. (2000 records involved) [source]. | |
Capital District Physicians Health Plan purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | BB&T Insurance had a data breach in 2008, in Virginia. A BB&T Insurance laptop containing the personnel information of some Harrisonburg City Schools employees was stolen. The laptop, used by an outside sales representative to develop an insurance proposal for the school system, was stolen from a car. The information contained names, dates of birth, Social Security numbers, and, in some cases, medical history. [source]. | |
Capital Health Plan purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Benefits Resources, Inc. had a data breach in 2011, in Ohio. A portable electronic device was lost or stolen on or around November 22, 2010. It contained the PHI of patients. [source]. | |
Centene Corporation purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Blue Cross and Blue Shield of Florida (BCBSF) had a data breach in 2011, in Florida. An April 2011 mailing error caused 3,500 member healthcare statements to be mailed to incorrect addresses. The statements were mailed to the former addresses of members and contained names, insurance numbers, diagnoses codes and descriptions, procedure codes and descriptions, prescription names and provider names. [source]. | |
Childrens Healthcare Of Atlanta purchases statewide personal hospital discharge data from at least FL WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Blue Cross and Blue Shield of Georgia had a data breach in 2008, in Georgia. Benefit letters containing personal and health information were sent to the wrong addresses last week. the letters included the patients name and ID number, the name of the medical provider delivering the service, and the amounts charged and owed. A small percentage of letters also contained the patients social Security numbers. (202000 records involved) [source]. | |
Coventry Health Care purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Blue Cross and Blue Shield of North Carolina had a data breach in 2006, in North Carolina. Social Security numbers of members were printed on the mailing labels of envelopes with information about a new insurance plan. Those who were affected were contacted immediately. (629 records involved) [source]. | |
Dirigo Health Agency purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Blue Cross and Blue Shield of Rhode Island (BCBSRI) had a data breach in 2010, in Rhode Island. A filing cabinet containing survey information from approximately 12,000 BlueCHIP for Medicare members was donated to a local nonprofit organization. The surveys were from 2001 to early 2004 and contained information such as names, Social Security numbers, telephone numbers, addresses and Medicare Identification numbers. (12,000 records involved) [source]. | |
DMHC purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Blue Cross Blue Shield Association had a data breach in 2010, in Illinois. An error in the quarterly address update process resulted in the mailing of approximately 15,000 individuals protected health information to incorrect addresses. The information in the letters included demographic information, explanation of benefits, clinical information, and diagnoses. The returned mail was collected and the organization verified whether or not it had been delivered. [source]. | |
Empire Health purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Blue Cross Blue Shield Florida had a data breach in 2011, in Florida. A system error caused mail to be sent to the wrong addresses. Current and former addresses were mixed up and mail containing an explanation of benefits was sent to incorrect (former) addresses.UPDATE(4/15/2011): The mailing error occurred on October 16, 2010 and was discovered in late January of 2011. [source]. | |
Harris County Healthcare Alliance purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Blue Cross Blue Shield of Alabama had a data breach in 2010, in Alabama. A dishonest employee was charged with identity theft. The employee fraudulently obtained credit by using the health insurance information of at least 15 clients. (15 records involved) [source]. | |
Harvard Pilgrim Health Care purchases statewide personal hospital discharge data from at least NY ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Blue Cross Blue Shield of Massachusetts (BCBS) had a data breach in 2012, in Massachusetts. A BCBS vendor misused BCBS employee information. The misuse appears to have been limited to one instance. Names, Social Security numbers, dates of birth, compensation information, and bank account information may have been exposed. (15000 records involved) [source]. | |
Health First, Inc. purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Blue Cross Blue Shield of Michigan (BCBSM), Tstream Software had a data breach in 2011, in Michigan. A BCBSM website created by Tstream was the source of a breach. A BCBSM found her personal information online when searching her name. People applying for individual health insurance between 2006 and an unclear date had their names, Social Security numbers, addresses and dates of birth exposed. BCBSM was notified of the error on November 17, 2010. The information was accessible for an unspecified amount of time. Though 6,500 BCBSM members were notified, only 2,979 were affected. (2979 records involved) [source]. | |
Health Scope Inc purchases statewide personal hospital discharge data from at least CA NJ FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Blue-Cross Blue-Shield of Western New York had a data breach in 2008, in New York. A laptop hard-drive containing vital information about members has gone missing. Blue-Cross Blue-Shield of Western New York says it is notifying its members about identity theft concerns after one of its company laptops went missing. (40,000 records involved) [source]. | |
HFN, Inc. purchases statewide personal hospital discharge data from at least IL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | BlueCross Blue Shield of North Carolina had a data breach in 2012, in North Carolina. A mailing software error caused the private information of current and former Blue Cross Blue Shield members to be mailed to other members. The error was discovered on April 12. The records were more than 10 years old and included patient names, Social Security numbers, type of medical care received, and other protected health information. (100 records involved) [source]. | |
Horizon Healthcare Innovations purchases statewide personal hospital discharge data from at least NJ [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | BlueCross BlueShield (BCBST) had a data breach in 2010, in Tennessee. The theft of 57 hard drives from a BlueCross BlueShield of Tennessee training facility last October has put at risk the private information of approximately 500,000 customers in at least 32 states. The hard drives contained 1.3 million audio files and 300,000 video files. The files contained customers personal data and protected health information that was encoded but not encrypted, including: names and BlueCross ID numbers. In some recordings-but not all-diagnostic information, date of birth, and/or a Social Security number were exposed. BCBS of TN estimates that the Social Security numbers of approximately 220,000 customers may be at risk. UPDATE (4/29/10): The number of plan members whose data were exposed has grown from 521,761, an estimate made in March, to nearly one million, as of April 2, according to a report issued by Mary Thompson, spokeswoman for the Tennessee Blues.UPDATE (11/3/10): According to a letter sent to the New Hampshire Attorney Generals Office, the total number of individuals affected was 1,023,209. BCBS used a three-tier system to categorize individuals affected by the breach. The total includes 451,274 clients whose Social Security numbers were involved, 319,325 clients whose personal and diagnostic health information was involved and 239,730 clients who had personally identifiable information that was neither medical nor their Social Security number. BlueCross Blue Shield also reported receiving fewer than 10 requests for credit restoration services from those who had their Social Security numbers exposed.UPDATE(3/14/2012): Blue Cross Blue Shield of Tennessee (BCBST) reached a $1.5 million resolution agreement with the U.S. Department of Health and Human Services. BCBS of Tennessee kept the drives and network data closet in a facility that was secured by a property management company. The closet was secured by biometric and keycard scan security with a magnetic look and an additional door with a keyed lock. BCBST eventually vacated most of the leased office space. Thieves may have taken the opportunity to steal the 57 unencrypted hard drives from the closet while the space was not fully occupied. (451,274 records involved) [source]. | |
Jefferson Healthcare purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | BlueCross BlueShield of Western New York, HealthNow New York Inc., Administrative Services of Kansas had a data breach in 2006, in New York. The laptop of an employee of HealthNows outside claims vendor Administrative Services of Kansas was stolen during the lunch break of a presentation. The laptop had potential member names and Social Security numbers. The theft occurred sometime around June 19 and notification letters were sent on October 16. (96 records involved) [source]. | |
Kaiser Foundation Health Plan purchases statewide personal hospital discharge data from at least CA WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Buckeye Community Health Plan had a data breach in 2006, in Ohio. Four laptop computers containing customer names, Social Security numbers, and addresses were stolen from the Medicaid insurance provider. (72,000 records involved) [source]. | |
Maine Community Health Options purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Cahaba Government Benefit Administrators LLC had a data breach in 2011, in Alabama. On April 11, 2011, someone discovered that sensitive paper records had been disclosed to outside parties or accessed without authorization. Centers for Medicare and Medicaid Services (CMS) uses Cahaba for administration of Medicare fee-for-service programs. [source]. | |
Maine Health purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | CalOptima had a data breach in 2009, in California. Personally identifiable information on members of CalOptima, a Medicaid managed care plan, may have been compromised after several CDs containing the information went missing. the unencrypted data on the CDs includes member names, home addresses, dates of birth, medical procedure codes, diagnosis codes and member iD numbers, and an unspecified number of Social Security numbers. the discs had been put in a box and sent via certified mail to CalOptima by one of its claims-scanning vendors, according to a statement by the health plan. CalOptima received the external packaging material minus the box of discs. (68,000 records involved) [source]. | |
Maine Health Alliance purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Catalyst Health Solutions, Alliant Health Plans, Inc. had a data breach in 2012, in Georgia. An unauthorized disclosure resulted in the exposure of protected health information. The breach occurred on or around January 1, 2012 and was reported on April 17. This incident was reported on the HHS website. [source]. | |
Medicaid and CHIP Payment and Access Commission (MACPAC) purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Centers for Medicare & Medicaid Services (CMS) had a data breach in 2012, in Maryland. The CMS experienced 13 breaches between September 23, 2009 and December 31, 2011. The CMS failed to notify beneficiaries of seven of the breaches in a timely manner. The HHSs Office of the Inspector General (OIG) also alleges that the notifications mailed to beneficiaries did not disclose what type of information had been exposed, the date the breach occurred, or how CMS was working to prevent future breaches. [source]. | |
Northwest Washington Medical Bureau purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Centra had a data breach in 2010, in Georgia. A laptop was stolen from the trunk of an employees rental car overnight on November 11. Patient names and billing information were on the laptop. The delay in notification occurred because of the time it took to determine what information was on the stolen laptop.UPDATE (1/14/11): The total number of affected individuals was changed from 13,964 to 11,982. [source]. | |
NovaHealth purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Central States Southeast and Southwest Areas Health and Welfare Fund had a data breach in 2012, in Illinois. An incident occurred on July 31 that may have caused sensitive health information to be exposed. The information was in the form of paper records that were exposed in some undisclosed way. [source]. | |
Pacific Business Group On Health purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | City of Virginia Beach, Flexible Benefits Administrators had a data breach in 2007, in Virginia. A former employee allegedly stole Virginia Beach city and school district employees personal information and used it to commit prescription fraud. Police discovered a list of names and Social Security numbers at the employees home. (2,000 records involved) [source]. | |
Pacificare Health System purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Colorado Department of Health Care Policy and Financing had a data breach in 2010, in Colorado. A hard drive containing personal information for clients enrolled in state-provided health insurance was stolen from the Colorado Office of Information Technology. The information included names, state ID number and the name of the clients program. The Agency is certain that contact information, financial information and Social Security numbers were not involved. [source]. | |
Pacificare Of Washington purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Colorado Department of Health Care Policy and Financing (HCPF) had a data breach in 2011, in Colorado. A disk with the information of medical-aid applicants was lost on its way between HCPF and another agency. It contained applicant names, state identification numbers, and addresses. The disk was discovered missing on May 6. [source]. | |
Parkland Health & Hospital System purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Colt Express Outsourcing Services, CNET Networks had a data breach in 2008, in California. Burglars stole computer systems from the offices of the company that administers the Internet publishers benefit plans. The computers contained names, birth dates, Social Security numbers and employment information of the beneficiaries of CNETs health insurance plans. CNET was only one of several clients affected. uPDATE (8/26/08): Among the companies whose staffers have been exposed by the Colt break-in in Walnut Creek, California: Google, Bebe Stores, Alston & Bird, and the California Bankers Assn. (17241 records involved) [source]. | |
Premera Blue Cross purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Commerce Banc Insurance Services (CBIS) had a data breach in 2007, in New Jersey. A CBIS vendor had a laptop stolen. CBIS employees may have had their names, Social Security numbers, and possibly health information exposed. (12876 records involved) [source]. | |
Regence Blue Shield purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Concordia Plan Services (CPS) had a data breach in 2011, in Missouri. Microfilm that contained the plan enrollment information of benefits members was lost by a delivery service sometime between February and May of 2011. It contained names, addresses, dates of birth and in some cases Social Security numbers and limited medical information from the 1960s and 1970s. A vendor received the microfilm from CPS on February 3rd. The vendor attempted to transfer the microfilm to another company, but learned that the microfilm had been misplaced sometime prior to or during May. CPSs vendor informed them of the situation on August 23. [source]. | |
Tricare Interactive purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Connextions, Anthem Blue Cross Blue Shield of Indiana, Anthem Blue Cross Blue Shield of Ohio, Empire Blue Cross Blue Shield of Indiana had a data breach in 2013, in Florida. A Connextions employee used Social Security numbers from a number of other organizations for criminal activity. At least four members of Anthem Blue Cross and Blue Shield were affected by the criminal activity. The breach was reported on HHS as affecting 4,814 patients, but more were affected. (6,000 records involved) [source]. | |
Scott & White Health System purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Cover Tennessee had a data breach in 2007, in Tennessee. A computer error at the Cover Tennessee health insurance program caused small business owners who chose not to print out their forms from the Web site to have their personal information including Social Security numbers added to the next users printout request. (279 records involved) [source]. | |
[24]7.ai. had a data breach in 2017, in California. A payment card breach suffered by [24]7.ai. between September 26 and October 12, 2017, is impacting major firm, including Best Buy, After Delta Air Lines and Sears Holdings.The intrusion occurred between September 26 and October 12, 2017. "We understand malware present in [24]7.ai’s software between Sept. 26 and Oct. 12, 2017, made unauthorized access possible for the following fields of information when manually completing a payment card purchase on any page of the delta.com desktop platform during the same timeframe: name, address, payment card number, CVV number, and expiration date." reads the advisory published by Delta Airline."No other customer personal information, such as passport, government ID, security or SkyMiles information was impacted." [source] | 1-800-Flowers had a data breach in 2016, in New York. 1-800-Flowers customer service received reports on February 15, 2016 from customers that they couldn't complete their online orders. The company investigated and discovered from February 15th, 2016 through February 17th, 2016 orders that were placed may have been compromised customer personal information.Information compromised may have included names, addresses, email addresses, payment card numbers, expirations dates and security codes. [source] | |
A&A Ready Mixed Concrete, Inc. had a data breach in 2016, in California. [source] | Abbott Nutrition had a data breach in 2017, in Ohio. [source] | |
ABM Parking Services had a data breach in 2014, in Missouri. ABM Parking Services notified customers of a data breach when the point of sale software system implemented by Datapark USA Inc, a third party vendor for several Chicago, Illinois parking facilities was hacked. The information was compromised from October 6, 2014 through October 31, 2014. The hackers were able to compromise certain customer credit and debit card information, including payment card numbers. A toll-free information line has been made available for those affected. [source] | Accuform Signs had a data breach in 2015, in Florida. Accuform Signs notified customers of a data breach when they noticed order information from their site and possible the site of a distributor of the company, which was hacked from an outside source. The information compromised included names, addresses, emails, phone and credit card information. [source] | |
Acer Service Corporation had a data breach in 2016, in California. [source] | Acosta Sales and Marketing had a data breach in 2014, in Florida. Acosta, Inc. and its subsidiaries (Mosaic Sales Solutions US Operating Co. LLC) informed customers of a data breach when an employee of their Human Resources department had a laptop containing personal information stolen from their car on November 11, 2014 [source] | |
Adult Friend Finder (owned by Penthouse Media) had a data breach in 2015, in Florida. The adult website Adult Friend Finder was hacked and personal information posted publicly for people to see.The information included customers' email addresses, usernames, passwords, birthdays and zip codes,and sexual preferences. To date they have not yet discovered if customer credit card information was exposed. [source] | Advanced Auto Parts had a data breach in 2016, in Virginia. Advance Auto Parts notified individuals of a data breach when the company suffered a phishing attack when an unauthorized individual posed as an employee, and convinced an employee of the company to provide a file containing information about certain individuals working for the company. The information compromised included names, Social Security numbers, 2015 gross wages, and the state(s) the individual pays income taxes. [source] | |
Advanced Graphic Products, Inc. /dba/ "Advanced-Online" had a data breach in 2017, in Texas. Advanced-Online, or Advanced graphic Products, Inc., experienced a data breach exposing 22,182 records. According to the breach notification form sent to the Indiana Office of Attorney General, Advanced-Online learned on January 3, 2018 that certain personal information housed on the company's online platform may have been subject to unauthorized access. The date range for the incident appears to be April 29, 2017until January 12, 2018. [source] | Advanced International Marketing Inc. had a data breach in 2016, in Ohio. Advanced International Marketing Inc. notified customers of a data breach when an unauthorized party gained access to certain images that were uploaded to the company's website. The information compromised included names and state ID's. [source] | |
Advanced Technology International, Inc. had a data breach in 2017, in South Carolina. On January 25, 2018, ATI began the process of mailing out Form 1099s to individuals and companies for the 2017 tax year. However, during the mailing process, an error occurred whereby approximately sixty-seven (67) recipients received their Form 1099 and the Form 1099 belonging to an unrelated individual or entity. On or around January 30, 2018, ATI discovered the error. ATI immediately commenced an investigation and confirmed the incident was the result of human error. ATI took steps to address the error to reduce the likelihood of a similar incident occurring in the future. [source] | Advanced-Online had a data breach in 2017, in California. Advanced-Online learned on January 3, 2018 that certain personal information housed on the company’s online platform may have been subject to unauthorized access. The date range for the incident appears to be April 29, 2017 until January 12, 2018. Upon becoming aware of the potential unauthorized access, Advanced-Online promptly engaged a nationally recognized cybersecurity and forensics firm to assess and address the situation. Advanced-Online and our cybersecurity and forensics firm believe that the following categories of information may have been compromised: name, address, username/email address, password, and payment card information (account number, expiration date, CVV number). [source] | |
AeroGrow International had a data breach in 2015, in Colorado. AeroGrow International Inc. informed customers of a data breach to their online servers when malware was detected on their system from October 15, 2014 through April 27, 2015. The information compromised included names, addresses, payment card account numbers, expiration dates, and CCV/CVV numbers. [source] | Aetna of Connecticut had a data breach in 2010, in Connecticut. A number of insured customers were affected by an unauthorized access or accidental disclosure of personal information in September. [source] | |
AHM, Inc. on behalf of the Staybridge Suites Lexington & Holiday Inn Express New Buffalo had a data breach in 2017, in Michigan. AHM, Inc. on behalf of the Staybridge Suites Lexington & Holiday Inn Express New Buffalo suffered a breach that affected 344 records, which included Account # and CC/DC account information. [source] | Alaska Communications had a data breach in 2014, in Alaska. Alaska Communications informed customers of a potential data breach on January 27, 2014. One of the company desktop computers was infected with a virus and subsequently sent data outside of their network. Possible personal information compromised could have included names, addresses, dates of birth, and Social Security numbers. The company stated they did not see any evidence of dependent, medical, or banking information that was compromised. The company is offering 1 year of AllClear ID protection at no cost and can be reached at 8-1-866-979-2593 for both AllClear Secure and AllClear PRO services.[source] | |
Allen Dell P.A. had a data breach in 2016, in Florida. [source] | Alliance Health had a data breach in 2015, in Utah. Alliance Health has put up a notification on their site regarding a databreach that potentially exposed their customers personal health information.\"Alliance Health had a configuration error in its MongoDB Database installation. The leak was reported to DataBreaches.net by Chris Vickery, who has uncovered other leaks including the Systema Software leak affecting numerous clients and millions of insurance or workers compensation claims.\" [source] | |
Alton Lane had a data breach in 2016, in New Hampshire. In late Nov. 2017, Alton Lane received notice that in or about November of 2017, malicious code was injected into its IT systems, allowing unauthorized access to certain data, including personal and financial information, that was stored on or managed by the systems. The time period of this code appears to have impacted users is approximately November of 2016 through November of 2017, unauthorized users may have had access to consumer information collected by Alton Lane via its website, affecting five (5) New Hampshire residents. [source] | Alton Lane had a data breach in 2017, in New Hampshire. In late November 2017, Alton Lane received notice that in or about November 2016, malicious code was injected into its information technology systems. Unauthorized users may have had access to consumer information collected by Alton Lane via its website. [source] | |
American Apparel, Inc. had a data breach in 2015, in California. [source] | American Association of Retired Persons, AARP Insurance had a data breach in 2010, in District Of Columbia. A client received another clients information in an insurance policy letter. He attempted to trace the mistake and notified the organization that underwrites AARPs life insurance program, New York Life Insurance. It is unknown how this error occurred and client names, phone numbers, policy numbers, check account information and dates of birth could have been exposed. [source] | |
American Bankers Association had a data breach in 2015, in District Of Columbia. American Bankers Association notified individuals of a data breach of their Shopping Cart affecting 6,400 records. The information compromised included Shopping Cart user names and passwords, which were posted online. At this time the company has stated that they do not believe that any financial information was compromised.The company is requesting that individuals change their online passwords. [source] | American Bankers Association had a data breach in 2015, in District Of Columbia. The American Bankers Association has notified customers of a data breach when email addresses and passwords used to make purchases on their site or used to register for events were compromised. "6,400 users' records had been posted online, the trade group said, though there was no evidence that credit card or other personal financial information had been accessed." [source] | |
American Express had a data breach in 2014, in New York. American Express sent out notification to cardholders regarding unauthorized activity on their cards from unnamed merchants. American Express has stated that names, card account numbers and expiration dates of cards could have been affected. At this time they have stated that no Social Security numbers have been affected.American Express has placed a fraud alert on their cardholders credit reports. [source] | American Express Company had a data breach in 2014, in New York. American Express announced, as part of an investigation by law enforcement and/or American Express, the company discovered a data breach that involved customer information. The data recovered included American Express cardholder acount numbers, names and other card information such as the expiration date. They have stated that Social Security numbers were not impacted and their systems did not detect any unauthorized activity on card holders accounts as related to this incident.UPDATE: (1/16/2014): American Express has sent out a new letter addressed to customers affected by the data breach. This new communication entailed information that one of the merchants that they purchased goods with was affected by the breach. The information breached did not change, in that card holder account numbers, names and other card information such as expiration date were compromised. No Social Security numbers were impacted. [source] | |
American Family Care had a data breach in 2014, in Alabama. American Family Care of Birmingham is alerting customers following the theft of two laptops containing sensitive information from an employee’s vehicle earlier this summer.The information on the laptops contained personal information of patients specifically related to work injuries, physicals, immunizations and drug screens. The lap top also included the names, dates of birth, addresses, phone numbers, medical record numbers, Social Security Numbers, additional medical information, insurance information, driver's license numbers and dates of service. [source] | American Optometric Association had a data breach in 2017, in Missouri. Another wave of malicious credit-line openings related to an ongoing suspected data breach are impacting students and doctors of optometry within the past week. These affected parties-like the initial group-report receiving unsolicited, fraudulent applications for Chase Amazon.com Visa cards submitted in their name. In some cases, these cards are approved.At the direction of the AOA's Board of Trustees, the AOA apprised federal authorities of the breach, including the U.S. Attorney General's Office (member login required) and Department of Justice. Additionally, the AOA called for a united front among affiliates and others, asking optometric testing organizations and state boards of optometry to immediately discontinue use of SSNs as personal identifiers. This petition resulted in the National Board of Examiners in Optometry (NBEO) eliminating the use of SSNs in favor of OE Tracker numbers. As of Jan. 26, the NBEO announced that its own months-long investigation into its systems found no evidence of compromised personal information. [source] | |
American Soccer Inc./SCORE had a data breach in 2014, in California. On October 21, 2014 SCORE discovered an unauthorized access to their server that processes customer payment information.According to the company on September 4, 2014 unauthorized access to their website compromised personal information of individuals who completed a transaction.The information includes names, payment card account numbers, expiration dates of cards, SCORE account numbers. Those who were affected conducted a transaction between June 1, 2014 and September 4, 2014. There was no evidence that customer addresses or security codes being compromised after an investigation was conducted.For those with questions or concerns call 1-800-626-77741-800-626-7774. [source] | American Tire Distributors had a data breach in 2017, in North Carolina. [source] | |
America's Job Link Alliance had a data breach in 2017, in Kansas. Hackers have breached America's Job Link Alliance (AJLA), a job portal offered by the Department of Labor (DOL), and stolen personal details from an undisclosed number of job seekers.AJLA, a multi-state database of US job seekers, acknowledged the security breach through a message on its website.Hackers stole information from job seekers in 10 statesAccording to AJLA officials, hackers registered an account on the job portal and then used a vulnerability in the AJLA source code to extract data from other users.An investigation revealed hackers managed to get access to names, dates of birth, and Social Security Numbers for users in ten of the sixteen states catered by the AJLA portal.Affected states include Alabama, Arizona, Arkansas, Delaware, Idaho, Illinois, Kansas, Maine, Oklahoma, and Vermont. Currently, job seekers in Georgia, Indiana, Kentucky, Nevada, New Jersey and Massachusetts don't appear to be affected.[source] | America's Thrift Stores had a data breach in 2015, in Georgia. America's Thrift Stores notified customers of a data breach when they thrift store chain discovered the software used through a third-party service provider was compromised.The hacking, alledgedly from Eastern Europe, compromised customer credit card or debit card information was compromised. [source] | |
Ameritas Life Insurance Corp. had a data breach in 2012, in Nebraska. A laptop was stolen or discovered stolen sometime around March 21, 2012. It contained the sensitive health information of 3,000 people. The incident was posted on the HHS website on June 8.UPDATE(08/03/2012): An official notice states that an employee notified Ameritas that their laptop and other items were stolen from their car on March 21. The laptop contained information used to provide group dental and vision quotes, as well as individual member enrollment information for employer-sponsored group health plans. The laptop was password protected but not encrypted. Names, Social Security numbers, addresses, dates of birth, and places of employment may have been exposed. [source] | Ancestry's RootsWeb.com had a data breach in 2017, in Utah. Ancestry's RootsWeb.com server, which hosts a free genealogical community site, exposed a file containing emails, login information, and passwords of 300,000 users.hile the 300,000 accounts were affiliated with RootsWeb.com's surname list service that it retired earlier this year, 55,000 of the user names belonged to both the free RootsWeb.com site and also to Ancestry.com, which charges for some of its genealogical services. The company noted that 7,000 of the emails and log-in credentials belonged to active Ancestry.com users.RootsWeb does not host sensitive information like credit card and social security numbers, the company stated, further noting it has "no reason to believe that any Ancestry systems were compromised." [source] | |
Anthem Blue Cross Blue Shield had a data breach in 2017, in Indiana. Anthem BlueCross BlueShield began notifying customers last week of a breach affecting about 18,000 Medicare members. The breach stemmed from Anthem’s Medicare insurance coordination services vendor LaunchPoint Ventures, based in Indiana.LaunchPoint discovered on April 12 that an employee was likely stealing and misusing Anthem and non-Anthem data. The employee emailed a file containing information about Anthem’s members to his personal address on July 8, 2016.The file contained Medicare ID numbers, including Social Security numbers, Health Plan ID numbers, names and dates of enrollment. Officials said limited last names and dates of birth were included. [source] | Anthem had a data breach in 2015, in Indiana. Anthem, the second largest health insurance company operating under Anthem Blue Cross, Anthem Blue Cross and Blue Shield Amerigroup and Healthlink has suffered a massive data breach.The company announced that they have been the victim of a "very sophisticated external cyber attack" on their system. The information compromised includes names, birthdays, medical ID's, Social Security Numbers, street addresses, e-mail addresses, employment and income information. [source] | |
Anthem had a data breach in 2017, in Indiana. [source] | Apple America Group LLC had a data breach in 2015, in Ohio. Apple America Group, LLC informed employees of a data breach when a portable USB flash drive owned by a third party vendor containing payroll information was lost.The information on the portable usb drive included names, addresses, Social Security numbers, and wage and tax information. [source] | |
Apple had a data breach in 2014, in California. Apple has revealed a security protocol breach of their iOS and OS X systems. The hacker was able to insert him/herself between the initial verfication and verification session's destination server. This type of hacking allows the hacker to take over as the trusted user. The destination server sees the hacker as the trusted user and will then allow the hacker to access secured connections such as websites, email messages, applications where you would typically enter a user id and password. [source] | Aptos Inc had a data breach in 2017, in Georgia. Shoppers of 40 online stores have had their bank card numbers and addresses slurped by a malware infection at backend provider Aptos.The security breach occurred late last year when a crook was able to inject spyware into machines Aptos used to host its retail services for online shops. This software nasty was able to access customer payment card numbers and expiration dates, full names, addresses, phone numbers and email addresses, we're told.Rather than being alerted to the infiltration by Aptos itself, instead we were warned this week by Aptos' customers – the retailers whose websites were infected by the malware on the backend provider's servers.According to these stores, which have had to file computer security breach notifications with state authorities, the malware was active on Aptos systems from February through December of 2016. [source] | |
Arby's had a data breach in 2017, in Georgia. Sources at nearly a half-dozen banks and credit unions independently reached out over the past 48 hours to inquire if I’d heard anything about a data breach at Arby’s fast-food restaurants. Asked about the rumors, Arby’s told KrebsOnSecurity that it recently remediated a breach involving malicious software installed on payment card systems at hundreds of its restaurant locations nationwide.A spokesperson for Atlanta, Ga.-based Arby’s said the company was first notified by industry partners in mid-January about a breach at some stores, but that it had not gone public about the incident at the request of the FBI."Arby’s Restaurant Group, Inc. (ARG) was recently provided with information that prompted it to launch an investigation of its payment card systems," the company said in a written statement provided to KrebsOnSecurity. [source] | Arkansas Blue Cross and Blue Shield had a data breach in 2015, in Arkansas. On June 16, 2015, two unencrypted desktop computers containing the protected health information (PHI) of approximately 560 individuals were stolen from the business associate (BA), Treat Insurance Agency, at its North Little Rock offices. The BA is an insurance broker that solicits and submits applications for health insurance coverage to the covered entity (CE), Arkansas Blue Cross and Blue Shield. The types of PHI involved in the breach included demographic, clinical and financial information. The CE provided breach notification to HHS, affected individuals, and the media. OCR reviewed the BA agreement in place between the CE and the BA and determined that the BA agreement was compliant with 45 C.F.R. §§ 164.314 and 164.504. Location of breached information: Desktop Computer Business associate present: No [source] | |
ArmorGames had a data breach in 2014, in California. [source] | Ashley Madison (owned by Canadian Avid Life Media) had a data breach in 2015, in Ontario. Ashley Madison, the online cheating website, confirmed a hack of their system, exposing 40 million records.The data that was stolen included the company's user databases, financial records along with other confidential information. The company has not stated the exact personal information compromised."Reached by KrebsOnSecurity late Sunday evening, ALM Chief Executive Noel Biderman confirmed the hack, and said the company was "working diligently and feverishly" to take down ALM’s intellectual property. Indeed, in the short span of 30 minutes between that brief interview and the publication of this story, several of the Impact Team’s Web links were no longer responding. Besides snippets of account data apparently sampled at random from among some 40 million users across ALM’s trio of properties, the hackers leaked maps of internal company servers, employee network account information, company bank account data and salary information." [source] | |
AT&T had a data breach in 2014, in Texas. AT&T is at the center of another data breach to their system, this time, by an internal employee. AT&T has announced that one of its staff members accessed account information of customers, which included Social Security Numbers, drivers license numbers, unique customer numbers, known as Customer Proprietary Network Information (CPNI), which includes information such as times, dates, durations and destination numbers of every call made. No specific numbers have yet been released.(10/7/2014): The Vermont Attorney General posted that 1,600 letters went out to customers regarding the recently announced data breach that happened in August of 2014 by an employee of AT&T. The employee has since been fired and the breach is still under investigation. [source] | Atkinson, Andelson, Loya, Ruud & Romo had a data breach in 2015, in California. The lawfirm of Atkinson, Andelson, Loya, Ruud & Romo notified clients of a data breach, when one of their attorney's laptops was stolen that contained personal information of their clients.The personal information on the laptop included names, addresses, telephone numbers, Social Security numbers, possible financial information, and medical records information. The firm is providing MyIDCare, ID Experts for free for 12 months for those who were affected. They can be reached by calling 1-877-341-4604. Monday through Friday from 6:00 a.m to 6 p.m Pacific Time. [source] | |
Atlantic Automotive Corporation/dba One Mile Automotive had a data breach in 2014, in Maryland. One Mile Automotive is notifying customers of a data breach of one of their third party vendors, Trade Motion who operates automobile websites and has notified One Mile Automotive that this breach could have included personal information of some of its customers.The information included names, addresses, email addreasses, telephone numbers, credit card information. [source] | Atlantis, Paradise Island had a data breach in 2016, in Grand Bahama. Atlantis, Paradise Island (the "Resort") today announced that a recent data security incident may have compromised the security of payment information of some customers who used debit or credit cards at food and beverage and retail locations at the Resort between March 9, 2016 and October 22, 2016. Customers can now safely use their credit and debit cards at the food and beverage and retail locations at the Resort. This incident did not affect credit and debit cards used to make or pay for hotel reservations or purchases made by guests who charged their food and beverage or retail purchases back to their room.What Happened? The Resort began investigating unusual activity after receiving reports from its credit card processor. The Resort immediately began working with third-party forensic experts to investigate these reports and to identify any signs of compromise on its computer systems. On October 21, 2016, the Resort discovered suspicious files on its computer systems that indicated a potential compromise of customers’ credit and debit card data for some credit and debit cards used at food and beverage and retail locations at the resort.Since that time, the Resort has been working with third-party forensic investigators to determine what happened and what information was affected. The Resort has confirmed that malware may have captured data from some credit and debit cards used at food and beverage and retail locations at the Resort. The Resort has removed the malware at issue to contain this incident and implemented additional procedures in an effort to prevent any further unauthorized access to customers’ credit and debit card information. [source] | |
Auto Pride Car Wash had a data breach in 2017, in California. Auto Pride Car Wash was informed on March 27, 2017 that our point-of-sale system experienced an intrusion last month. Our point-of-sale system is operated by a third-party platform provider and this provider experienced the intrusion. To date, the investigation indicates that the intruder placed malware on the point-ofsale system, and by doing so gained access to our customers’ payment card data, including the cardholder’s first and last name, payment card number, and security code. If you used a payment card at any of our locations between the dates of 02/11/17 – 02/27/17, your payment card information may be at risk. Because we are unable to determine contact information for each customer whose information may be at risk, we are notifying our customers of this risk in this Substitute Notice. What information was involved? For those customers who used a payment card at our location(s) between the dates of 02/11/17 – 02/27/17, the information the intruder had access to includes the cardholder’s first and last name, card number and security code. [source] | Automotive Recovery Services Inc. had a data breach in 2015, in Illinois. Automotive Recovery Services (ARS) notified customers of a breach when an unauthorized party gained access to one of their legacy systems compromising customer information.The information compromised included names, Social Security numbers, street addresses, email addresses, phone numbers, driver's license numbrs, the type of vehicles donated, name of the charity that the vehicle was donated to.The company is providing identity theft protecton for 12 months for free with AllClear ID. For those with a questions call 1-855-861-4023.More Information: http://oag.ca.gov/ecrime/databreach/reports/sb24-56920 [source] | |
AutoNation Toyota of South Austin had a data breach in 2014, in Texas. AutoNation Toyota of South Austin informed customers of a data breach that occured when a third party vendor, TradeMotion, who operates parts websites for auto dealers nationwide, had their systems hacked potentially exposing credit card information that was stored on their system. The hackers may have also gotten names, addresses, telephone numbers, and email addresses.The company has arranged for those affected to receive one year of identity theft protection through Experian's ProtectMyID. [source] | Avis Budget Group had a data breach in 2015, in New Jersey. Avis Budget Group notified customers of a data breach when the third-party provider that manages their open enrollment process accidentally sent a file to another company that is also their client. The information exposed to this other client included names, addresses and Social Security numbers. [source] | |
AvMed Health Plans had a data breach in 2010, in Florida. AvMed Health Plans announced that personal information of some current and former subscribers may have been compromised by the theft of two company laptops from its corporate offices in Gainesville. The information included names, addresses, phone numbers, Social Security numbers and protected health information. The theft was immediately reported to local authorities but attempts to locate the laptops have been unsuccessful. AvMed determined that the data on one of the laptops may not have been protected properly, and approximately 80,000 of AvMeds current subscribers and their dependents may be affected. An additional approximate 128,000 former subscribers and their dependents, dating back to April 2003, may also have been affected.UPDATE (06/03/2010): The theft of the laptops compromised the identity data of 860,000 more Avmed members than originally thought. The total now nears 1.1 million. [source] | Ayuda Medical Case Management had a data breach in 2012, in Texas. Thousands of patient records were found in an unsecured trash can. They contained names, Social Security numbers, addresses, phone numbers, medical conditions, and treatment information. The boxes of medical records were traced to Ayuda, whose owner claimed to have been doing little or no business after losing a state contract in September. The boxes were auctioned off after the owner failed to pay the rental fee on a storage unit. [source] | |
Backcountry Gear had a data breach in 2014, in Oregon. Backcountry Gear notified customers of a data breach with a server that handles credit card information. The company discovered malware that was put onto their server that was able to gain customer names, addresses, purchase information, and credit card/debit card information. The company has stated they do not collect pin numbers or bank account numbers in a transaction so those would not have been compromised in the breach.For those who were affected and have questions can call 1-800-953-5499 ext. 5 or email at data@backcountrygear.com. [source] | Bailey's Inc. had a data breach in 2016, in California. Bailey's Inc. have notified customers of a data breach when an unauthorized party access their website server, obtaining credit card information of customers who puchased items from the company's online store. [source] | |
Bartell Hotels had a data breach in 2014, in California. Name, address, credit/debit card info were breached. [source] | BB&T Insurance had a data breach in 2008, in Virginia. A BB&T Insurance laptop containing the personnel information of some Harrisonburg City Schools employees was stolen. The laptop, used by an outside sales representative to develop an insurance proposal for the school system, was stolen from a car. The information contained names, dates of birth, Social Security numbers, and, in some cases, medical history. [source] | |
BeautifulPeople.com had a data breach in 2016, in New York. BeautifulPeople.com notified individuals of a data breach when their system was hacked compromising personal information. The information included member's names, addresses, sexual preferences, relationship status, phone numbers, email addresses and private messages. [source] | BeautyBlender had a data breach in 2017, in Pennsylvania. Beautyblender was recently contacted by two customers reporting fraud on credit cards used to make purchases on our site. Beautyblender discovered what it believed was a form of malicious code on its site on October 26, 2017 which it then removed. The specific information that may have been obtained by the unidentified third party included the customers’ name, billing address, full credit card number, expiration date, and CVV number, affecting 3,673 California residents. A third party forensic investigator was also retained to assist with beautyblender’s investigation. On November 27, 2017, the forensic investigator confirmed that the malware inserted into the website collected certain payment card information used at checkout.On January 5, 2018, beautyblender will begin providing written notice of this incident to all potentially affected customers, which includes three thousand, six hundred and seventy-three (3,673) California residents. On January 5, 2018, beautyblender will begin providing written notice of this incident to all potentially affected customers, which includes three hundred and nine (309) Oregon residents. [source] | |
Bebe Retail had a data breach in 2014, in California. Name and payment card info were breached. [source] | Bed Bath & Beyond, Inc. had a data breach in 2018, in New Jersey. A call center employee processing orders over the phone illegally compromised three customers' credit card information. BB&B recently determined that this same employee processed an order for one North Carolina resident over the phone between November 21, 2017 and December 8, 2017, although they do not know if that customer's credit card number was compromised. [source] | |
Bed Bath and Beyond had a data breach in 2015, in New York. Bed Bath and Beyond notified customers of a data breach in their New York city store, between March 7, 2015 and August 3, 2015. Customers who used their cards during that time period have been encouraged to notify their banks of the potential for credit card theft. [source] | Benefits Resources, Inc. had a data breach in 2011, in Ohio. A portable electronic device was lost or stolen on or around November 22, 2010. It contained the PHI of patients. [source] | |
Best Buy had a data breach in 2017. [source] | Beyond Yoga had a data breach in 2016, in California. [source] | |
Big Blue Bus had a data breach in 2015, in California. The Big Blue Bus has notified customers of a data breach when the company discovered unauthorized access at NextBus, a third party company that Big Blue Bus works with to provide real-time bus arrival information to customers. The individual (s) may have gained accress to account information of customers. The company claims that no Social Security numbers or financial information was compromised. [source] | Big Fish Games had a data breach in 2015, in Washington. Big Fish contacted customers of a data breach when they discovered malware installed on their billing and payment pages of their online stores that affected purchases from December 24, 2014 through January 8, 2015. The information affected included names, addresses, and payment card information, including the card number, expiration date, and CVV2 code. The company is providing one year free of Experian's ProtectMyID Alert. [source] | |
BigMoneyJobs.com had a data breach in 2014. [source] | Billy Casper Golf had a data breach in 2016, in Virginia. The information was breached via Email. [source] | |
Black Phoenix, Inc had a data breach in 2018, in California. [source] | Bloomberg had a data breach in 2017, in New York. [source] | |
Blue Beacon had a data breach in 2018, in California. [source] | Blue Cross and Blue Shield of Florida (BCBSF) had a data breach in 2011, in Florida. An April 2011 mailing error caused 3,500 member healthcare statements to be mailed to incorrect addresses. The statements were mailed to the former addresses of members and contained names, insurance numbers, diagnoses codes and descriptions, procedure codes and descriptions, prescription names and provider names. [source] | |
Blue Cross and Blue Shield of Georgia had a data breach in 2008, in Georgia. Benefit letters containing personal and health information were sent to the wrong addresses. The letters included the patients name and ID number, the name of the medical provider delivering the service, and the amounts charged and owed. A small percentage of letters also contained the patients social Security numbers. [source] | Blue Cross and Blue Shield of Kansas City, Inc. had a data breach in 2014, in Maryland. Name, credit card info, bank account info were breached via Desktop Computer. [source] | |
Blue Cross and Blue Shield of North Carolina had a data breach in 2006, in North Carolina. [source] | Blue Cross and Blue Shield of Rhode Island (BCBSRI) had a data breach in 2010, in Rhode Island. A filing cabinet containing survey information from approximately 12,000 BlueCHIP for Medicare members was donated to a local nonprofit organization. The surveys were from 2001 to early 2004 and contained information such as names, Social Security numbers, telephone numbers, addresses and Medicare Identification numbers. [source] | |
Blue Cross Blue Shield Association had a data breach in 2010, in Illinois. An error in the quarterly address update process resulted in the mailing of approximately 15,000 individuals protected health information to incorrect addresses. The information in the letters included demographic information, explanation of benefits, clinical information, and diagnoses. The returned mail was collected and the organization verified whether or not it had been delivered. [source] | Blue Cross Blue Shield of Alabama had a data breach in 2010, in Alabama. A dishonest employee was charged with identity theft. The employee fraudulently obtained credit by using the health insurance information of at least 15 clients. [source] | |
Blue Cross Blue Shield of Massachusetts (BCBS) had a data breach in 2012, in Massachusetts. A BCBS vendor misused BCBS employee information. The misuse appears to have been limited to one instance. Names, Social Security numbers, dates of birth, compensation information, and bank account information may have been exposed. [source] | Blue Cross Blue Shield of Michigan (BCBSM), Tstream Software had a data breach in 2011, in Michigan. A BCBSM website created by Tstream was the source of a breach. A BCBSM found her personal information online when searching her name. People applying for individual health insurance between 2006 and an unclear date had their names, Social Security numbers, addresses and dates of birth exposed. BCBSM was notified of the error on November 17, 2010. The information was accessible for an unspecified amount of time. Though 6,500 BCBSM members were notified, only 2,979 were affected. [source] | |
Blue Cross Blue Shield of Michigan had a data breach in 2015, in Michigan. The information was breached via Email. [source] | Blue Cross Blue Shield of Michigan Blue Care Network had a data breach in 2014, in Michigan. The information was breached via Email. [source] | |
Blue Cross Blue Shield of Nebraska had a data breach in 2015, in Nebraska. Blue Cross Blue Shield of Nebraska notified patients of a data breach when personal information was inadvertently disclosed on dental form claims. "The company said a printing error caused some dental explanation of benefits forms to be sent to the wrong customers. The forms reveal treatment and services that the insurer paid on a customer’s behalf.The company said an internal review found that 1,872 dental plan customers received mail statements that included another customer’s name, member identification number and dental claim information. The forms did not disclose birth dates, Social Security numbers, or financial or employment information. [source] | Blue Cross Blue Shield of North Carolina (BCBSNC) had a data breach in 2015, in North Carolina. Blue Cross BlueShield of North Carolina notifed customers of a data breach when they discovered two incidences that may have exposed personal information.The first incident occurred when a printing error resulted in members' billing invoice information printed on the back of other members' invoices. The information exposed here included names, addresses, internal BCBSNC account numbers, group numbers, coverage dates and premium amounts. The second incident occurred when payment letters included incorrect information and sent to the wrong members. This information included they type of health plan purchased, effective dates, health insurance marketplace identification numbers, payment amounts, telephone numbers and payment identification numbers. [source] | |
Blue Cross Blue Shield of South Carolina had a data breach in 2016, in South Carolina. Name and ssn were breached via Website. [source] | Blue Mountain Community Foundation had a data breach in 2014, in Maryland. Name and ssn were breached via Website. [source] | |
Blue Shield of California/Department of Managed Healthcare had a data breach in 2014, in California. [source] | Blue Shield of California had a data breach in 2016, in California. Blue Shield of California admitted to a PHI data breach involving an insurance broker who was not authorized to receive patient information, according to a breach notification submitted to the California Attorney General’s Office. The Blue Shield of California Privacy Office received confirmation on March 23, 2018 that a breach had occurred in November 2017 during the 2018 Medicare Annual Enrolment Period when a Blue Shield employee emailed a document containing PHI to an insurance broker "in violation of Blue Shield policies."The PHI included names, home addresses, mailing addresses, Blue Shield subscriber identification numbers, telephone numbers, and subscribers’ Blue Shield Medicare Advantage plan numbers.Blue Shield of California said that it believes the insurance broker may have contacted some of the individuals identified in the document to sell a Medicare Advantage Plan offered by another health insurance company.The health insurer said that individuals affected by the disclosure are eligible for free identity repair and credit monitoring services. [source] | |
Blue Shield of California had a data breach in 2016, in California. The information was breached via Network Server . [source] | Blue Shield of California had a data breach in 2017, in California. Per Health and Human Services Blue Shield of California suffered a data breach when one of their network servers was hacked. No information was provided as to what information was compromised in the hack. [source] | |
BlueCross Blue Shield of North Carolina had a data breach in 2012, in North Carolina. A mailing software error caused the private information of current and former Blue Cross Blue Shield members to be mailed to other members. The error was discovered on April 12. The records were more than 10 years old and included patient names, Social Security numbers, type of medical care received, and other protected health information. [source] | Blue-Cross Blue-Shield of Western New York had a data breach in 2008, in New York. A laptop hard-drive containing vital information about members has gone missing. Blue-Cross Blue-Shield of Western New York says it is notifying its members about identity theft concerns after one of its company laptops went missing. [source] | |
Boersma Bros.LLC/dba DutchWear had a data breach in 2014, in Oregon. Boersma Brothers, dba DutchWear suffered a databreach when their website was breached exposing the payment information for customers from November 7 and December 6, 2014. The information compromised included names, addresses, phone numbers, credit card numbers, expiration dates, and credit card security codes. The company has set up a toll-free help line for customers at 1-844-835-8656 from 8 a.m. and 4 p.m PST, Monday through Friday. [source] | Bombas, LLC had a data breach in 2018, in California. Bombas sells socks online using an outside vendor to develop and manage their website and a third party e-commerce platform for purchases. Malware in the code of the e-commerce platform was identified and initially removed from their website on January 15, 2015, and then finally removed on February 9, 2015. They cannot determine which transactions were impacted, and are sending notice to all of the approximately 41,000 customers who made a credit card purchase on the website during the period the malware may have existed, essentially from the date of launch of the website, September 1, 2013, until the day the identified malware was finally removed.What Information was Involved?The data accessed may have included personal information such as name, address, and credit card information. [source] | |
Boomerang Tags.com had a data breach in 2014, in California. Boomerand Tags.com notified customers of a data breach to their online website. The company released a letter to customers stating that hackers installed some form of malware onto the server that manages their website. The motivation of the hackers appears to be to gain the credit card information of the individual. Individuals financial information may have been exposed from July 4, 2013 through February 18, 2014. [source] | BraceAbility had a data breach in 2016, in Iowa. The information was breached via Email. [source] | |
Brazzers.com had a data breach in 2016, in Quebec. The information was breached via Desktop Computer. [source] | Brinderson had a data breach in 2017, in California. [source] | |
Brinker International, Inc. had a data breach in 2018, in California. Time Warner Cable, now known as Spectrum, became the latest company to realize exactly how vulnerable its data is when a third-party vendor entrusted with its safety made an error exposing millions of records.Kromtech Security Center researchers discovered late last week that about four million Time Warner customer records were exposed when it found two cloud-based AWS S3 buckets, connected to software and service provider BroadSoft, open to the public. The information compromised spanned the period from November 10, 2010 to July 7, 2017, and included transaction numbers, MAC numbers, user names, account numbers types of service purchased along with internal development information like SQL database dumps and code with login credentials, Kromtech said. [source] | Brooks Brothers had a data breach in 2017, in New York. U.S. clothing company Brooks Brothers said on Friday payment card information of certain customers were compromised at some of its retail locations in the United States and Puerto Rico over 11 months until March.The company said that an unauthorized individual was able to gain access to and install malicious software designed to capture card information on some of its payment processing systems at the locations.Some customers who shopped at certain Brooks Brothers and Brooks Brothers Outlet retail locations between April 4, 2016 and March 1, 2017 were affected, the company said.Brooks Brothers said the malicious software could have affected payment card data – including names, payment card account numbers, card expiration dates and card verification codes.However, the company said no sensitive personal information, such as Social Security numbers or customer addresses, was impacted.Brooks Brothers, which operates over 400 stores worldwide, said it had engaged independent forensic experts and alerted law enforcement after being informed of the breach. [source] | |
Buckeye Community Health Plan had a data breach in 2006, in Ohio. Four laptop computers containing customer names, Social Security numbers, and addresses were stolen from the Medicaid insurance provider. [source] | Bulk Reef Supply had a data breach in 2015, in Minnesota. Bulk Reef Supply notified customers of a data breach when their online website was compromised. The customer information compromised included names, addresses, phone numbers, email addresses, usernames, passwords, and credit card information. The company is asking customers to change their passwords. [source] | |
Bulletproof had a data breach in 2017, in Washington. [source] | Cahaba Government Benefit Administrators LLC had a data breach in 2011, in Alabama. On April 11, 2011, someone discovered that sensitive paper records had been disclosed to outside parties or accessed without authorization. Centers for Medicare and Medicaid Services (CMS) uses Cahaba for administration of Medicare fee-for-service programs. [source] | |
California DMV had a data breach in 2014, in California. The California DMV is investigating a potential data breach of their credit card processing systems. Reportedly several large financial institutions received private alerts this week from MasterCard about compromised cards used for charges. As reported by Krebs on Security, "the alert, sent privately by MasterCard to financial institutions this week, did not name the breached entity but said the organization n question experienced a "card-not-present" breach-industry speak for transactin conducted online. The alert further stated that the date range of the potentially compromised transactions extended from August 2, 2013 to January 31, 2014, and that the data stolen included the card number, expiration date, and three-digit security code printed on the back of cards".Krebs contacted 5 different financial institutions, two mid-sized California banks and "confirmed receipt of the MasterCard notice, and said that all of the cars MasterCard alerted them about as cmopromised had been used for charges bering the notation "STATE OF CALIF DMV INT."The DMV, who originally stated they would investigate, put out a statement at 6:44 Eastern Time on March 22, 2014, placing blame on the the third party credit card processing company.The total amount of individuals potentially affected at this time is unknown. KrebsOnSecurity stated that they had received a list of more than 1,000 cards, from one bank, that were potentially exposed that included credit card numbers, expiration dates and three-digit security codes printed on the back. [source] | California Physicians Service d/b/a Blue Shield of California had a data breach in 2018, in California. The information was breached via Email . [source] | |
California Virtual Academies had a data breach in 2016, in California. California Virtual Academies (CAVA) notified individuals of a data breach to their system. On December 9, 2015 the company discovered a "vulnerability in a data storage system" belonging to a third party provider.For those with questions call 1-805-587-0202 Monday through Friday 8:00 a.m to 5:00 p.m Pacific Standard Time. [source] | Care Plus Health Plans had a data breach in 2015, in Florida. CarePlus Health Plans have notified customers of a data breach when an error in processing their statements exposed their personal information to other members. The machine that processed these statement had a programming error that inserted two statements into one envelope vs. just one.According to the company, no Social Security numbers were on these statements. The information compromised included names, addresses and CarePlus identification numbers. For those affected, call 1-800-794-5907 from 8:00 a.m. to 8 p.m ESt seven days a week. More information: http://www.wtsp.com/story/news/health/2015/10/09/careplus-might-mishandl... [source] | |
CareFirst BlueCross BlueShield had a data breach in 2015, in Maryland. The information was breached via Paper/Films. [source] | Castle Creek Properties, Inc./Rosenthal Wine Shop had a data breach in 2014, in California. Castle Creek Properties Inc/ Rosenthal Malibu Estate notified customers of unauthorized access to computer systems used to process credit card transactions at their Rosenthal wine shop. The unauthorized access may have compromised payment card data of visitors who used their cards for payment of items at the wine shop tasting room. Information compromised included names, addresses, payment card account numbers, card expiration dates and security codes. The company is offering a complimentary one year membership of Experian ProtectMyID Alert. For those affected and wish to enroll in the services they are asked to call 1-310-899-8903. [source] | |
Catalyst Health Solutions, Alliant Health Plans, Inc. had a data breach in 2012, in Georgia. An unauthorized disclosure resulted in the exposure of protected health information. The breach occurred on or around January 1, 2012 and was reported on April 17. This incident was reported on the HHS website. [source] | Catholic United Financial had a data breach in 2017, in Minnesota. A data breach at an Arden Hills-based financial services company serving Catholic Church members in the upper Midwest has affected nearly 130,000 current and former members.The unidentified hacker accessed the first and last names, mailing addresses, dates of birth, email addresses, insurance policy information, and Social Security numbers of members. Beneficiary information, log-in credentials and other information were not accessed. [source] | |
Centers for Medicare & Medicaid Services (CMS) had a data breach in 2012, in Maryland. On August 3, 2010 paper records were discovered stolen. It is not clear who the paper records belonged to, where they were stolen from, and what type of information the records contained. [source] | Centra had a data breach in 2010, in Georgia. A laptop was stolen from the trunk of an employees rental car overnight on November 11. Patient names and billing information were on the laptop. The delay in notification occurred because of the time it took to determine what information was on the stolen laptop.UPDATE (1/14/11): The total number of affected individuals was changed from 13,964 to 11,982. [source] | |
Cetera Advisors, LLC had a data breach in 2017, in Colorado. Cetera Advisors, LLC suffered a hack on 11/8/2017, affecting 1,260 records, exposing social security numbers. [source] | Chic-Fil-A had a data breach in 2015, in Georgia. Chic-Fil-A has announced they are investigating a possible data breach to their payment card system. They have not released any details as to the reality of the breach, however, many experts are predicting it could be extensive.The restaurant chaind operates over 1,850 stores nationwide. Suspicious activity on their payment systems and a report provided to the on December 19, 2014 as to suspicious activity, prompted the company to launch an investigation. [source] | |
Chiorini, Hunt & Jacobs, Certified Public Accountants had a data breach in 2017, in California. Popular Mexican food chain Chipotle is warning customers about a data breach.The company says it recently found unauthorized activity on a network used for payment processing in its restaurants. Chipotle immediately launched an investigation, and believe it has stopped the unauthorized activity. Additional security measures have also been put in place.Investigators are focusing on payment card transactions made in restaurants between March 24 and April 18 of this year.Chipotle says the investigation is still ongoing, but it does plan to notify affected customers.As a reminder, Chipotle says you should always monitor your payment card statements and contact your bank if you see any suspicious charges. [source] | Chipotle Mexican Grill had a data breach in 2017, in Colorado. Popular Mexican food chain Chipotle is warning customers about a data breach.The company says it recently found unauthorized activity on a network used for payment processing in its restaurants. Chipotle immediately launched an investigation, and believe it has stopped the unauthorized activity. Additional security measures have also been put in place.Investigators are focusing on payment card transactions made in restaurants between March 24 and April 18 of this year.Chipotle says the investigation is still ongoing, but it does plan to notify affected customers.As a reminder, Chipotle says you should always monitor your payment card statements and contact your bank if you see any suspicious charges. [source] | |
Cici's Pizza had a data breach in 2016, in Texas. [source] | Cicis Restaurants had a data breach in 2016, in Texas. The information was breached via Paper/Films. [source] | |
CICS Employment Services, Inc had a data breach in 2015, in Oregon. CICS Employment Services notified customers of a data breach when their system was accessed by an unauthorized user (s) gaining access to employment application information on individuals.The information accessed included names, addresses, dates of birth and Social Security Numbers.The company is providing 12 months free of AllClearID. Call 1-855-865-4453. [source] | Cisco had a data breach in 2016, in California. The information was breached via Website. [source] | |
City of Virginia Beach, Flexible Benefits Administrators had a data breach in 2007, in Virginia. A former employee allegedly stole Virginia Beach city and school district employees personal information and used it to commit prescription fraud. Police discovered a list of names and Social Security numbers at the employees home. [source] | Clarks Americas, Inc. had a data breach in 2016, in Massachusetts. [source] | |
Cloudfare had a data breach in 2017, in California. A well-known Google security researcher discovered that Cloudflare was exposing chat messages, encryption keys, cookies, password manager data, hotel bookings and more. The content delivery network quickly confirmed the finding, traced it to a coding error involving just a single wrong character and put related remediations in place.But the leaked data had been cached by major search engines, and the discovery triggered a frantic effort to remove the cached data before the flaw was publicized. Much of the exposed data would have normally been protected by SSL/TLS, but the nature of the vulnerability caused it to be exposed to the internet in unencrypted form.It's unknown how much data may have been leaked, which may make it difficult for companies and users to decide what their most prudent reaction to this bug report should be.Cloudflare specializes in improving the performance and redundancy of websites, as well as offering protection against attacks such as distributed denial-of-service. [source] | CM Ebar LLC (Elephant Bar restaurants) had a data breach in 2015, in Texas. CM Ebar LLC (Elephant Bar restaurants) notified customers of a data breach when malware was discovered on their payment systems, potentially compromising customer debit and credit card information. The breach affected restaurants in California, Colorado, Arizona, Missouri, Nevada, New Mexico, and Florida. The incident was discovered on November 3, 2015 and affective dates are anywhere from August 12, 2015 through December 4, 2015. [source] | |
Coca-Cola Company had a data breach in 2014, in Georgia. The Coca-Cola Company announced the theft of several computers from one of their locations that contained personal information on employees and other individuals. The company did not detail the specific information that was stored on the stolen computers. The theft was discovered on December 19, 2013.UPDATE (11/13/2014): "A class action lawsuit has been filed against the Coca-Cola company and its regional distribution subsidiaries on behalf of 70,000 people whose information and identities have been allegedly compromised by the theft of 55 laptops from the company's Atlanta headquarters over a six year period."The company did not notice the theft of these laptops until November of 2013 prompting the company to send notices to those affected in January 2014. According to the company 18,000 individuals had Social Security numbers affected, and an additional 56,000 individuals that may have had their drivers license information compromised. The laptops were not encrypted and along with the above information, the laptops may have also included names, addresses, ethnicity and other personal information.The class action suit alleges that the company failed to protect personal data, but failed in adequately notifying victims of the breach. [source] | Cole Taylor Mortgage had a data breach in 2014, in Oregon. Cole Taylor Mortgage (a division of Cole Taylor Bank) informed customers of a data breach that occured due to an error by one of their third party vendors. Information was inadvertently made accessible to employees of another federally regulated bank. The information included names, addresses, Social Security numbers, loan numbers and certain loan information. According to the mortage company, the breach was caused by a technical error by the vendor that provides them information technology services and solutions to both banks. [source] | |
Colorado Department of Health Care Policy and Financing (HCPF) had a data breach in 2011, in Colorado. A disk with the information of medical-aid applicants was lost on its way between HCPF and another agency. It contained applicant names, state identification numbers, and addresses. The disk was discovered missing on May 6. [source] | Colorado Department of Health Care Policy and Financing had a data breach in 2010, in Colorado. A hard drive containing personal information for clients enrolled in state-provided health insurance was stolen from the Colorado Office of Information Technology. The information included names, state ID number and the name of the clients program. The Agency is certain that contact information, financial information and Social Security numbers were not involved. [source] | |
Combat Brands had a data breach in 2017, in Kansas. [source] | Comcast had a data breach in 2015, in California. Comcast may be the latest victim of a breach when 590,000 customer email addresses and passwords were posted on the Dark Web website, an underground site selling people's information for money. The company is denying that they were a victim of a breach, and were "certain that none of their systems or apps had been compromised."The company took precaution and reset passwords of those affected. "Over the weekend, a reader (@flanvel) directed Salted Hash to a post on a Dark Web marketplace selling a number of questionable, if not outright illegal goods. The post in question offered a list of 590,000 Comcast email addresses and corresponding passwords.As proof, the seller offered a brief list of 112 accounts with a going rate of $300 USD for 100,000 accounts. However, one wished to purchase the entire list of 590,000 accounts, the final price was $1,000 USD."More information: http://www.csoonline.com/article/3002604/cyber-attacks-espionage/comcast... [source] | |
Commerce Banc Insurance Services (CBIS) had a data breach in 2007, in New Jersey. A CBIS vendor had a laptop stolen. CBIS employees may have had their names, Social Security numbers, and possibly health information exposed. [source] | Community Catalysts of California had a data breach in 2015, in California. The information was breached via Network Server. [source] | |
Community Health Systems had a data breach in 2014, in Tennessee. The information was breached via Email. [source] | Concordia Plan Services (CPS) had a data breach in 2011, in Missouri. Microfilm that contained the plan enrollment information of benefits members was lost by a delivery service sometime between February and May of 2011. It contained names, addresses, dates of birth and in some cases Social Security numbers and limited medical information from the 1960s and 1970s. A vendor received the microfilm from CPS on February 3rd. The vendor attempted to transfer the microfilm to another company, but learned that the microfilm had been misplaced sometime prior to or during May. CPSs vendor informed them of the situation on August 23. [source] | |
Concordia Plan Services on behalf of the Concordia Health Plan had a data breach in 2015, in Missouri. The information was breached via Network Server. [source] | CoPilot Provider Services Inc. had a data breach in 2017, in New York. [source] | |
Corporation Service Company had a data breach in 2017, in California. The information was breached via Network Server. [source] | Country Mutual Insurance Company had a data breach in 2018, in Illinois. A large mailing was mailed out by our third party vendor. Three COUNTRY Financial packages containing documents with individual personally identifiable information (PII) failed to be delivered by the United States Postal Service to the servicing COUNTRY Representative. They have also been unable to track the current location of these three packages. One additional package containing the same documents was damaged while in transit with the United States Postal Service. In their attempt to resolve the issue they removed the documents and repackaged them. All documents were received by the COUNTRY Representative.Records breached include Account Numbers and SSN. [source] | |
Cox Communications had a data breach in 2015, in Georgia. Recently, the Enforcement Bureau of the Federal Communications Commission (FCC) entered into a settlement with Cox Communications (Cox) resolving an investigation into whether the cable operator failed to properly protect its customers' personally identifiable information (PII) when its electronic data systems were breached in 2014. Cox is the third-largest cable television provider and the seventh-largest telephone carrier in the United States with over six million subscribers. This settlement presents the FCC's first privacy and data security enforcement action with a cable operator, echoing steps the FCC has recently taken against telecommunications providers to regulate and enforce privacy and cybersecurity breaches.The BreachCox's electronic data systems were breached in August 2014 by a hacker using the alias Evil Jordie, a member of the band of teenage cybercriminals known as the Lizard Squad. [source] | cPanel had a data breach in 2016, in Texas. [source] | |
Craftsman Book Company had a data breach in 2014, in California. Craftsman Book Company notified customers of a breach that occured on their site. On Tuesday May 27th the company discovered unauthorized access to their site and recommended a change in their username and password. Since that time they discovered that the breach also included charges on customers credit card. The hackers found another site operated by the company and through the security vulnerabilities in the one site, they were able to get to the Craftsman Book site and ultimately to the customers information.Since the vulnerability was discovered, the company has shut down the other site and is in the process of securing it. [source] | Crescent Hotels & Resorts had a data breach in 2015, in Virginia. Name, dob, ssn were breached. [source] | |
CVS Health had a data breach in 2016, in Rhode Island. [source] | Cyberswim.com had a data breach in 2014, in Pennsylvania. Cyberswim.com notified customers of a data breach to their online ecommerce store and the discovery of customers' personal information being breached.On September 24, 2014 the company confirmed that an unauthorized individual(s) or entities installed malware on the server hosting their website. This malware was able to access personal information entered by customers when completing a purchase on the site.Information breached includes names, addresses, website usernames and passwords, payment card account numbers, card expiration dates, and payment card security codes.Purchases made between May 12, 2014 and August 28, 2014 are the dates this breach occurred. [source] | |
CyrusOne, Inc. had a data breach in 2017, in Texas. CyrusOne, Inc. learned of a breach on 10/18/2017 affecting 402 Indiana residents. Breach resulted in social security numbers being exposed. [source] | Dairy Queen had a data breach in 2014, in Minnesota. [source] | |
DC Chartered Health Plan had a data breach in 2010, in District Of Columbia. [source] | DealerBuilt had a data breach in 2016, in Iowa. If you bought a car in the last few years, there's a good chance your personal information may have found its way to the open internet.Names, addresses, phone numbers, and social security numbers for both customers and employees for over a hundred car dealerships have leaked online, all thanks to a centralized records system coupled with shoddy security.The system, built and operated by DealerBuilt, an Iowa-based database software company, sells management systems for car dealerships across the US, offering a central system for sales, customer relations, and employee payroll needs. [source] | |
Deep Root Analytics had a data breach in 2017, in Virginia. [source] | Deloitte had a data breach in 2017, in London. One of the world’s "big four" accountancy firms has been targeted by a sophisticated hack that compromised the confidential emails and plans of some of its blue-chip clients, the Guardian can reveal.The Guardian understands Deloitte clients across all of these sectors had material in the company email system that was breached. The companies include household names as well as US government departments.So far, six of Deloitte’s clients have been told their information was "impacted" by the hack. Deloitte’s internal review into the incident is ongoing.The Guardian understands Deloitte discovered the hack in March this year, but it is believed the attackers may have had access to its systems since October or November 2016. [source] | |
Delta Air Lines, Inc. had a data breach in 2018, in California. Delta now says that payment-card information for about "several hundred thousand" airline customers may have been exposed by a malware breach last fall that also hit Sears and other companies.The airline says that the malware attack may have exposed customers’ names, addresses, credit card numbers, card security codes and expiration dates.Delta Air Lines Inc. offered the additional details about the attack on Thursday, a day after saying that only a "small subset" of customers was affected.The Atlanta-based airline said that it wasn’t sure whether customers’ information was actually compromised by malware that it believes was in software used by (24)7.ai, which provided the airline with online chat services for customers, for about two weeks. The software company said it discovered and fixed the breach in October. [source] | Delta Dental of Illinois had a data breach in 2012, in Illinois. A box that contained paper claims information and X-rays was lost during shipping between an unnamed subcontractor and Delta Dental of Illinois. The paperwork included enrollees dates of birth, Social Security numbers, and other information that dentists provided on their claims. [source] | |
Delta Dental of Pennsylvania, ZDI had a data breach in 2013, in Pennsylvania. The March 20 loss of paper records may have exposed the information of patients. ZDI lost the records of their associate Delta Dental of Pennsylvania. [source] | Digital Theatre, LLC (ShowTix4U) had a data breach in 2015, in Nevada. Digital Theatre, LLC which operates ShowTix4U notified individuals of a data breach when some payment cards were affected. Investigators found between late April 2015 and late September 2015 unauthorized access was discovered on a computer server hosting ShowTix4U's website. The information compromised names, addresses, payment card account numbers, card expiration dates, and payment card security codes of customers. [source] | |
Discover Financial Services had a data breach in 2014, in Utah. Discover Financial Services sent a notice to their card holders that they were replacing their current cards in wake of all of the retail data breaches. They stated this was not due to a breach of their own systems. The card replacement specifically replaces the security codes on the back of the card withouth changing the card holders current account number.They have stated to their members this was strictly a security measure on behalf of Discover Financial Services. No information was communicated in the letter that the members card had been compromised. [source] | Disney Consumer Products and Interactive Media had a data breach in 2016, in California. On December 12, 2014, the covered entity (CE), District Medical Group, reported that when a workforce member used a thumb drive while working from home the contents of the thumb drive became accessible on the Internet. The media device contained the electronic protected health information (ePHI) of approximately 616 individuals. The PHI involved in the breach included names, addresses, social security numbers, transaction amounts and clinical information. The CE provided breach notification to HHS, the affected individuals and the media. The CE revised its policies and procedures and retrained workforce members. OCR obtained assurances that the CE implemented the corrective actions noted above. Location of breached information: Other Portable Electronic Device Business associate present: No [source] | |
District Council 37 Health and Security Plan of New York City had a data breach in 2007, in New York. A CD containing prescription drug data was discovered missing from the organizations files. People who had their prescription drugs filled through DC 37s prescription drug benefits plan may have had their names and Social Security numbers exposed. Prescription information from between February 13 and February 22 of 2006 (the previous year) was also exposed. [source] | Diversified Resources Inc. had a data breach in 2011, in Georgia. The theft of a laptop on or around August 11, 2011 resulted in the exposure of protected health information. [source] | |
DocuSign had a data breach in 2017, in California. On January 15, 2018, one of our service providers, Ernst & Young LLP (EY), became aware that on three separate occasions during the week of January 8, 2018, one of their tax professionals had mistyped a fax number while transmitting a total of forty-four (44) Tax Credit and Incentive Forms which contained personal information pertaining to 43 current employees and prospective hires of Dollar General. These faxes were transmitted in connection with the Work Opportunity Tax Credit (WOTC) services EY provides to Dollar General. Due to the EY tax professional transposing digits in the fax number, the Forms were sent to an unintended recipient's fax machine (instead of the fax machine located at another EY office). [source] | Dollar Shave Club, Inc. had a data breach in 2018, in California. On March 21, 2018, Dollar Shave Club Inc.'s tech team identified attempts by a third party system using email and password combinations obtained elsewhere (not from Dollar Shave Club) to log in to certain Dollar Shave Club customers’ e-commerce accounts. This incident involved the email address and password combinations (obtained through some other source, not Dollar Shave Club) that were then used to access a Dollar Shave Club online account, which allows someone to view the information in an account, including name, address, and the last four digits of the payment card on file (if you’ve provided that information). Based on ts investigation, Dollar Shave Club has no reason to believe that any Dollar Shave Club additional systems, accounts, personal information or financial information were affected. [source] | |
Dominion Resources Inc. had a data breach in 2014, in Virginia. Personal information of more than 1,700 people at Dominion Resources Inc. were compromised when unauthorized parties hacked the employee wellness plan. The hacker gained access via a subcontractor's system, StayWell Health Management LLC who runs Dominions "Well on Your Way" program which includes a health screening, to gain the information hacked.The hacking actually occurred at a vendor Stay Well uses, Onsite Health Diagnostics, based in Irvine, Texas, that provideds the sign-up mechanism for "Well on Your Way's" health-screening appointments. The information included individuals' names, addresses, email addresses, phone numbers, gender and dates of birth of employees, spouses and domestic partners who went online to schedul a health-screening appointment going back to 2012. "Dominion Resources said the company was notified of the breach on June 24 but didn't learn the identities of those affected until July 7th. Dominion Resources is investigating why it took so long for the company to be notified. They are no longer using Onsite Health Diagnostics for scheduling". [source] | Doral Corporation had a data breach in 2018, in Wisconsin. The Doral Corporation experienced a phishing attack that resulted in the exposure of 335 records. Exposed records included social security numbers in combination with first and last names. [source] | |
doTerra had a data breach in 2016, in Utah. doTerra notified customers of a data breach when a third party data provider that their system was accessed by an unauthorized party. The information included names, Social Security numbers, other government issued i.d. numbers, payment card information, dates of birth, postal and email addresses, telephone numbers, and usernames and passwords. [source] | DRB Systems LLC had a data breach in 2017, in Ohio. Credit/debit card info were breached via payment card system . [source] | |
Driscoll's, Inc. had a data breach in 2017, in California. Home address and ssn were breached. [source] | Dungarees had a data breach in 2015, in Missouri. Dungarees has notified individuals of a data breach when they discovered their online store was hacked. The hacking may have been compromised both debit and credit card numbers. The hacking may have compromised customer names, billing information, mailing information email addresses, credit and debit card information, the expiration dated, the CVV on the back of the card. [source] | |
Dungarees had a data breach in 2015, in Oregon. Dungarees notified customers of a breach to their system when they discovered an illegal hack that may have compromised customer credit card or debit card information. Based on the investigation the company believes that information provided with orders placed on their website between March 26, 2015 and June 5, 2015 was compromised. The information compromised included names, billing information, address, email addresses, credit or debit card number, the card expiration number and the CVV codes on the back of the card. The company is providing those affected with identity theft protection through ID Experts. Those affected can call -866-833-7917 to speak to a representative. = [source] | Dunn and Bradstreet had a data breach in 2017, in New York. Millions of records from a commercial corporate database have been leaked. The database, about 52 gigabytes in size, contains just under 33.7 million unique email addresses and other contact information from employees of thousands of companies, representing a large portion of the US corporate population. Dun & Bradstreet, a business services giant, confirmed that it owns the database, which it acquired as part of a 2015 deal to buy NetProspex for $125 million.The purchased database contains dozens of fields, some including personal information such as names, job titles and functions, work email addresses, and phone numbers. Other information includes more generic corporate and publicly sourced data, such as believed office location, the number of employees in the business unit, and other descriptions of the kind of industry the company falls into, such as advertising, legal, media and broadcasting, and telecoms. [source] | |
DXC Technology had a data breach in 2017, in Indiana. Medicaid members may receive a letter about a possible data breach involving personal information.DXC Technology, the fiscal agent for the Indiana Health Coverage Program (IHCP), says an internet hyperlink containing patient information was accessible between February and May of this year, according to The Indy Channel.The information included patient’s names, Medicaid ID numbers, names and addresses of healthcare providers, patient numbers, procedure codes, dates of service, and payment amounts.No financial information, social security numbers or patient addresses were released.The Family and Social Services Administration and DXC do not believe any patient information was stolen, but letters are being sent out as a precaution.If you were affected, you will be receiving a letter from the company responsible for maintaining the state’s Medicaid software, along with a year of free credit monitoring, according to 44 News. [source] | Dyn had a data breach in 2016, in New Hampshire. [source] | |
Eastern Alliance Insurance Group had a data breach in 2014, in Alabama. [source] | Eastern Bank had a data breach in 2016, in Massachusetts. It was an electronic breach affecting credit/debit cards as reported by the department of Consumer Affairs and Business Regulation the state of Massachusetts. [source] | |
easybreathe.com had a data breach in 2017, in California. On February 10, 2017, we learned that an unknown individual may have accessed your credit or debit card information used to make purchases at our online store. We immediately took action to secure our system and commenced an investigation to determine what information may have been accessed. We determined that the unknown individual may have accessed customer payment card information, including name, address, telephone number, and credit/debit card information. None of your health information (for example, social security number, insurance member ID number, etc.) was present or at risk.More Information: https://oag.ca.gov/ecrime/databreach/reports/sb24-67162 [source] | Eddie Bauer had a data breach in 2016, in Washington. [source] | |
Eileen Fisher had a data breach in 2016, in New York. Our records show that you made a purchase on eileenfisher.com between Wednesday, September 7 – Monday, October 24, 2016. In late October, we were informed of a possible data security incident that affected our website during that time.We immediately began investigating the situation and are working diligently with a leading forensics firm to explore the issue. At this time, we believe that malicious code was added to our website which allowed unauthorized individuals to capture certain information during the checkout process. We have removed that malicious code and excluded the unauthorized individuals from our website.More information: https://oag.ca.gov/ecrime/databreach/reports/sb24-64832 [source] | Electronic Data Systems had a data breach in 2007, in Alabama. A former employee was arrested this week for allegedly trafficking in stolen identities she received through her work with the company. She obtained the names and identifying information of 498 Alabama Medicaid recipients and subsequently sold 50 of those identities. [source] | |
Elex (mobile game Clash of Kings) had a data breach in 2016, in Beijing. [source] | ELightBulbs.com had a data breach in 2014, in Minnesota. Elightbulbs.com is in a series of companies who have had security breaches due to exposure of ColdFusion weaknesses. The online company was contacted by Discover card alerting them to a pattern of fraudulent activity on cards that were recently used at their store. This is a similar incident to what happened with Smucker's. ELightbulbs.com was listed in the ColdFusion botnet panel. The Vice President of the company, Paul McLellan said "he first learned of the breach on November 7, 2013 from his company's processor, Heartland Payment Systems". He also stated that "shortly before we were told by Heartland, we paid $6,000 a year for a company to brutalize our server, for protection and peace of mind. Turns out this flaw had existed for two years and they never saw it."The FBI has stated that group responsible for the attack have also compromised much higher-profile targets as well. [source] | |
EmblemHealth had a data breach in 2016, in New York. [source] | Emcor Services Mesa Energy Systems had a data breach in 2014, in California. [source] | |
eMinor Incorporated d/b/a ReverbNation had a data breach in 2015, in North Carolina. [source] | Employer Leasing Company had a data breach in 2017, in California. Name or other personal identifier in combination with SSN and Driver's license number or non-driver ID number for one Maine citizen breached. [source] | |
Epsilon Data Management LLC had a data breach in 2014, in Texas. [source] | Equifax Corporation had a data breach in 2017, in Georgia. Equifax, which supplies credit information and other information services, said Thursday that a data breach could have potentially affected 143 million consumers in the United States.Equifax said it discovered the breach on July 29. Criminals exploited a U.S. website application vulnerability to gain access to certain files, the company said.Equifax said exposed data includes names, birth dates, Social Security numbers, addresses and some driver's license numbers, all of which the company aims to protect for its customers.The company added that 209,000 U.S. credit card numbers were obtained, in addition to certain dispute documents with personal identifying information for approximately 182,000 U.S. consumers.Link to Equifax breach notification: https://www.equifaxsecurity2017.com/ UPDATE: (10/02/2017): Equifax said hackers may have stolen the personal information of 2.5 million more U.S. consumers than it initially estimated, bringing the total to 145.5 million.The company said the additional customers were not victims of a new attack but rather victims who the company had not counted before. [source] | |
Evans Hotels had a data breach in 2015, in California. Evans Hotels has notified customers of a breach of backup card readers used to encrypt payment card data. The hotel chain kept the card readers as backup for IT disaster recovery. These back-up readers were being used in conjunction with their current system for check-in with large groups. For those with questions they can call 888-738-3786 Monday through Friday between 9:00 a.m and 9:00 p.mMore Information: http://oag.ca.gov/ecrime/databreach/reports/sb24-56969 [source] | Evony Gaming Company had a data breach in 2016, in Delaware. In June 2016, the official website of Evony gaming suffered a massive data breach in which 33,407,472 of its registered user accounts were stolen. Things couldn't go worse when in August 2016, the gaming site suffered another data breach on its forum in which 938,000 of its registered accounts were stolen. The information compromised included usernames, email addresses, passwords and IP addresses. [source] | |
Excellus Blue Cross Blue Shield had a data breach in 2015, in New York. Excellus has revealed that in August the company discovered a breach to their system that may have started two years prior by hackers, gaining access to its customers' information.The information accessed included names, birth dates, Social Security numbers, mailing addresses, telephone numbers, claims and financial payment information, which included some credit card numbers. "Excellus spokesperson Cane confirmed in a phone call with WIRED that between 10 and 10.5 million customers had their data potentially accessed in the breach. Beyond just Excellus itself, the company says that even some of its insurance partners within the Blue Cross Blue Shield network may be affected, accounting for about 3.5 million of those victims. Everyone affected will receive a letter from Excellus, along with two years of free credit monitoring from the company." [source] | Express Scripts had a data breach in 2008, in Missouri. Express Scripts has received a letter demanding money from the company under the threat of exposing records of millions of patients. The letter, included personal information on 75 people covered by Express Scripts, including birth dates, Social security numbers and prescription information. Express manages prescription benefits for roughly 50 million people. UPDATE 10/1/09: Express Scripts notified about 700,000 consumers that their records may have been breached. [source] | |
Facebook, inc. had a data breach in 2018, in California. The information was breached via Network Server. [source] | Fallon Community Health Plan had a data breach in 2008, in Massachusetts. A vendor computer containing personal information on patients of Fallon Community Health Plan has been stolen. the data included names, dates of birth, some diagnostic information and medical ID numbers. Some of which may be based on Social Security numbers. [source] | |
Farm to Feet had a data breach in 2015, in North Carolina. Name, address, phone number, account number, account value, dob, and investment products were breached. [source] | Farmgirl Flowers, Inc. had a data breach in 2018, in California. Fashion Figure is notifying customers of a data breach to their system when they discovered unauthorized access to names, customer ID's, addresses, phone numbers, email addresses, and credit card information. After investigation, the company found malware installed on their webserver. The company is providing ID Experts for free for one year for those who were affected. For those with questions call 1-877-868-0171 Monday through Friday from 8:00 am-8:00 pm CST. More information: https://oag.ca.gov/ecrime/databreach/reports/sb24-58851 [source] | |
Fashion Figure (B. Lane, Inc.) had a data breach in 2015, in New York. Fashion Figure is notifying customers of a data breach to their system when they discovered unauthorized access to names, customer ID's, addresses, phone numbers, email addresses, and credit card information. After investigation, the company found malware installed on their webserver. The company is providing ID Experts for free for one year for those who were affected. For those with questions call 1-877-868-0171 Monday through Friday from 8:00 am-8:00 pm CST. More information: https://oag.ca.gov/ecrime/databreach/reports/sb24-58851 [source] | FDIC had a data breach in 2016, in District Of Columbia. The information was breached via Website. [source] | |
FedEx had a data breach in 2017, in Tennessee. [source] | Fidelity Investments had a data breach in 2017, in Massachusetts. Fidelity National Financial, Inc (FNF) informed customers of a breach to their system due to a targeted phishing attack to certain employees.FNF is the parent company of Ticor Title Company of Oregon, Ticor Title of Nevada, Inc., Lawyers Title Company, and Lawyers Title of Oregon, LLC, which provides title insurance and real estate settlement services in Oregon, Nevada, and/or California. From April 14, 2014 and April 16, 2014 a certain number of employees were targeted in a phishing attack that allowed the hackers to obtain username and password information for employees of the company. The company hosts their email with a third party vendor and after investigating did not find any evidence that the hackers were able to breach FNF's internal network or systems. However, the investigation did reveal that personal information was obtained including Social Security numbers, bank account numbers, credit/debit card numbers and driver's license numbers. [source] | |
First Transit, FirstGroup America had a data breach in 2011, in Ohio. A flash drive with First Transit applicant personal information was lost on a bus on January 21. Applicant names, Social Security numbers, addresses, dates of birth and possibly other employment information such as conviction record and drug test results may have been on the flash drive. [source] | Flagship had a data breach in 2017, in California. [source] | |
Flewelling & Mitton PC had a data breach in 2015, in Colorado. Flewelling & Mitton PC notified individuals of a data breach when their offices were broken into the morning of December 11, 2015. The individual broke the locks on several file cabinets that contained customer information.The information compromised included names and Social Security numbers. They stated that the only thing stolen was petty cash.More Information: https://www.oag.state.md.us/idtheft/Breach%20Notices/2015/itu-262309.pdf [source] | Flexible Benefit Service Corporation had a data breach in 2017, in Illinois. Flexible Benefit Service Corporation suffered a breach which affected 19438 records, including Medical Information and SSN. [source] | |
Flinn Scientific, Inc. had a data breach in 2014, in Illinois. Flinn Scientific, an ecommerce site focused on scientific materials for teachers and students, notified customers of a data breach to their online payment system when a cyber attacker inserted malware to gain access to the server that hosts payment information. The information breached includes payment card numbers, card verification codes, expiration dates, names, addresses, and email addresses.The company has set up credit monitoring with AllClearID for 12 months for those individuals affected by the breach. For questions individuals can call 1-866-979-2595 to get credit monitoring started. [source] | Fontainebleau Miami Beach had a data breach in 2018, in Florida. Fontainebleau Miami Beach suffered a data breach affecting 158 records which included both Credit card and debit card information. [source] | |
Forbes.com had a data breach in 2014, in New York. Forbes.com announced on their Facebook page February 14th, that they had been a target of a data breach by hackers. They claim that "the email address for anyone registered with Forbes.com has been exposed Please be wary of emails that purport to come from Forbes, as the list of email addresses may be used in phishing attacks. The passwords were encrypted, but as a precaution, we will strongly encourage Forbes.com readers to change their passwords on our system once we make sign-on available again". [source] | Forever 21 had a data breach in 2017, in California. Over the past several years we have seen a multitude of security problems plague major retail stores around the world. Breaches have come in many forms and have frequently targeted credit card information, though in some cases personal data has been part of the haul.Now we find ourselves looking at yet another incident. Retail chain Forever 21, which is wildly popular among young people in the United States -- you can barely find a mall that doesn't have one -- has officially announced that its systems were compromised.The extent of the damage is not fully known as of yet. The company posted a brief statement on its website to warn its customers. It seems to downplay the breach to a certain extent, claiming it boosted security back in 2015, but that some stores hadn't yet been brought up to speed. This resulted in point-of-sale attacks at certain locations. The investigation is focusing on transactions between March and October of this year. [source] | |
Forever21 had a data breach in 2017, in California. [source] | FourSquare had a data breach in 2016, in California. The data breach notification LeakedSource has revealed that the web design platform Weebly and FourSquare, a local search-and-discovery service mobile app suffered a data breach. As a result, 43,430,316 Weebly and 22,534,984 FourSquare users accounts were stolen.The NewYork-based company FourSquare suffered a security breach in December 2013 in which 22,534,984 user accounts were stolen however FourSquare has denied that it was hacked and claims that email addresses were simply cross-referenced with publicly available data from FourSquare. The data includes usernames, emails and Twitter and Facebook IDs. [source] | |
Fred's Inc. had a data breach in 2015, in Tennessee. Name, address, credit card number, cvv, expiration date, and in some cases email address and account password (if the customer elected to create an account) were breached. [source] | Freedom Management Group, LLC dba The Natural had a data breach in 2014, in New York. The information was breached via Network Server. [source] | |
Freeman had a data breach in 2014, in Texas. [source] | Fresenius Medical Care Holdings Inc., Fresenius Medical Care North America (FMCNA) had a data breach in 2007, in Massachusetts. A laptop was stolen from the locked car of an employee on December 13 while it was parked outside of a restaurant. The laptop contained patient names, dates of birth, dates of service and insurance information. [source] | |
Freshology had a data breach in 2014, in California. Name, address, payment card info were breached. [source] | FriendFinder had a data breach in 2016, in California. [source] | |
Fuzzy's Taco ShopAbi had a data breach in 2016, in Texas. The information was breached via Desktop Computer. [source] | Game Stop had a data breach in 2017, in Texas. GameStop recently identified and addressed a security incident that may have involved your payment card information. We are providing this notice to inform you of the incident and to call your attention to some steps you can take to protect yourself. At GameStop, we value our customers and understand the importance of protecting customer personal information. We sincerely apologize for any inconvenience or concern this incident may cause.What HappenedAfter receiving a report that data from payment cards used on www.GameStop.com may have been obtained by unauthorized individuals, we immediately began and investigation and hired a leading cybersecurity firm to assist us. Although the investigation did not identify evidence of unauthorized access to payment card data, we determined on April 18, 2017 that the potential for that to have occurred existed for certain transactions. [source] | |
Geekface LLC had a data breach in 2014, in Connecticut. Geekface LLC, which runs the online sites Hatchwise.com and eLogoContest.com notified customers of a data breach to their server that compromised personal information.The information breached included names, addresses, birth dates, usernames, passwords, and Social Security numbers.[source] | Genentech Inc. had a data breach in 2011, in California. An unauthorized person may have gained access to Genentechs list of personal information for patients who used Genentech assistance to pay for their drugs. The breach was discovered on August 17. Names, Social Security numbers, addresses, phone numbers, dates of birth, email addresses, drivers licence numbers, medical information, and health insurance information may have been exposed. [source] | |
Gingerbread Shed Corporation had a data breach in 2014, in Arizona. Gingerbread Shed Corporation notified customers of unauthorized access to their system that compromised the personal data of its customers. The information included names, addresses, phone numbers, email addresses, credit card information, user names and passwords for website accounts. [source] | GlamGlow had a data breach in 2015, in California. GlamGlow notified customers of a data breach when their online ecommerce site was compromised. The information accessed occurred between September 19 and September 21, 2014 and May 12 and May 15, 2015 and included names, addresses, telephone numbers, payment card numbers, expiration dates, security codes, email addresses and GlamGlow account passwords. For those affected with questions call 1-800-219-2031 between 9:30 am and 4:30 pm EST. [source] | |
GNAC had a data breach in 2017, in Missouri. On September 21, 2017, our system monitoring tools identified unusual activity relating to a database within our network that is tied to a web application used by customers. We disabled the web application and immediately launched an investigation to determine the nature and scope of this activity. A leading third-party forensic investigation firm was retained to assist with our own internal investigation. Although the investigation is ongoing, we determined on October 6, 2017 that there was evidence a small amount of data left our system between June 18, 2017 and September 19, 2017. [source] | Godiva Chocolatier Inc. had a data breach in 2014, in New York. Godiva notified employees of the company of a data breach when a Human Resources employee, who was traveling to retail sites, had a briefcase stolen from a car. The briefcase contained a lap top that had employee information on it. The lap top was not encrypted.The information included names, addresses, Social Security numbers and drivers license numbers.The company is providing Experian ProtectMyID Alert for 12 months for free. For questions call 1-866-328-1993 Monday through Friday 6:00 a.m to 6:00 p.m Pacific time. [source] | |
Golden 1 Credit Union had a data breach in 2015, in California. Golden State Credit Union notified members of a data breach when a credit union employee viewed member accounts without authorization. The information viewed included names, Social Security numbers, driver's license numbers and additional financial information. The credit union is providing Credit Watch through Equifax to those affected for 12 months at no cost. Those affected must apply by April 15, 2016. [source] | Golden 1 Credit Union had a data breach in 2018, in California. [source] | |
Goldman Sachs had a data breach in 2014, in New York. Name and credit card info were breached. [source] | Goodwill Industries International Inc. had a data breach in 2014, in Maryland. Financial institutions are tracking what appears to be fraudulent activity at numerous Goodwill retail stores. The fraudulent activity involves credit card breaches and that the compromised credit cards appear to have started at Goodwill stores across the country. The credit card information is then showing up at other retail establishments, similar to the breaches that occurred at Target, Neiman Marcus, P.F. Changs, etc."Goodwill Industries International was contacted last Friday afternoon by a payment card industry fraud investigative unit and federal authorities informing us that select U.S. store locations may have been the victims of possible theft of payment card numbers," the company wrote in an email. "Investigators are currently reviewing available information," the statement continued. "At this point, no breach has been confirmed but an investigation is underway. Goodwills across the country take the data of consumers seriously and their community well-being is our number one concern. Goodwill Industries International is working with industry contacts and the federal authorities on the investigation. We will remain appraised of the situation and will work proactively with any individual local Goodwill involved taking appropriate actions if a data compromise is uncovered."Goodwill Industries stated they learned of the potential breach on July 18th and is working with federal investigators to determine if the breach is legitimate and if legitimate. how many stores were affected. UPDATE (9/10/2014): Goodwill Industries announced that the data breach they suffered is linked to a third party vendor. "Goodwill said a forensic investigation had found that a third-party vendor's systems had been attacked by malware, providing the attackers with access to the credit card data of several of that vendor's customers intermittently between February 10, 2013 and August 14, 2014".According to Goodwill, 330 Goodwill stores in 20 states were affected. Forbes reported that 868,000 individuals were affected.[source] | |
GoToMyPC had a data breach in 2016, in California. [source] | Graphik Dimensions, Ltd. (pictureframes.com) had a data breach in 2016, in North Carolina. On or around November 9, 2016, Graphik Dimensions was advised that it had been identified as a common point of purchase for credit card fraud. On or around November 29, 2016, Graphik Dimensions’ investigation confirmed that an unidentified third party had injected malicious code into the pictureframes.com e-commerce site. The malicious code enabled the unidentified third party to acquire credit card information while the purchase took place. Graphik Dimensions’ investigation revealed that the exploit existed between July 12, 2016 and November 30, 2016. The specific information that may have been obtained by the unidentified third party included customers’ name, billing address, full credit card number, expiration date, CVV number, and user name and password. Graphik Dimensions removed the malicious code from the affected system, and continues to take steps to ensure the security of its systems. It worked with the investigators, along with other subject matter experts, to ensure the security of its customers’ data and to implement a remediation plan to improve security in Graphik Dimensions’ network. [source] | |
Grill Parts.com had a data breach in 2015, in California. Grillparts.com notified customers of a data breach to their website from January 2014 through October 2014. The information compromised included first and last names, addresses, personal card account numbers, expiration dates, and credit/debit card security codes. It is currently unknown or has not been reported as to the number of people who were affected.The company is providing the services of Kroll identity theft protection for one year at no cost to those who might have been affected by the breach. Visit kroll.idMonitoringService.com and follow the online instructions to take advantage of the Identity Theft Protection Services. You will need to enter the membership ID provided by the company sent in a letter to those whose information has been or could have been compromised. [source] | ground (ctrl) had a data breach in 2014, in California. Ground(ctrl) operates social networking community websites focused on musicians, informed customers of a data breach to their website. The information breached included e-mail addresses and passwords. The company did inform customers that their credit card information was never stored with them and was not at risk. [source] | |
Gyft had a data breach in 2016, in California. Gyft notified customers of a data breach when they discovered unauthorized access to two cloud providers used by the company contained personal information of customers.The information compromised included names, addresses, dates of birth, phone numbers, email addresses, and gift card numbers. Gift cards may have been used to make purchases on their site. The dates of the breach were March 19, 2015 and December 4, 2015.For additional information on the breach go to www.myidcare.com/gyft. [source] | Hampton Jitney and Ambassador Riders had a data breach in 2017, in New York. [source] | |
Harbortouch had a data breach in 2015, in Pennsylvania. Harbortouch, a POS vendor, announced a breach of several of the companies restaurant and bar customers. Patrons to the restaurants and/or bars were notified that their payment cards may have been compromised when malicious software was found on the POS systems. [source] | Harmony Information Systems had a data breach in 2008, in Wisconsin. A computer program housing personal information about Wisconsin seniors and disabled people had a significant security hole. A senior center volunteer in McFarland said he could see hundreds of files of peoples private information from across the country in the system run by Virginia-based Harmony Information systems. The information is entered into an electronic record that includes the persons name and Social Security number. [source] | |
Hawaii Medical Service Association (HMSA) had a data breach in 2016, in Hawaii. HMSA notified 10,800 members of a data breach when letters communicating care management went to the wrong addresses.The information compromised included patient names, management of certain health conditions and steps individuals could take to identify or treat an ailment. [source] | HDIS, Inc. had a data breach in 2015, in Missouri. On behalf of our client, HDIS, Inc. (the Company), a supplier of incontinence related products, we write to advise you of an incident involving the unauthorized introduction of maiware onto the shopping cart program used on the Company's website, www.hdis.com. This malware resulted in the possible compromise of personal information of Company customers residing in Maryland. Based upon the Company's investigation, the malware was present from November 27, 2015 to November 30, 2015 and potentially exposed certain personal information of seven residents that was inputted by those customers during the online checkout process. The personal information that was potentially affected by the incident includes: customer name, address, credit or debit card number, payment card expiration date and the card's CVV security number. The Company does not collect customers' social security or driver's license numbers during the online checkout process and that data was in no way affected by the incident. [source] | |
Health Care Service Corporation (HCSC) had a data breach in 2011, in Illinois. The theft of paper records on or around June 28, 2011 resulted in the exposure of patient information. [source] | Health Net Inc., International Business Machines (IBM) had a data breach in 2011, in California. [source] | |
Health Net had a data breach in 2008, in California. The information was breached via Network Server. [source] | Health Net had a data breach in 2010, in California. Customer information was sent to the wrong agent. The format of the information is unknown. The information included names and Medicare numbers. [source] | |
Healthcare.gov had a data breach in 2014, in District Of Columbia. The information was breached via Desktop Computer, Laptop, and Other Portable Electronic Device. [source] | HealthEquity had a data breach in 2016, in Utah. Health Equity notified individuals of a data breach when an employee inadvertently sent an email on December 11, 2015 containing personal information to another employer the company conducts business with.The information compromised included Social Security numbers.The company is providing identity monitoring services through Kroll for one year for free. [source] | |
HealthNow New York had a data breach in 2008, in New York. Clients may be at risk for identity theft, after a former employees laptop computer went missing with confidential information several months ago. The potential information includes names, dates of birth, Social Security numbers, addresses, employer group names, and health insurance identifier numbers. [source] | HealthSpring Inc. had a data breach in 2008, in Tennessee. A laptop computer containing personal information of about 450 state residents was stolen. The laptop, believed to contain names, dates of birth and Social Security numbers of about 9,000 individuals, was stolen from a HealthSpring employees locked car. [source] | |
Heartland Automotive/Jiffy Lube had a data breach in 2014, in Texas. [source] | HEI Hotels & Resorts had a data breach in 2016, in Connecticut. Name, credit/debit card info were breached. [source] | |
Hickory Grove Gas Station had a data breach in 2014, in Ohio. A local area gas station in Vincent Ohio off of Ohio 339 has a credit card breach and those affected are customers who recently used either debit or credit cards at the gas station. So far 100 people have reported fraudulent charges on their account that dates back to at least a month ago. Reports are saying that the number could go as high as 300 victims.It appears hackers infiltrated the network that gas station and grocery store uses. The breach could have also potentially happened through the Kentucky-based credit card processing company they use. They have stopped accepting any credit or debit cards until a full investigation is completed.Those who think they have been victimized are asked to call the Vincent Ohio Sheriffs Department. [source] | Highmark Insurance had a data breach in 2010, in Pennsylvania. Highmark notified 3,700 members that documents containing their names, policy identification and Social Security numbers were missing. This is the second such data spill involving the regioní£s dominant health insurer in four months. In January, the company mailed a premium billing statement to Boscoví£s Department Store, a client in Reading, according to Highmark. The envelope arrived damaged and torn; pages were also missing. The pages included the names and other identifying information for 3,700 members. [source] | |
Hilton Hotels had a data breach in 2015, in Virginia. [source] | Hi-Tec Sports USA, Inc. had a data breach in 2016, in California. Hi-Tec received reports from several customers of fraudulent charges appearing on their payment cards shortly after they were used to make a purchase on our Magnum Boots online order page. Hi-Tec immediately began working with the company that developed and maintains its websites. On March 11, 2016, the web developer reported that it had identified unauthorized code that had been inserted into the program that operates its order completion page. Hi-Tec began an analysis to determine when the code was inserted and its functionality. While that analysis was being conducted, Hi-Tec stopped accepting payment cards on its site and engaged a leading computer security investigation firm to assist in the investigation.The information compromised included names, email addresses, phone numbers, payment card numbers, expiration dates and security codes (CVV codes). Orders placed between January 24, 2016 to March 11, 2016 on their Magnum Boots and Hi-Tec websites may have been affected. [source] | |
Hobe & Lucas Certified Public Accountants, Inc. had a data breach in 2017, in Ohio. The information was breached via Desktop Computer. [source] | Hogan Services Inc. had a data breach in 2012, in Missouri. An email or emails with sensitive health information related to a health care premium plan was mistakenly emailed to or accessed by unauthorized people. The incident occurred or was discovered sometime around March 30, 2012. The incident was posted on the HHS website on June 8. [source] | |
Holly A. Nordhues had a data breach in 2015, in California. [source] | Horizon Blue Cross Blue Shield had a data breach in 2008, in New Jersey. More than 300,000 members names, social Security numbers and other personal information were contained on a laptop computer that was stolen. The laptop was being taken home by an employee who regularly works with member data. [source] | |
Horizon Healthcare Services Inc. doing business as Horizon Blue Cross Blue Shield of New Jersey and its affiliates had a data breach in 2016, in New Jersey. The information was breached via Paper/Films . [source] | Horizon Healthcare Services, Inc., doing business as Horizon Blue Cross Blue Shield of New Jersey, and its affiliates had a data breach in 2014, in New Jersey. The information was breached via Laptop . [source] | |
HSBC Bank USA, National Association had a data breach in 2016, in New York. [source] | HSBC Finance Corporation had a data breach in 2015, in Florida. HSBC notified customers of a data breach when customer mortgage information was inadvertently exposed via the Internet, which included personal information. The personal information included names, Social Security numbers, account numbers and old account information. [source] | |
Humana had a data breach in 2015, in Wisconsin. [source] | Humana Inc, Matrix Imaging had a data breach in 2010, in Kentucky. The information was breached via Paper/Films. [source] | |
Humana had a data breach in 2006, in Kentucky. Personal information of humana customers enrolled in the companys Medicare prescription drug plans could have been compromised when an insurance company employee called up the data through a hotel computer and then failed to delete the file. [source] | Humana had a data breach in 2010, in Kentucky. A former employee pleaded guilty to illegally accessing and using patient information in order to support his drug habit. The employee worked in Humanas information technology department. He also agreed to help address internal security flaws. [source] | |
HumanGood had a data breach in 2017, in California. [source] | Hutton Hotel had a data breach in 2016, in Tennessee. The Hutton Hotel has sent an alert to cutomers about a possible data breach.This is pretty unsettling news for the tens of thousands of people who have stayed at the hotel over this nearly four-year period.The hotel is calling this a payment card security incident. It's basically a breach of payment processing system and they say it could have affected guests who stayed there between Sept. 19, 2012, and April 16, 2015.This also affects anyone who made food and beverage purchases at the hotel from Sept. 19, 2012, to Jan. 15, 2015, and Aug. 12, 2015, to June 10, 2016.The release doesn't say if fraudulent charges have shown up on anyone's credit cards, but with nearly 250 rooms on the property, there are tens of thousands of credit cards that may have had information stolen.The hotel is asking past guests to keep an eye on their statements and report any fraudulent charges to their bank. [source] | |
Hyatt Hotels had a data breach in 2016, in Illinois. Multinational hotel corporation Hyatt recently alerted its customer of a credit card breach at some of its hotels – the second major incident of its kind in two years.The corporation said that its cyber security team discovered evidence of unauthorized access to payment card information from cards manually entered or swiped at the front desk of 41 of its hotels in locations such as Hawaii (three locations breached), Guam (1), Puerto Rico (1), and China (18, the highest number of breaches reported), between March 18 and July 02, 2017. [source] | I Love Kick Boxing (ILKB LLC) had a data breach in 2017, in New York. Name and payment card info were breached. [source] | |
IATSE Local 134 had a data breach in 2016, in California. IA 134 notified individuals of a data breach when a laptop that belonged to the organization was connected to a network at Levi's Stadium was hacked compromising personal information.Individual Social Security numbers may have been compromised. [source] | Illinois Board of Elections had a data breach in 2016, in Illinois. Hackers have breached databases for election systems in Illinois and Arizona, according to state election systems in Illinois and Arizona, according to state election and law enforcement officials.In Illinois, hackers accessed a database for the Illinois Board of Elections, compromising up to 200,000 personal voter records according to Ken Menzel, General Counsel for the board.The information compromised included names, addresses, sex and birthdays, plus voter's social security number or drivers' license numbers. The database that was compromised had information going back 10 years and most likely included outdated information which was never purged. [source] | |
Imgur had a data breach in 2014, in California. [source] | Infowars/ Prison Planet TV had a data breach in 2016, in Texas. Tens of thousands of subscriber accounts for media company Infowars are being traded in the digital underground.Infowars, created by famed radio host and conspiracy theorist Alex Jones, produces radio, documentaries and written pieces. The dumped data relates to Prison Planet TV, which gives paying subscribers access to a variety of Infowars content. The data includes email addresses, usernames, and poorly hashed passwords.The administrator of breach notification site Databases.Land provided a copy of 100,223 records to Motherboard for verification purposes. Vigilante.PW, another breach notification service, also has the Infowars dump listed on its site, and says the data comes from 2014. However, every record appears to have been included twice in the data, making the actual number of user accounts closer to 50,000.More Information: http://motherboard.vice.com/read/infowars-accounts-hacked-prison-planet-... [source] | |
Ingenix had a data breach in 2011, in Minnesota. A search of health care providers on the Ingenix website revealed that Social Security numbers were sometimes attached to the names of providers as ID numbers. It appears that some health plans or preferred providers had listed the Social Security numbers as ID numbers. People searching for providers covered by their plans would have seen the numbers. Some health care providers may have had their Social Security numbers used as ID numbers for five years. At least 142 New Hampshire residents were affected, but the number of affected individuals nationwide was not revealed. [source] | Inland Empire Health Plan/Children's Eyewear Sight had a data breach in 2014, in California. Inland Empire Health Plan notified customers of a data breach when a desktop computer and other items were stolen from Children's Eyewear Sight. The police were able to apprehend the individual who perpetrated the theft. The files on the computer included names, dates of birth, genders, addresses, contact phone numbers, email addresses, IEHP Member ID number, dates of appointments, dates of purchases, and the names of doctors who provided services. [source] | |
Inogen, Inc. had a data breach in 2018, in California. [source] | Instagram had a data breach in 2017, in California. [source] | |
Insurance Co. of the West (ICW) had a data breach in 2013, in California. Confidential medical records were found under a freeway by a concerned citizen.A local news team investigationtraced the documents back to the insurance claims processor ICW.ICW reported thatthe issue occurred on February 28 when a bin with files broke open on the way to a disposal site. An unnamed document destruction company responsible for the documents was replaced.Names, dates of birth, Social Security numbers, and other sensitive and medical information were on the documents. [source] | InterContinental Hotels Group (IHG) had a data breach in 2016, in Buckinghamshire. IHG values the relationship we have with our guests and understands the importance of protecting payment card data. On Dec. 28, 2016, IHG reported it was conducting an investigation after receiving a report of unauthorized charges occurring on some payment cards that were used at a small number of U.S. hotel properties. IHG hired leading cyber security firms to examine the payment card processing systems for the hotels that it manages in the Americas region. Based on the investigation, IHG is providing notification to guests who used their payment card at restaurants and bars of 12 company managed properties during the time periods from August 2016 – December 2016 identified below. An investigation of other properties in the Americas region is ongoing.Findings show that malware was installed on servers that processed payment cards used at restaurants and bars of 12 IHG managed properties. Cards used at the front desk of these properties were not affected. The malware searched for track data (cardholder name, card number, expiration date, and internal verification code) read from the magnetic stripe of a payment card as it was being routed through the affected server.= [source] | |
Internal Revenue Service had a data breach in 2015, in District Of Columbia. A previous story that was broken by Brian Krebs, Krebs On Security, regarding fradulent tax returns being filed by identity thieves who gained the information using data directly from the IRS website, was confirmed today by the IRS Commissioner Josh Koskinen.Mr. Koskinen confirmed that the identity thieves pulled data off of the IRS website to file fraudulent tax returns on unsuspecting individuals. The IRS became suspicious due to a large increase of individuals requesting their tax transcripts. The investigation revealed that approximately 200,000 suspicious attempts occurred and 100,000 of those were successful in being authenticated through the IRS website. [source] | Internal Revenue Service had a data breach in 2016, in District Of Columbia. The IRS revealed on Tuesday that it discovered and stopped an automated cyberattack on its e-filing personal identification number (PIN) system last month. According to the IRS, the cybercriminals used information stolen "elsewhere outside the IRS" to generate e-file PINs for stolen Social Security numbers (SSNs). E-file PINs are used by some taxpayers to electronically file their tax returns. Although no personal taxpayer data were compromised or disclosed by the breach, the IRS noted that the cybercriminals succeeded in using 101,000 SSNs to access e-file PINs (out of 464,000 attempts).The IRS is notifying individuals and placing markers on their tax accounts to try and catch any fraudulent tax returns being filed. More information: http://www.journalofaccountancy.com/news/2016/feb/irs-data-breach-expose... [source] | |
Intex Recreation Corp. had a data breach in 2017, in California. [source] | Intuit Inc. had a data breach in 2018, in California. Intuit, Inc. suffered a data breach that affected 31 records, which included both Driver's License and SSN data. [source] | |
J.P Morgan Chase had a data breach in 2014, in New York. The FBI is investigating a sophisticated hacking attack on JP Morgan Chase and potentially seven other financial institutions. Originally it was reported that possibly one to four other institutions may have been affected, but it appears that the breach could be much larger than originally thought.The hackers, who are reportedly Russian, gained enough personal information to completely wipe out bank accounts. The sophisticated and coordinated attacks go beyond the typical criminal hacker (s) according to authorities. Investigators are looking into the reasons behind the coordinated attack. It appears that not only did the hackers gain access to the accounts, but also altered and possibly deleted information.The attack appears to have been coordinated and directed at specific JP Morgan Chase employees to gain access to their computers and databases at the bank.Experts are communicating that the hackers would have had to of spent a significant amount of time researching and studying the record system of the bank prior to attempting any kind of unauthorized access. "What was even more concerning is these hackers were able to modify records using high-level credentials and do it in a way that was undetected." [source] | Jack Anthony Industries, Inc. had a data breach in 2017, in California. The information was breached via Email. [source] | |
JB Autosports.com had a data breach in 2016, in Iowa. [source] | JB Autosports had a data breach in 2016, in Iowa. JB Autosports, Inc. notified customers of a data breach when the system their check out page was the target of a cyberattack. The cyberattack affected customers who used their credit cards to pay for purchases from the companies website.The information compromised included names, addresses, credit card numbers, credit card expiration dates, CID numbers, CAV2 numbers, CVC2 numbers and CVV2 numbers. [source] | |
JCM Partners LLC had a data breach in 2014, in Georgia. JCM Partners informed customers of a data breach that occured when a file containing personal information of housing applicants was taken from a JCM database and posted on an unauthorized website. An internal investigation was launched.The information in the file included Social Security numbers, driver's license numbers, email addresses and mailing addresses. [source] | JoFit had a data breach in 2017, in Pennsylvania. [source] | |
Juniper Network had a data breach in 2015, in California. Juniper Networks, a computer network company, disclosed late last week that they suffered a major breach. The attack may have compromised the encrypted communications of many of their enterprise customers, including the U.S. government. Juniper Networks officials confirmed that hackers installed a "back door" on their computer equipment to gain access to the private communications of their customers. The company reports that "unauthorized code" was inserted in ScreenOS software that "could allow a knowledgeable attacker to gain administrative access." USA Today reports, "The rogue code could potentially compromise the whole system and decrypt VPN devices, without leaving a trace of the party behind the breach." [source] | Kaiser Foundation Health Plan of the Mid-Atlantic States, Inc. had a data breach in 2015, in Maryland. Kaiser Foundation Health Plan of the Mid-Atlantic States, Inc. notified patients of a data breach when a printing error patients received appointment reminders containing other patients health information. the breach affected 630 individuals. The information compromised included names, medical record numbers, types of appointments to be scheduled, and providers' names and departments. [source] | |
Kaiser Foundation Health Plan, Inc. had a data breach in 2017. [source] | Kaiser Foundation Hospital had a data breach in 2016, in California. The information was breached via Network Server. [source] | |
Kaiser Permanente Colorado-- Skyline and Southwest offices had a data breach in 2006, in Colorado. A laptop was stolen from the personal car of a Kaiser employee in California on Oct. 4. It contained names, Kaiser ID number, date of birth, gender, and physician information. The data did not include SSNs. [source] | Kaiser Permanente Health Plan, Inc of Northern California had a data breach in 2016, in California. The information was breached via Network Server . [source] | |
Kaiser Permanente Northern California Office had a data breach in 2006, in California. A laptop was stolen containing names, phone numbers, and the Kaiser number for each HMO member. The data file did not include SSNs. The data was being used to market Hearing Aid Services to Health Plan members. [source] | Kaiser Permanente had a data breach in 2005, in California. A disgruntled employee posted information on her blog noting that Kaiser Permanente included private patient information on systems diagrams posted on the Web. uPDATE (6/21/2005): The California Department of Managed health Care fined Kaiser $200,000 for exposing the confidential health information. [source] | |
Kaiser had a data breach in 2017, in California. [source] | Kardashian Website had a data breach in 2015, in California. The Kardashian brand recently launched a new website design which appears to have some security holes. One developer discovered a misconfiguration in the site that allowed him to access full names and emails of over 600,000 users who signed up for Kylie Jenner's website.This developer stated "I’ll admit I downloaded Kylie’s app just to check it out. I also checked out the website, and just like most developers, I decided to take a look around to see what was powering the site. After I started digging a little bit deeper, I found a JavaScript file namedkylie.min.75c4ceae105ad8689f88270895e77cb0_gz.js. Just for fun, I decided to un-minify this file to see what kind of data they were collecting from users and other metrics they may be tracking. I saw several calls to an API, which of course made sense. I popped one of those endpoints into my browser, and got an error just liked I expected."The developer then logged in with his own username and password and was "directed to a web page that contained the first and last names and email addresses of the 663,270 people who had signed up for the site." [source] | |
Keenan and Associates had a data breach in 2015, in California. Keenan and Associates, a third party administrator of health insurance benefits, notified individuals of a data breach when one of their vendors inadvertently exposed personal information when a security setting was not configured correctly on their portal system, potentially exposing the information.The information compromised included names, addresses, telephone numbers, birth dates, medical plan names, plan identifiers and Social Security numbers. The company is providing 24 months free of theft protection through Kroll. [source] | KeyPoint Government Solutions had a data breach in 2014, in Virginia. KeyPoint Government Solutions notified over 48,000 individuals of a data breach when their computer network was hacked. KeyPoint Solutions was hired by the Office of Personnel Management to take over the background checking process for the agency, when the agency did not renew the contract of USIS who suffered a breach earlier in the year. [source] | |
Keystone Mercy Health Plan and AmeriHealth Mercy Health Plan had a data breach in 2010, in Pennsylvania. A flash drive with patient information was lost or stolen on or around September 20. Patient names, addresses, and personal health information were on the drive. Seven patients had their full Social Security numbers exposed and 801 had the last four digits of their Social Security numbers exposed. As of October 21, the two companies had released very little information about the breach.UPDATE (1/29/11): The final total of patients affected appears to be 808 rather than 280,000. [source] | Kichlerlightinglights.com had a data breach in 2014, in New York. KichlerLightingLights is another victim of the ColdFusion botnet. The company's owner Gary Fitterman stated "It was like being attacked by terrorists. When we learned what had happened, we immediately went into frenzy, spent a ton of money to get forensic experts to take a look." The hacking gang used vunerabilities in Adobe's ColdFusion to build a botnet of hacked ecommerce sites, designed to bilk the customers credit card data, KichlerLightingLights was just another one of the ecommerce sites affected.The various companies that have been affected all handled credit card processing on their site. Mr. Fitterman has now outsourced all of his credit card processing transactions to a third party company.Experts state that if you run your own credit card processing you must be diligent about software updates. [source] | |
Kickstarter had a data breach in 2014, in New York. [source] | Kicky Pants, Inc. had a data breach in 2016, in Washington. Kicky Pants (previously spelled KicKee Pants) notified customers of a data breach when the company discovered unauthorized access into their system. The breach occurred between September 24, 2015 and December 26, 2015.The information compromised included firs and last names, credit card numbers, expiration dates, security codes on the back of cards, billing address, telephone numbers and email addresses. [source] | |
Kimpton Hotels had a data breach in 2016, in California. [source] | Kingston Residence of Hickory, LLC had a data breach in 2018, in North Carolina. A clerical mistake lead to including 2 separate 1099's in one envelope resulting in the unauthorized disclosure of 1099 information to other vendors [source] | |
KontrolFreek, LLC had a data breach in 2016, in Georgia. [source] | KURU Footwear had a data breach in 2014, in Utah. [source] | |
L.A Care Health Plan had a data breach in 2014, in California. [source] | L.A. Care Health Plan had a data breach in 2012, in California. A mailing error caused ID cards to be mailed to the wrong members. The cards were mailed on September 17, 2012 and the problem was discovered on September 18, 2012. Names, member ID numbers, and dates of birth were exposed. [source] | |
La Jolla Group had a data breach in 2014, in California. Name, address, phone number, email address, credit card info were breached. [source] | Laborers Funds Administrative Office of Northern California, Inc. had a data breach in 2016, in California. On February 17, 2016, the covered entity (CE), Laborers Funds Administrative Office of Northern California, Inc, discovered that a tax sent to its clients and beneficiaries inadvertently contained protected health information (PHI) about unrelated individuals. The breach affected approximately 800 individuals and included names, social security numbers, and eligibility information. The CE provided breach notification to HHS, affected individuals, and the media. In response to the breach, the CE implemented new technical safeguards for creating and transmitting this type of data, conducted a new/updated security analysis, revised its HIPAA policies and procedures, and trained its workforce. The CE also provided OCR with additional documentation including its HIPAA Notice of Privacy Practices Policy, as relevant to this breach investigation. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | |
Lamps Plus had a data breach in 2016, in California. Lamps Plus notified employees of a data breach when a phishing email sent to an employee that posed as an executive of the company asking for employee W-2 information. The information compromised included names, Social Security numbers, addresses and unfortunately this compromised information was used to file fraudulent tax returns.More Information: http://oag.ca.gov/ecrime/databreach/reports/sb24-60670UPDATE (4/4/2016): "Lamps Plus is facing a proposed class action lawsuit over allegations that the company failed to provide adequate security measures to prevent a recent massive data hack into the company’s payroll system, putting more than 1,300 employees’ sensitive information at risk."Information regarding the lawsuit is as follows: "The Lamps Plus Employee Data Breach Class Action Lawsuit is Frank Varela, et al. v. Lamps Plus Inc., et al., Case No. 5:16-cv-00577, in the U.S. District Court for the Central District of California, Eastern Division – Riverside." [source] | Landry's had a data breach in 2015, in Texas. [source] | |
Las Vegas Sands Hotels and Casinos had a data breach in 2014, in Nevada. The information was breached via Network Server. [source] | Lasko Group, Inc. had a data breach in 2014, in Pennsylvania. [source] | |
LastPass had a data breach in 2015, in Virginia. LastPass notified customers of a data breach when they discovered suspicious activity on their network. The company has communicated that "In our investigation, we have found no evidence that encrypted user vault data was taken, nor that LastPass user accounts were accessed. The investigation has shown, however, that LastPass account email addresses, password reminders, server per user salts, and authentication hashes were compromised."The company is requiring that "all users who are logging in from a new device or IP address first verify their account by email, unless you have multifactor authentication enabled. As an added precaution, we will also be prompting users to update their master password." [source] | Lawrence Memorial Hospital, Mid Continent Credit Servies, Inc. (Blue Sky Credit), BrickWire LLC had a data breach in 2011, in Kansas. A breach of a website hosted by BrickWire LLC resulted in the exposure of patient names, phone numbers, email addresses, health care providers, payment amounts, dates of payment, credit card information and checking account information. Lawrence Memorial Hospitals vendor Blue Sky Credit used BrickWire LLC for the online bill-pay service offered to Lawrence Memorials patients. The personal and financial information of patients who paid through the website was accidentally made available on the Internet between September 20, 2011 and October 28, 2011. UDPATE (11/17/2011): It appears that BrickWire left a portal open that contained payment records from 28 LMG patients after doing a system upgrade on September 20. However, the information of every patient who used the online bill pay system between 2005 and September of 2011 was available in a database that was accessible through the portal. [source] | |
Legal Sea Foods had a data breach in 2014, in Massachusetts. Legal Sea Foods informed customers of a data breach that occured on June 5, 2014 that a segment of their mail order web sales and e-commerce environment, that an unauthorized person gained access to a server that contained information from mail order web customer transactions. After an investigation, transactions made between Jaunary 1, 2014 and May 21, 2014 were potentially affected, which included transactions used with credit cards. Names, credit card numbers, card expiratin dates, and card verification values may have been breached. The company has informed their payment processing company of the breach and the processor has been working with the credit card companies to provide them the card numbers of those affected. [source] | Liberty Tax Services had a data breach in 2015, in California. Liberty Tax Services contacted customers to inform them of a data breach due to a burglary. The thieves took some files and electronic records that included personal information of their customers.The information included names, addresses, dates of birth, identification numbers, Social Security numbers, income documents and names of dependents, their dates of births, and their Social Security numbers. [source] | |
Lime Crime had a data breach in 2015, in New York. Lime Crime, an online cosmetics company notified customers of an unauthorized access to their website server which resulted in malware being installed. This malware allowed customer data to be captured, including credit card payment information. The information compromised included names, addresses, card account numbers, expiration dates, security codes and Lime Crime website usernames and passwords. The malware affected customers who purchased items on the website from October 4, 2014 through February 15, 2015. For those customers that used PayPal to purchase items, their Lime Crime website usernames and passwords may have also been compromised. [source] | Lincoln Financial Securities Corporation, Red Boat Advisor Resources had a data breach in 2012, in New Hampshire. A server that held TIFF images of customer financial applications was accessed by an unauthorized party between January and early April of 2012. Customers who applied for brokerage accounts, life insurance and annuities, and provided other financial applications may have had their names, Social Security numbers, addresses, email addresses, government issued identification numbers, and financial account information exposed. Named beneficiaries and other family members may have also had their information exposed. [source] | |
LinkedIn had a data breach in 2016, in California. A recent incident involving LinkedIn, the business-oriented social networking service, is showing that data breaches can cause big problems for companies and consumers — even years after the breaches take place. On May 17, 2016, LinkedIn discovered that information stolen in a 2012 incident was being made available online, and notified site users immediately the next day about what happened and what they were doing to fix it. In 2012, an alleged 117 million email and password combinations were stolen by hackers. At the time, LinkedIn issued a mandatory password reset for any accounts they thought were compromised; all LinkedIn members were encouraged to change their passwords as well, just in case. [source] | LiveGlam, Inc. had a data breach in 2017, in California. [source] | |
Lokai had a data breach in 2014, in New York. Lokai informed customers of a data breach to their system from July 18, 2014 to October 28, 2014 by hackers who gained access to their server that hosts their website. The hackers installed a program that was designed to record information entered by customers. The information affected included names, addresses, payment card information, expiration dates, verification codes, and user name and passwords. [source] | Lone Star Circle of Care had a data breach in 2015, in Texas. Lone Star Circle of Care notified individuals of a data breach after the discovery of a back-up file containing containing names, addresses, phone numbers, and birth dates was accidentally posted on their website for view. [source] | |
Lord & Taylor's, Saks had a data breach in 2018, in New Jersey. Hackers have stolen the personal and financial information of customers who shop at Lord and Taylor and Saks Fifth Avenue in the latest of a string of data breaches in recent years.Records for more than five million credit and debit cards used at all the chains’ North American locations were compromised, according to Gemini Advisory, a cybersecurity firm. Most were obtained from stores in New York and New Jersey, Gemini said. [source] | Lowes Corporation had a data breach in 2014, in North Carolina. Lowes Corporation had to issue a data breach notice to current and former drivers for the company due to a security breach with one of the third party vendors they use.Information breached included including names, addresses, birthdays, Social Security numbers, driver's license numbers, and other driving record information with a company called E-DriverFile, an online database provided by SafetyFirst, a driver safety firm headquartered in New Jersey. The third party vendor unintentionally backed up the data to an unsecure server that was accessible via the Internet. The information may have been exposed from July 2014 through April 2014 before it was discovered.[source] | |
Lucky Pet had a data breach in 2016, in Washington. Lucky Pet notified customers of a data breach when an unauthorized individual (s) accessed the company's third party shopping cart software compromising customers personal information.The information compromised consisted of names, addresses, and credit card information including expiration dates and security codes. More Information: http://oag.ca.gov/ecrime/databreach/reports/sb24-61371 [source] | Lulu's Fashion Lounge, Inc. had a data breach in 2016, in California. On August 23, 2016, we discovered that our payment card processing system may have been accessed without our authorization. We immediately launched a full investigation, including working with a third-party digital forensic investigator. We determined that the unauthorized access occurred intermittently between August 11 and August 16, 2016, and only affected customers entering a payment card new to our system.The information compromised included names, addresses, payment card number which includes the security code and expiration date. [source] | |
LYFE Kitchen Notice of Data Breach had a data breach in 2017, in Tennessee. [source] | M&M Automotive Group, Inc. (Volkswagen of Oakland) had a data breach in 2015, in California. Volkswagen of Oakland notified customers of a data breach when the dealership was broken into and boxes of files were stolen. The company stated that "We believe that some of the stolen boxes held sold vechicles jackets. Each sold vehicle jacket typically contains copies of the forms signed by the vehicle purchaser including the name, address, phone number, driver's licens information, bank account information, car insurance information and information on the vehicle purchased. In some cases where financing is provided in connection with the purchase of a vehicle, the deal jacket will also contain a copy of the consumer's credit application, credit report, pay stubs, job information and references. [source] | |
Make-up Designory had a data breach in 2018, in California. According to the data breach notification form sent to the Indiana Office of Attorney General, "Each January our client is required to send a tax document (1098-T Statement) to students and graduates. The information for this form i s gathered by Its accounting office and securely transferred to a certified public accounting firm. The accounting firm works with a financial communications service provider that specializes in creating and mailing these and similar type tax forms to be sent by US mall. This year was no different, except an error occurred In the preparation of the mailing that cause three individual ta~documents to be placed In one envelope, As a result, some students received their own 1098-T Statements and Statements fur two other students. We are contacting all students affected by this Incident to notify them of the unintentional disclosure and requesting the return of all 1098-T Statements that were mailed in error. We will follow-up with such students to confirm that the Statements are returned to the school and/or destroyed." [source] | Mama Mio US had a data breach in 2015, in California. Mama Mio informed customers of a cyber-attack to their system where their personal information may have been compromised. According to the company, the attack happened on July 28, 2015. The information compromised included first names and surnames, emails, billing addresses and telephone numbers, card numbers, expiration dates, and the 3-digit security code on the back of the card. [source] | |
Mandarin Oriental had a data breach in 2015, in New York. The Mandarin Oriental Hotel Group has informed customers of a breach when malware was found on their credit card transaction systems. [source] | Marian Regional Medical Center had a data breach in 2014, in California. Marian Regional Medical Centers (Santa Maria and Arroyo Grande Campuses) notified patients of a data breach. A secured electronic file containing patients information was sent to a contracted health insurance plan in error. The health insurance plan notified the company immediately that they received the email in error. The file included names, addresses, types of insurance, dates of birth, dates of service, types of laboratory tests and test results for dates of service between March 1 and March 6, 2014. The company has stated that the Social Security number was not included in the electronic file. [source] | |
McDavid Inc had a data breach in 2017, in Illinois. The information was breached via Network Server. [source] | McDermott Will & Emery LLP is the plan sponsor for the McDermott medical plan had a data breach in 2015, in Illinois. The information was breached via Network Server . [source] | |
MDwise had a data breach in 2012, in Indiana. An upgrade of MDwises customer record computer system in February 2011 resulted in the leak of records from several organizations. Anyone searching by name could have accessed the information online. Members of Healthy Indiana Plan, Care Select, and Hoosier Healthwise may have had their names, addresses, Medicaid numbers, and doctors names and addresses exposed online. Administrators corrected the error as soon as it was detected. [source] | Medco Health Solutions, Inc. had a data breach in 2012, in New Jersey. [source] | |
Medica Health Plans had a data breach in 2005, in Minnesota. It was discovered that two employees had engaged in unauthorized activities for an extended period of time. The computer administrators were fired for sabotaging the companys computers and downloading data. Sensitive information for 1.2 million Medica members may have been accessed. The former employees prolonged their activities and avoided heavier punishment by hiding and destroying evidence of their activities. [source] | Medical Science & Computing, LLC had a data breach in 2018, in Maryland. Medical Science & Computing, LLC suffered a breach affecting 139 (paper) records, which included account numbers. [source] | |
MeetMe, Inc. had a data breach in 2014, in Pennsylvania. MeetMe, Inc. has announced a data breach of their system when hackers gained access to their customer information. The information included names, emails addresses, and passwords. The company reported that they have contacted their customers to change their usernames and passwords. [source] | Member First Mortgage, LLC had a data breach in 2017, in Michigan. [source] | |
Metropolitan Atlanta Rapid Transit Authority had a data breach in 2015, in Georgia. The Metropolitan Atlanta Rapid Transit Authority (MARTA), acting on behalf of its self-insured health plan, mailed 785 Voluntary Critical Illness Insurance forms to the incorrect employees. The correspondence contained protected health information (PHI) including names, addresses, social security numbers, and dates of birth. MARTA conducted a breach assessment and provided breach notification to HHS, affected individuals, and the media. In response to the incident, MARTA developed standard operating procedure for the Benefits Office for handling employees’ PHI and trained employees. Under the new procedures, the staff will not prepopulate employee forms, applications, worksheets, and confirmation statements with individually identifiable information nor will they send documents containing individually identifiable data to the internal print shop. OCR obtained assurances that MARTA implemented the corrective actions listed above. [source] | Microsoft xBox had a data breach in 2014, in Washington. Microsoft Xbox Live networks were hacked by a group called "LizardSquad", preventing users from playing games over the holiday. The assault was a DDoS attack (distributed denial-of-service) which "harness the Internet connectivity of many hacked or misconfigured systems so that those systems are forced to simultaneously flood target network with junk Internet traffic. The goal, of course, is to prevent legitimate visitors from being able to load the site or use the service under attack."More Information: http://krebsonsecurity.com/2014/12/cowards-attack-sony-playstation-micro... [source] | |
Microsoft/Xbox One had a data breach in 2015, in Washington. A 19 year hacker has pleaded guilty to hacking and stealing "11,266 log-in credentials from an unnamed which he then shared amongst the other members." Austin Alcala was part of a larger hacking network that stole software and data from gaming companies such as Microsoft, Valve, Epic. The group stole internal documents from companies, source code and games that had not yet been released to the public. The items stolen were stated to be worth approximately $100 million dollars. The hacking took place from 2012 to 2014. [source] | Mise En Place Restaurant Services, Inc. had a data breach in 2018, in California. Mise en Place Restaurant Services, Inc. experienced a ransomware attack on March 15, 2018. Information exposed may include names, addresses and social security numbers of Mise en Place cients, employees or investors of Mise En Place clients. [source] | |
Missing Link Networks Inc. had a data breach in 2015, in California. [source] | MMM Healthcare, Inc. had a data breach in 2011, in Puerto Rico. Names and financial information were leaked [source] | |
Molina Healthcare had a data breach in 2014, in California. [source] | Motivate International Inc. had a data breach in 2016, in New York. [source] | |
Mt. Gox- Worlds Largest Bitcoin Exchange had a data breach in 2014, in Tokyo. From a distance, the world's largest bitcoin exchange looked like a towering example of renegade entrepreneurism. But on the inside, according to some who were there, Mt. Gox was a messy combination of poor management, neglect, and raw inexperience.Its collapse into bankruptcy last week – and the disappearance of $460 million, apparently stolen by hackers, and another $27.4 million missing from its bank accounts – came as little surprise to people who had knowledge of the Tokyo-based company's inner workings. [source] | Muji USA had a data breach in 2015, in New Jersey. Muji USA notified customers of a data breach when they discovered malware on their online shopping portal which may have compromised their customers personal information.The information compromised included names, addresses, payment card numbers, the expiration dates of cards, the CVV code on the back of cards. [source] | |
Multnomah Athletic Club had a data breach in 2017, in Washington. The information was breached via Email. [source] | MyHeritage had a data breach in 2018. [source] | |
MySpace had a data breach in 2016, in California. The information was breached via Electronic Medical Record. [source] | National Wholesale Incorporated had a data breach in 2016, in North Carolina. Name, address, account number were breached. [source] | |
Nationstar Mortgage LLC had a data breach in 2015, in Texas. [source] | Native Canada Footwear had a data breach in 2017, in British Columbia. Native Shoes became aware of a potential vulnerability in the security of our website in late June 2017 immediately launched an investigation. That investigation has confirmed that malware may have infected the Native Shoes website as early as April 2015. [source] | |
Natural Grocers had a data breach in 2015, in Colorado. [source] | Navistar, Inc. had a data breach in 2018, in Illinois. A third-party vendor failed to follow instructed mailing folding protocols. As a result, personal information may have been visible through the envelope window of 1099 mailings, when only a name and address were meant to be seen. Records breached include SSN. [source] | |
NCO Financial Systems Inc. had a data breach in 2014, in Pennsylvania. NCO Financial Systems Inc. informed customers of a data breach when their third party communication vendor, RevSpring, Inc. sent an email to a number of loan customers that mistakenly included an attachment that contained loan statements. The information on these statements included names, addresses, Social Security numbers, and account numbers.The company is offering 12 months free of ProtectMyID through Experian. [source] | NECA/IBEW Family Medical Care Plan had a data breach in 2013, in Maryland. NECA/IBEM Family Medical Care Plan (FMCP) participants received disclosure documents related to benefits coverage and modifications. The outside of the envelopes in which the documents arrived displayed participant Social Security numbers. [source] | |
Neiman Marcus Group had a data breach in 2017, in Texas. On or about January 17, 2017, unauthorized individuals began attempting to access our InCircle, Neiman Marcus, Bergdorf Goodman, Last Call, CUSP, and Horchow websites (collectively the NMB websites) by trying various companies (not associated with NMG websites), in which user login names and passwords were stolen. The intruders were able to access customers' names, basic contact information, email addresses, purchase history, but only the last four digits of payment card numbers. For InCircle online accounts, the accessible information also included customers' gift card numbers and Circle Level. At present, all indications are that the InCircle and Neiman Marcus Group database of customer email addresses and passwords remains safe, and that our cyber defenses repelled the majority of the attacks.A similar automated login/password attack occurred on or about December 26, 2015 in which unauthorized individuals began attempting to access NMG websites' online accounts. At the time, the outside forensic experts we engaged to investigate this matter determined that the online intruders were able to view customers' names, basic contact information, email addresses, purchase history, and only the last four digits of the payment cards associated with the online accounts. Unfortunately, it has become clear that the intruders also had access to full payment card numbers and card expiration dates. [source] | Neiman Marcus had a data breach in 2014, in Texas. Neiman Marcus has notified individuals of a data breach when the company discovered unauthorized access to online accounts on or around December 26, 2015.The information compromised included usernames, passwords, names, mailing addresses, phone numbers, last four digits of payment card along with purchase histories. "The firm suspects the attacker obtained the login credentials from large breaches at other companies where login names and passwords were stolen in order to gain unauthorized access to other accounts where victims might use the same credentials. Rawlinson said, customers will be required to reset their passwords on all NMG websites the next time they log into their accounts." [source] | |
Neiman Marcus had a data breach in 2016, in Texas. Neiman Marcus has notified individuals of a data breach when the company discovered unauthorized access to online accounts on or around December 26, 2015.The information compromised included usernames, passwords, names, mailing addresses, phone numbers, last four digits of payment card along with purchase histories. "The firm suspects the attacker obtained the login credentials from large breaches at other companies where login names and passwords were stolen in order to gain unauthorized access to other accounts where victims might use the same credentials. Rawlinson said, customers will be required to reset their passwords on all NMG websites the next time they log into their accounts." [source] | New England Calendar and Novelty Company had a data breach in 2015, in New York. [source] | |
New Horizons Computer Learning Centers, Inc. had a data breach in 2015, in Texas. New Horizons Computer Learning Centers, Inc. notified business owners of a data breach when unauthorized access to employee and vendor information stored on the company network may have been compromised. The information included names and bank account information. For those with questions can call their confidential inquiry line at 1-866-979-2512 Monday through Saturday, 8:00 a.m - 8:00 p.m. Central Time. [source] | New Mexico Medicaid had a data breach in 2010, in New Mexico. A employee of a subcontractor for the company that processes claims and provides dental benefits for the Stateí£s Medicaid program, filed a stolen car report for a vehicle whose trunk contained an í£Œunencryptedí£Œ laptop loaded with patient information. The patient information in the laptop included name, health plan identification number, which in some cases is the individualí£s Social Security number, and a provider identification number but not the name of the provider. The agency sent out a message today saying that it was in the process of notifying 9,500 New Mexicans who use its Medicaid Salud plan of a possible security breach. [source] | |
Newkirk Products Inc. had a data breach in 2016, in New York. Personal information about members of two local health insurance companies has been breached in a data security incident involving an Albany firm.Newkirk Products Inc., an Albany company that prints identification cards for insurers, reported a cybersecurity incident that exposed information including names, mailing addresses and, in some cases, date of birth. Social Security numbers, medical information and financial account information was not breached.Newkirk makes insurance ID cards for Albany nonprofit insurer CDPHP and BlueShield of Northeastern New York, the Latham division of Buffalo's HealthNow New York Inc. More than half a million CDPHP members and 70,000 BlueShield members were affected by the data incident, according to the insurers.The data systems of the health insurers were not affected. [source] | NextBus had a data breach in 2015, in California. NextBus has notified customers of a data breach to their system that disclosed usernames, email addresses, telephone numbers and passwords of customers. The company is advising customers to change their passwords.More information: http://oag.ca.gov/ecrime/databreach/reports/sb24-58315 [source] | |
Nintendo of America Inc. had a data breach in 2016, in Washington. [source] | NLU Products, LLC had a data breach in 2016, in Utah. [source] | |
Noble House and Resorts had a data breach in 2015, in Washington. The Nobel House Hotels and Resorts notified customers of a data breach when guests informed them of unauthorized charges on their payment cards used at one of their hotels, The Commons.The company identified malware on the payment card system on September 25, 2015. The information compromised included cardholder name, card numbers, expired dates, and the CVV number on the back of the cards. The dates cards were potentially compromised were from January 28, 2015 to August 3, 2015. [source] | Noble House Hotels and Resorts (Noble House) had a data breach in 2016, in Washington. [source] | |
Noodles and Company had a data breach in 2016, in Michigan. [source] | North Shore Care Supply had a data breach in 2015, in Texas. North Shore Care Supply notified customers of a data breach when their online ecommerce site was compromised exposing customers' personal information.The information accessed included debit/credit card information, names, addresses, card numbers, verification codes and expiration dates.Online purchases made between June 7, 2015 and August 24, 2015 are at risk. The company has set up AllClearID for 12 months for free. Those affected can call 1-855-229-0069. [source] | |
Novozymes US, Inc. had a data breach in 2018, in California. On or about December 25, 2017, an unauthorized individual executed an email-based attack and gained access to certain emails from a Novozymes employee's email account. Some of the email potentially accessed included the personal information of North Carolina residents. Novozymes discovered the breach on January 11, 2018 and took immediate action to prevent further unauthorized access. Novozymes also promptly investigated the issue, engaged outside counsel, and is notifying affected individuals and offering them consumer protection services. Novozymes is reviewing its policies and procedures and evaluating additional safeguards to help prevent this type of incident in the future.Breached records include Account #, Driver's License, Passport, SSN. [source] | NVIDIA Corporation had a data breach in 2014, in California. NVIDIA Corporation suffered a data breach when hackers infiltrated their network and stole employee usernames and passwords. The company is requesting that those affected change their password and be cautious of "phishing" emails that look like they are coming from a colleague or friend requesting sensitive information. [source] | |
OANDA had a data breach in 2014, in New York. OANDA informed customers of an unauthorized breach affecting some of their clients. On Monday March 3, 2014 a historical log of some payments received via PayPal (prior to 2007) was accessed. The company states that the incident did not impact any fxTrade services, client trades or funds. The information accessed included named and email addresses. The company states that usernames or passwords for thier "fxPense" expense reporting tool may have been accessed. These accounts are not related to fxTrade. They are asking customers who registered for this service and use the same username and password on any other external websites, to change those passwords.Upon learning of the breach, the company shut down access to the system and alerted the FBI, their regulators and relevant privacy offices of the breach. [source] | O'Charley's Restaurant and Bar had a data breach in 2016, in Tennessee. O'Charley's Restaurant and Bar notified customers of data breach when a third party security firm discovered unauthorized access to their payment card system. Between March 19, 2016 and April 8, 2016 customers who used their debit or credit card information could be the target of identity theft. The information compromised included data found on the magnetic strip of the card which would include the cardholder names and card numbers. The following locations were potentially compromised. O'Charley's Restaurants locatd at 930 Windham Court, Boardman Ohio and 2077 Interchange Drive, Erie Pennsylvania. The number of debit/credit cards affected has not yet been released.[source] | |
Office of Personnel Management (OPM) had a data breach in 2015, in District Of Columbia. [source] | Ohio State University had a data breach in 2008, in Ohio. Ohio State University has notified 18,000 current and former students that their personel information was mistakenly stored on a computer server exposed to the Internet. The data included student names, Social Security numbers, addresses and coverage dates for those enrolled in the health insurance plan for three quarters in 2005-06. [source] | |
OneLogin had a data breach in 2017, in California. Password manager and single sign-on provider OneLogin has been hacked, the company has confirmed.In a brief blog post, the company's chief security officer Alvaro Hoyos said that it had detected unauthorized access to OneLogin data in our The blog post had no further information or technical details about the incident -- though, the post omitted that hackers had stolen sensitive customer data, which was only cursorily mentioned in an email to customers, seen by ZDNet.OneLogin believes that all customers served by our US data center are affected and customer data was potentially compromised, the email read.Hackers have the ability to decrypt encrypted data, says a support page, accessible only to OneLogin customers (a copy of the post was published online).The company has advised customers to change their passwords, generate new API keys for their services, and create new OAuth tokens -- used for logging into accounts -- as well as to create new security certificates. The company said that information stored in its Secure Notes feature, used by IT administrators to store sensitive network passwords, can be decrypted.But questions remain over how the hackers had access to data that could be decrypted in the first place. [source] | OnePlus had a data breach in 2017, in Guangdong. OnePlus has confirmed that up to 40,000 customers have been affected by a credit card breach, in the latest embarrassing misstep for the Chinese handset maker. The news comes several days after OnePlus shut down credit card processing following complaints from customers about fraudulent charges landing on their cards after they bought products through OnePlus’s online store.OnePlus offered an explanation of what had happened on its website."One of our systems was attacked, and a malicious script was injected into the payment page code to sniff out credit card info while it was being entered," the company said. "The malicious script operated intermittently, capturing and sending data directly from the user’s browser. It has since been eliminated. We have quarantined the infected server and reinforced all relevant system structures."The affected users entered their card information on OnePlus’s store between mid-November and January. Customers who made purchases with a saved card "should not" be affected, OnePlus said. The same goes for ones who paid with PayPal or credit card via PayPal. Affected users will be offered a year of credit monitoring. [source] | |
Onsite Health Diagnostics had a data breach in 2014, in Texas. [source] | Operating Engineers Local Union No. 3 had a data breach in 2017, in California. On or about February 9, 2017, OE3 learned that the security of user data stored on our website, www.oe3.org, had been breached. OE3 is not currently aware of the reason for the breach, but does not have any reason to believe that is was caused by intentional interference or a deliberate effort by any unauthorized person to misappropriate the data. OE3 immediately tested the website for malware and viruses, and found no traces of any. WHAT ARE DOING?After OE3 became aware of the breach, we promptly notified the website host, which shut down the website. We also contacted the web developer, who immediately corrected the issue on the website that caused the breach, and secured the data once again. Although the public portion of OE3's website is back up, we are suspending the members-only portion pending our investigation to determine the cause of the breach. We are also exploring additional security measures to assist us in preventing any future security breach. [source] | |
Optimum HealthCare Inc. had a data breach in 2012, in Florida. An Optimum HealthCare claims specialist stole the personal information of at least 32 clients. The documents information was later found on a man who was arrested after a traffic stop in 2011. The man who was arrested never worked for Optimum and the dishonest employee who stole the documents is believed to have separated from Optimum. [source] | OptumRx had a data breach in 2016, in Minnesota. The information was breached via Laptop. [source] | |
Oracle's MICROS Point-of-Sale had a data breach in 2016, in California. A Russian organized cybercrime group known for hacking into banks and retailers appears to have breached hundreds of computer systems at software giant Oracle Corp., KrebsOnSecurity has learned. More alarmingly, the attackers have compromised a customer support portal for companies using Oracle’s MICROS point-of-sale credit card payment systems.MICROS is among the top three point-of-sale vendors globally. Oracle’s MICROS division sells point-of-sale systems used at more than 330,000 cash registers worldwide. When Oracle bought MICROS in 2014, the company said MICROS’s systems were deployed at some 200,000+ food and beverage outlets, 100,000+ retail sites, and more than 30,000 hotels.The size and scope of the break-in is still being investigated, and it remains unclear when the attackers first gained access to Oracle’s systems. Sources close to the investigation say Oracle first considered the breach to be limited to a small number of computers and servers at the company’s retail division. That source said that soon after Oracle pushed new security tools to systems in the affected network investigators realized the intrusion impacted more than 700 infected systems.[source] | Orange County Employees Association had a data breach in 2015, in California. The Orange County Employees Association (OCEA) notified members of a data breach when they were a recent victim of a cyber attack. The attack affected OCEA members, certain non-members, OCEA Health & Welfare Trust participants, OCEA staff, customers of Velece Corporation and dependents.The information included names, addreses, dates of birth, Social Security numbers, driver's license numbers, payroll information, dental, vision, life and disability enrollment information, retirement status, information concerning dependents and usernames and passwords. OCEA is providing one year free credit monitoring and identity theft recover and restoration services. [source] | |
Orangeburg-Calhoun Technical College had a data breach in 2014, in South Carolina. Orangeburg-Calhoun Technical College in South Carolina is notifying 20,000 former and current students and faculty members that an unencrypted laptop computer stolen this month from a staff member's office contained their personal information.The information contained on the laptops included names, birth dates and Social Security numbers of individuals.The college stated that the information goes back 6 or 7 years and that they believe the thief was after the hardware, not the data stored on it. The college neglected to comment on whether or not they are providing credit monitoring services for those affected. [source] | Orbitz had a data breach in 2016, in Illinois. [source] | |
Oregon Educators Benefit Board had a data breach in 2014, in Maryland. Name, benefit number, address, dob, ssn, benefit plan selections, Names of dependents, were breached via Website. [source] | PageUp had a data breach in 2018. [source] | |
Palm Springs Federal Credit Union had a data breach in 2014, in California. On January 18, 2018, Palo Alto Unified School District learned that an employee was storing confidential parent information on his laptop. This same employee had a prior laptop stolen and based on this information, the District conducted an investigation to determine whether personal information was affected by the prior incident. The District's investigation determined that although the stolen laptop was password protected, confidential information may have been stored on the device, including the name, address, and Social Security number for seven (7) North Carolina residents. The District will begin notifying North Carolina residents by U.S. Mail in accordance with North Carolina law in substantially the same form as the document enclosed herewith. The District is also offering the affected individuals a complimentary one year membership in credit monitoring and identity theft protection services through Experian and has provided a dedicated phone number to answer any questions that individuals may have regarding the incident. [source] | Parkbytext had a data breach in 2017, in Dublin. Motorists who use the parkbytext service have been told of a potential breach to customer data by malicious software during a service outage.The mobile parking operator said it does not believe that any customer data was compromised but we cannot say this with 100% certainty at this stage, until further investigation is completed.The company said credit and debit card information along with customer passwords are encrypted and have not been compromised.However, the customer data that may have been compromised includes phone numbers, email addresses, home addresses and vehicle registrations. [source] | |
Paytime Inc. had a data breach in 2014, in Pennsylvania. The information was breached via Electronic Medical Record. [source] | Paytime had a data breach in 2014, in Pennsylvania. [source] | |
Peppermill Resort Spa & Casino had a data breach in 2015, in Nevada. The information was breached via Email. [source] | PetSmart, Inc. had a data breach in 2017, in Arizona. Petssmart suffered a breach affecting 1,434 records from 12/19/2017-12/26/2017. The breach was discovered on 12/22/2017 and notified the public on 1/10/2018 [source] | |
PF Chang's had a data breach in 2014, in Arizona. P.F Chang's is investigating a potential data breach, when credit cards showed up on an underground website that criminals use. Brian Krebs broke the story, when the banks he contacted confirmed that the cards had been used at P.F Chang's restaurants. P.F Chang's is investigating the allegations currently with authorities.UPDATE (06/30/2014): PF Chang's has had a class action lawsuit filed against the restaurant chain. The company confirmed on June 12, 2014 that a breach had occured. Some experts believe that the lawsuit is unlikely to succeed because some security experts have said, because proving consumer losses linked to the specific restaurant data breach is difficult to do.Some believe it was a breach of the restaurants POS system, most likely infiltrated by malware, similar to the Target and Salley Beauty breaches, the restaurant chain has yet to divulge any details, including the number of cards exposed. UPDATE (8/4/2014): "P.F Chang's China Bistro Ltd. stated Monday that the data breach that affected customer credit and debit cards affected 33 locations throughout the continental U.S.", the investigatin is still ongoing. [source] | Phoenix House Foundation Inc. had a data breach in 2015, in New York. On December 22, 2014, the Phoenix House discovered a data breach when their payroll system when a consultant they hired made unauthorized changes to their electronic payroll systems. The information accessed included names, addresses, Social Security numbers, salary information, and benefit information. The company has terminated the contracted with the consultant and contacted authorities. The company is offering a 12 month membership in Experian's ProtectMyID Alert for free for those affected. [source] | |
Piedmont Advantage Credit Union had a data breach in 2015, in North Carolina. [source] | Pizza Hut had a data breach in 2017, in Texas. If you kicked October off with a Pizza Hut pizza, you might want to keep a close eye on your credit report – and credit card statement.The chain has emailed some patrons alerting them their personal information might have been compromised after hackers gained access to its website and app.Roughly 60,000 customers are thought to have been impacted by the "third party security intrusion." Emails to customers said the hack occurred over a 28-hour period from the morning of Oct. 1 to midday Oct. 2.Among the data that might have been compromised are customer names, billing ZIP codes, delivery addresses, email addresses, and payment card information, such as account numbers, expiration dates and Card Verification Value numbers. [source] | |
PMC Medicare Choice had a data breach in 2011, in Puerto Rico. The March 8 theft of a computer resulted in the exposure of the protected health information of patients. [source] | PNI Digital Media had a data breach in 2015, in British Columbia. PNI Digital Media is investigating their online photo printing service that they either manage or host for a number of large retailers such as Costco, Walmart, Walgreens, CVS, Rite to name a few. The photo printing service has been taken off line while the company and their customers investigate the breach. The concern is that the hackers gained credit card information from customers of the retailers they service. [source] | |
Point Breeze Credit Union had a data breach in 2015, in Maryland. Names,SSN, credit card numbers and CVV code or expiration date, usernames and passwords were breached. [source] | Pool Supply Unlimited had a data breach in 2016, in California. On January 11, 2017 Pool Supply Unlimited learned that a third party computer server utilized for our website was hacked. In the last week poolsupplyunlimited.com has been held hostage by a group of hackers in Iran. Unfortunately, this specific group of hackers have been cuasing problems for American companies big ans small for years.We have been working closely with the FBI since the breach. It was only this morning that we learned the extent of the information stolen during the hack. [source] | |
Power Equipment Direct had a data breach in 2014, in Georgia. [source] | Praetorian Digital/ PoliceOne Forum had a data breach in 2017, in California. [source] | |
Precision Planting had a data breach in 2014, in Illinois. Precision Planting customers have been impacted by a security breach affecting one of the company's data servers. The company has not communicated specifically how their system was compromised, however the information breached included customer names, addresses, tax identification numbers and financial information. The server also contained some employee W-2 forms, Social Security numbers, and driver's license numbers. [source] | Premium Beat had a data breach in 2016, in Quebec. [source] | |
Prescription Advantage had a data breach in 2007, in Massachusetts. [source] | Private Internet Access had a data breach in 2015, in California. Customers of Private Internet Access were notified via email of a data breach when the company discovered a vulnerability to an IP address affecting the "port forwarding feature" of the service the company provided to customers. "On November 17, we were privately notified of an IP address leak vulnerability affecting the port forwarding feature of our service. Essentially, anyone connecting to a forwarded port on any of our VPN gateways could have their real IP address leaked to an attacker specifically targeting a PIA user. Within 12 hours of the initial report, we developed and tested what we thought was a complete fix, and deployed it to all of our VPN gateways. On November 26, the researchers who discovered the vulnerability made it public and we quickly noticed that our service was still vulnerable to the IP address leak in certain cases, despite our initial fix. After further investigation, we also realized there was a separate but related issue on our desktop client. To fix this issue we are releasing updated VPN apps to prevent any leaks. We released v.52 on November 27." [source] | |
Pro Sports Daily had a data breach in 2016, in Ontario. [source] | ProAssurance Mid-Continent Underwriters had a data breach in 2010, in Texas. Customer names, Social Security numbers, dates of birth, and addresses were exposed on the Per Diem Insurance web page. [source] | |
Project Management Institute had a data breach in 2016, in Pennsylvania. [source] | Prudential Financial Inc. had a data breach in 2006, in New Jersey. A health insurer claims data were erroneously faxed to a company in Canada by doctors and clinics across the U.S.. data included the patients Social Security numbers, bank account details and health care information. [source] | |
PumpUp, inc. had a data breach in 2018, in Ontario. The information was breached via Desktop Computer, Other, Other Portable Electronic Device, Paper/Films. [source] | Quench had a data breach in 2017, in Pennsylvania. [source] | |
R.E. Moulton had a data breach in 2008, in Texas. [source] | Rate My Professors had a data breach in 2016, in New York. [source] | |
Rea.deeming Beauty, Inc. /d/b/a/ beautyblender had a data breach in 2017, in Pennsylvania. The information was breached via Laptop. [source] | RealSelf had a data breach in 2016, in Washington. RealSelf.com notified customers of a data breach when they company noticed unauthorized access to their consumer data located on their servers. The information compromised included username, email address and passwords. [source] | |
Record Assist LLC had a data breach in 2014, in Texas. Name, address, website username, payment card info were breached. [source] | Recreational Equipment Inc. (REI) had a data breach in 2014, in Washington. On July 23, REI discovered that a third-party may have accessed REI customer accounts without authorization obtaining email addresses and passwords. [source] | |
Reeves International Inc/ Breyer Horses had a data breach in 2014, in New Jersey. Reeves International Inc. is informing customers of a data breach of one of their online retail sites called Breyer Horses (www.breyerhorses.com). On September 9, 2014 the company discovered an unauthorized party installed malware on the server hosting the Breyer Horse website, the malware compromised customers' personal data. The dates of the attack were from March 31, 2013 through October 6, 2014.The information compromised includes names, addresses, website usernames and passwords, payment card account numbers, card expiration dates, and payment card security codes. [source] | Regional Income Tax Agency had a data breach in 2016, in Ohio. The Regional Income Tax Agency announced Dec. 31 that nearly two months earlier it lost personal data for about 50,000 people who filed tax forms with the agency. A backup DVD with the information cannot be located, according to RITA. The agency says it will provide one-year of free credit monitoring to those affected. Nothing in our investigation indicates that the DVD was stolen, or that there has been any misuse of information, agency attorney Amy L. Arrighi said today. Our investigation to locate the missing DVD led us to the conclusion that it was most likely destroyed. [source] | |
Remote DBA Experts, LLC had a data breach in 2018, in Pennsylvania. [source] | RJL Insurance Services, LLC, RJL Wealth Management had a data breach in 2012, in California. RJL Insurance Services became aware of a vulnerability in its computer network that may have resulted in the exposure of some electronic files. The information was secured, but some RJL files were accessible for a period of two weeks in late September and early October of 2011. Client names, Social Security numbers, drivers license numbers, and medical conditions may have been exposed. [source] | |
Rob Kirby, CPA had a data breach in 2014, in California. Rob Kirby CPA notified customers of a data breach when the car he was driving was broken into and his briefcase, a password protected laptop and flash drive containing confidential client information was stolen.The information stolen included tax returns for current and previous years, copies of supporting documents associated with the returns, including names, addresses, birth dates, and Social Security numbers for clients, spouses, and dependents. [source] | Roberts Hawaii, Inc. had a data breach in 2017, in Hawaii. [source] | |
Rockland Nissan had a data breach in 2015. [source] | Rosen Hotels & Resorts had a data breach in 2016, in Florida. Guest name and payment card information (cardholder name, payment card number, exp date and security code) for 8 records breached. [source] | |
RR Donnelley, UnitedHealthcare, Boy Scouts of America had a data breach in 2013, in Illinois. An unencrypted desktop computer was stolen from an RR Donnelley facility sometime between mid September and the end of November, 2012. RR Donnelley is a vendor of UnitedHealthcare. It is unclear why the breach was not noticed until December 3, 2012. The stolen computer contained UnitedHealthcare member information that was related to participation in the Boy Scouts of America 2003 health benefit plan. Names, Social Security numbers, and addresses may have been exposed. [source] | Russian hacking discovered by Hold Security had a data breach in 2014, in Wisconsin. A gang of Russian hackers has amassed over 1 billion username and password combinations and more than 500 million email addresses, a security firm reported late Tuesday, calling it the largest-ever haul of stolen Internet credentials.The massive trove — stolen from hundreds of thousands of websites — was discovered by the Milwaukee firm Hold Security, according to a post on its website. [source] | |
RxAmerica and Accendo Insurance Company had a data breach in 2011, in Utah. Medicare Part D beneficiaries enrolled in Prescription Drug Plans may have had their information exposed. A formatting mistake made member names, ID numbers, drug names and dates of birth viewable through the envelope window of letters sent.UPDATE(7/27/2011): Current and former Molina Medicare, Healthy Advantage HMO SNP, and ChoicePartners Medicare HMO members were also affected.UPDATE (10/28/2011): An additional 1,378 Windsor Health Plan enrollees were affected as well. [source] | Sabre Corporation had a data breach in 2014, in Texas. Breaches involving major players in the hospitality industry continue to pile up. Today, travel industry giant Sabre Corp. disclosed what could be a significant breach of payment and customer data tied to bookings processed through a reservations system that serves more than 32,000 hotels and other lodging establishments.In a quarterly filing with the U.S. Securities and Exchange Commission (SEC) today, Southlake, Texas-based Sabre said it was "investigating an incident of unauthorized access to payment information contained in a subset of hotel reservations processed through our Hospitality Solutions SynXis Central Reservations system."According to Sabre’s marketing literature, more than 32,000 properties use Sabre’s SynXis reservations system, described as an inventory management Software-as-a-Service (SaaS) application that "enables hoteliers to support a multitude of rate, inventory and distribution strategies to achieve their business goals." [source] | |
Sabre Corporation had a data breach in 2017, in Texas. Breaches involving major players in the hospitality industry continue to pile up. Today, travel industry giant Sabre Corp. disclosed what could be a significant breach of payment and customer data tied to bookings processed through a reservations system that serves more than 32,000 hotels and other lodging establishments.In a quarterly filing with the U.S. Securities and Exchange Commission (SEC) today, Southlake, Texas-based Sabre said it was "investigating an incident of unauthorized access to payment information contained in a subset of hotel reservations processed through our Hospitality Solutions SynXis Central Reservations system."According to Sabre’s marketing literature, more than 32,000 properties use Sabre’s SynXis reservations system, described as an inventory management Software-as-a-Service (SaaS) application that "enables hoteliers to support a multitude of rate, inventory and distribution strategies to achieve their business goals."Sabre said it has engaged security forensics firm Mandiant to support its investigation, and that it has notified law enforcement."The unauthorized access has been shut off and there is no evidence of continued unauthorized activity," reads a brief statement that Sabre sent to affected properties today. "There is no reason to believe that any other Sabre systems beyond SynXis Central Reservations have been affected."Sabre’s software, data, mobile and distribution solutions are used by hundreds of airlines and thousands of hotel properties to manage critical operations, including passenger and guest reservations, revenue management, flight, network and crew management. Sabre also operates a leading global travel marketplace, which processes more than $110 billion of estimated travel spend annually by connecting travel buyers and suppliers. [source] | Sabre Corporation had a data breach in 2017, in Texas. Sabre Corporation is investigating a possible recent data breach that was brought to light by the announcement of the American Airlines breach. American Airlines uses the reservation software developed by the Sabre Corporation."Sabre said in a statement Friday, "We recently learned of a cybersecurity incident, and we are conducting an investigation into it now. At this time, we are not aware that this incident has compromised sensitive protected information, such as credit card data or personally identifiable information, but our investigation is ongoing." [source] | |
Safety First had a data breach in 2014, in New Jersey. SafetyFirst has come forward to announce a data breach of their E-DriverFile service. The company is connected to the announcement that Lowe's current and former employees were involved in a data loss."A new filing with the California Attorney General’s Office obtained today indicates that a server containing a wealth of information about client vehicle operators was unprotected and accessible via the Internet for a period that exceeded six months. SafetyFirst reported that the breach dated back to September 27, 2013. It was not discovered until April 2, 2014 according to those records".SafetyFirst unintentionally backed up data to an unsecured computer server that was accessible from the Internet. The information breached included Social Security numbers, and driver license numbers. [source] | Salem Five Cents Savings Bank had a data breach in 2016, in Massachusetts. It was an electronic breach affecting credit/debit cards as reported by the department of Consumer Affairs and Business Regulation the state of Massachusetts. [source] | |
Sally Beauty Supply had a data breach in 2014, in Texas. As reported by Krebs on Security, it appears that Sally Beauty Supply may be one of the latest victims of a string of credit card data breaches affecting their payment systems."On March 2, a fresh batch of 282,000 stolen credit and debit cards went on sale in a popular underground crime store. Three different banks contacted by KrebsOnSecurity made targeted purchases from this store, buying back cards they had previously issued to customers".The banks used a "common point of purchase" or "CPP" to determine where the cards were used over the same period of time. "Each bank independently reported that all of the cards (15 in total) had been used within the last ten days at Sally Beauty Supply locations across the United States". [source] | Sally Beauty Supply had a data breach in 2015, in Texas. [source] | |
San Antonio Shoemakers had a data breach in 2016. [source] | SAS Safety Corporation had a data breach in 2015, in California. On behalf of our client, SAS Safety Corporation (the Company), we write to advise you of an incident involving the unauthorized introduction of maiware onto the Company's website,www.sassafety.com. This malware resulted in the possible compromise of personal information of Company customers residing in Maryland. Based upon the Company's investigation, the maiware was present from September 23, 2015 to December 8, 2013 and potentially exposed certain personal information of three residents that was inputted by those customers. The personal information that was potentially affected by the incident includes: customer name, address, credit or debit card number, payment card expiration date and the card's CVV security number. Additionally, the customer's logon identification and password for the website may have been affected. The Company does not collect customers' social security or driver's license numbers and that data was in no way affected by the incident. [source] | |
Sausalito Yacht Club had a data breach in 2014, in California. The Sausalito Yacht Club notified its members of a data breach to their online member roster. The information on the roster included member names linked to private Sausalito Yacht Club member numbers. These two pieces of information together allows for the charging of beverages, goods, services and meals at the club. Additionally, members personal contact information, financial information, including accounts receivable information could have been obtained. Currently, the breach is under investigation and depending upon what is found, the club may issue new cards and account numbers. [source] | SCAN Health Plan had a data breach in 2016, in California. On June 27, 2016 we learned that contact sheets, which are documents kept in a system used for sales purposes, had been accessed and possibly viewed for unauthorized purposes. We immediately began an investigation and brought in outside experts. We determined the unauthorized access occurred between March and June of 2016. While there is no indication that the information in this system has been used fraudulently, we needed to let you know that your information was in this system.What Information Was Involved? The information on the contact sheets that were exposed included name, address, and phone number. For some people it also included date of birth and limited health notes, such as a doctor name, health condition, or medication name. For a small number of individuals it may have also included Social Security number. [source] | |
Schoolzilla had a data breach in 2017, in California. More than a million American students had their information exposed this month in a data breach at a California-based company that offers data services to kindergarten through 12-grade schools.A student data warehouse platform, Schoolzilla first acknowledged the breach on April 12 in a message on its website, informing customers: "A well-known computer security researcher was doing a targeted analysis of Schoolzilla when he uncovered a file configuration error."The researcher, Chris Vickery of the Kromtech Security Research Team, told the Daily Dot this week that he discovered the Schoolzilla breach in early April while scanning the web for an "all too common" misconfiguration in Amazon cloud storage devices (Amazon S3 buckets).The storage device discovered by Vickery included a database that contains the personal information of approximately 1.3 million students in the United States, including some Social Security numbers. The researcher was unable to provide the Dot with evidence of the breach because he deleted the database from his own computer shortly after realizing the leaked data pertained to minors."The sheer volume of private student data, including [test] scores and social security numbers for children, convinced me that it should be purged from my storage in an expedited fashion," Vickery said. [source] | Schwaab Inc. had a data breach in 2016, in Wisconsin. Schwaab, Inc. notified customers of a data breach when DiscountRubberStamps.com (a Schwaab owned company) discovered unauthorized access in their computer system from January 22, 2014 through February 8, 2016. The information compromised may have included credit card information. [source] | |
Schwab Retirement Plan Services, Inc. had a data breach in 2015, in California. Schwab Retirement Plan Services Inc. (SRPS), notified customers of a data breach when a spreadsheet containing Social Security numbers, names, addresses, dates of birth, dates of termination, employment status, division code, marital status and account balance was accidentally emailed to a participant in another retirement plan serviced by SRPS. [source] | Schwan's Home Service, Inc. had a data breach in 2016, in Minnesota. As a precaution, we want to make you aware that CARDSource, the third-party company that manufactured the cards for the Schwan’sPay™ program, has notified us ofa possible compromise of its data. Thankfully, this activity represents a low risk, and there has been no evidence that your Schwan’sPay card information has been misused in anyway. As part of CARDSource’s investigation, it was determined that the potentially compromised data included the names of some of our Schwan’sPay customers, along with their mailing addresses, email addresses , phone numbers and Schwan’sPay card numbers.CARDSource did not possess any other data for our Schwan’sPay card users. [source] | |
Scottrade had a data breach in 2015, in Missouri. [source] | Scripps Network LLC. (Food.com) had a data breach in 2015, in Tennessee. Food.com notified customers of a databreach to their system that may have affected emails, usernames and passwords. These credentials were used to login onto the site for managing their recipe box and posting recipes on the site. These same credentials are used to Foodnetwork.com website as well as mobile applications through the site. This intrusion occurred between August 8, 2015 and September 2, 2015. According to the company no financial information or Social Security information was compromised. The company is recommending that customers change their usernames and passwords. [source] | |
Sears Holding Company/K-Mart had a data breach in 2014, in Illinois. Sears Holding Corp announced Friday that a data breach occurred at their K-Mart stores starting last month, with malicious software targeting their Point of Sale systems that compromised customers' credit card information.Currently, Sears Holding Corp is not clear as to the number of affected customer cards and the breach is currently under investigation. K-Mart has said that they were able to remove the malware from their systems.K-Mart is working currently working with federal investigators. [source] | Sears Holdings Management Corporation had a data breach in 2017, in California. [source] | |
Sears had a data breach in 2017, in Illinois. Department store chain Sears Holding Corp (SHLD.O) and Delta Air Lines Inc (DAL.N) said on Wednesday some of their customer payment information may have been exposed in a cyber security breach at software service provider [ 24]7.ai.Department store chain Sears Holding Corp (SHLD.O) and Delta Air Lines Inc (DAL.N) said on Wednesday some of their customer payment information may have been exposed in a cyber security breach at software service provider [ 24]7.ai.A Delta Air Lines flight is pushed put of its gate at the airport in Salt Lake City, Utah, U.S., January 12, 2018. REUTERS/Mike BlakeSears said it was notified of the incident in mid-March and the incident led to unauthorized access to the credit card information of under 100,000 of its customers.Technology firm [ 24]7.ai, which provides online support services for Delta, Sears and Kmart among other companies, found that a cyber security incident affected online customer payment information of its clients, it said.The incident happened on or after Sept. 26, 2017 last year and was found and resolved on Oct. 12, the company said. [source] | Select Restaurants Inc. had a data breach in 2017, in Ohio. [source] | |
Sentry Insurance had a data breach in 2006, in Wisconsin. [source] | Service Systems Associates, Inc. had a data breach in 2015, in Colorado. The information was breached via Email. [source] | |
Service Systems Associates had a data breach in 2015, in Colorado. Service Systems Associates, who specifically services zoos, restaurants and various cultural centers across the US, has notified customers of a breach of its credit and debit card processing systems.""The violation occurred in the point of sale systems located in the gift shops of several of our clients," the company said in a written statement. "This means that if a guest used a credit or debit card in the gift shop at one of our partner facilities between March 23 and June 25, 2015, the information on that card may have been compromised." [source] | Sheet Metal Workers' Local Union No.104 had a data breach in 2016, in California. [source] | |
ShowTix4U had a data breach in 2017, in Nevada. ShowTix4U recently became aware of a potential security incident possibly affecting the personal information of certain individuals who made a payment card purchase on the ShowTix4U.com website. We are providing this notice as a precaution to inform potentially affected individuals about the incident and to call your attention to some steps you can take to help protect yourself. We sincerely regret any concern this may cause you. What Happened We were recently alerted by our payment card processor to a potential security incident involving our website. Based upon an ongoing forensic investigation, it appears that an unauthorized actor was able to gain access to our third-party vendor’s server and install malicious software on our website. The malicious software appears designed to capture payment card information as the information was inputted. What Information Was Involved We believe that the incident could have affected certain information (including name, address, email address, telephone number, payment card account number, expiration date, and card verification code) of individuals who made a purchase on the website between December 11, 2016, and February 2, 2017. According to our records, you made a payment card transaction on the website during that timeframe and your information may be affected. Please note that because we do not collect sensitive personal information like Social Security numbers, this type of sensitive information was not affected by this incident. [source] | Shutterfly/Tiny Prints/Treats/Wedding Divas had a data breach in 2014, in California. [source] | |
Signature Hardware had a data breach in 2017, in Kentucky. [source] | Silverpop Systems, Inc. Health and Welfare Plan had a data breach in 2011, in Georgia. A burglary that occurred on or around April 15, 2011 resulted in the theft of laptop with patient information. [source] | |
SilverPop had a data breach in 2011, in Georgia. A laptop that contained information related to SilverPops Health and Welfare Plan was stolen on April 15. Affected individuals may have had their protected health information exposed. [source] | Silversage Advisors had a data breach in 2014, in California. On February 20, 2014 Silversage Advisors notified customers of a theft of back-up computer drives from a secure offsite location used as part of the company's disaster recovery plan. The drives contained names, addresses, Social Security numbers, driver's license numbers and account information. The company is providing one year of Breach Protector credit monitoring and identity theft restoration coverage. For those affected with question they are to call 1-888-969-7500. [source] | |
Sisters of Charity of Leavenworth Health System Health Benefits Plan had a data breach in 2016, in Colorado. [source] | Smucker's had a data breach in 2014, in Ohio. Smucker's announced a data breach to their Online Store, stealing customer data that could have included customer names, addresses, email addresses, phone numbers, credit card or debit card numbers, expiration dates, and verification codes. The hackers utilized a sophisticated malware that steals information from Web server applications. This particular malware obtains form data submitted by visitors as customers entered the data for the online checkout process. These particular hackers look for weaknesses in either the end-users computer or weakensses in the Web server. If there is a weakenss in either one, that web session then becomes compromised and the hackers "suck down customer data post or pre-encryption (this all depends on whether the data was incoming or outgoing)".KrebsOnSecurity noted "when a reader first directed my attention to the Smucker's breach notice, I immediately recalled seeing the cmopany's name among a list of targets picked last year by a criminal hacking group that plundered sites running outdated, vulnerable versions of ColdFusion, a Web applicatoin platform made by Adobe Systems Inc". [source] | |
Snapchat had a data breach in 2014, in California. Snapchat has notified current and former employes of a phishing scam that targeted their payroll department that compromised employee information.The information compromised included names, Snapchat employee ID, Social Security numbers, state of residence and work, 2015 wages earned, including stock-option gains, costs of company paid benefits for life and health insurance, relocation reimbursements, employee contricutions to retirement, dependent care, and healthcare plans, additional required payments and taxes withheld. [source] | Snapchat had a data breach in 2016, in California. The hacker or group known as "Lightcontact" is claiming to have hacked Snapchat.com. Reportedly, the group published a database containing Snapchat user names and phone numbers and posted it to several public forums such as Reddit.com.UPDATE: Snapchat has announced a security update to their mobile image sharing services to include an opt out option to the Find Friends system. This update is said to prevent others from looking up their account information through address books. This update will allow a person to no longer appear if this type of search is initiated. According to security vendor AdaptivMobile, the compromised accounts are concentrated mostly in California and New York, with the two states accounting for nearly 2.3 million accounts. Other regions affected include Illinois, Colorado and Florida(1/4/2014) [source] | |
Snapsaved.com had a data breach in 2014, in California. Snapsaved.com, a third party vendor to Snapchat, announced that their servers were hacked, which in turn caused thousands of photos and videos from the third party service to show up on the Internet."On Sunday, thousands of photos and videos from the Snapchat service were put online, apparently taken from sites including Snapsaved.com, which had allowed people to log in using their Snapchat username and password to offer desktop-based rather than handset-based access to the site - and also the chance to store photos, which are meant to be deleted within seconds of being viewed."Snapsaved posted on Facebook the following:"I would like to inform the public that snapsaved.com was hacked" due to a mistake in the setup of its web server. "As soon as we discovered the breach in our systems, we immediately deleted the entire website and the database associated with it," the unsigned statement continues. "As far as we can tell, the breach has effected [sic] 500MB of images, and 0 personal information from the database." [source] | Sonic Drive-In had a data breach in 2017, in Oklahoma. Sonic Drive-In, a fast-food chain with nearly 3,600 locations across 45 U.S. states, has acknowledged a breach affecting an unknown number of store payment systems. The ongoing breach may have led to a fire sale on millions of stolen credit and debit card accounts that are now being peddled in shadowy underground cybercrime stores, KrebsOnSecurity has learned.The first hints of a breach at Oklahoma City-based Sonic came last week when I began hearing from sources at multiple financial institutions who noticed a recent pattern of fraudulent transactions on cards that had all previously been used at Sonic. [source] | |
Sony Pictures Entertainment Health and Welfare Benefits Plan (the Plan) had a data breach in 2014, in California. OCR determined that no breach occurred in this case. Location of breached information: Desktop Computer, Laptop, Network Server Business associate present: No [source] | Sony PlayStation had a data breach in 2014, in New York. PlayStation and xBox networks over the holiday season. A group calling itself "LizardSquad" hacked both gaming networks on Christmas Day. According to the group and KrebsOnSecurity, "various statements posted by self-described LizardSquad members on their open online chat forum - chat.lizardpartrol.com - suggest that these misguided individuals launched the attack for no other reason than because they thought it would be amusing to annoy and dissapoint people who received new Xbox and Playstation consoles as holiday gifts". [source] | |
Sorrento Pacific Financial LLC had a data breach in 2015, in California. [source] | Sourcebooks Inc. had a data breach in 2014, in Illinois. The information was breached via Laptop. [source] | |
South Carolina Health and Human Services, South Carolina Medicaid had a data breach in 2012, in South Carolina. An employee was fired and arrested after he sent the names, addresses, phone numbers, and dates of birth of Medicaid patients to his private email. It was discovered that he had compiled and emailed the information of South Carolina Medicaid patients over a period of several months. He was charged with five misdemeanor counts of violating the confidentiality of medical indigents and one count of disclosing confidential information. At least 22,600 patients had their Medicaid ID numbers emailed. It is unclear how many of those patients had their Social Security number used in place of a Medicaid ID number. Patients were warned not to give any personal information to anyone contacting them and claiming to be from the Medicaid agency.UPDATE (02/20/2013): A dishonest employee and another individual have been charged with criminal conspiracy. The employee was also charged with willful examination of private records by a public official, public member, or public employee. [source] | South Carolina State Budget and Control Board Employee Insurance Program had a data breach in 2011, in South Carolina. People who are covered by South Carolinas state insurance program may have had their personal information obtained. A virus affected one of the Insurance Programs computers. The breach occurred sometime between November 8 and November 18. Insured current and former employees, dependents and survivors may have had their names, Social Security numbers, health information, addresses and dates of birth exposed. [source] | |
Spiral Toys had a data breach in 2017, in California. A company selling internet-connected stuffed toys used by kids and parents to send voice messages to one another leaked 800,000 user account credentials and 2 million message recordings, according to security researcher Troy Hunt. The data was hacked, locked and held for ransom.Researchers and journalists have been trying to reach the company, Spiral Toys, since late last year to confirm and fix the data breach and security problems for the CloudPets brand. No one has heard back from the manufacturers as the data hit the web and was passed around between hackers and researchers.The magnitude of problems and the nature of the victims — small children and families — have set up the CloudPets hack to be a textbook-example security failure for a long time to come. Spiral Toys is a virtually worthless company, according to its stock prices and activity. It does not appear to have a functioning phone number, and no one at Spiral Toys has answered an email on this issue for months, including messages sent Monday by CyberScoop.CloudPets’ data is stored in a public-facing MongoDB database without any authentication required. The database was indexed by search engines like Shodan and found independently by multiple individuals. [source] | Splash Car Wash had a data breach in 2014, in Connecticut. The information was breached via Desktop Computer. [source] | |
Sports Memorabilia.com had a data breach in 2017, in Florida. [source] | Springfield Armory had a data breach in 2016, in Illinois. In late September, Springfield Armory received a report from a payment card network that it had noticed a pattern of unauthorized charges occurring on payment cards after they were used to make a purchase on our website. Springfield Armory immediately initiated an investigation and engaged a leading cyber security firm to examine our website network. In early October, the investigation determined that an unauthorized person gained access to the web server and installed code that was designed to copy information entered during the checkout process. What Information Was Involved Information entered during the checkout process included order ID, name, address, email address, phone number, payment card number, expiration date and card security code. This information from orders placed between October 3, 2015 and October 9, 2016 may have been affected. [source] | |
SRI, Inc. had a data breach in 2015, in Virginia. The information was breached via Electronic Medical Record. [source] | Stanford Federal Credit Union had a data breach in 2014, in California. Stanford Federal Credit Union informed 18,000 members that their personal information was sent to another member accidentally. According to the letter sent to the members, credit union employees recognized the error immediately and the data was destroyed without it being read to the recipient. The data sent was a list of members who were pre-approved for loans. The credit union employee who sent the list inadvertently sent it to a member who had the same first name as the staff member it was meant for. According to the credit union, the member had not yet read the mail and worked with the staff of the credit union to properly destroy it. [source] | |
Staples Inc. had a data breach in 2014, in Massachusetts. Name and payment card info were breached. [source] | Starbucks had a data breach in 2015, in Washington. [source] | |
Starwood Hotels had a data breach in 2015, in Connecticut. Starwood Hotel chain is the latest to have been affected by cyber criminals. The hotel has notified customers of exposure of credit/debit card information used at retail shops, gift shops and restaurants at W Hotels, Sheraton Hotels and Westin brands. 54 locations may have been affected and included credit/debit card numbers, names and security codes on the back of the cards. [source] | State of Tennessee Sponsored Group Health Plan had a data breach in 2011, in Tennessee. [source] | |
Stater Brothers Market had a data breach in 2015, in California. Stater Brothers Markets in West Covina has sent out a notice to the public to help aprehend three suspects who placed a skimmer device on a pin pad in the deli department of the grocery chain located at 375 North Azuza Avenue, West Covina California.They have also send the notification out for those who may have used their debit or credit card at the West Covina location from March 5, 2015 and March 29, 2015 to review their bank or credit card statements for any unauthorized activity. [source] | Statista had a data breach in 2014, in New York. Online statistics portal, Statista, notified customers of a data breach that occurred with their system. The breach was noticed when the company internally started receiving spam emails. The company investigated and approximately 50,000 of its customers username and password combination were compromised.The company has not said whether or not the breach goes beyond access to username and passwords, but at present, this seems to be all that has been affected.The company notified users almost immediately and assured them that the compromised passwords "cannot be used by third parties due to masking procedures". The company did not encourage customers to change their passwords. Experts are questioning how secure the passwords are for those that created accounts prior to December 2013 and have stated that "the passwords of those who signed up before this data were stored in the Statista database as MD5 hashes. As many experts will tell you, MD5 passwords can be easily cracked". The main risk for those affected would be a higher incidence of spam and phishing emails, potentially impersonating Statista. [source] | |
Steel Technology LLC dba Hydro Flask had a data breach in 2017, in Oregon. [source] | Sterling BackCheck had a data breach in 2015, in New York. [source] | |
Sterne, Agee & Leach had a data breach in 2014, in Alabama. The information was breached via Network Server. [source] | Stiletto Solutions had a data breach in 2015, in California. [source] | |
Straight Dope Message Board had a data breach in 2014, in Illinois. The security team at The Straight Dope discovered hackers broke into their online message board forum. This resulted in unauthorized access of members usernames, emails and passwords. The message board does not store Social Security numbers or credit card information. The company is suggesting all users change their password in their system. [source] | Streets of New York had a data breach in 2015, in Arizona. [source] | |
StumbleUpon had a data breach in 2014, in California. The information was breached via Paper/Films. [source] | Summit Financial Group had a data breach in 2015, in California. [source] | |
SunTrust Banks, Inc. had a data breach in 2018, in Georgia. [source] | Supervalue had a data breach in 2014, in Minnesota. Supervalu, which operates 3,763 outlets, both corporate and franchised stores, has reported a data breach in their point-of-sale system which affected some of its retail food stores, along with several of its stand-alone liquor stores.The information compromised includes account numbers and other information on customer payment cards used at the point-of-sale systems. The data breach occurred from June 22, 2014 through July 17, 2014 according to company spokesperson. [source] | |
Sutter Health had a data breach in 2015, in California. Sutter Health has notified patients/customers of a data breach when they discovered that a former employee had emailed documents of individuals to a personal email address on April 26, 2013.The information in these electronic documents included names, dates of birth, insurance identification numbers, dates of services and billing codes. They have stated that no Social Security numbers, drivers' license or ID numbers, credit card or bank information was contained in these documents. Sutter Health is offering one year free of Experian's ProtectMyID Alert for those who were affected. [source] | SwimOutlet.com had a data breach in 2017, in California. On October 31, 2016, we began investigating some unusual activity reported by our credit card processor. We immediately began to work with third-party forensic experts to investigate these reports and to identify any signs of compromise on our systems. On November 28, 2016, we received confirmation of a sophisticated cyberattack in which a hack into our system may have compromised some customers’ debit and credit card data used at www.swimoutlet.com between May 2, 2016-November 22, 2016. The information at risk as a result of this event includes the cardholder’s name, address, phone number, email address, card number, expiration date, and CVV. [source] | |
Swiss Cleaners had a data breach in 2015, in Connecticut. The information was breached via Paper/Films. [source] | Systema Software had a data breach in 2015, in California. Systema Software has communicated that a "single individual gained unapproved access into our data storage system." It has been communicated that this breach exposed over 1.5 million records of public agencies in California, Kansas and Utah.The records included police injury reports, drug tests, detailed doctor visit notes and Social Security numbers. [source] | |
Target Corporation Health Plan had a data breach in 2016, in Minnesota. During the maintenance of a printer press, a technician incorrectly changed a printer setting resulting in errors on printed explanation of benefit (EOB) letters sent by a subcontractor on behalf of a business associate (BA), Kaiser Permanente Insurance Company. The error impacted the letters of 719 individuals. The protected health information (PHI) involved in the breach included names, addresses, annual deductibles, annual out of pocket maximum, dollars spent "year to date" towards the deductible, and out of pocket maximums. The BA provided breach notification to HHS, affected individuals, and the media. Following the breach, the subcontractor BA updated its procedures to include additional oversight and additional print testing during printer updates or maintenance. OCR’s investigation resulted in the subcontractor BA improving safeguards in the printing of PHI for the covered entity's health plan. [source] | Tarte Cosmetics had a data breach in 2017, in New York. Tarte Cosmetics, a cruelty-free cosmetics brand carried by major retailers like Sephora and Ulta, exposed the personal information of nearly two million customers in two unsecured online databases.The databases were publicly accessible and included customer names, email addresses, mailing addresses, and the last four digits of credit card numbers, according to the Kromtech Security Center, the firm that discovered the exposed data. [source] | |
Taskrabbit had a data breach in 2018. [source] | T-Bird Restaurant Group, Inc. (Outback Steakhouse) had a data breach in 2015, in California. Names and bank accounts were breached. [source] | |
TeenSafe had a data breach in 2018, in California. [source] | TennCare had a data breach in 2010, in Tennessee. An electronic error caused information such as Social Security numbers for about 3,900 enrollees to be sent to incorrect addresses. The error was the result of a modification to the system that pulls addresses into an electronic file for TennCare, the states expanded Medicaid program. Letters and cards that contained one or more pieces of personal information were sent to incorrect addresses. [source] | |
Texas Insurance Claims Services had a data breach in 2008, in Texas. Hundreds of files with peoples names, Social Security numbers and policy numbers were found in a richardson dumpster, apparently discarded by Texas Insurance Claims Services. [source] | Texas Veterans Commission had a data breach in 2009, in Texas. A Waco individual received a packet in the mail with the application for her daughters tuition benefits. at the bottom of the packet, was a claims log that listed more than 20 veterans names, Social Security numbers and medical claim information. the Waco Veterans Commission and the VAs regional office were not able to explain how the veterans personal information found its way into the envelope containing the unrelated information about the tuition benefits for the womans daughter. [source] | |
The Buckle Inc. had a data breach in 2017, in Nebraska. The information was breached via Network Server. [source] | The Cooperative Bank of Cape Cod had a data breach in 2016, in Massachusetts. It was an electronic breach affecting credit/debit cards as reported by the department of Consumer Affairs and Business Regulation the state of Massachusetts. [source] | |
The Health Plan of San Mateo (HPSM) had a data breach in 2011, in California. Member notifications of approval of medical procedures were sent to the incorrect addresses. Each approval letter contained the members name, address, service requested, and HPSM member ID number. The mistake was discovered on June 9, 2011 and the programming error that caused it was immediately fixed. [source] | The Home Depot had a data breach in 2014, in Georgia. [source] | |
The Honest Kitchen had a data breach in 2017, in California. [source] | The Houstonian Hotel, Club and Spa had a data breach in 2014, in Texas. Secret Service notified The Houstonian Hotel, Club and Spa regarding a breach to their system that houses customer credit card information.Once the notification happened, the company launched a forensics investigation and discovered that their POS system had been accessed by an unauthorized third party from December 2013 through June 2014, and that the credit card information stored on these systems were compromised.The company has since stopped the intrusions, but has not communicated how many individuals were affected by the breach. The company is offering 12 months free of credit monitoring services for those affected. [source] | |
The LANG Companies, Inc. had a data breach in 2016, in Wisconsin. On October 12, 2016, we learned that unauthorized individuals installed malicious software on the computer server used to process credit card transactions at www.LANG.com. Based on our investigation, we believe that customers who placed an order on our website from September 1, 2016 to October 19, 2016, may have had information associated with the order transmitted outside of our system. What Information Was InvolvedOur records show that you made a purchase using a payment card during this time. The information that could have been transmitted may include your name, address, payment card number, expiration date and security code (CVV). [source] | The Madison Square Garden Company had a data breach in 2016, in New York. The information was breached via Portable Electronic Device. [source] | |
The Metropolitan Companies had a data breach in 2014, in New York. [source] | The Office of Jeb Bush had a data breach in 2015, in Florida. Jeb Bush's office inadvertently exposed 12,500 individuals' personal information as part of a larger cached file of 332,999 emails sent to him when he was the Governor of Florida. The email was sent as part of a measure for transparency, however his team neglected to remove personal information if 12,500 of those individuals exposing names, Social Security numbers, and birthdates. The office has since redacted the information, which were believed to have been individuals on a family services waiting list from 2003. [source] | |
The Paper Works had a data breach in 2016, in California. The information was breached via Paper/Films. [source] | The Sacramento Bee had a data breach in 2018, in California. The Sacramento Bee said in a statement that a firewall protecting its database was not restored during routine maintenance last month, leaving the 19,501,258 voter files publicly accessible. Additionally, the names, home addresses, email addresses, and phone numbers of 52,873 Sacramento Bee subscribers were compromised."We take this incident seriously and have begun efforts to notify each of the individuals on the contact list and to provide them resources to help guard against potential misuse of their personal contact information," the paper said in a statement. "We are also working with the Secretary of State’s office to share with them the details of this intrusion." [source] | |
The UPS Store had a data breach in 2014, in Georgia. The UPS Store, Inc has notified customers of a data breach when they discovered malware in their systems targeting UPS retailers. UPS retained a security firm to review their systems and found malware at 51 locations in 24 states. UPS has a total of 4,470 franchised center locations within the US. The company announced that both credit and debit card purchases were impacted at the franchised locations from January 20, 2014 through August 11, 2014. The company has since removed the malware from their system. [source] | Tim McCoy & Associates/ dba.NEAT Management Group had a data breach in 2014, in Texas. Tim McCoy and Associates, also known as NEAT Management Group informed customers of a data breach when the laptop belonging to one of the company's software engineers was stolen on August 27, 2014.The information on the laptop included names, Social Security Numbers, dates of birth, addresses, phone numbers, employer identification numbers and email addresses.The company is providing a free membership for a year to ProtectMyID. [source] | |
Time Warner Cable had a data breach in 2016, in California. PayPal's recently-acquired payment processor TIO Networks has revealed that up to 1.6 million customers have had their information stolen in a recent data breach.Last week, the Vancouver, Canada-based TIO Networks said that following the suspension of operations, evidence has been uncovered of a data breach due to unauthorized access.In a statement, the company said that unknown attackers were able to gain access to locations that stored personal information of some of TIO's customers and customers of TIO billers.In total, up to 1.6 million customers may have had their information leaked, which could include personally identifiable information (PII) or potentially financial data. [source] | TIO Networks had a data breach in 2017, in British Columbia. PayPal's recently-acquired payment processor TIO Networks has revealed that up to 1.6 million customers have had their information stolen in a recent data breach.Last week, the Vancouver, Canada-based TIO Networks said that following the suspension of operations, evidence has been uncovered of a data breach due to unauthorized access.In a statement, the company said that unknown attackers were able to gain access to locations that stored personal information of some of TIO's customers and customers of TIO billers.In total, up to 1.6 million customers may have had their information leaked, which could include personally identifiable information (PII) or potentially financial data. [source] | |
T-Mobile had a data breach in 2016, in Washington. [source] | T-Mobile had a data breach in 2018. [source] | |
Topps had a data breach in 2016, in New York. Topps, the iconic maker of Star Wars, Frozen and various sports-related trading cards, has just notified its customers of security breaches that happened earlier this year. In it, the company has admitted that one or more intruders infiltrated its system and may have gained access to [customers'] names, addresses, email addresses, phone numbers, debit or credit card numbers, card expiration days and card verification numbers. Topps said it didn't find out about the intruders until October 12th, but anyone who bought items through its website from June 30th to that date could be affected. Upon discovering the breaches, it worked with a security firm to fix the vulnerability the hackers exploited and to fortify its system. [source] | Toys "R" Us had a data breach in 2015, in New Jersey. Toys "R" Us contacted customers that their passwords to their reward program account would be reset in order to avoid an unauthorized attempts to their rewards program account. The company communicated that those notified did not necessarily have their accounts accessed, however, the risk was higher due to the discovery by the company of "recycled login details used by some of its customers." Between January 28th and January 30th, 2015, the company discovered a number of "illegal login attempts made to its Rewards "R" Us accounts." The current announcement is an additional security measure so that other customer accounts cannot be accessed in a similar way. "Out of an abundance of caution, we are therefore treating your account password as compromised and taking appropriate steps to address the situation," in a letter sent by the company to its customers. [source] | |
Toys R Us had a data breach in 2017, in New Jersey. [source] | TRICARE Management Activity, Science Applications International Corporation (SAIC) had a data breach in 2011. [source] | |
Triple-C, Inc. (TCI), Triple-S Salud, Inc. (TSS) had a data breach in 2010, in Puerto Rico. An internet database managed by TCI containing information of some people insured by Triple-S Salud, Inc. was accessed by employees of a competitor. People insured by TSS under the Puerto Rican governments health insurance plan and independent practice associations (IPA) that provided services to those people may have had their information accessed. The breach was the result of the unauthorized use of one or more active user IDs and passwords for the TCI IPA database. TCI believes that financial information related to IPAs was the target of the attack and not the information of individuals. Multiple intrusions happened in September. A TCI competitor notified the organization on September 21. [source] | Triumph LLC had a data breach in 2012, in North Carolina. A laptop with Triumph client and family member information was stolen on December 13. The office burglary was committed by three men. Two of them distracted the receptionist while the third entered a hallway and stole the laptop. People in Davie, Forsyth, and Stoke counties were affected. The laptop contained spreadsheets with names, dates of birth, medical record numbers, insurance numbers, and Medicaid numbers. Notifications went out on February 2 after it was determined that the laptop would most likely not be recovered. [source] | |
Turner Construction had a data breach in 2016, in California. Turner Construction notified individuals of a data breach when certain personal information was disclosed in an email to an unauthorized party. The information included names, Social Security number, name of each state in which wages or taxes are reported, federal, state, local and Medicare earnings and tax withholding data.The company is providing identity monitoring services through Kroll. [source] | Twitter had a data breach in 2016, in California. It was reported that the login credentials of more than 32 million Twitter users were compromised. According to LeakedSource, which indexes hacked credentials from data breaches, the credentials are being traded on the Dark Web for about 10 bitcoin a pop or a little under $6,000. LeakedSource goes on to note that passwords are stored as plain text files, and many seem to be attached to Russian users. That detail indicates that the passwords were stolen from users, as opposed to through a hack into Twitter’s central systems.In response to the leak, Twitter quickly initiated forced resets for many of its users. [source] | |
U.S. Health Holdings, Ltd. had a data breach in 2014, in Michigan. The information was breached via Laptop. [source] | U.S. Weather System had a data breach in 2014, in District Of Columbia. Officials from the National Oceanic and Atmospheric Administration (NOAA), which includes the National Weather Service, have notified officials of a data breach to the National Weather Service's satellite network.Reports are stating "hackers from China breached the federal weather network recently, forcing cybersecurity teams to seal off data vital to disaster planning, aviation, shipping and scores of other crucial uses, officials said."It appears the system was affected in September, but officials did not communicate that there was a problem until late October. an NOAA spokesman Scott Smullen did confirm that there were hacks and communicated that "incident response began immediately". [source] | |
Uber Technologies Inc. had a data breach in 2015, in California. Uber notified 50,000 drivers of an unauthorized access to their database which resulted in compromising driver data. The hacking took place in May of 2014. According to the company only names and driver's license numbers were compromised. The company is offering identity protection services for affected drivers. [source] | Uber had a data breach in 2015, in California. Uber disclosed Tuesday that hackers had stolen 57 million driver and rider accounts and that the company had kept the data breach secret for more than a year after paying a $100,000 ransom.The deal was arranged by the company’s chief security officer and under the watch of the former chief executive, Travis Kalanick, according to several current and former employees who spoke on the condition of anonymity because the details were private.The security officer, Joe Sullivan, has been fired. Mr. Kalanick was forced out in June, although he remains on Uber’s board.The two hackers stole data about the company’s riders and drivers — including phone numbers, email addresses and names — from a third-party server and then approached Uber and demanded $100,000 to delete their copy of the data, the employees said. [source] | |
Ubiquiti Networks Inc. had a data breach in 2015, in California. Ubiquiti Networks Inc. announced that cyber thieves stole $46.7 million using a scam " in which crooks spoof communications from executives at the victim firm in a bid to initiate unauthorized international wire transfers."Ubiquiti disclosed the attack when they filed a report with the U.S. Securities and Exchange Commission. "The company said it discovered the fraud on June 5, 2015, and that the incident involved employee impersonation and fraudulent requests from an outside entity targeting the company’s finance department." [source] | UFCW Local 655 had a data breach in 2016, in Missouri. Name, ssn, dob, address were breached. [source] | |
Ullrich Delevati had a data breach in 2016, in California. Ullrich Delevati CPA's notified customers of a data breach when their system was compromised exposing names, addresses, dates of birth, Social Security numbers, and bank account numbers. [source] | Unconfirmed had a data breach in 2016. [source] | |
Union Security Insurance Company had a data breach in 2011, in Nevada. On February 18 of 2011, it was discovered that patient health and personal information had accidentally been disclosed. [source] | United Airlines had a data breach in 2015, in Illinois. United Airlines may be the latest victim of Chinese hackers. It is being reported that the hackers are potentially the same group that infiltrated OPM and Anthem."United, the world’s second-largest airline, detected an incursion into its computer systems in May or early June, said several people familiar with the probe. According to three of these people, investigators working with the carrier have linked the attack to a group of China-backed hackers they say are behind several other large heists -- including the theft of security-clearance records from the U.S. Office of Personnel Management and medical data from health insurer Anthem Inc."The information compromised included flight information, passenger itinerary, passenger information, origins and destinations. The airline has not announced whether or not any financial data was compromised in this hack. [source] | |
United Airlines had a data breach in 2015, in Illinois. United Airlines notified customers of an unauthorized access to their MileagePlus account with usernames and passwords obtained from a third-party source. The unauthorized access began on December 9, 2014, where the hacker (s) attempted to infiltrate the accounts of United Mileage Plus accounts. The hackers obtained MileagePlus numbers and possible account details. The company has stated that if the profile included a credit card number, only the last 4 digits of the card were visible. United temporarily suspended Mileage Plus accounts. [source] | United Healthcare (UnitedHealthcare), Deere and Company had a data breach in 2010, in Minnesota. [source] | |
United Healthcare Inc., Futurity First Insurance Group had a data breach in 2011, in Minnesota. A hard drive containing information on United Healthcare Medicare plan members was stolen from Futurity First Insurance Group. Member names, Social Security numbers, and in some cases, birth dates and private health information were exposed. Futurity First, United Healthcares sales and marketing services provider, sent the hard drive to a vendor for repair. The hard drive was stolen from the vendor on or around June 28 July 28 and reported stolen on August 12. Futurity First then told United Healthcare on September 14.UPDATE (10/30/2011): Three additional organizations were affected by the breach. A total of 705 members from Mutual of Omaha Insurance Company, 1,631 United of Omaha Life Insurance Company enrollees, and 3,994 United Health Group Health Plan in Minnesota enrollees were also affected in addition to the 582 originally reported. Information from the Health and Human Services website also reveals that the hard drive was lost on July 28.UPDATE (11/4/2011): A total of 690 American Continental Insurance Company members from Tennessee were also affected by the breach. [source] | United Healthcare Inc. had a data breach in 2011, in Alabama. A man was sentenced to six years in prison for his role in an identity theft scheme. The man and an unknown number of accomplices somehow obtained the personal information of people who had Flexible Spending Accounts administered by United Healthcare Inc. The group then created counterfeit prescriptions for controlled substances by using the information of patients covered by a prescription drug plan sponsored by the Federal Employees Health Benefit Plan. The group sold the prescribed drugs to third parties from September 2008 through April 2009. The Federal Employees Health Benefit Plan lost $72,746 on drugs and services obtained by the criminals. [source] | |
United HealthGroup had a data breach in 2010, in Minnesota. A breach involving paper records and categorized by the Health and Human Services (HHS) website as theft, unauthorized access occurred when patient documents were stolen on March 2. The incident was reported to HHS on August 4. Little more is known about the incident. [source] | United HealthGroup had a data breach in 2010, in Minnesota. United HealthGroup reported a breach of paper records to Health and Human Services in June. The breach occurred on January 26. [source] | |
United States Navy Career Waypoints (C-WAY) Database had a data breach in 2016, in District Of Columbia. A dishonest employee used the names, Social Security numbers, addresses, phone numbers, dates of birth, and Medicare Health Insurance Claim Numbers to steal the identities of at least 24 Idaho customers enrolled in UnitedHealthcare Medicare plans. On January 30, 2012, it was discovered that the former employee may have accessed the information in the United Health Care database in a way that was inconsistent with his job duties and possibly for fraud purposes. The information was taken between June 28 and December 12 of 2011. Affected patients were notified on March 30. [source] | UnitedHealth Group had a data breach in 2010, in Minnesota. A breach involving UnitedHealth Group and its business associate CareCore National was posted on the Health and Human Services (HHS) website. Unauthorized persons were able to access paper records on or around July 8. [source] | |
UnitedHealthcare (United Health Group Plan) had a data breach in 2012, in Minnesota. A dishonest employee used the names, Social Security numbers, addresses, phone numbers, dates of birth, and Medicare Health Insurance Claim Numbers to steal the identities of at least 24 Idaho customers enrolled in UnitedHealthcare Medicare plans. On January 30, 2012, it was discovered that the former employee may have accessed the information in the United Health Care database in a way that was inconsistent with his job duties and possibly for fraud purposes. The information was taken between June 28 and December 12 of 2011. Affected patients were notified on March 30. [source] | Universal American Action Network had a data breach in 2009, in Pennsylvania. Thousands of Pennsylvanians are at risk for identity theft because postcards were sent to their homes with their Social Security numbers printed in plain view. The postcards were from the Universal American Action Network, a subsidiary of Universal American Insurance. 80,000 postcards with SSNs on them were sent to Universal clients throughout the country. More than 10,000 were mailed to Medicare participants in Pennsylvania. [source] | |
Universal Care, dba, Brand New Day had a data breach in 2017, in California. A major breach of electronic protected health information has been discovered by Universal Care, dba, Brand New Day – A Medicare approved health plan.On December 28, 2016, Brand New Day became aware that an unauthorized individual had gained access to ePHI provided to one of its HIPAA business associates. Access to ePHI was gained via a third-party vendor system used by Brand New Day’s contracting provider six days previously on December 22, 2016.The breach notification submitted to the California attorney general does not indicate whether the ePHI of plan members was stolen, although the data were accessed and a criminal investigation into the breach has been launched by law enforcement. The types of data accessed include plan members’ names, addresses, phone numbers, dates of birth and Medicare ID numbers.Upon discovery of the incident, Brand New Day immediately launched an investigation and contacted its vendor to ensure that access to ePHI was immediately terminated. The vendor was informed that someone had improperly accessed plan members’ data and rapid action was taken to block access. Brand New Day says the error that allowed ePHI to be accessed was eliminated ‘within hours’ of its vendor being notified of the breach. [source] | University California Irvine had a data breach in 2014, in California. On March 26, 2014, the California Information Security Office notified the University California Irvine that three of the computers in the Student Health Center had been infected by a keylogging virus, which captured the keystrokes as information was being entered into the computers, then transmitted the data to unauthorized servers. They believe that hackers gained information from February 14th through March 27th 2014. As a result of the virus personal information of individuals was compromised. The information included names, unencrypted medical information, potentially including health or dental insurance number, CPT codes, ICD9 codes and/or diagnosis, student ID numbers, non-student patient ID numbers, mailing addresses, telephone numbers, amounts paid to the Student Health Center for services, bank names and check numbers. UC Irvine has contracted with ID Experts to provide one year of FraudStop credit monitoring and one year of CyberScan Internet monitoring for those affected. [source] | |
University of Missouri, Coventry Health Care had a data breach in 2011, in Missouri. A Coventry Health Care computer malfunction caused the names of University of Missouri health insurance program participants to be aligned with incorrect mailing addresses. Names, member numbers and birth dates were on mailed documents like benefits statements, health services letters and new ID cards. The erroneous mail was sent out to employees between January 6 and 10. An employee notified the University on or around January 14. [source] | USA Hoist Company, Inc./Mid-American Elevator/Mid-American Equipment had a data breach in 2017, in Illinois. A server used by USA Hoist Company, Inc., Mid-American Elevator Company, Inc., and Mid-American Elevator Equipment Company, Inc. to store employee and vendor information was subject to a ransomware attack by the hacker group called the Dark Overlord. We discovered the attack on the morning of Tuesday, October 17, 2017, when we could not access certain of our data systems as a result of the breach. On Thursday, October 19, 2017, the FBI visited our offices to inform us that we may become the subject of a such an attack, but by that time the attack had already occurred.What Information was Involved: The information breached contained employee names, mailing addresses, cancelled checks for employee direct deposits, direct payment account numbers for employees and vendors, non-union member employee health insurance applications, and/or employee Social Security numbers. To our knowledge, other information (bank account PIN, security codes, etc.) was not breached. [source] | |
Utah Department of Health had a data breach in 2012, in Utah. The information was breached via Email. [source] | Vacaville Housing Authority had a data breach in 2015, in California. The Vacaville Housing Authority (VHA) notified individuals of a data breach when a VHA employee inadvertently sent sent an email with a file that had customers personal information in it. The information included names and Social Security numbers. The file reportedly was sent to only one person and she immediately contacted the VHA. According to the VHA authorities verified that the email was deleted from this persons computer. The VHA is offering 12 months free of credit monitoring services through Kroll for those individuals that were affected. [source] | |
Valley Kaiser, Kaiser Permanente had a data breach in 2010, in California. An electronic storage device stolen from an employees car in Sacramento last month contained health information from 15,500 patients, including about 800 in the Fresno area. Information included patient names, medical-record numbers and, for some individuals, ages, dates of birth, gender, phone numbers and other information related to their care and treatment. [source] | Value Eyecare Network, Inc (39dollarglasses.com) had a data breach in 2017, in New York. [source] | |
Ventiv Technology, Inc. had a data breach in 2017, in Georgia. Ventiv Technology, Inc. experienced a phishing attack and exposed the records of 239 individuals. The breach occurred from 10/14/17 until 12/5/17, was discovered on 1/5/18 and Ventiv began notifying consumers on 2/1/2018. Information that was exposed included Social Security numbers. [source] | Vera Bradley had a data breach in 2016, in Indiana. Payment cards used at Vera Bradley store locations between July 25, 2016 and September 23, 2016 may have been affected. Not all cards used in stores during this time frame were affected. Cards used on verabradley.com were not affected. Information on steps customers may take to protect their information can be found at www.verabradley.com/protectingourcustomers.The information compromised included all information on the magnetic stripe of the card. The information on the stripe includes the card number, name on the card, expiration date and verification code. [source] | |
Verifone had a data breach in 2017, in California. Credit and debit card payments giant Verifone [NYSE: PAY] is investigating a breach of its internal computer networks that appears to have impacted a number of companies running its point-of-sale solutions, according to sources. Verifone says the extent of the breach was limited to its corporate network and that its payment services network was not impacted.San Jose, Calif.-based Verifone is the largest maker of credit card terminals used in the United States. It sells point-of-sale terminals and services to support the swiping and processing of credit and debit card payments at a variety of businesses, including retailers, taxis, and fuel stations.On Jan. 23, 2017, Verifone sent an "urgent" email to all company staff and contractors, warning they had 24 hours to change all company passwords."We are currently investigating an IT control matter in the Verifone environment," reads an email memo penned by Steve Horan, Verifone Inc.’s senior vice president and chief information officer. "As a precaution, we are taking immediate steps to improve our controls."An internal memo sent Jan. 23, 2017 by Verifone’s chief information officer to all staff and contractors, telling them to change their passwords. The memo also states that Verifone employees would no longer be able to install software at will, apparently something everyone at the company could do prior to this notice. [source] | Verizon Enterprise Solutions had a data breach in 2016, in New York. Verizon Enterprise Solutions has suffered a data breach of their customer data. "Earlier this week, a prominent member of a closely guarded underground cybercrime forum posted a new thread advertising the sale of a database containing the contact information on some 1.5 million customers of Verizon Enterprise. The seller priced the entire package at $100,000, but also offered to sell it off in chunks of 100,000 records for $10,000 apiece. Buyers also were offered the option to purchase information about security vulnerabilities in Verizon’s Web site."Verizon communicated to KrebsOnSecurity that "the company recently identified a security flaw in its site that permitted hackers to steal customer contact information, and that it is in the process of alerting affected customers." [source] | |
Verizon had a data breach in 2014, in New Jersey. The security issue, uncovered by research from cybersecurity firm UpGuard, was caused by a misconfigured security setting on a cloud server due to human error. The error made customer phone numbers, names, and some PIN codes publicly available online. PIN codes are used to confirm the identity of people who call for customer service.No loss or theft of customer information occurred, Verizon told CNN Tech.UpGuard -- the same company that discovered leaked voter data in June -- initially said the error could impact up to 14 million accounts.Chris Vickery, a researcher at UpGuard, discovered the Verizon data was exposed by NICE Systems, an Israel-based company Verizon was working with to facilitate customer service calls. The data was collected over the last six months.Vickery alerted Verizon to the leak on June 13. The security hole was closed on June 22.The incident stemmed from NICE security measures that were not set up properly. The company made a security setting public, instead of private, on an Amazon S3 storage server -- a common technology used by businesses to keep data in the cloud. This means Verizon data stored in the cloud was temporarily visible to anyone who had the public link. [source] | Vertical Scope Inc. had a data breach in 2016, in Ontario. On June 13, 2016, we became aware that February 2016 data stolen from VerticalScope was being made available online.The information compromised included member usernames, email addresses, hashed passwords, community userIDS, community website, and IP addresses usernames originally registered with. [source] | |
Veterans Of Foreign Wars Of The United States had a data breach in 2014, in Missouri. The OurMine hacking collective broke into the servers of music video hosting service Vevo and on late Thursday posted approximately 3.12 terabytes of stolen documents and data on its website, in an unusually aggressive attack by the group.Normally, OurMine is known for accessing celebrities' or companies' social media accounts and defacing their corresponding pages. In such circumstances, the group typically claims to be testing victims' security and offers to help improve their defenses. But the data dump constitutes a more serious infraction, as it involves the posting of private documents. [source] | Vevo had a data breach in 2017, in California. The OurMine hacking collective broke into the servers of music video hosting service Vevo and on late Thursday posted approximately 3.12 terabytes of stolen documents and data on its website, in an unusually aggressive attack by the group.Normally, OurMine is known for accessing celebrities' or companies' social media accounts and defacing their corresponding pages. In such circumstances, the group typically claims to be testing victims' security and offers to help improve their defenses. But the data dump constitutes a more serious infraction, as it involves the posting of private documents. [source] | |
Viator Inc had a data breach in 2014, in California. Viator Inc, was notified of a data breach by their credit card service provider when they had received numerous complaints of erroneous charges to accounts. Their investigation lead to seeing fraudulent charges to Viator customers via their online payment processing system. The breach includes the compromise of customer credit card and debit card data, card expirations, names, billing addresses, email addresses and Viator "nicknames". The company is offering 12 month of credit monitoring services at no cost. [source] | Vibram had a data breach in 2014, in Massachusetts. Name and credit card info were breached. [source] | |
Vine had a data breach in 2017, in Connecticut. Twitter is alerting Vine users of a bug that exposed their email addresses and, in some cases, phone numbers to third parties. It’s also advising affected users to be cautious about any emails from unknown senders as a result. The company says the bug was only active for 24 hours before being patched, and doesn’t believe that the data was misused in any way, at this time.To be clear, Twitter was not hacked nor is this considered a data breach – instead, the email address or phone number the company had on file for some Vine users was only available under certain circumstances, the company says.The company declined to officially comment on the specifics of how the bug was discovered or how it may have been seen by third parties, but we understand that this data was not published on the Vine archive website where anyone on the public internet could have seen it. Instead, if anyone was to have seen the data at the time of exposure, they would have had to do so through a more technical means – such as using an API to pull the information.Twitter is only alerting users out of a desire to be transparent in disclosing the vulnerability, not because they believe that anyone actually captured the user data or misused it in any way. [source] | Virgin Mobile had a data breach in 2016, in New Jersey. A privacy breach seems to be underway at Virgin Mobile. Customers attempting to access their voicemail messages are instead getting access to the voicemail messages of other people.When dialing the 212 number used by Virgin Mobile that allows access to your own voicemail box, Virgin Mobile customers are instead reporting that they are hearing strangers' voicemail messages, getting access to their voicemail account menus, or being directed to leave messages on a stranger's voicemail.Customers are already taking to social media to report the issue. One Facebook user, Alison, raised concerns with Virgin Mobile customer service. This is clearly a security issue when I'm reaching other customers, I assume they're customers, voicemail inboxes. [source] | |
Volunteer State Health Plan, Inc. (VSHP), Comprehensive Counseling Network had a data breach in 2012, in Tennessee. Envelopes containing BlueCare member protected health information were damaged while being sent to Comprehensive Counseling Network. Lists of claims containing patient protected health information became separated from the envelopes and were lost. Patient names, BlueCare ID numbers, dates of services, procedure codes, claim numbers, totals charged, amounts paid, provider names and provider addresses may have been exposed. The envelopes also contained check to pay for medical visits that were listed on the claims, but the checks were not lost. [source] | VTech had a data breach in 2015, in Illinois. VTech, a Hong Kong based company notified customers of a data breach when hackers were able to gain access to childrens' photos, chat logs, children's names, genders and birthdates, account email addresses, passwords, secret questions and answers for password retrieval, IP addresses, mailing addresses and download history. "The majority of the people hacked - more than 2.2 million parents and nearly 2.9 million kids - are in the U.S. The hacks were spread across more than a dozen countries, including France, the U.K. and Germany." [source] | |
W. W. Grainger, Inc. had a data breach in 2017, in California. On April 10, 2018, Grainger as notified by [24]7.ai that [24]7.ai was involved in a cyber incident, during which time, credit card information of those conducting business with certain [24]7.ai clients, including Grainger, may have been accessed. Customers who used guest check out and manually entered credit card information on Grainger.com or its app were potentially affected. Information includes credit card numbers, security codes, card expiration dates, names and addresses. [source] | Walgreens Health Initiative had a data breach in 2009, in Illinois. Names, dates of birth and Social security numbers of roughly 28,000 state retirees were e-mailed to the kentucky Retirement Systems without being properly encrypted for security purposes by its pharmacy benefit provider. The e-mail contained dates of birth, Social Security numbers and health insurance claim numbers but not personal health information. The file contained information only on members who were both Medicare-eligible and used the retiree pharmacy benefit through Walgreens in 2007. [source] | |
Washington Department of Fish and Wildlife had a data breach in 2016, in Washington. About 1.7 million people who bought Washington hunting and fishing licenses before mid-2006 have been notified that their personal information may have been exposed earlier this year to a hacker who gained unauthorized access to a data base maintained by the state's license vendor. Customers' personal information included their names; addresses; birthdates; driver's license numbers (customers had the option of providing this information)and related details such as height, weight, and eye/hair color; and the last four digits of Social Security numbers (the other five Social Security numbers were encrypted). No credit card or other financial data was exposed. [source] | We End Violence, LLC had a data breach in 2015, in California. [source] | |
We Heart It had a data breach in 2017, in California. [source] | Web.com had a data breach in 2015, in Florida. Web.com notified customers of a data breach to their systems, when hackers were able to infiltrate their system gaining personal information of customers.The information included credit card numbers, names, addresses, card validation numbers and the security codes associated with the credit cards.The CEO of Web.com put out a statement regarding the breach. [source] | |
Weebly had a data breach in 2016, in California. Weebly, a San Francisco-based company that has allowed more than 40 million people create websites with since 2007; will start sending notification letters to all of their customers on Thursday, informing them of a data breach that occurred eight months ago.The breach, affecting 43,430,316 customers, happened February 2016, but the root cause remains unknown. The compromised database is just now coming to the public's attention after an anonymous source sent it to LeakedSource.The information compromised included email addresses, usernames, IP addresses and passwords. [source] | WellCare Health Plans Inc. had a data breach in 2008, in Georgia. [source] | |
WellCare Health Plans had a data breach in 2014, in New York. 500 Monroe County residents were notified by WellCare Health of disclosure of some of their personal information when their Medicare records were "mishandled" by a sub-contractor for the insurer.The insurers vendor had an error in their computer coding causing denial letters to be sent to the wrong members. The information on the letters included names, addresses, member ID numbers and general descriptions of the procedure. According to the insurer, no Social Security numbers or financial information was disclosed in the letter. [source] | WellPoint, Inc. had a data breach in 2012, in Indiana. A hacking or IT incident that occurred or was discovered around November 3, 2009 resulted in the possible exposure of protected health information on a network server. The incident was reported by HHS on August 6, 2010. [source] | |
WellPoint had a data breach in 2008, in Indiana. [source] | WellPoint's Empire Blue Cross and Blue Shield unit in NY had a data breach in 2007, in Indiana. An unencrypted disc containing patients names, Social Security numbers, health plan identification numbers and description of medical services back to 2003 was lost en route to a subcontractor. uPDATE (3/14/07): The subcontrator reported that the CD that was reported missing on Feb. 9 has been found. [source] | |
Wells Fargo had a data breach in 2017, in California. The information was breached via Paper/Films. [source] | Wendy's had a data breach in 2016, in Ohio. On December 22 of 2010, Wentworth became aware of a breach that left sensitive student information online. A file was accidentally placed on Wentworths website at some point. Current and former students may have had their names, Social Security numbers, dates of birth and medical information exposed. [source] | |
Westlake Touchless Car Wash had a data breach in 2017, in California. [source] | Whiting Turner Contracting had a data breach in 2016, in Maryland. Whiting-Turner notified customers of a data breach when a thirs party vendor that they use had a data breach. "Whiting-Turner uses an outside vendor to provide tax filing and information services, including preparation of our employees' W-2 and 1095 tax forms. On March 8, 2016, this vendor notified us they had detected suspicious activity on their systems. We also received reports around that time from some of our employees regarding fraudulent tax filings in their names." The information compromised included names, dates of birth, and Social Security number of any minor dependent. [source] | |
Whole Foods had a data breach in 2017, in Texas. [source] | Wilderness at the Smokies had a data breach in 2015, in Tennessee. On November 3, 2015, Wilderness at the Smokies discovered that sophisticated malware may have been placed on certain computer systems used at the Wilderness at the Smokies to process credit and debit cards. Following this discovery, Wilderness at the Smokies launched an in-depth investigation to determine what happened and what information was affected. After extensive investigation, forensic investigators determined that credit and debit cards used at the Wilderness at the Smokies onsite food beverage outlets, attractions and retail locations between February 18, 2015 and March 10, 2015 were being collected by the malware. The cardholder data that may be at risk as a result of this incident includes name, card number, expiration date, and CVV. The systems used to process credit and debit cards to reserve and pay for hotel stays were not affected. [source] | |
WildWater Express Carwash had a data breach in 2017, in California. [source] | Willis North America Inc. had a data breach in 2014, in Tennessee. [source] | |
Wilshire Mutual Funds had a data breach in 2014, in Missouri. Wilshire Mutual Funds informed customers of a data breach that took place on March 13, 2014. It was brought to the company's attention that a copy of individuals 1099-Div tax form was sent by fax to an incorrect shareholders in error. The information contained on the 1099-Div form included registered owner's names, the registration of the mutual fund account, the addresses of record, the last 4 digits of the Social Security numbers, the fund and account numbers assigned in their recordkeeping system, the taxable amounts, and the Payer's (Wilshire Equity Fund) Federal ID number. [source] | Wishbone had a data breach in 2017, in California. The information was breached via Paper/Films. [source] | |
Word Press had a data breach in 2015, in California. The information was breached via Email. [source] | WP Technology Inc. dba Wattpad had a data breach in 2015, in Ontario. [source] | |
Wyoming Department of Health Kid Care CHIP had a data breach in 2010, in Wyoming. Applicants of the Wyoming Kid Care CHIP program had their information exposed online. Family home addresses and the Social Security numbers of children involved were available to the general public via a Google search. [source] | Xero had a data breach in 2015, in California. The information was breached via Desktop Computer, Email, Laptop, Network Server, Other, and Other Portable Electronic Device. [source] | |
XOS Technologies d/b/a XOS Digital, Inc. had a data breach in 2017, in Massachusetts. In 2017 XOS Technologies d/b/a XOS Digital, Inc. suffered a data breach affecting 10 records incl. account user names and passwords [source] | Yahoo had a data breach in 2016, in California. Federal investigators say two women orchestrated an identity theft ring that targeted at least 20 people. But it's how suspects Jamila Williams-Stevenson and Loretta Coburn are said to have gotten some of their victim's personal information that is most shocking.Authorities said several of the alleged victims had been patients at Yale-New Haven Hospital where Williams-Stevenson was working as a companion or sitter.According to a court affidavit, once the two changed their alleged victims addresses, they took control of their mail, then took control of their finances.[source] | |
Yahoo had a data breach in 2016, in California. Yahoo is poised to confirm a massive data breach of its service, according to several sources close to the situation. The company was the victim of hacking that has exposed several hundred million user accounts. While sources were unspecific about the extent of the incursion, since there is the likelihood of government investigations and legal action related to the breach, they noted that it is widespread and serious. Earlier this summer, Yahoo said it was investigating a data breach in which hackers claimed to have access to 200 million user accounts and one was selling them online. [source] | Yandy.com had a data breach in 2014, in Arizona. [source] | |
Yap Stone Payment Systems had a data breach in 2015, in California. [source] | Yellowfront Grocery had a data breach in 2015, in Maine. Yellowfront Grocery has notified customers of a databreach when malware was discovered on the POS system called CSTARS of Maine, compromising customers debit and credit card statements. The grocery company is sure that the card numbers were compromised but it is still unclear whether or not additional information was stolen. CSTARS reported that card numbers and expiration dates were stolen and no other information was compromised. CSTARS is communicating that the hackers were able to gain access through "compromised LogMeIn credentials. "Authorities believe that cards used at the store between August 11, 2015 to October 16, 2015 are at risk of being compromised. The local branch of First Bancorp and Damariscotta Bank & Trust are replacing nearly 2,000 cards and 1,000 cards, respectively, in relation to the breach. [source] | |
Zazzle Inc. had a data breach in 2016, in California. Our Security Team detected some unauthorized login attempts to Zazzle accounts, including on using your Zazzle username (email address) and password. Given the nature of the incident, Zazzle believes that the usernames and passwords used in the incident, including yours, were obtained from a data breach of some other website.More Information: https://oag.ca.gov/ecrime/databreach/reports/sb24-63988 [source] | Zest Dental Solutions had a data breach in 2017, in California. [source] | |
Zymo Research had a data breach in 2017, in California. On or about August 2, 2017, Zymo Research Corporation ("Zymo") discovered that its external cloud e-commerce network may have been accessed by an unknown actor. The unauthorized access appears to have occurred on or about March 15, 2017. In particular, the unauthorized access occurred when an unknown actor placed code on Zymo’s system allowing for access to a database containing personal information about its customers.The personal information about Zymo’s customers maintained in the database affected by the unauthorized access included first and last names; physical addresses; email addresses as well as hashed passwords; and credit card information, including credit card number, card verification code, and expiration date. [source] | ||