Documenting all the places
personal data goes.
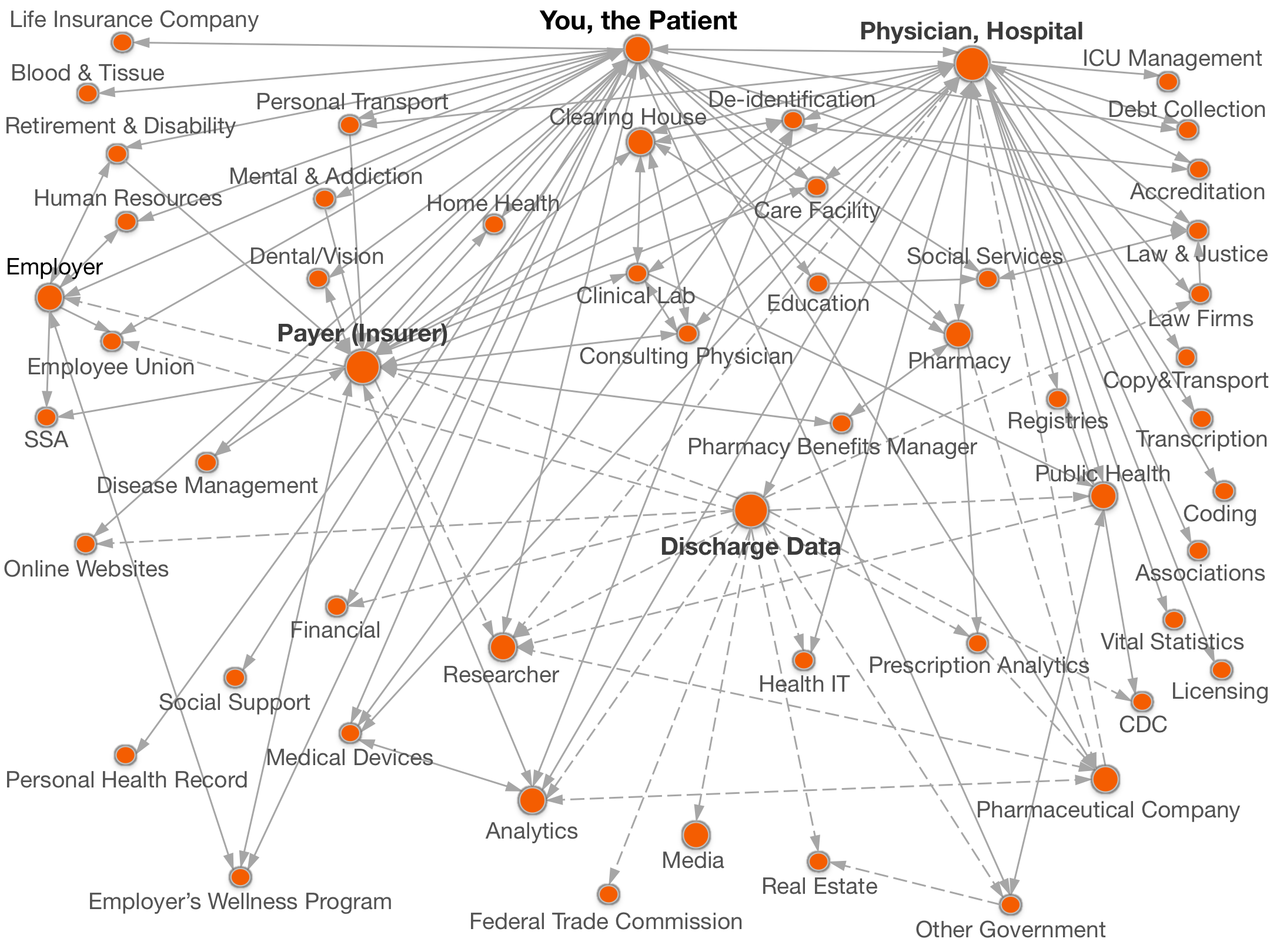
Legend:  with your name,
with your name, without your name.
without your name.
Click on a circle above for names of organizations and details of data shared.
Hospital consortiums or entities authorized by the state receive patient health data from providers (e.g., hospitals and physicians) and distribute that information to researchers, analytic companies, prescription analytic companies, public health departments, the CDC, health payers, other government entities, health information technology companies, the FTC, online websites, employee unions and providers.
States and hospital consortiums receive patient health data from providers and in many states make that data publicly available (usually by legislative mandate) once certain identifiers like patient name and birthdate have been removed or made less detailed. For information on which states share patient data and the amount of identifiable information they provide, see State Survey Maps, Demographic Info, Admit-Discharge Info, HIPAA Equivalence, and Costs.
For a demonstration of how to put personal names to this kind of data, see Risks.
Examples
Alaska State Hospital and Nursing Home Association collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Arizona Department of Health Services collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Arkansas Department of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | California Office of Statewide Health Planning & Development collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Colorado Hospital Association collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Connecticut Office of Health Care Access collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Delaware Health Statistics Center, Division of Public Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | District of Columbia Hospital Association collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Florida Center for Health Information and Policy Analysis collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | GHA: An Association of Hospitals & Health Systems collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Hawaii Health Information Corporation collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Idaho Hospital Association collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Illinois Department of Public Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Indiana Hospital Association collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Iowa Hospital Association collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Kansas Hospital Association collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Kentucky Cabinet for Health and Family Services- Office of Health Policy collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Louisiana Department of Health and Hospitals collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Maine Health Data Organization collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Health Services Cost Review Commission, Maryland State collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Division of Health Care Finance and Policy, Massachusetts State collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Michigan Health & Hospital Association collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Minnesota Hospital Association collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Mississippi Dept of Health, Office of Health Informatics collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Missouri Department of Health and Senior Services collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | MHA - An Association of Montana Health Care Providers collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Nebraska Hospital Association collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Center for Health Information Analysis at University of Nevada at Las Vegas collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
New Hampshire Department of Health & Human Services collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | New Jersey Department of Health & Senior Services collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
New Mexico Department of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | New York State Dept of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Cecil G. Sheps Center for Health Services Research, University of North Carolina at Chapel Hill collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | North Dakota Department of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Ohio Hospital Association collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Oklahoma State Department of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Office for Oregon Health Policy and Research collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Pennsylvania Health Care Cost Containment Council (PHC4) collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Rhode Island Department of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | South Carolina State Budget & Control Board, Office of Research and Statistics collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
South Dakota Association of Healthcare Organizations collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Office of Health Statistics, Tennessee Department of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Texas Health Care Information Collection, Center for Health Statistics, Texas Department of State Health Services collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Office of Health Care Statistics, Utah Department of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Division of Health Care Administration, Vermont State collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Virginia Health Information collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Washington State Department of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | West Virginia Health Care Authority collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Wisconsin Hospital Association collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Wyoming Hospital Association collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
The Agency for Healthcare Research and Quality (AHRQ) is a division of the U.S. Department of Health and Human Services focused on researching public health policy and implementation issues.AHRQ sells and purchases statewide personal hospital discharge data. AHRQ purchased data from at least 3 states: CA, PA, and TX [source]. AHRQ also sells statewide personal hospital discharge data for 23 states through its Federal-State-Industry partnership called the Healthcare Cost and Utilization Project (HCUP). [source] | Clinical Outcomes Assessment Program (Coap) purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Dfwhc Foundation purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Health Market Science purchases statewide personal hospital discharge data from at least CA FL NJ TN WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Hospital Industry Data Institute purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Peardiver Technologies Inc purchases statewide personal hospital discharge data from at least CA WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Strategic Healthcare Measures purchases statewide personal hospital discharge data from at least CA WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | University Healthsystem Consortium purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | |
Vaida Health Data Consultants purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | 2020 On-Site Optometry had a data breach in 2017, in Massachusetts. The information was breached via Network Server . [source] | |
7-Eleven, Inc. Comprehensive Welfare Benefits Plan No. 525 had a data breach in 2015, in Texas. The information was breached via Network Server . [source] | Aarow Equipment & Services Inc. had a data breach in 2014, in Maryland. Name, SSN, DOB, DLN were breached via Laptop . [source] | |
AB Acquisition LLC had a data breach in 2014, in Idaho. Credit and debit card info was breached via payment card system . [source] | ABB, Inc. had a data breach in 2017, in North Carolina. The information was breached via Email . [source] | |
Abbott Nutrition had a data breach in 2017, in Illinois. Name, address, payment card info were breached via Website . [source] | ABCD Pediatrics, P.A. had a data breach in 2017, in Texas. The information was breached via Network Server . [source] | |
ABM Parking Services, Inc. had a data breach in 2014, in Maryland. The information was breached via Desktop Computer . [source] | AdminisTEP had a data breach in 2014, in Texas. The covered entity's (CE) print and mail sorting vendor, Administep, improperly stuffed and mailed letters which contained other enrollees' names, addresses, subscriber identifications, claims amounts, and service descriptions. The breach affected approximately 4,469 of the CE's enrollees. The CE provided breach notification to HHS, the media, and affected individuals, and offered individuals free one-year identity theft protection services. In response to the incident, the CE provided evidence that it placed the business associate (BA) responsible for the breach on a corrective action plan which required the BA to complete a documented quality assurance check for each new implementation or modification of a mailing project. This includes administrative sign- offs and ongoing, random audits on a sample of envelopes for each project. [source] | |
Administracion de Seguros de Salud - Triple S Salud Inc (BA) had a data breach in 2014. [source] | Administracion de Seguros de Salud - Triple S Salud Inc (BA) had a data breach in 2014. [source] | |
ADT LLC Group Health & Welfare Plan had a data breach in 2015, in Florida. The information was breached via Network Server . [source] | Adult Internal Medicine of North Scottsdale had a data breach in 2017, in Arizona. The information was breached via Network Server . [source] | |
Advance Rehabilitation & Consulting LTD had a data breach in 2015, in Georgia. On December 30, 2014, the covered entity (CE), Advance Rehabilitation & Consulting LTD, discovered that a port on one of its servers was publically accessible to the Internet and allowed an automated botnet attack to the server. Internal investigation revealed that one spreadsheet from 2009 was accessed, but there was no way of knowing if the spreadsheet was viewed. The spreadsheet contained patients' names, diagnoses, dates of visits, account types, and therapists'/physicians' names for 570 patients. In response to the breach, the CE conducted a security risk analysis and improved deficient areas with a detailed risk management plan. The CE provided breach notification to HHS and affected individuals. OCR provided technical assistance regarding media notification and such notification was made. OCR obtained assurances that the CE implemented the corrective actions listed above.[source] | Advanced Radiology Consultants, LLC had a data breach in 2015, in Connecticut. A patient scheduler of the covered entity (CE), Advanced Radiology Consultants, emailed 754 patients' protected health information (PHI) from her work email account to a personal email account in order to keep a separate record for any performance issues. An additional 100 patients were affected by the breach because the scheduler had access to PHI about them in emails and a USB device (854 total individuals affected). The PHI involved in the breach included patients' names, dates of birth, phone numbers, account balances, insurance information, treatment and examination information, appointment dates and times, appointment notes, and referring physicians' information. Following discovery of the breach, the CE sanctioned the workforce member and requested that she delete the PHI she sent to her personal email account. The CE also provided breach notification to HHS, affected individuals, and the media, and provided individuals with credit monitoring services at no cost. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | |
Advantage Consolidated LLC had a data breach in 2015, in Oregon. In February 2015, the covered entity (CE), Advantage Consolidated, LLC, reported that the access credentials of one of its users were wrongfully, acquired through the use of malicious software that had been installed on the user's computer. The intrusion was detected by the CE's intrusion detection system. The breach affected the e-PHI (names, addresses, DOBs, and SSNs of 151,626 individuals. The CE provided breach notification to HHS, the affected individuals, and to the media. Following the breach, the CE updated its risk analysis and risk management plan and enhanced its electronic and technical security. OCR obtained assurances that the CE implemented the corrective actions noted above.[source] | ADVANTAGE Health Solutions had a data breach in 2016, in Indiana. The information was breached via Network Server . [source] | |
AECOM Technology Corporation had a data breach in 2014, in Maryland. Name, address, ssn, personal bank account info were breached via Website . [source] | AeroCare Holdings had a data breach in 2017, in Florida. The information was breached via Email . [source] | |
Aetna Inc. had a data breach in 2016, in Connecticut. A business associate was present. [source] | Aetna Inc. had a data breach in 2017, in Connecticut. A business associate was not present. [source] | |
Aetna Inc. had a data breach in 2017, in Connecticut. The information was breached via Paper/Films . [source] | Aetna, Inc. had a data breach in 2017, in Connecticut. The information was breached via Network Server . [source] | |
Affinity Health Plan, Inc. had a data breach in 2015, in New York. The covered entity (CE), Affinity Health Plan, Inc., mistakenly sent renewal letters to members that contained a different member's name and address and their children's names and identification numbers and coverage information. The breach affected 497 heads of household and 224 children. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE placed a hold on outgoing bulk mailings. As a result of OCR's investigation, the CE reviewed and revised the organization's mailing procedures to ensure that they comply with minimum necessary standards, and quality standards. The CE also retrained all staff on its updated policies and procedures and on HIPAA safeguards for members' PHI. OCR obtained assurance that the CE implemented the corrective actions noted above. Location of breached information: Paper/Films Business associate present: No [source] | Aflac had a data breach in 2014, in Georgia. Due to a vendor error, the covered entity (CE), Aflac, erroneously sent correspondence containing protected health information (PHI) to the wrong customers, affecting 930 policyholders. The types of PHI included names, policy numbers, types of coverage, employee numbers, and premium amounts, depending on the type of correspondence mailed. In addition, six policyholders' social security numbers were potentially comprised. In response to the breach, the CE retrained employees and revised its impermissible disclosures and safeguard policies. Additionally, the CE sanctioned the manager who led the address standardization project and terminated its contract with all third party vendors and contractors involved in the breach. The CE provided breach notification to HHS, and affected individuals. Media notice was not required because the incident did not involve more than 500 residents in any particular state. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | |
Aflac had a data breach in 2015, in Georgia. [source] | Aflac had a data breach in 2016, in Georgia. Some of the covered entity's (CE) policyholders erroneously received welcome packets in the mail that contained the protected health information (PHI) of other individuals on a summary page. The breach affected 6,166 individuals and the types of PHI involved in the incident included policyholders' names, coverage applied for, premium amounts, whether the applicant was a new employee, codes or names representing employees' departments, and denial or acceptance of insurance coverage. In response to the breach, the CE updated its privacy and security procedures, which included updating its mailing process. The CE installed new printer software on all IT quality assurance (QA) desktops and on additional machines located in the IT QA lab. The CE also purchased and installed new local printers that will allow IT testers and coders to confirm packet accuracy. The CE provided breach notification to HHS, affected individuals, and the media. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | |
Aflac had a data breach in 2018, in Georgia. The information was breached via Email . [source] | Agency for Health Care Administration had a data breach in 2018, in Florida. The information was breached via Email . [source] | |
AHRC Nassau had a data breach in 2016, in New York. The information was breached via Paper/Films . [source] | Airway Oxygen, Inc. had a data breach in 2017, in Michigan. The information was breached via Network Server . [source] | |
Akron General Medical Center had a data breach in 2016, in Ohio. The business associate (BA), Ambucor Health Solutions, filed a separate breach report for an incident also reported by this covered entity, (CE), Akron General Medical Center. OCR obtained a copy of the BA agreement between this CE and BA and a copy of the breach notification letter sent to the affected individuals. This case has been consolidated into the other review of the BA.[source] | Alaska Communications Systems Holdings, Inc. had a data breach in 2014, in Alaska. Name, address, dob, ssn were breached via computer virus . [source] | |
Alaska Orthopedic Specialists, Inc. had a data breach in 2015, in Alaska. A workforce member of the covered entity (CE), Alaska Orthopedic Specialists, impermissibly sent copies of electronic protected health information (ePHI) to a personal email account between December 18, 2014 and April 14, 2015, which potentially affected approximately 553 individuals. The ePHI included demographic, financial and clinical information. The CE provided breach notification to HHS, affected individuals, and the media. The CE established a website, a related call center, and offered identity-theft protection at no charge. After discovering the breach, the CE hired a digital services consultant to investigate the matter and audit the company's computer server and email to identify the scope and content of the breach. The CE issued a “cease and desist” letter to the former employee, demanding that the former employee take steps to secure the information and return it. The CE securely stored its remaining paper records and the computer server containing ePHI. OCR verified that business operations for the sole practitioner were officially dissolved on December 31, 2016. [source] | Albertina Kerr Centers had a data breach in 2014, in Oregon. Thieves took two notebook computers belonging to the covered entity (CE), Albertina Kerr Centers, which contained the electronic protected health information (ePHI) of 1,320 patients. The CE reported the burglary to the local law enforcement, but neither computer was recovered. The computers were encrypted, but certain cache files for email were unencrypted. The types of ePHI involved in the breach included names, addresses, dates of birth, social security numbers, phone numbers, medications, and treatments. The CE provided breach notification to HHS, affected individuals, and the media and posted substitute notice on its website. To prevent a similar breach from happening in the future, the CE enhanced mobile device security and encryption, improved the physical security of its facility, revised its policies and procedures, and retrained its workforce members. OCR obtained assurances that the CE implemented the corrective actions listed. [source] | |
Alere Toxicology had a data breach in 2017, in Massachusetts. The information was breached via Paper/Films . [source] | Alexian Brothers Medical Center had a data breach in 2015, in Illinois. On April 13, 2015, several files containing electronic protected health information (ePHI) were discovered on computers accessible to the public in the medical library at the covered entity (CE), Alexian Brothers Medical Center. The files included the first and last names, medical record numbers, and medication information related to 618 patients, and other clinical information for 14 patients. Approximately 632 individuals were affected by this breach. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach the CE posted signs noting that the computers were “public computers” and not to save files on the device, secured computers so that no data could be saved onto the virtual desktop or the hard drive, and essentially rendered folders as “read only”. The CE also implemented a process to track user access on all but one of the public computers. The CE retrained workforce groups involved in the breach. OCR obtained documented assurances that the CE implemented the corrective actions listed above. [source] | |
Alicia Ann Oswald had a data breach in 2018, in California. The information was breached via Email . [source] | Allergy, Asthma & Immunology of the Rockies, PC had a data breach in 2016, in Colorado. The information was breached via Network Server . [source] | |
Alliance Health Networks, LLC had a data breach in 2016, in Utah. The information was breached via Network Server . [source] | Alliance Workplace Solutions, LLC had a data breach in 2014, in Maryland. Name, dob, ssn, were breached via Laptop . [source] | |
Alliant Health Plans, Inc. had a data breach in 2016, in Georgia. The information was breached via Network Server . [source] | AlliedBarton Security Services LLC had a data breach in 2014, in Maryland. Name, dln, were breached via Desktop Computer . [source] | |
Allina Health System had a data breach in 2017, in Minnesota. The information was breached via Paper/Films . [source] | Allina Health had a data breach in 2015, in Minnesota. The covered entity (CE), Allina Health, erroneously mailed a number of letters to patients about preventative screenings which resulted in individuals receiving a letter and a screening sample collection kit at their address, but labeled with another individual's name. Two business associate (BA) vendors were also involved in processing the mailing. The breach affected approximately 838 individuals and the protected health information (PH)I involved in the breach included individuals' name. Following the breach, the CE immediately ceased mailing preventative screening kits until it was able to complete an investigation to determine the root cause of the breach, which included reviewing its business associate's practices regarding the mailing of the screening kits to ensure it had quality control processes in place and were appropriately followed. The CE also initiated and implemented its incident system to timely and effectively manage the investigation, patient notification, and risk mitigation. The CE provided breach notification to HHS, affected individuals, media outlets, and a Minnesota state senator. The CE engaged an outside vendor to mail the individual notifications and establish a call center to accommodate any patient inquiries. The CE also implemented a new workflow in its mailing processes to reduce the number of manual steps and incorporated an additional quality check so as to reduce the potential for error and to ensure the accuracy of mailing lists. The CE also retrained its employees on safeguarding PHI when mailing correspondence, and verified that its employees received the training. OCR obtained documentation evidencing that the CE implemented the corrective actions listed. [source] | |
AltaMed Health Services Corporation had a data breach in 2014, in California. The information was breached via Desktop Computer, Network Server, and Paper/Films. [source] | Ambucor Health Solutions, an unincorporated division of The ScottCare Corporation had a data breach in 2016, in Delaware. The information was breached via Email and Other Portable Electronic Device . [source] | |
Amedisys West Virginia, LLC had a data breach in 2017, in West Virginia. The information was breached via Paper/Films . [source] | Amedisys had a data breach in 2015, in Louisiana. The information was breached via Desktop Computer, Electronic Medical Record, Laptop . [source] | |
American Athletic Conference had a data breach in 2014, in Maryland. Name, ssn, address, email address, phone number, dob, were breached via Website. [source] | American Family Care, Inc. had a data breach in 2014, in Alabama. On July 17, 2014, two password-protected, unencrypted laptop computers belonging to the covered entity (CE), American Family Care, were stolen from an employee's vehicle while he was on business travel. The laptops contained the electronic protected health information (ePHI) of 2,500 individuals, and included different types of data for different individuals, such as patients' names, dates of visits, patient identification numbers, social security numbers, dates of birth, and specific health information. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE contacted the local police department and conducted an internal investigation. The CE also revised its HIPAA policies and procedures, retrained its workforce, and encrypted all of its laptops. Location of breached information: Laptop Business associate present: No [source] | |
American Family Care, Inc. had a data breach in 2016, in Alabama. The information was breached via Electronic Medical Record, Other . [source] | American Health Information Management Association (AHIMA) had a data breach in 2014, in Maryland. Credit card info was breached via Desktop Computer . [source] | |
American Home Patient had a data breach in 2017, in Tennessee. The information was breached via Desktop Computer . [source] | American Sleep Medicine had a data breach in 2015, in California. The covered entity (CE), American Sleep Medicine of San Diego, California reported a breach of 1,787 individuals' electronic protected health information (ePHI), as a result of a stolen backup computer hard drive. The hard drive contained names, birthdates, medical histories, physicians' names, and study results. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE improved physical safeguards, conducted a new security analysis, revised policies and procedures, and trained its workforce. As a result of OCR's investigation OCR provided technical assistance regarding the HIPAA Security Rule. Location of breached information: Other Business associate present: No [source] | |
American Urgent Care Center, PSC had a data breach in 2017, in Kentucky. The covered entity (CE), American Urgent Care Center, PSC, discovered that, upon her resignation, a former employee took an x-ray logbook on October 28, 2016. The log book contained the names and treatment dates of 822 individuals. Following the breach, the CE revised its policies and re-trained staff, including providers and management. The CE also revised its procedures to eliminate the use of the paper x-ray log book. As a result of technical assistance from OCR, the CE provided breach notification to HHS, to affected individuals, and in the local newspaper. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Other Business associate present: No [source] | Amerigroup Texas, Inc. had a data breach in 2014, in Virginia. The information was breached via Paper/Films . [source] | |
Ameriprise Financial Services, Inc. had a data breach in 2014, in Minnesota. Name, dob, ssn, account number, address were breached via Desktop Computer . [source] | Amida Care had a data breach in 2017, in New York. The information was breached via Paper/Films . [source] | |
Amsterdam Nursing Home Corporation (1992) had a data breach in 2015, in New York. OCR opened an investigation of the covered entity (CE), Amsterdam Nursing Home Corporation (1992), after it reported that on January 31, 2015, some of its protected health information (PHI) stored at its business associate (BA), Citistorage, LLC, may have been impermissibly disclosed during efforts to extinguish a fire. The incident affected 621 individuals. The typed of PHI involved in the breach included residents' names, addresses, dates of birth, health insurance information, social security numbers, and information about health status and treatment. The CE provided breach notification HHS, affected individuals, and the media and posted a substitute notification on its website. As a result of OCR's investigation, the CE recorded the impermissible disclosure of the affected individuals' PHI for accounting of disclosure purposes, reminded the BA of its notification obligations as set forth in the BA agreement, and obtained written assurances from the BA that the BA is in compliance with all relevant building and safety codes. The CE also re-issued HIPAA-compliant breach notification letters to the affected individuals residing in Massachusetts. [source] | Anderson & Murison, Inc. had a data breach in 2014, in Maryland. Name, dob, dln,address were breached via Website . [source] | |
Anne Arundel Health System had a data breach in 2015, in Maryland. The information was breached via Paper/Films . [source] | Anthem (Working file) had a data breach in 2015, in Indiana. The information was breached via Network Server . [source] | |
Anthem, Inc. Affiliated Covered Entity had a data breach in 2015, in Indiana. The information was breached via Network Server . [source] | Anthem, Inc. had a data breach in 2016, in Indiana. The covered entity's (CE) employee emailed protected health information (PHI) to himself, claiming it was for commission reconciliation purposes. The CE ensured that all the PHI was deleted from the employee's home computer and smart phones. The employee resigned from the company, and attested that all PHI was deleted from his devices. The CE provided breach notification to HHS, affected individuals, and the media and substitute notice was posted on the CE's websites on October 29, 2016, and will remain posted through January 27, 2017. To prevent a similar breach from happening in the future, the CE retrained its Medicare sales workforce, took steps to ensure that the former employee can no longer work or sell the CE's products, and changed its commission statement to reflect only the minimum necessary PHI. OCR obtained written assurances that the CE implemented the corrective actions listed above. [source] | |
Apex EDI, Inc. had a data breach in 2017, in Utah. The information was breached via Network Server . [source] | APi Group, Inc. had a data breach in 2014, in Maryland. Name, ssn, dob were breached via Email . [source] | |
Appalachian Gastroenterology, P.A. had a data breach in 2016, in North Carolina. The information was breached via Network Server . [source] | Apple Valley Care Center had a data breach in 2014, in California. The information was breached via Network Server . [source] | |
Apria Healthcare had a data breach in 2016, in California. The information was breached via Email . [source] | Area Agency of Aging 1-B had a data breach in 2017, in Michigan. The information was breached via Email . [source] | |
Arizona State Retirement System had a data breach in 2014, in Maryland. Name and ssn were breached via Portable device . [source] | Asante had a data breach in 2016, in Oregon. The information was breached via Electronic Medical Record . [source] | |
Ascena Retail Group, Inc. had a data breach in 2014, in Maryland. Email address and ssn were breached via Website . [source] | Ashland Women's Health had a data breach in 2017, in Kentucky. The information was breached via Network Server . [source] | |
Aspire Home Care and Hospice had a data breach in 2015, in Oklahoma. The information was breached via Email . [source] | Aspire Indiana, Inc. had a data breach in 2015, in Indiana. The information was breached via Laptop . [source] | |
Assisted Living Concepts, LLC had a data breach in 2014, in California. Names, address, DOB, ssn were breached via Website . [source] | Associated Catholic Charities Incorporated had a data breach in 2017, in Maryland. The information was breached via Email . [source] | |
Associated Dentists had a data breach in 2015, in Minnesota. The information was breached via Laptop . [source] | Associates In EyeCare, P.S.C. had a data breach in 2016, in Kentucky. An office of the covered entity (CE), Associates in EyeCare, P.S.C., was broken into and two laptop computers and an external hard drive were stolen. The breach affected 971 individuals and the types of protected health information (PHI) involved in the breach included patients' names, internal account numbers, optical images, technical information about the images, and dates of birth. The CE provided timely breach notification to HHS, affected individuals, and the media. The CE also posted notification about the breach to its website. In response to the breach, the CE changed the exterior locks on the clinic doors, revised its policies for moving laptops between offices, began saving all patient information to the cloud, and equipped its new laptop with encryption and physical security. Further, CE revised its security policies. OCR obtained assurances that the CE will train its employees on its updated policies. [source] | |
Associates in Psychiatry and Psychology had a data breach in 2018, in Minnesota. The information was breached via Network Server . [source] | Astadia, Inc. had a data breach in 2017, in Florida. Name, address, ssn, w2 tax info were breached via Website . [source] | |
AT&T Group Health Plan had a data breach in 2015, in Texas. The information was breached via Network Server . [source] | AT&T had a data breach in 2014, in Maryland. Name, ssn, dob were breached via Desktop Computer . [source] | |
Atchison Hospital Association had a data breach in 2018, in Kansas. The information was breached via Network Server . [source] | Athens Orthopedic Clinic, P.A. had a data breach in 2016, in Georgia. The information was breached via Electronic Medical Record . [source] | |
Athletes' Performance Los Angeles, LLC had a data breach in 2016, in Arizona. The information was breached via Laptop . [source] | ATI Holdings, LLC and its subsidiaries had a data breach in 2018, in Illinois. The information was breached via Email . [source] | |
ATI Holdings, LLC and its subsidiaries had a data breach in 2018, in Illinois. The information was breached via Email . [source] | Atlantic Automotive Corp. DBA MileOne, Inc. had a data breach in 2014, in Maryland. The information was breached via Email . [source] | |
Atlantic Digestive Specialists had a data breach in 2017, in New Hampshire. The information was breached via Network Server . [source] | Aultman Hospital had a data breach in 2018, in Ohio. The information was breached via Email . [source] | |
Aurora Health Care, Inc. had a data breach in 2016, in Wisconsin. The information was breached via Network Server . [source] | Austin Pulmonary Consultants had a data breach in 2016, in Texas. The information was breached via Paper/Films . [source] | |
Autism Home Support Services had a data breach in 2016, in Illinois. The covered entity's (CE) employee disclosed protected health information (PHI) to a university practicum student who contacted individuals by email to ask if they would like to participate in a survey related to autism. The PHI involved in the breach included the demographic information of approximately 533 individuals. The CE provided breach notification to HHS and affected individuals. Following the breach, the CE sanctioned and re-trained the involved employee and confirmed that the practicum student destroyed the PHI received. OCR obtained documentation that the CE implemented the corrective actions listed above. [source] | AutoNation, Inc. had a data breach in 2014, in Florida. The information was breached via Website. [source] | |
Backcountry Gear had a data breach in 2014, in Maryland. Name, address, and credit/debit info were breached via payment card system . [source] | Bank of America had a data breach in 2014, in Maryland. Name and ssn were breached via Website . [source] | |
Bank of the West had a data breach in 2014, in California. Name and ssn were breached via Website . [source] | Baptist Health and Arkansas Health Group had a data breach in 2015, in Arkansas. [source] | |
Baptist Medical Center South had a data breach in 2014, in Florida. The information was breached via Other Portable Electronic Device . [source] | Baptist Primary Care, Inc. had a data breach in 2014, in Florida. The information was breached via Electronic Medical Record. [source] | |
Barclays Bank Delaware had a data breach in 2017, in Delaware. Name, addrss, payment card number were breached via Website . [source] | Barnes-Jewish Hospital had a data breach in 2018, in Missouri. The information was breached via Network Server . [source] | |
Barnes-Jewish St. Peters Hospital had a data breach in 2018, in Missouri. The information was breached via Network Server . [source] | Barrington Orthopedic Specialists, Ltd had a data breach in 2015, in Illinois. On August 18, 2015, an employee of the covered entity (CE), Barrington Orthopedic Specialists, Ltd., discovered that a laptop and an electromyography (EMG) machine were stolen from her vehicle. The laptop and the EMG machine contained the names, dates of birth, and clinical and demographic information of approximately 1,009 individuals. The CE provided breach notification to HHS, affected individuals, and the media. It also filed a police report. To prevent similar breaches from happening in the future, the CE added additional units to its inventory, and stopped transporting EMG machines. The CE also retrained and counseled the employee involved in this matter on its HIPAA policies and procedures. OCR obtained and reviewed documentation that substantiates all the CE's actions taken in response to the breach incident. [source] | |
Bartell Hotels had a data breach in 2014, in Maryland. Name, address, and credit/debit card info were breached via payment card system . [source] | Baxter Healthcare had a data breach in 2016, in Illinois. [source] | |
Baxter Regional Medical Center - Home Health Facility had a data breach in 2016, in Arkansas. On September 15, 2016, an employee transmitted an email to patients inviting them to participate in a product-specific Patient Advisory Council. The email contained patients' complete email addresses in the “To” field of the email message, so that recipients could see other recipient's email addresses, which may have also included names. Approximately 992 individuals were affected by the breach. The covered entity (CE), Baxter Healthcare, provided breach notification to HHS, affected individuals, and the media, and also filed a police report. To prevent similar breaches from happening in the future, the CE reeducated and counseled the employee involved in this matter on its HIPAA policies and procedures and sanctioned the employee in accordance with its sanctions policy. The CE also provided training to its workforce on its policies and procedures regarding HIPAA, which highlighted the risks involved with emailing protected health information. OCR obtained written assurances that the CE implemented the corrective actions noted above. [source] | Bay Park Hospital had a data breach in 2014, in Ohio. An employee of the covered entity (CE), Bay Park Hospital, accessed the electronic protected health information (ePHI) of 594 individuals without a necessary business reason to do so. The ePHI included names, dates of birth, diagnoses and other clinical information. The CE provided breach notification to HHS, affected individuals, and the media. Upon discovering the breach, the CE questioned the responsible workforce member, who immediately resigned, and retrained its workforce members on its HIPAA policies and procedures. OCR obtained assurances that the corrective actions listed above were completed. [source] | |
Baylor College of Medicine had a data breach in 2015, in Texas. The information was breached via Paper/Films. [source] | baystate family dental inc had a data breach in 2018, in Massachusetts. The information was breached via Paper/Films . [source] | |
Baystate Health, Inc. had a data breach in 2016, in Massachusetts. The information was breached via Email . [source] | Beacon Health System had a data breach in 2015, in Indiana. The information was breached via Email . [source] | |
Beacon Health System had a data breach in 2017, in Indiana. The information was breached via Electronic Medical Record . [source] | Bebe Stores, Inc. had a data breach in 2014, in Maryland. Name, payment card info were breached via Payment card system . [source] | |
Behavioral Health Center had a data breach in 2017, in Maine. The information was breached via Network Server . [source] | BeHealthy Florida, Inc. had a data breach in 2015, in Florida. [source] | |
Belgrade Regional Health Center had a data breach in 2015, in Maine. A business associate (BA), The Snowman Group, working on behalf of the covered entity (CE), Belgrade Health Center, erroneously mailed letters to patients containing the name of another individual due to a printing mistake, affecting 854 individuals. The protected health information involved included names and an indication of a treatment relationship with the CE. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE changed its template for letters to prevent this printing mistake from occurring again. OCR reviewed the BA agreement between the CE and the BA and obtained assurances that the CE implemented the corrective actions noted above. Location of breached information: Paper/Films Business associate present: No [source] | Bell Nursery USA, LLC had a data breach in 2014, in Maryland. The information was breached via Email. [source] | |
Bellevue Hospital Center had a data breach in 2015, in New York. The information was breached via Email . [source] | Benefit Express Services had a data breach in 2014, in Maryland. Name, address, dob, SSN were breached via Email . [source] | |
Benefit Outsourcing Solutions had a data breach in 2018, in Michigan. A business associate was present. [source] | Benesch, Friedlander, Coplan & Aronoff LLP had a data breach in 2017, in Ohio. The information was breached via Paper/Films . [source] | |
Benjamin F. Edwards and Co. had a data breach in 2014, in Maryland. The information was breached via Website. [source] | Berkeley Endocrine Clinic had a data breach in 2016, in California. The covered entity (CE) reported to OCR that it disclosed electronic protected health information (ePHI) when it inadvertently sent a notification to 1,370 individuals without blind copying the recipients. The ePHI involved in the breach included patients' first and last names and email addresses. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE revised administrative procedures for email communications, enhanced technical measures (including encryption for desktop computers), and retrained staff. OCR's investigation resulted in the CE enhancing its practices for safeguarding ePHI. Location of breached information: Email Business associate present: Yes [source] | |
Berkshire Medical Center had a data breach in 2016, in Massachusetts. A former employee of a business associate (BA), Ambucor Health Solutions, stole the protected health information (PHI) of the covered entity's (CE) patients that was contained in a mobile computer drive. The types of PHI involved in the breach included clinical and demographic information such as patients' names, dates of birth, diagnoses, and treatment, and affected1,745 individuals. OCR reviewed the CE's BA agreement and determined that it is compliance with the Privacy Rule. OCR obtained assurances that individuals affected by this breach were notified in accordance with the Breach Notification Rule. [source] | Best Health Physical Therapy, LLC had a data breach in 2016, in Connecticut. A business associate was not present. [source] | |
Billings Clinic had a data breach in 2018, in Montana. The information was breached via Email . [source] | BioIQ Inc. had a data breach in 2018, in California. The information was breached via Email . [source] | |
BioReference Laboratories, Inc had a data breach in 2016, in New Jersey. A business associate was not present. [source] | Birmingham Printing and Publishing, Inc dba Paper Airplane had a data breach in 2014, in Alabama. [source] | |
BJC HealthCare ACO, LLC had a data breach in 2016, in Missouri. The information was breached via Email . [source] | Black Hawk College had a data breach in 2016, in Illinois. A computer server for the covered entity's (CE) reinsurer was infected with ransomware from March 12 to August 8, 2016, making protected health information (PHI) accessible. The PHI included the names, addresses, dates of birth, Social Security numbers, and clinical data pertaining to approximately 1,000 individuals. The CE submitted a breach report to HHS out of caution even though the reinsurer was not a business associate (BA). The CE provided evidence that a BA was not necessary and the disclosures were permitted under HIPAA for health care operations purposes. The reinsurer provided breach notification to the affected individuals and the CE sent notice to the media and posted a substitute notice on its website. The CE also retrained staff and reviewed its BA agreements and its HIPAA policies and procedures. OCR obtained documentation that the CE implemented the actions listed above. Location of breached information: Network Server Business associate present: No [source] | |
Blaine Chiropractic Center had a data breach in 2016, in Minnesota. The information was breached via Email. [source] | Bloom Physical Therapy, LLC dba Physicians Physical Therapy Service had a data breach in 2017, in Arizona. The information was breached via Email . [source] | |
BLUE CROSS AND BLUE SHIELD OF KANSAS CITY had a data breach in 2014, in Missouri. Name, credit card info, bank account info were breached. [source] | BlueCross BlueShield of South Carolina had a data breach in 2016, in South Carolina. [source] | |
Bon Secours Health System Incorporated had a data breach in 2016, in Maryland. The information was breached via Network Server . [source] | Bon Secours Kentucky had a data breach in 2014, in Kentucky. The covered entity (CE), Bon Secours Kentucky, discovered suspicious activity on its billing software from the user account of a former employee. The CE found it had not properly deactivated access, putting at risk the demographic and clinical information of 697 individuals. The CE provided breach notification to HHS, affected individuals, and posted substitute notice on its website. Media notice was not performed because the number of affected individuals in each state was less than 500. In response to the breach, the CE revised its access monitoring policy and centralized its access allowance procedures. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Other Business associate present: No [source] | |
Booking.com had a data breach in 2014, in Maryland. Name, address, and payment card info were breached via payment card system. [source] | Boomerang Tags had a data breach in 2014, in Maryland. The information was breached via Website . [source] | |
Borgess Medical Center d/b/a Borgess Rheumatology had a data breach in 2016, in Michigan. On April 13, 2015, the covered entity (CE), Borgess Medical Center-Borgess Rheumatology, impermissibly disclosed protected health information (PHI) due to an erroneous use of “mail merge,” which mixed up 700 patients' names and addresses. The PHI involved in the breach included patients' names, medications, and their association with Borgess Rheumatology as patients. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE implemented a new process that included verification of the data files used for mail merges, including a Privacy Officer review. It also trained workforce members and added an informal quality check of spreadsheets involving patient information. OCR obtained documented assurances that the CE implemented the corrective actions noted above. Location of breached information: Paper/Films Business associate present: No [source] | Boston Baskin Cancer Foundation had a data breach in 2015, in Tennessee. Name, address, ssn, and w2 tax info were breached. [source] | |
Bostwick Laboratories had a data breach in 2017, in Virginia. Name, address, ssn, w2 tax info were breached via Email . [source] | Bozeman Health Deaconess Hospital had a data breach in 2016, in Montana. Due to a misaligned spreadsheet, on or about February 19, 2016, Executive Services, a business associate (BA) of the covered entity (CE), Bozeman Health Deaconess Hospital, erroneously sent letters to 1,124 patients containing the another patient's name. The type of protected health information (PHI) involved in the breach included names. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE implemented a new process for sending mass mailings, required the responsible employee, as well as managers and supervisors, to attend HIPAA refresher training, and required the responsible employee to take a class on specific spreadsheet software. OCR obtained assurances that the CE implemented the corrective actions noted above. Location of breached information: Paper/Films Business associate present: No [source] | |
Brandywine Pediatrics, P.A. had a data breach in 2016, in Delaware. The information was breached via Network Server . [source] | Braun Dermatology & Skin Cancer Center had a data breach in 2017, in District Of Columbia. The information was breached via Email . [source] | |
Braun Internal Medicine, P.C. had a data breach in 2017, in Georgia. The information was breached via Email . [source] | Brevard Physician Associates had a data breach in 2017, in Florida. The information was breached via Desktop Computer . [source] | |
Briar Hill Management had a data breach in 2016, in Mississippi. The information was breached via Desktop Computer, Laptop, and Network Server. [source] | Bridget P Early MD LLC d/b/a Namaste Health Care had a data breach in 2017, in Missouri. The information was breached via Network Server . [source] | |
Briggs & Stratton Corporation had a data breach in 2017, in Wisconsin. The information was breached via Desktop Computer, Laptop, Network Server. [source] | Brigham and Women's Hospital had a data breach in 2014, in Massachusetts. An employee of the covered entity (CE), Brigham & Women's Hospital, had an encrypted laptop and cell phone stolen during an armed robbery and was forced to disclose password and encryption keys during the robbery. The devices contained the protected health information PHI) of 999 individuals. The types of PHI involved in the breach included names, medical records numbers, age, and diagnostic information. In response to OCR's investigation, the CE initiated a new enterprise wide risk analysis. Location of breached information: Laptop, Other Portable Electronic Device Business associate present: No [source] | |
Brigham and Women's Hospital had a data breach in 2016, in Massachusetts. The information was breached via Email . [source] | Bronson Healthcare Group had a data breach in 2017, in Michigan. The information was breached via Email . [source] | |
Bryan Myers, MD PC, Ashley DeWitt, DO PC, Michael Nobles, MD PC had a data breach in 2016, in Tennessee. The information was breached via Network Server . [source] | BUFFALO HEART GROUP had a data breach in 2015, in New York. The information was breached via Electronic Medical Record . [source] | |
Bulloch Pediatric Group, LLC had a data breach in 2014, in Georgia. The covered entity (CE), Bullock Pediatric Group, LLC, rented two locked storage units from a facility that was burglarized for its metal shelves. Boxes containing the protected health information (PHI) of approximately 10,000 individuals were strewn about on the floor along with the documents in the boxes. The documents contained demographic, financial, and clinical information, including Explanation of Benefits (EOB) forms from insurance companies, cleared checks, credit card information, balance sheets, end of day reports, some social security numbers, and possibly names and addresses. The CE provided breach notification to HHS, affected individuals, and the media, and posted notification on its website. It also offered one year of free credit monitoring. Following the breach, the CE moved its documents to another storage facility with improved safeguards. In addition, the CE destroyed documents pursuant to the state medical record retention laws. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | Burlington Northern Santa Fe Group Benefits Plan had a data breach in 2014, in Texas. The information was breached via Email. [source] | |
Burrell Behavioral Health had a data breach in 2016, in Missouri. The information was breached via Email . [source] | c3controls had a data breach in 2014, in Maryland. Name, billing address, credit card info were breached via Website . [source] | |
California College of Arts had a data breach in 2018, in California. The information was breached via Laptop . [source] | California Correctional Health Care Services had a data breach in 2016, in California. The information was breached via Laptop . [source] | |
California Pacific Orthopaedics and Sports Medicine had a data breach in 2014, in California. The information was breached via Laptop and Paper/Films . [source] | California Physicians' Service d/b/a Blue Shield of California had a data breach in 2015, in California. Name, ssn, address were breached. [source] | |
Calypso St. Barth, Inc. had a data breach in 2014, in Maryland. Name and credit card info were breached. [source] | Camas Center Clinic, Kalispel Tribe of Indians had a data breach in 2016, in Washington. The information was breached via Desktop Computer, Paper/Films. [source] | |
Cambridge Health Alliance had a data breach in 2018, in Massachusetts. A business associate was not present. [source] | Camelback Women's Health had a data breach in 2015, in Arizona. In early September 2015, the covered entity (CE), Camel Back Women's Health, discovered that a former employee retained of copies 1,564 patients' documents to solicit the CE's patients for her own practice. The types of protected health information (PHI) in the documents included names, addresses, social security numbers, dates of birth, diagnoses and medical conditions, medications, and other treatment information. The CE provided breach notification to HHS, affected individuals, and the media. In response to the breach, the CE asked the former nurse practitioner to return and/or destroy all of its patients' PHI in her possession and hired a lawyer to ensure that the former employee signed an affidavit and return all of the documents. Additionally, the CE revised policies and procedures and retrained workforce members. The CE also provided OCR with additional documentation including its HIPAA Notice of Privacy Practices Policy, as relevant to this breach investigation. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | |
Camp Bow Wow Franchising, Inc. had a data breach in 2014, in Maryland. Name, address, ssn, financial account info, routing numbers were breached via Website . [source] | Cancer Specialists of Tidewater had a data breach in 2014, in Virginia. The information was breached via Paper/Films. [source] | |
Capital Digestive Care, Inc. had a data breach in 2018, in Maryland. A business associate was present. [source] | Capital District PhysiciansŠ—_'Ü'‚ Health Plan had a data breach in 2018, in New York. The information was breached via Paper/Films . [source] | |
Capital Nephrology had a data breach in 2017, in Maryland. The information was breached via Electronic Medical Record, Network Server. [source] | Capitol Administrators, Inc had a data breach in 2018, in California. The information was breached via Email . [source] | |
Capitol Anesthesiology Association had a data breach in 2018, in Texas. The information was breached via Network Server . [source] | Cardiology Associates of Jonesboro, Inc. had a data breach in 2016, in Arkansas. The information was breached via Paper/Films . [source] | |
Cardiology Associates had a data breach in 2016, in Maryland. [source] | Cardiology Center of Acadiana had a data breach in 2017, in Louisiana. The information was breached via Network Server . [source] | |
Care Advantage, Inc. had a data breach in 2014, in Virginia. The information was breached via Network Server. [source] | Care Partners Hospice and Palliative Care had a data breach in 2018, in Oregon. The information was breached via Email . [source] | |
CareAll Management, LLC had a data breach in 2014, in Tennessee. A business associate was not present. [source] | CareCentrix, Inc. had a data breach in 2014, in Maryland. Name, address, dob, ssn, health plan numbers were breached via Desktop Computer . [source] | |
Career Education Corporation had a data breach in 2015, in Illinois. The information was breached via Network Server . [source] | CareFirst BlueCross BlueShield had a data breach in 2014, in Maryland. Information was inadvertently emailed . [source] | |
CareFirst BlueCross BlueShield had a data breach in 2014, in Maryland. Name and ssn were breached via Paper . [source] | CareFirst BlueCross BlueShield had a data breach in 2015, in Maryland. The information was breached via Network Server . [source] | |
CareFirst BlueCross BlueShield had a data breach in 2018, in Maryland. The information was breached via Email . [source] | CareMeridian, LLC had a data breach in 2018, in Massachusetts. The information was breached via Other Portable Electronic Device . [source] | |
CarePlus Health Plan [case #HU1800066] had a data breach in 2018, in Kentucky. The information was breached via Paper/Films . [source] | CarePlus Health Plans [case 18772] had a data breach in 2015, in Kentucky. [source] | |
Caring for Women, PA had a data breach in 2016, in Texas. An employee of FTGU Medical Consulting, LLC (FTGU) sent the electronic protected health information (ePHI) of approximately 700 individuals to an unknown third party. FTGU is a business associate (BA) of Caring for Women, PA, the covered entity (CE). The ePHI included clinical (diagnostic and treatment) information, as well as financial information related to billing. The BA discovered the breach when the recipient of the ePHI notified the BA that he was not the intended recipient. The BA requested that the recipient delete the ePHI file from his email and his computer and received assurances from the recipient that he would comply with this request. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE provided the BA with additional training. In addition, the BA took steps to increase or implement technological safeguards, implement periodic evaluations, and retrain employees. OCR also verified that the CE had a proper BA agreement in place, which restricted the BA's use and disclosure of PHI and required the BA to safeguard all PHI. [source] | Carmike Cinemas, Inc. had a data breach in 2014, in Ohio. Name, address, ssn were breached via paper . [source] | |
Carolina Digestive Health Associates, PA had a data breach in 2018, in North Carolina. The information was breached via Desktop Computer . [source] | Carolina Oncology Specialists had a data breach in 2017, in North Carolina. The information was breached via Electronic Medical Record . [source] | |
Carolyn B Lyde, MD, PA had a data breach in 2015, in Texas. The information was breached via Email. [source] | Catalina Post-Acute Care and Rehabilitation had a data breach in 2017, in Arizona. The information was breached via Paper/Films . [source] | |
Catamaran had a data breach in 2014, in Illinois. [source] | Catholic Charities of the Diocese of Albany had a data breach in 2017, in New York. The information was breached via Network Server . [source] | |
CBS Consolidated, Inc. had a data breach in 2017, in Nebraska. The information was breached via Network Server . [source] | CCRM Minneapolis, P.C. had a data breach in 2017, in Minnesota. The information was breached via Network Server . [source] | |
CDC/NIOSH World Trade Center Health Program (WTCHP) had a data breach in 2015, in Georgia. On February 5, 2015, a remittance advice report containing the health services and financial information of approximately 958 individuals was ripped open while at the U.S. postal office, improperly disclosing the individuals' protected health information (PHI), including patients' names, member numbers, services rendered, dates of service, and provider information. The postal office rewrapped the remaining pages from the package, and delivered them to a business associate (BA) of the covered entity (CE), World Trade Center Health Program, to which they were addressed. The CE provided breach notification to HHS and affected individuals, but no media notice was required due to the geographic locations of the affected individuals. In response to the breach, the CE revised its HIPAA training program. Additionally, National Government Services, the BA that sent the mailing on behalf of the CE, revised its mailing processes and procedures by using only non-tear envelopes or boxes for future mailings. OCR obtained assurances that the CE implemented the correction actions listed above. [source] | CDC/NIOSH/ World Trade Center Health Program (WTCHP) had a data breach in 2016, in Georgia. The information was breached via Email. [source] | |
Ceaton C Falgiano had a data breach in 2016, in New York. The information was breached via Email . [source] | Cedars-Sinai Health System had a data breach in 2014, in California. [source] | |
CEMEX, Inc. had a data breach in 2015, in Texas. The information was breached via Network Server . [source] | Centegra Health System had a data breach in 2015, in Illinois. The information was breached via Paper/Films . [source] | |
Centene Management Corporation had a data breach in 2015, in Missouri. The information was breached via Paper/Films. [source] | Center for Comprehensive Services, Inc. had a data breach in 2018, in Massachusetts. The information was breached via Other Portable Electronic Device . [source] | |
Center for Minimmally Invasive Bariatric and General Surgery had a data breach in 2016, in Pennsylvania. An employee erroneously emailed a group of 992 patients about a support group and copied other patients so that they were able to see the email addresses of all the other individuals to whom the email was sent. The types of protected health information (PHI) involved in this incident included email addresses and information which may have suggested that the individual was a patient of the covered entity (CE). The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE revised its policies and procedures, attempted to recall the email, and retrained workforce members. OCR obtained assurances that the CE implemented the corrective actions noted above and provided technical assistance on reasonable safeguards. Location of breached information: Email Business associate present: No [source] | Center for Neurosurgical & Spine Disorders, LLC had a data breach in 2016, in Louisiana. The information was breached via Desktop Computer . [source] | |
Center for Sports Medicine and Orthopedics had a data breach in 2018, in Tennessee. The information was breached via Paper/Films . [source] | Centers Plan for Healthy Living had a data breach in 2016, in New York. The information was breached via Laptop . [source] | |
Central Brooklyn Medical Group, PC had a data breach in 2015, in New York. Between January 1, 2015 and April 18, 2015, a physician employed by the covered entity (CE), Central Brooklyn Medical Group, PC, impermissibly disclosed the protected health information (PHI) of approximately 500 patients to his former medical assistants via facsimile on multiple occasions. On one occasion, the physician accidentally transposed digits in the intended facsimile number and disclosed the PHI of 88 patients to an unrelated third party. The types of PHI involved in the breach included patients' names, ages, sex, appointment dates, times and reasons for visits, treating physician's names, and medical conditions. The CE sent breach notification letters to 4,135 patients who had been scheduled to see the physician in the year prior to the breach because the CE could not identify which specific patients were affected; however, they were most likely within this group. The CE also provided breach notification to HHS and the media. Upon discovery of the breach, the CE confirmed the destruction of any PHI possessed by the unrelated third party and the medical assistant and sanctioned the physician. [source] | Central City Concern had a data breach in 2014, in Maryland. Name, dob, ssn, health info were breached via Desktop Computer . [source] | |
Central City Concern had a data breach in 2014, in Oregon. [source] | Central Dermatology Center, P.A. had a data breach in 2014, in North Carolina. The information was breached via Network Server . [source] | |
Central Iowa Hospital Corporation d/b/a Blank Children's Hospital had a data breach in 2017, in Iowa. The information was breached via Paper/Films . [source] | Central Ohio Urology Group, Inc. had a data breach in 2016, in Ohio. The information was breached via Network Server. [source] | |
Central Utah Clinic had a data breach in 2014, in Utah. The information was breached via Network Server . [source] | Centura Health had a data breach in 2014, in Colorado. The information was breached via Email. [source] | |
CenturyLink had a data breach in 2014, in Maryland. [source] | Cerebral Palsy Research Foundation of Kansas, Inc. had a data breach in 2018, in Kansas. The information was breached via Network Server . [source] | |
CFG Community Bank had a data breach in 2017, in Maryland. Name, address, ssn, w2 tax info were breached via Email . [source] | Chadron Community Hospital & Health Services had a data breach in 2017, in Nebraska. The information was breached via Electronic Medical Record . [source] | |
Charles River Medical Associates, pc had a data breach in 2018, in Massachusetts. The information was breached via Other Portable Electronic Device . [source] | Charles Stamitoles had a data breach in 2016, in Florida. The information was breached via Paper/Films . [source] | |
Chase Brexton Health Care had a data breach in 2017, in Maryland. The information was breached via Email . [source] | Chesapeake Regional Medical Center had a data breach in 2018, in Virginia. The information was breached via Other Portable Electronic Device . [source] | |
CHI Franciscan Health Hospice-Tacoma had a data breach in 2016, in Washington. The information was breached via Laptop . [source] | Chicago Yacht Club had a data breach in 2014, in Illinois. Name, address, potentially bank/credit card info were breached via Payment card system . [source] | |
Children's Eyewear Sight had a data breach in 2015, in California. The information was breached via Desktop Computer . [source] | Children's Heart Center had a data breach in 2015, in Nevada. [source] | |
Children's Hospital Colorado had a data breach in 2017, in Colorado. The information was breached via Email . [source] | Children's Hospital Medical Center of Akron had a data breach in 2015, in Ohio. The information was breached via Email. [source] | |
Children's Mercy Hospital had a data breach in 2014, in Missouri. [source] | Children's Mercy Hospital had a data breach in 2017, in Missouri. A business associate was not present. [source] | |
Children's National Medical Center had a data breach in 2015, in District Of Columbia. A former business associate (BA) of the covered entity (CE), Children's Medical Center, Ascend Health System, misconfigured a File Transfer Protocol site (FTP), which may have allowed access from the internet to transcription documents from a number of healthcare entities, including the CE. The breach was discovered in December 2015; however, the CE had ceased doing business with the BA on June 23, 2014. The transcriptions may have contained protected health information including children's names, dates of birth, medications, and attending physicians' names. The CE provided breach notification to HHS, affected individuals, and the media. OCR obtained copies of the notification letters and BA agreement, as well as assurances that the CE implemented the corrective actions listed above. Location of breached information: Network Server Business associate present: No [source] | Children's National Medical Center had a data breach in 2016, in District Of Columbia. [source] | |
ChildrenŠ—_'Ü'‚s National Medical Center had a data breach in 2018, in District Of Columbia. The information was breached via Laptop . [source] | Cigna Home Delivery Pharmacy had a data breach in 2015, in Connecticut. A printing error affected 592 individuals, living in 13 states: The covered entity (CE) printed two customer letters on one sheet of paper (front and back) during a mailing to customers. The protected health information involved in the breach included names, mailing addresses, and medication information. The CE provided breach notification to HHS and affected individuals and provided free credit monitoring services. To prevent a printing error from occurring in the future, the CE implemented a new letter creation procedure. OCR obtained assurances that the CE implemented the corrective actions noted above. Location of breached information: Paper/Films Business associate present: No [source] | |
Cigna had a data breach in 2014, in Connecticut. The information was breached via Paper/Films . [source] | Cigna-HealthSpring had a data breach in 2015, in Tennessee. [source] | |
Citi had a data breach in 2014, in Maryland. The information was breached via Paper . [source] | Citibank, N.A. had a data breach in 2014, in Maryland. Name, banking information were breached via email . [source] | |
Citibank, N.A. had a data breach in 2014, in Maryland. The information was breached via Website . [source] | City of Dallas Fire-Rescue Department had a data breach in 2014, in Texas. Multiple laptop computers containing EKG strips were lost, stolen, or unaccounted for from the covered entity (CE), City of Dallas Fire-Rescue Department. The electronic protected health information (ePHI) on the laptops included EKG strips in addition to the names, addresses, medical history, diagnoses, dates of birth, and the social security numbers of approximately 1,000 individuals. Upon discovering the breach, the CE formed a breach assessment team to review and address investigation findings. The CE provided breach notification to HHS, affected individuals, and the media. The CE improved physical security to address deficiencies within its system. OCR obtained assurances that the CE implemented the corrective actions listed. Location of breached information: Laptop Business associate present: No [source] | |
City of Detroit had a data breach in 2018, in Michigan. The information was breached via Other Portable Electronic Device . [source] | City of Hope had a data breach in 2017, in California. The information was breached via Email . [source] | |
City of Houston Medical Plan had a data breach in 2018, in Texas. The information was breached via Laptop . [source] | City of Philadelphia Fire Department Emergency Medical Services Unit had a data breach in 2015, in Pennsylvania. On Feb 28, 2018, City of Thousand Oaks Financial Department learned that an unauthorized individual may have gained access to the computer used by the City's vendor to process credit card transactions. During the incident, information entered into the City of Thousand Oaks' online payment system (Click2 Gov) between Jan 4 and Jan 10 may be have been accessed. This information may have included name, payment card number and expiration date. [source] | |
ClamCase, LLC had a data breach in 2014, in California. The information was breached via Website . [source] | Clay County Hospital had a data breach in 2014, in Maryland. Name, address, ssn, dob were breached via Email . [source] | |
Cleveland Medical Associates, PLLC had a data breach in 2017, in Tennessee. The information was breached via Network Server . [source] | Clinical Pathology Laboratories Southeast had a data breach in 2017, in Florida. The information was breached via Laptop . [source] | |
Clinical Reference Laboratory, Inc. had a data breach in 2014, in Kansas. [source] | Clinical Reference Laboratory, Inc. had a data breach in 2015, in Kansas. The covered entity (CE), Clinical Reference Laboratory, Inc., sent a parcel which was damaged and opened during the mailing process by the United States Postal Services (USPS). The protected health information (PHI) involved in the breach included the names, dates of birth, partial social security numbers, and lab test types of approximately 979 individuals residing in multiple states. The CE provided breach notification to HHS and affected individuals. Since multiple breach reports have been received involving the same CE and fact pattern, this investigation was consolidated into one investigation. Location of breached information: Paper/Films Business associate present: No [source] | |
Clinical Reference Laboratory, Inc. had a data breach in 2015, in Kansas. The covered entity (CE), Clinical Reference Laboratory, Inc., sent a parcel which was damaged and opened during the mailing process by the United States Postal Services (USPS). The protected health information (PHI) involved in the breach included the names, dates of service, partial social security numbers, and lab test types of approximately 4,668 individuals. The CE provided breach notification to HHS, affected individuals, and the media. Since multiple breach reports have been received involving the same CE and fact pattern, this investigation was consolidated into one investigation. Location of breached information: Paper/Films Business associate present: No [source] | Clinton County Board of Developmental Disabilities had a data breach in 2017, in Ohio. The information was breached via Network Server . [source] | |
Codman Square Health Center had a data breach in 2016, in Massachusetts. A workforce member provided an unauthorized individual with the workforce member's credentials so as to allow the individual access to the New England Health Exchange Network (NEHEN) via computer. The unauthorized individual was thus able to access the protected health information (PHI) of 102 patients of the covered entity (CE), Codman Square Health Center. The types of PHI involved in the breach included patients' names, addresses, birthdates, medical insurance information, and for patients receiving Medicaid, social security numbers. The CE provided breach notification to the affected individuals, the media and HHS. The CE also provided individuals fraud resolution and credit monitoring services at no cost. Following discovery of the breach, the CE sanctioned the involved employees and re-trained all employees. As a result of OCR's investigation, the CE revised its Breach Notification policy and implemented related procedures. [source] | Colorado Department of Health Care Policy & Financing had a data breach in 2014, in Colorado. [source] | |
Colorado Neurodiagnostics, PLLC had a data breach in 2014, in Colorado. An unencrypted laptop computer containing protected health information (PHI) was stolen from Colorado Neurodiagnostics' locked offices on April 25, 2014, affecting approximately 750 individuals. The PHI on the laptop included patients' names, dates of birth, diagnoses, conditions, laboratory results, medications, and treatment information. The covered entity (CE) provided breach notification to affected individuals, the media, and HHS. It also immediately filed a police report and implemented additional physical safeguards. As a result of OCR's investigation and technical assistance, the CE conducted a risk analysis, developed a risk management plan, encrypted its electronic devices containing PHI, and implemented additional technical safeguards. Location of breached information: Laptop Business associate present: No [source] | Colorado River Indian Tribes had a data breach in 2014, in Arizona. Name, address, SSN were breached. [source] | |
Comanche County Hospital Authority had a data breach in 2016, in Oklahoma. A business associate (BA), Avatar Solutions, e-mailed satisfaction surveys for patients who visited Memorial Medical Group, a provider affiliate of the covered entity (CE), Comanche County Hospital Authority, to incorrect e-mail addresses. The surveys contained patients' and providers' names and affected 2,199 individuals. In response to the incident, the BA updated its Security Management Plan, implemented new technical safeguards, applied policy changes to mitigate harm, and implemented training to prevent further incidents. In response to OCR's investigation, the CE provided evidence it provided breach notification to the media and affected individuals and offered affected individuals a year of free credit monitoring and identity theft protection. Location of breached information: Email Business associate present: No [source] | Commonwealth Health Corporation had a data breach in 2017, in Kentucky. A business associate was not present. [source] | |
Community Health Network had a data breach in 2015, in Indiana. On February 2, 2015, the covered entity (CE) learned that one of its facilities was unable to locate a binder containing point-of-care test results. The missing binder was never found. The binder contained the protected health information of approximately 650 individuals. The types of protected health information involved in the breach included names, dates of service, test types, test results, and possibly dates of birth. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE retrained its staff, implemented a new quality control log, and instructed medical practices to store information in its electronic medical record. OCR obtained assurances the CE implemented the corrective actions listed above. Location of breached information: Paper/Films Business associate present: No [source] | Community Health Plan of Washington had a data breach in 2016, in Washington. The information was breached via Network Server and Other. [source] | |
Community Health Plan of Washington had a data breach in 2017, in Washington. The information was breached via Network Server . [source] | Community Health Systems Professional Services Corporation had a data breach in 2014, in Tennessee. The information was breached via Network Server . [source] | |
Community Health Systems Professional Services Corporations had a data breach in 2014, in Tennessee. A business associate was not present. [source] | Community Link Inc had a data breach in 2014, in Wisconsin. The information was breached via Email . [source] | |
Community Memorial Health System had a data breach in 2017, in California. The information was breached via Email . [source] | Community Mercy Health Partners had a data breach in 2015, in Ohio. [source] | |
Community Mercy Health Partners had a data breach in 2016, in Ohio. The information was breached via Paper/Films . [source] | Complete Chiropractic & Bodywork Therapies had a data breach in 2016, in Michigan. On March 7, 2016, the covered entity (CE) discovered a malfunction on certain of its computer workstations. The CE hired a forensic expert who concluded that the CE's server was left vulnerable to access by unauthorized users from November 19, 2015 to March 10, 2016. The types of protected health information (PHI) on the server included patients' full names, social security numbers, dates of birth, home addresses, and treatment notes. Approximately 4,082 individuals were affected by the breach. The CE provided breach notification to HHS, affected individuals, and the media and offered free identity protection for 1 year to the affected individuals. To prevent a similar breach from happening in the future, the CE installed a new firewall to monitor all incoming and outgoing traffic to and from the server. It also hired a new IT vendor and Security Rule experts to enhance safeguards. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | |
Complete Family Foot Care had a data breach in 2016, in Nebraska. The information was breached via Laptop and Paper/Films. [source] | Complete Family Medicine, LLC had a data breach in 2018, in Nebraska. The information was breached via Laptop and Paper/Films . [source] | |
COMPLETE MEDICAL HOMECARE had a data breach in 2014, in Kansas. On December 12, 2013, the covered entity's (CE) business partner, All American Medical Supplies (AAMS) received a portable computer drive containing protected health information (PHI), including electronic copies of medical records from the CE, that was delivered in error. The incident affected approximately 1,700 individuals and the types of PHI included patients' names, addresses, medical diagnoses, and in some cases social security numbers. Although AAMS accessed the portable drive, it subsequently deleted the data and returned the drive to the CE. The CE provided breach notification to HHS and affected individuals. As a result of OCR's investigation, the CE began developing policies and procedures related to breach notification, training, removal of hardware and electronic media, and encryption and decryption of PHI, and indicated that it would train its workforce on the new policies and procedures once they were implemented. On December 5, 2016, the CE's former parent company provided written documentation that the CE legally dissolved on December 23, 2015, and has ceased carrying on business. [source] | Complete Wellness had a data breach in 2017, in Maryland. The information was breached via Other Portable Electronic Device . [source] | |
CompuNet Clinical Laboratories had a data breach in 2015, in Ohio. The information was breached via Paper/Films. [source] | Computer Programs and Systems, Inc. had a data breach in 2014, in Alabama. The information was breached via Network Server . [source] | |
Cone Health Medical Group had a data breach in 2014, in North Carolina. The information was breached via Paper/Films . [source] | Conference USA, Inc. had a data breach in 2014, in Maryland. Name, address, dob, ssn were breached via Website . [source] | |
ConnectiCare had a data breach in 2018, in Connecticut. The information was breached via Paper/Films . [source] | Consolidated Tribal Health Project, Inc. had a data breach in 2015, in California. The information was breached via Desktop Computer, Electronic Medical Record, Email, Laptop, Network Server, and Other Portable Electronic Device. [source] | |
Consultants Choice, P.A. had a data breach in 2017, in Florida. The information was breached via Desktop Computer . [source] | Consultants in Neurological Surgery, LLP had a data breach in 2016, in Florida. The information was breached via Paper/Films . [source] | |
Cook County Health & Hospitals System had a data breach in 2014, in Illinois. A desktop computer was found to be missing on or around November 1. It contained the medical record identification numbers, names, dates of birth, clinic names, physician names, and lab results of some patients. [source] | Cook County Health & Hospitals System had a data breach in 2017, in Illinois. The information was breached via Network Server . [source] | |
Coordinated Health had a data breach in 2014, in Pennsylvania. The information was breached via Laptop . [source] | Coordinated Health Mutual, Inc. had a data breach in 2016, in Ohio. The information was breached via Paper/Films . [source] | |
Cornerstone Foot & Ankle had a data breach in 2018, in New Jersey. The information was breached via Email . [source] | Cornerstone Health Care, PA had a data breach in 2014, in North Carolina. The information was breached via Laptop . [source] | |
Cottage Health had a data breach in 2015, in California. The information was breached via Network Server . [source] | Coulee Medical Center had a data breach in 2014, in Washington. [source] | |
County of Los Angeles had a data breach in 2015, in California. The information was breached via Email. [source] | County of Los Angeles had a data breach in 2016, in California. Paper documents were stolen from an employee car, while off-site. The paper documents contained the protected health information (PHI) of approximately 743 individuals. The types of PHI involved in the breach included first and last names, dates of birth, medical record numbers, telephone numbers, gender information, names of treatment clinics, appointment types, date and time of appointment(s), and reasons for the examination and/or diagnosis. Following the breach, the covered entity (CE) notified local law enforcement and re-trained staff. The CE provided breach notification to HHS, affected individuals and the media. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Paper/Films Business associate present: No [source] | |
Courier Corporation of Hawaii had a data breach in 2015, in Hawaii. [source] | Courier Express/Atlanta, Courier Express/Charlotte & Courier Express US, Inc. had a data breach in 2014, in Georgia. The information was breached via Paper/Films . [source] | |
Cromwell Fire District had a data breach in 2016, in Connecticut. The information was breached via Paper/Films . [source] | Crothall Services Group had a data breach in 2014, in Maryland. Name, dob, ssn were breached via email . [source] | |
Crown Point Health Center had a data breach in 2016, in Indiana. Patients' empty paper file folders with protected health information (PHI) appearing on the front cover were improperly disposed of when an employee put them in the regular trash. The PHI on the cover included patients' dates of birth, medical record numbers, and guarantors' names. Approximately 1,854 individuals were affected by this breach. The covered entity (CE) provided breach notification to HHS, affected individuals and the media. The notification letter informed the individuals that a hotline had been established to address their questions and provided the hotline phone number. To prevent a similar breach from happening in the future, the CE sanctioned the involved employee and counseled the remaining staff regarding this matter. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | Cultivian Ventures, LLC had a data breach in 2014, in Maryland. Name, address, ssn, financial info were breached via Website . [source] | |
CVS Health had a data breach in 2016, in Rhode Island. An individual broke into a CVS Pharmacy in Whiteville, NC during Hurricane Matthew. The thief stole 626 individuals' completed prescriptions. The types of PHI on the prescriptions included names, partial birthdates, addresses, medication names and doses, providers' names, and prescription numbers. The covered entity (CE) provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE assessed the damage and secured the store to prevent any other unauthorized access. OCR reviewed the CE's policies and procedures on uses and disclosure of PHI and safeguarding PHI, and determined that they were in compliance with the Privacy Rule. OCR obtained assurances that the CE implemented the corrective actions noted above. [source] | Cyberswim, Inc. had a data breach in 2014, in Maryland. Name, payment card info, website userName and pw, address were breached via Website. [source] | |
D&J Optical Inc. had a data breach in 2014, in Alabama. In June 2014, the covered entity (CE), D&J Optical, suspected that a former independently contracted optometrist had created credentials for herself and accessed electronic protected health information (ePHI) without authorization. This inappropriate access would have exposed the demographic and clinical information of 1,100 individuals. The CE filed a breach report with HHS and met the requirements of the Breach Notification Rule. In response to this suspected incident, the CE increased security for access to its server and software, eliminated wireless internet capabilities in its office, and strengthened procedures for password access. OCR reviewed evidence of the subsequent investigation by a computer forensic expert which revealed that no inappropriate access had occurred and no ePHI was disclosed. Location of breached information: Desktop Computer Business associate present: No [source] | D. Andrew Loomis MD, Paula Schulze MD,Tammara Stefanelli MD, Christen Vu DO, Anja Crider MD had a data breach in 2017, in Washington. The information was breached via Network Server . [source] | |
Daniel A. Sheldon, M.D., P.A. had a data breach in 2015, in Florida. [source] | Data Media had a data breach in 2014, in Georgia. A business associate was present. [source] | |
DataStat, Inc. had a data breach in 2016, in Michigan. An employee of a business associate (BA), DataStat, erroneously misdirected surveys to 487 individuals after failing to following the BA's re-print protocol after a printer paper jam. The types of protected health information (PHI) involved in the breach included demographic information, including names and addresses. The CE provided breach notification to HHS and affected individuals. The BA also improved technical safeguards to assist with quality assessment checks and sanctioned the involved employee with a written warning. OCR obtained documentation that the BA implemented the corrective actions steps listed above. Location of breached information: Paper/Films Business associate present: Yes [source] | David DiGiallorenzo, D.M.D. had a data breach in 2014, in Pennsylvania. [source] | |
David E. Hansen DDS PS had a data breach in 2015, in Washington. On January 29, 2015, the covered entity (CE), David E. Hansen DDS PS, reported that a password protected computer back-up disk, 20 encrypted flash drives and 32 paper dental patients' records were stolen during a break-in at the CE's facility. The media devices contained the electronic protected health information (ePHI) of approximately 2000 individuals. The PHI involved in the breach included patients' names, diagnoses, medications, and other clinical information. The CE provided breach notification to HHS, affected individuals, and the media. The CE improved physical security and retrained workforce members. OCR obtained assurances that the CE implemented the corrective actions noted above. Location of breached information: Other Portable Electronic Device, Paper/Films Business associate present: No [source] | David Stanley Dodge had a data breach in 2014, in Maryland. On January 7, 2017, our Phoenix office was burglarized and one employee laptop was stolen. We contacted law enforcement and conducted an investigation. What Information Was Involved? The stolen laptop data may have included personal information such as employee, former employees, and their respective dependents from December 2014 to present. Specifically, the information may have included: name, address, social security number, employee identification number, date of birth, and direct deposit bank information. The stolen data may also have included name, address, social security number and date of birth for dependents of the employees and former employees. [source] | |
DaVita Healthcare Partners had a data breach in 2014, in Colorado. Name, ssn, clinical diagnoses, health insurance info, dialysis info were breached via paper . [source] | Dean Health Plan had a data breach in 2015, in Wisconsin. [source] | |
Dean Health Plan had a data breach in 2018, in Wisconsin. The information was breached via Paper/Films . [source] | Decatur County General Hospital had a data breach in 2018, in Tennessee. The information was breached via Network Server . [source] | |
Decatur Health Systems had a data breach in 2016, in Kansas. On 12/08/2017, as a result of insider wrong-doing, Deaconess Hospital suffered a breach that resulted in the exposure of 4 records including Social Security numbers. [source] | Defense Point Security LLC had a data breach in 2017, in Virginia. Name, address, ssn, w2 tax info were breached via Email . [source] | |
Delaware River & Bay Authority had a data breach in 2014, in Delaware. Credit/debit card data and name were breached via payment card system . [source] | Dennis East International, LLC had a data breach in 2014, in Maryland. The information was breached via Website. [source] | |
Dennis Flynn MD had a data breach in 2014, in Illinois. The information was breached via Laptop . [source] | Denton County Health Department had a data breach in 2015, in Texas. On April 9, 2015, OCR received a breach report from the covered entity (CE), Denton County Health Department, stating that on February 15, 2015, an employee used an unencrypted portable computer, to save and print a personal document at FedEx/Kinko's. The mobile drive contained the protected health information (PHI) of approximately 874 individuals from the tuberculosis clinic. The PHI included lab test results, demographic information, and clinical data. Based on the information gathered during the investigation, OCR has opened a compliance review regarding the CE's potential non-compliance with multiple HIPAA standards and is consolidating this investigation with that review. Location of breached information: Other Portable Electronic Device Business associate present: No [source] | |
Desert Care Family and Sports Medicine had a data breach in 2016, in Arizona. The information was breached via Network Server . [source] | Detroit Medical Center - Harper University Hospital had a data breach in 2014, in Michigan. Patients' medical information was found in the possession of an employee who had worked for the covered entity, Detroit Medical Center Harper University. The protected health information (PHI) included the names, dates of birth, age, gender and reasons for visits for approximately 1,087 individuals. The CE provided breach notification to HHS, affected individuals, and the media, and offered one year of credit protection and monitoring service at no cost to all affected patients. OCR obtained documentation which showed that the CE implemented the corrective actions listed. [source] | |
Detroit Medical Center had a data breach in 2017, in Michigan. The information was breached via Desktop Computer, Paper/Films. [source] | Diagnostic Radiology & Imaging, LLC had a data breach in 2018, in North Carolina. The information was breached via Email . [source] | |
Diamond Computing Company had a data breach in 2014, in Georgia. The information was breached via Network Server. [source] | Diamond Institute for Fertility and Menopause, LLC had a data breach in 2017, in New Jersey. The information was breached via Network Server . [source] | |
Diana S. Guth DBA Home Respiratory Care had a data breach in 2015, in California. The information was breached via Paper/Films. [source] | Diatherix Laboratories had a data breach in 2014, in Maryland. Name, ssn, dob, insurance, test information were breached via Website . [source] | |
Digia USA, Inc. had a data breach in 2014, in Maryland. Name, address, dob ssn, health insurance, beneficiary data, DLN, banking data were breached via Laptop . [source] | Dignity Health Medical Foundation had a data breach in 2017, in California. The information was breached via Paper/Films . [source] | |
Dignity Health St. Rose Dominican Hospitals - San Martin had a data breach in 2018, in Nevada. The information was breached via Paper/Films . [source] | Dignity Health St. Rose Dominican Hospitals - Siena had a data breach in 2018, in Nevada. The information was breached via Paper/Films . [source] | |
Dignity Health St. Rose Dominican Hospitals-DeLIma had a data breach in 2018, in Nevada. The information was breached via Paper/Films . [source] | Dignity Health had a data breach in 2018, in California. The information was breached via Email . [source] | |
Dino-Peds had a data breach in 2018, in Colorado. The information was breached via Electronic Medical Record . [source] | Direct Learning Systems, Inc., d/b/a 123ce.com had a data breach in 2014, in Maryland. Names, financial information were breached via Website . [source] | |
District Medical Group, Privacy Manager Breach had a data breach in 2014, in Arizona. On December 12, 2014, the covered entity (CE), District Medical Group, reported that when a workforce member used a thumb drive while working from home the contents of the thumb drive became accessible on the Internet. The media device contained the electronic protected health information (ePHI) of approximately 616 individuals. The PHI involved in the breach included names, addresses, social security numbers, transaction amounts and clinical information. The CE provided breach notification to HHS, the affected individuals and the media. The CE revised its policies and procedures and retrained workforce members. OCR obtained assurances that the CE implemented the corrective actions noted above. Location of breached information: Other Portable Electronic Device Business associate present: No [source] | Doctors First Choice Billings, Inc. had a data breach in 2014, in Florida. A business associate was present. [source] | |
Doctors First Choice Billings, Inc had a data breach in 2014, in Florida. A business associate was present. [source] | Dr. Anthony T. R. Green DDS had a data breach in 2015, in New York. A self-storage facility in Hollis, New York auctioned off the contents of a unit rented by the covered entity (CE) that contained medical records of 8,636 individuals. Ultimately, many of the records were left unattended in a Home Depot parking lot in Jamaica, New York. The protected health information (PHI) involved in the breach included names, dates of birth, addresses, social security numbers, diagnoses, conditions, lab results, and other treatment information. Following the breach, the CE provided breach notification to HHS, affected individuals, and the media, and provided credit and identity theft services to individuals at no cost. The CE also ended its practice of storing patient files outside of the office and implemented policies and procedures that prohibit business associates from having access to PHI before a business associate agreement is in place. OCR obtained assurances that the CE implemented the corrective actions listed above. Additionally, the New York Attorney General and the CE agreed to enter into an Assurance of Discontinuance that requires the CE to take additional corrective actions. [source] | |
Dr. Dennis T. Myers, D.D.S., P.A. had a data breach in 2016, in Missouri. The information was breached via Network Server . [source] | Dr. Melissa D. Selke had a data breach in 2016, in New Jersey. The information was breached via Desktop Computer and Electronic Medical Record. [source] | |
Dr. Q Pain and Spine d/b/a Arkansas Spine and Pain had a data breach in 2016, in Arkansas. A virus or malware was potentially installed on the information systems of Bizmatics, Inc., a business associate (BA) of the covered entity, Arkansas Spine and Pain (CE). Approximately 17,100 individuals' electronic medical records were compromised, but the BA and CE were unable to determine whose records or what information, if any, was accessed. OCR obtained a copy of the BA agreement in place between the CE and this BA. This review has been addressed by a separate review of the BA. Location of breached information: Network Server Business associate present: No [source] | Dr. Veronica Joann Barber had a data breach in 2014, in California. Another provider, Veronica Joann Barber, O.D., (VB) copied the covered entity's (CE) entire data base and used the electronic protected health information (ePHI) to solicit patients for her own practice. VB worked at the CE's office under a space-sharing agreement until the CE terminated the agreement. The CE requested that VB cease and desist using the PHI, but she did not agree. The theft occurred on December 15, 2013, and affected 4,000 individuals. The ePHI involved in the breach included individuals' names, social security numbers, addresses, driver's licenses, dates of births, other identifiers, credit card and bank account numbers, claims information, other financial information, diagnoses and medical conditions, medications, and other treatment information. The CE provided breach notification to HHS and affected individuals. Following the breach the CE installed computer firewalls. Based on OCR's provision of technical assistance, the CE notified the media and completed a risk assessment. It also improved safeguards by denying access by unlicensed persons to its computer systems and updating its policies and procedures regarding computer user names and passwords. The CE improved physical safeguards by moving the computer with the ePHI behind a 5-foot tall counter. [source] | |
Dreslyn had a data breach in 2014, in Maryland. Credit/debit card info were breached via payment card system . [source] | DST Systems, Inc. had a data breach in 2014, in Maryland. Home address and ssn were breached via paper . [source] | |
Duke LifePoint Conemaugh Memorial Medical Center had a data breach in 2015, in Pennsylvania. The information was breached via Portable Electronic Device. [source] | Duluth Pack had a data breach in 2014, in Maryland. Name, address, payment account numbers, email address were breached via Website . [source] | |
Dutch Bros. Coffee had a data breach in 2014, in Maryland. Name, address, and credit card info were breached via Website . [source] | East Bay Perinatal Medical Associates had a data breach in 2015, in California. The information was breached via Laptop . [source] | |
East Central Kansas Area Agency on Aging had a data breach in 2017, in Kansas. The information was breached via Network Server . [source] | East Valley Community Health Center, Inc. had a data breach in 2016, in California. The information was breached via Network Server . [source] | |
Easter Seal Society of Superior California, Privacy Manager Breach had a data breach in 2014, in California. A work-issued laptop computer containing 3,026 clients' protected health information (ePHI) was stolen out of an employee's locked car. The types of ePHI involved in the breach included financial, demographic, and clinical information. The covered entity's (CE) investigation revealed that, although the computer was powered off, password protected and not connected to the internet at the time of the theft, e-mails containing the respective e-PHI could still be accessed. The CE provided breach notification to HHS, affected individuals, and the media, and posted substitute notice on its website. It also provided affected individuals with one free year of credit monitoring and restoration, tips on protecting against ID theft, and a confidential privacy line to call with questions or concerns. Upon learning of the theft, the CE launched an internal investigation, hired specialized data security counsel to assist in responding to the incident, and retained external forensic experts to assist in determining the scope of the breach. The CE improved safeguards by reviewing its privacy and security policies and procedures, implementing a risk mitigation plan that reflects the current work environment, encrypting its laptop computers, and updating its policies and procedures on portable/mobile devices. It also retrained workforce members. OCR provided technical assistance regarding the HIPAA Security Rule requirements and obtained written documentation that the CE implemented the corrective actions listed above. [source] | hi | |
Eastern Maine Medical Center had a data breach in 2018, in Maine. The information was breached via Other Portable Electronic Device . [source] | Echo Canyon Healthcare, Incorporated dba Heritage Court Post Acute of Scottsdale had a data breach in 2018, in Arizona. The information was breached via Paper/Films . [source] | |
Ecolab Health and Welfare Benefits Plan had a data breach in 2016, in Minnesota. The information was breached via Network Server . [source] | EDWARD G. MYERS D.O. INC had a data breach in 2016, in Ohio. The information was breached via Network Server . [source] | |
Edwin Shaw Rehabilitation had a data breach in 2016, in Ohio. On February 19, 2016, an employee of the covered entity (CE), Edwin Shaw Rehabilitation, mistakenly left behind a day planner that contained an unencrypted mobile computer drive (a universal serial bus, or “USB” drive), at a business-related function. The drive contained a spreadsheet file that included the names, medical record numbers, insurance providers' names, and limited clinical information of 975 individuals. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE sanctioned the involved employee, conducted mandatory privacy and security training for all members of its leadership team, and implemented a month-long security awareness campaign for all employees that included HIPAA education and collection of unencrypted USB drives. The CE also deployed new forms for employees to request an encrypted mobile computer drive. OCR obtained written assurances that the CE implemented the corrective actions noted above. [source] | Einstein Healthcare Network had a data breach in 2016, in Pennsylvania. The covered entity (CE), Einstein Healthcare Network, reported that between April 11, 2013 and March 21, 2017, its website, Einstein.edu, contained a webpage form where a visitor could “Request an Appointment” that allowed protected health information (PHI) to be left accessible via the internet, including demographic and clinical information. The CE staff used this data to schedule the requested appointment(s) for patients. The CE learned that it was possible to cause the website to display PHI by submitting an unexpected string of characters in the universal resource locator (URL). Google accessed these specially crafted URL's in order to attempt to add these web pages to the list of pages that can be searched by Google. The CE reviewed the information provided on the forms and determined that it demonstrated a low probability of compromise for most patients. The CE provided breach notification to the remaining 2,034 patients, HHS, and the media. Following the breach, the CE worked with Google to have the information removed from indexing. Subsequently, the CE conducted a system wide risk assessment and penetration test to specifically assess for security vulnerabilities on the website, changed the vendor used for website creation and hosting and built and tested a new "Einstein.edu" website. OCR obtained assurances that the CE implemented the corrective actions listed.[source] | |
Elite Imaging had a data breach in 2016, in Florida. Per Health and Human Services, Elite Imaging notified HHS of a data breach when they discovered paper files had been stolen. What specific personal information was compromised was not communicated. [source] | Elizabeth Kerner, M.D. had a data breach in 2015, in Texas. The information was breached via Desktop Computer. [source] | |
Elliot Health System had a data breach in 2014, in New Hampshire. The information was breached via Desktop. [source] | ELLIOT J MARTIN CHIROPRACTIC PC had a data breach in 2016, in New York. The information was breached via Desktop Computer . [source] | |
Embassy suites had a data breach in 2014, in Tennessee. The information was breached via Paper/Films. [source] | Emblem Health - GHI had a data breach in 2016, in New York. The information was breached via Network Server, Other and Paper/Films. [source] | |
Emblem Health - GHI had a data breach in 2017, in New York. The information was breached via Paper/Films . [source] | Emdeon had a data breach in 2014, in Tennessee. The information was breached via Paper/Films . [source] | |
Emergence Health Network had a data breach in 2015, in Texas. The information was breached via Network Server . [source] | EMERGENCY COVERAGE CORPORATION had a data breach in 2017, in Tennessee. The information was breached via Paper/Films . [source] | |
Emergency Room Associates doing business as Emergency Medicine Associates had a data breach in 2016, in Arizona. Five months' worth of hospital labels containing protected health information (PHI) were stolen from the car of a workforce member physician that was parked offsite from the covered entity (CE). The PHI was located in a locked briefcase within the car. The types of PHI involved in the breach included patients' names, birthdates, ages, sex, and treatment facilities. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE filed a report with local law enforcement and retrained the workforce member involved. As a result of OCR's investigation, the CE provided assurances that it conducted a full risk assessment and reviewed and updated its policies and procedures. [source] | Empi Inc and DJO, LLC had a data breach in 2015, in Minnesota. The information was breached via Laptop . [source] | |
Endocrinology Associates, Inc. had a data breach in 2015, in Ohio. [source] | ENT and Allergy Center had a data breach in 2016, in Arkansas. One or more hackers attacked the data servers of Bizmatics, a business associate (BA) for the covered entity (CE), ENT & Allergy Center, which resulted in unauthorized access to Bizmatics' customer records including those of the CE. Approximately 16,200 patient's electronic medical records were compromised. The types of protected health information involved in the breach included demographic and clinical information. OCR opened an investigation of the CE to determine if the CE complied with the HIPAA Privacy and Security Rules with respect to business associate contracts. OCR reviewed the business associate agreement between the CE and BA and determined that it appears to be consistent with the requirements of the Privacy and Security Rules. OCR initiated a separate investigation of Bizmatics. Location of breached information: Network Server Business associate present: No [source] | |
ENT Partners of Texas (legally known as Irving-Coppell Ear, Nose and Throat) had a data breach in 2014, in Texas. The information was breached via Network Server. [source] | Entercom Portland, LLC had a data breach in 2014, in Oregon. Backup of data server was stolen froma car. [source] | |
Enterprise Services LLC had a data breach in 2014, in Colorado. The information was breached via Network Server and Other. [source] | Enterprise Services LLC had a data breach in 2017, in Indiana. The information was breached via Network Server and Other. [source] | |
EnvisionRx had a data breach in 2015, in Ohio. [source] | eScreen, Inc. had a data breach in 2014, in Maryland. Name and ssn were breached via Desktop Computer . [source] | |
Estill County Chiropractic, PLLC had a data breach in 2017, in Kentucky. The information was breached via Network Server . [source] | Eureka Internal Medicine had a data breach in 2014, in California. The information was breached via Paper/Films . [source] | |
Excel Plus Home Health, Incorporated had a data breach in 2016, in Texas. The information was breached via Desktop Computer . [source] | Excellus Health Plan, Inc. had a data breach in 2015, in New York. The information was breached via Network Server . [source] | |
Experian had a data breach in 2014, in Maryland. [source] | Experian had a data breach in 2014, in Maryland. Information was accessed without proper authorization . [source] | |
Experian had a data breach in 2014, in Maryland. Name, address, ssn, dob, account numbers were breached via Website . [source] | Experian had a data breach in 2014, in Maryland. Name, dob, address, ssn, account numbers were breached via Website . [source] | |
Experian had a data breach in 2014, in Maryland. Name, dob, ssn, address were breached via Website . [source] | Experian had a data breach in 2014, in Maryland. Name, ssn, dob, account number were breached via Website . [source] | |
EyeCare of Bartlesville had a data breach in 2015, in Oklahoma. Name and payment card info were breached. [source] | Eyecare Services Partners Management, LLC had a data breach in 2017, in Texas. A business associate was present. [source] | |
EZ Prints, Inc. had a data breach in 2014, in Maryland. Name, payment card info were breached via Website . [source] | Fairbanks Hospital had a data breach in 2016, in Indiana. The information was breached via Network Server . [source] | |
fairway independent mortgage corporation had a data breach in 2014, in Maryland. Name, ssn, financial information were breached via Website . [source] | Family & Children's Services of Mid Michigan, Inc. had a data breach in 2016, in Michigan. The information was breached via Network Server . [source] | |
Family & Cosmetic Dentistry of the Rockies had a data breach in 2017, in Colorado. The information was breached via Paper/Films . [source] | Family Medicine East, Chartered had a data breach in 2017, in Kansas. The information was breached via Desktop Computer . [source] | |
Family Medicine of Weston had a data breach in 2016, in Florida. The information was breached via Electronic Medical Record . [source] | Family Service Rochester had a data breach in 2017, in Minnesota. The information was breached via Network Server . [source] | |
Family Tree Health Clinic had a data breach in 2017, in Texas. The information was breached via Network Server . [source] | FastHealth Corporation had a data breach in 2014, in Alabama. The information was breached via Network Server . [source] | |
FastHealth Corporation had a data breach in 2018, in Alabama. The information was breached via Network Server . [source] | Federal Home Loan Mortgage Corporation (Freddie Mac) had a data breach in 2014, in Virginia. The information was breached via Website . [source] | |
Felicia Lewis, MD Lakewood Hills Internal Medicine had a data breach in 2016, in Texas. OCR closed the investigation after it determined that the covered entity (CE) had closed its medical practice and was no longer a CE. Location of breached information: Electronic Medical Record Business associate present: No [source] | Ferguson Advertising, Inc. had a data breach in 2014, in Indiana. The information was breached via Network Server . [source] | |
Fidelis Care had a data breach in 2015, in New York. The covered entity (CE), Fidelis Care, mailed Explanation of Benefits (EOB) letters to the wrong members. The EOBs contained the names, addresses, identification numbers and recent claim activities of 738 individuals. The CE provided breach notification to HHS and affected individuals and offered credit monitoring. Upon discovering the breach, the CE performed a risk assessment. As a result of OCR's investigation, the CE revised its safeguards policy regarding the printing of documents containing protected health information (PHI) and implemented a quality review process to assist with the inspection of outgoing mail that contains PHI. Additionally, the CE sanctioned and retrained the employees involved in the breach. Location of breached information: Paper/Films Business associate present: No [source] | Fidelity Investments had a data breach in 2014, in Maryland. Name, ssn, brokerage account number were breached via email . [source] | |
Fidelity National Financial, Inc. had a data breach in 2014, in Maryland. [source] | FireKeepers Casino Hotel had a data breach in 2015, in Michigan. The information was breached via Network Server . [source] | |
Flexible Benefit Service Corporation had a data breach in 2018, in Illinois. The information was breached via Email . [source] | Flinn Scientific, Inc. had a data breach in 2014, in Maryland. The information was breached via Paper/Films. [source] | |
Florida Agency for Persons with Disabilities had a data breach in 2018, in Florida. The information was breached via Email . [source] | Florida Agency Persons for Disabilities had a data breach in 2018, in Florida. The information was breached via Email . [source] | |
Florida Blue had a data breach in 2017, in Florida. The information was breached via Paper/Films . [source] | Florida Department of Health, Children's Medical Services had a data breach in 2015, in Florida. [source] | |
Florida Healthy Kids Corporation had a data breach in 2017, in Florida. A business associate was not present. [source] | Florida Hospital had a data breach in 2018, in Florida. The information was breached via Network Server . [source] | |
Florida Hospital Medical Group had a data breach in 2016, in Florida. The information was breached via Email . [source] | Florida Hospital Medical Group had a data breach in 2016, in Florida. The information was breached via Paper/Films . [source] | |
Flowers Hospital had a data breach in 2014, in Alabama. The covered entity (CE), Flowers Hospital was informed by law enforcement on February 27, 2014, that while one of its employees was being arrested, the CE's paper facesheets were found in his possession. An internal investigation revealed that the employee may have accessed or allowed another individual access to the clinical and demographic information of 1,208 individuals. The CE provided breach notification to HHS, to affected individuals, and to the media. In response to the breach, the CE implemented procedures to further restrict access to paper records and improved its maintenance and storage procedures. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Paper/Films Business associate present: No [source] | Fondren Orthopedic Group L.L.P. had a data breach in 2018, in Texas. The information was breached via Paper/Films . [source] | |
Forrest General Hospital had a data breach in 2018, in Mississippi. The information was breached via Email . [source] | Four Star Drug of Bethany, Inc. had a data breach in 2016, in Nebraska. On August 30, 2016, the covered entity (CE), Four Star Drug of Bethany, Inc., discovered that it left boxes containing protected health information (PHI) outdoors in an unprotected area where a garbage truck eventually retrieved the boxes and transported them to a recycling plant. The breach affected the PHI of approximately 647 individuals and included patients' names, dates of birth, social security numbers, clinical and demographic information, claims information, and medications. The CE provided breach notification to HHS, affected individuals, and the media. The CE further advised HHS that on May 24, 2016, its pharmacy department was sold, and consequently it was closed at the time of the breach incident that occurred on August 30, 2016. Following the breach, the CE updated its HIPAA policies and procedures to ensure that its remaining records that contain PHI are safeguarded and disposed of properly. The CE no longer generates records containing PHI because it is closed. OCR obtained documented assurances that the CE implemented the corrective actions listed above.[source] | |
Francisco Jaume, D.O. had a data breach in 2016, in Arizona. The information was breached via Network Server . [source] | Fred Finch Youth Center had a data breach in 2015, in California. The information was breached via Network Server and Other. [source] | |
Fred's Stores of Tennessee, Incorporated had a data breach in 2016, in Tennessee. The information was breached via Laptop . [source] | Freelancers Insurance Company had a data breach in 2015, in New York. The information was breached via Network Server . [source] | |
Freeport Memorial Hospital had a data breach in 2016, in Illinois. A business associate was not present. [source] | Freshology, Inc. had a data breach in 2014, in Maryland. Name, address, payment card info were breached via Website . [source] | |
Front Range Dermatology Associates, P.C. had a data breach in 2018, in Colorado. The information was breached via Electronic Medical Record, Email, Laptop . [source] | FujiFilm had a data breach in 2014, in New York. Email system was accessed without authorization . [source] | |
G&S Medical Associates, LLC had a data breach in 2016, in New Jersey. The information was breached via Desktop Computer . [source] | Geekface LLC had a data breach in 2014, in Maryland. Name, address, userName, password, ssn were breached via Website . [source] | |
Geisinger Bloomsburg Hospital had a data breach in 2014, in Pennsylvania. Archived protected health information (PHI) for 3,101 individuals could not be located by the CE, Geisinger Bloomsburg Hospital, after it was acquired by Geisinger, although copies of the PHI were available. There was no evidence that the PHI had been impermissibly disclosed or stolen. OCR provided the CE with information on what constitutes a breach under the Breach Notification Rule. The CE posted notice on its website and notified the media and patients although there was no indication that PHI had been accessed, used, or disclosed. The CE also re-trained staff on safeguards and proper disposal of PHI and stated that additional corrective steps would be taken to reinforce privacy practices in its new facility. Location of breached information: Paper/Films Business associate present: No [source] | Geisinger Health Plan had a data breach in 2016, in Pennsylvania. A business associate was not present. [source] | |
Genesis Physical Therapy, Inc. had a data breach in 2016, in California. Rehab Billing Solutions (RBS) is a business associate (BA), which handled the billing and medical records, for the covered entity (CE), Genesis Physical Therapy, Inc. A third party impermissibly accessed protected health information (PHI) by exploiting a vulnerability in the BA's application that stores scanned documents. The demographic and/or financial information of 2,245 individuals was potentially involved in the breach. The CE ended the BA agreement with this BA on August 31, 2016, and did not have access to the application at the time of the breach. The CE provided breach notification to HHS, affected individuals and the media pursuant to the Breach Notification Rule. In response to OCR's investigation, the CE provided OCR with a copy of its BA agreement with RBS, which contained satisfactory assurances regarding safeguarding PHI pursuant to the requirements of the Privacy and Security Rules. [source] | Georgia Department of Human Services had a data breach in 2015, in Georgia. Georgia Department of Human Services, the covered entity (CE), discovered that on June 8, 2015, an employee emailed a password protected spreadsheet containing protected health information (PHI) to three recipients at a contractor of the CE for research purposes. The contractor was not considered a business associate of the CE. The CE investigated and determined that the spreadsheet contained PHI for 2,983 individuals, including full names, general geographic areas of residence, internal identification numbers, dates of most recent medical assessments, and the diagnoses associated with those assessments. The CE obtained assurances from the recipients that all versions of the spreadsheet and corresponding email chains were deleted and not accessed by anyone else The CE timely breach notification to HHS, affected individuals, and the media. In response to the breach, the CE retrained its workforce, revised its policies and procedures, improved its training program, and implemented additional clearance and approval requirements for the sharing of data. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | |
Giant Eagle, Inc. had a data breach in 2014, in Maryland. There was an error in the internal HR portal . [source] | Gibson Insurance Agency, Inc. had a data breach in 2016, in Indiana. The information was breached via Laptop . [source] | |
Gillette Medical Imaging had a data breach in 2018, in Wyoming. The information was breached via Paper/Films . [source] | Gingerbread Shed Corporation had a data breach in 2014, in Maryland. Name, address, medical diagnosis, ssn were breached. [source] | |
Global Care Delivery, Inc. had a data breach in 2015, in Texas. Five password-protected, but unencrypted laptop computers were stolen from Global Care Delivery, a business associate (BA) of the covered entity (CE), North Shore LIJ Health System in September 2014. The laptops contained the protected health information (PHI) of 18,213 individuals, including names, dates of birth, insurance identification numbers (which contained social security numbers), and diagnoses and/or treatment codes related to claims. The BA notified police at the time of the incident, but did not notify the CE until May 11, 2015. The BA retained Knoll, Inc. to assist with individual notification and provide call center services to answer questions from individuals impacted by the breach. Breach notification was provided to HHS and affected individuals, and the BA offered complimentary one-year identity theft protection services. The business relationship between the CE and BA ended effective May 11, 2015. The BA has closed its business.[source] | Godiva Chocolatier, Inc. had a data breach in 2014, in Maryland. Name, address, medical diagnosis, ssn were breached via stolen laptop . [source] | |
Gold's Gym had a data breach in 2014, in Maryland. Name, credit card info were breached via Desktop Computer . [source] | Good Care Pediatric, LLP had a data breach in 2015, in New York. Name and payment card info were breached. [source] | |
Goodwill Industries International had a data breach in 2014, in Maryland. Name, payment card info were breached via Payment card system . [source] | Gordon Feinblatt LLC had a data breach in 2014, in Maryland. Name, ssn, bank account tin were breached via email . [source] | |
Grace Primary Care, PC had a data breach in 2016, in Tennessee. Grace Primary Care, PC, the covered entity (CE), discovered that its business associate (BA), Bizmatics, suffered a malicious cyber-attack to its computer servers, potentially exposing the names, dates of birth, addresses, phone numbers, email addresses, social security numbers, health insurance numbers, diagnoses, and treatment information for 6,853 individuals. In addition, while the CE was completing breach notification requirements, some of the notification letters to the affected individuals were inadvertently mailed to invalid addresses due to a spreadsheet error. The CE recovered all but 135 letters, unopened, and conducted a breach risk assessment. The CE determined that the 135 letters had a low probability of impermissible disclosure, and OCR provided technical assistance to the CE concerning the elements which constitute PHI. The CE provided timely breach notification to the affected individuals, to HHS, and to the media. OCR determined that a BA agreement was in place at the time of the breach and the subsequent investigation. In response to the breach, the CE offered free identity protection services to the affected individuals, and initiated a process of terminating its business relationship with the BA, which is its electronic health records provider. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | Graybill Medical Group had a data breach in 2014, in California. [source] | |
Greenleaf Book Group, LLC had a data breach in 2014, in Texas. Name, credit card info, email address, mailing address were breached via Laptop . [source] | Greenwood Leflore Hospital had a data breach in 2014, in Mississippi. [source] | |
Group Health Incorporated had a data breach in 2014, in New York. The information was breached via Paper/Films . [source] | Group Health had a data breach in 2016, in Washington. The covered entity (CE), through its business associate (BA), erroneously mailed coverage termination letters to the wrong members/patients. The paper documents contained the protected health information (PHI) of approximately 668 individuals and included names, addresses, insurance group names, and medical record numbers. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE worked with the BA to take additional quality control steps. OCR obtained assurances that the CE/BA implemented the corrective actions listed above. [source] | |
Grx Holdings, LLC dba Medicap Pharmacy had a data breach in 2016, in Iowa. An external hard drive containing the clinical and demographic information of approximately 2,300 individuals inadvertently fell into a garage can around November 5, 2015. The covered entity (CE), Grx Holdings, LLC dba Medicap Pharmacy, provided breach notification to HHS, affected individuals, and the media. In response to the breach, the CE adhered the external hard drives to the wall and initiated a change to eliminate the use of external hard drives as a data backup. It also sanctioned and retrained the involved employees. OCR obtained documentation that the CE implemented these corrective action steps. Location of breached information: Other Business associate present: No [source] | Guardian Pharmacy of Jacksonville had a data breach in 2018, in Florida. The information was breached via Email . [source] | |
Hal Meadows, M.D. had a data breach in 2016, in California. The information was breached via Desktop Computer . [source] | Hancock County Board of Developmental Disabilities had a data breach in 2018, in Ohio. The information was breached via Paper/Films . [source] | |
Hanover Foods Corporation had a data breach in 2014, in Pennsylvania. The information was breached via Website. [source] | Harrisburg Gastroenterology Ltd had a data breach in 2017, in Pennsylvania. The information was breached via Network Server . [source] | |
Harrisonburg OB GYN Associates, P.C. had a data breach in 2016, in Virginia. Harrisonburg Obstetrics and Gynecology Associates, P.C., the covered entity (CE), reported that on August 11, 20, 2016, a physician and former president of the CE, printed out the protected health information (PHI) of approximately 800 patients prior to his resignation. The CE determined that the reports showed patients' names, account numbers, phone numbers, addresses, dates of service and reasons for the visits. At the time of OCR's review, the CE was in litigation for the return of the reports. The CE disabled all access to such reports except by a few employees with a business need. The CE provided breach notification to HHS, the media, and affected individuals. OCR obtained assurances that the CE implemented the corrective actions listed. Location of breached information: Electronic Medical Record Business associate present: No [source] | HawaiŠ—_'Ü'_i Medical Service Association had a data breach in 2016, in Hawaii. [source] | |
Haywood County NC had a data breach in 2015, in North Carolina. [source] | Haywood County NC had a data breach in 2016, in North Carolina. On or around October 31, 2014, a paper accounts receivable report went missing from the covered entity (CE) billing office. The report contained the protected health information (PHI) of 955 individuals and included patients internal identifications numbers, names, clinics visited, and amounts owed. The CE provided breach notification to HHS, affected individuals, and the media, and set up a toll free number anser line and e-mail contact. [source] | |
Health Care Service Corporation had a data breach in 2015, in Illinois. The information was breached via Paper/Films. [source] | Health Care Solutions at Home Inc. had a data breach in 2014, in Ohio. [source] | |
Health Dimensions had a data breach in 2014, in Michigan. The information was breached via Network Server . [source] | Health Incent, LLC had a data breach in 2016, in Tennessee. Health Incent, the covered entity (CE), discovered on June 8, 2016 that a patient database containing electronic protected health information (ePHI) was available on the internet through web searches. The breach affected 1,100 individuals and the types of ePHI involved in the breach included patient names, dates of birth, email addresses, and mailing addresses. The CE provided timely breach notification to HHS, affected individuals, and the media. The CE successfully contacted all affected individuals who did not receive the initial notification. In response to the breach, CE sanctioned those responsible for the breach and created a new process for uploading files to its website. OCR obtained assurances from CE that it implemented the corrective actions noted above. Location of breached information: Other Business associate present: No [source] | |
Health Plan sponsored by Covenant Ministries of Benevolance had a data breach in 2015, in Illinois. The information was breached via Network Server . [source] | HealthEquity, Inc. had a data breach in 2018, in Utah. The information was breached via Email . [source] | |
Healthfirst Affiliates that include Healthfirst PHSP, Inc., Managed Health, Inc., HF Management Services, LLC, and Senior Health Partners had a data breach in 2015, in New York. The information was breached via Electronic Medical Record . [source] | HealthPartners Administrators, Inc. had a data breach in 2014, in Minnesota. The information was breached via Desktop Computer, Laptop, and Other Portable Electronic Device. [source] | |
HealthPartners Inc had a data breach in 2014, in Minnesota. The information was breached via Desktop Computer, Laptop, Other Portable Electronic Device. [source] | HealthPoint had a data breach in 2015, in Washington. The covered entity (CE) reported a breach concerning the theft of a laptop computer from its medical office. The laptop was used for eye scans and contained the names, dates of birth, and medical record numbers of 1,300 patients. The CE provided breach notification to HHS, affected individuals, and the media. As a result of OCR's investigation, and to prevent a similar breach from happening in the future, the CE undertook a comprehensive risk analysis, encrypted its mobile devices, and ensured that physical safeguards were in place. It also retrained employees and revised its security policies and procedures. Location of breached information: Laptop Business associate present: No [source] | |
HealthSouth Rehabilitation Hospital of Round Rock had a data breach in 2015, in Texas. The information was breached via Electronic Medical Record. [source] | HealthTexas Provider Network had a data breach in 2014, in Texas. The information was breached via Email. [source] | |
Healthy Connections, Inc had a data breach in 2014, in California. In April 2014, the covered entity (CE), Healthy Connections Inc., reported that an unencrypted mobile computer drive containing patients' electronic protected health information (ePHI) was lost in transit between the CE and another CE. The breach was noticed when the other CE received the envelope minus the flash drive in the mail. The breach affected the demographic and clinical information of 793 individuals. The CE provided breach notification to HHS, affected individuals, and the media. As a result of OCR's investigation, the CE conducted a comprehensive system-wide risk analysis, implemented a risk management plan, and enhanced its entire electronic and technical security system. OCR obtained assurances that the CE implemented the corrective actions noted above. Location of breached information: Other Portable Electronic Device Business associate present: No [source] | Heard County EMA had a data breach in 2014, in Georgia. A business associate was not present. [source] | |
HeartCare Consultants had a data breach in 2016, in Florida. The information was breached via Electronic Medical Record . [source] | Herbaria had a data breach in 2014, in Missouri. Name, credit/debit card info were breached via Website . [source] | |
Heritage Medical Partners, LLC had a data breach in 2016, in South Carolina. The covered entity (CE), Heritage Medical Partners, while moving to a new facility, left medical records unsecured in the former facility from November 17, 2014 to January 22, 2015, affecting 1,019 individuals. The types of protected health information (PHI) on the documents included patients' names, dates of birth, addresses, phone numbers, social security numbers, genders, ages, ethnicity, height and weight, facility names, treating physicians, dates of tests, and clinical information. OCR provided technical assistance so that the CE provided breach notification to HHS, affected individuals, and the media, and on a website set up by the CE. The CE was in the process of dissolving and stopped treating patients in December 2015. The CE reported that medical records are stored in secure areas of the individual providers' current facilities with access limited to authorized employees. OCR provided technical assistance regarding proper retention and destruction of PHI. OCR obtained assurances that the CE implemented the corrective actions listed above.[source] | High Plains Surgical Associates had a data breach in 2018, in Wyoming. The information was breached via Paper/Films . [source] | |
Highland Rivers Community Service Board had a data breach in 2017, in Georgia. The information was breached via Paper/Films . [source] | Highlands Cashier Hospital had a data breach in 2014, in North Carolina. A business associate (BA), Computer Programs and Systems, Inc., adjusted the covered entity's (CE) firewall in a manner that potentially exposed the protected health information (PHI) of 26,115 individuals on the internet. The types of PHI included patients' names, addresses, dates of birth, treatment information, and social security numbers (for 21,072 individuals). The CE sent timely breach notification to HHS, affected individuals, and the media. The CE also posted notification about the breach on its website. In response to the breach, the CE implemented additional firewall safeguard procedures, began monitoring traffic to and from its website, and began conducting external vulnerability scans. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Network Server Business associate present: No [source] | |
Hilbert College had a data breach in 2014, in Maryland. Paperwork distributed at financial aid workshop inadvertently contained personal info. [source] | Hillsides had a data breach in 2015, in California. The information was breached via Email . [source] | |
Holy Cross Hospital had a data breach in 2014, in Maryland. Name, address, credit card number and expiration date were breached via Network Server . [source] | Home Depot, Inc. had a data breach in 2014, in Maryland. Name, credit card number, expiration date, were breached via Payment card system . [source] | |
Hospice of North Central Ohio had a data breach in 2017, in Ohio. A business associate was not present. [source] | Hospital for Special Surgery had a data breach in 2014, in New York. The information was breached via Desktop Computer and Paper/Films. [source] | |
Hospital for Special Surgery had a data breach in 2016, in New York. The information was breached via Email . [source] | Hospitalists of Arizona had a data breach in 2014, in Arizona. The information was breached via Laptop . [source] | |
Houston Methodist Hospital had a data breach in 2014, in Texas. A business associate was not present. [source] | Houston Methodist Hospital had a data breach in 2017, in Texas. The information was breached via Email . [source] | |
Howard L. Weinstein D.P.M. had a data breach in 2014, in Texas. Four encrypted laptop computers and the back-up system containing the electronic protected health information (ePHI) of approximately 1,000 individuals were stolen as a result of a break-in at the office of the covered entity (CE), Howard L. Weinstein, D.P.M. The CE immediately reported the incident to police and an investigation ensued. The ePHI involved in the theft was encrypted and the CE determined that a breach of ePHI was unlikely. However, the CE responded to the incident as though a breach had occurred and personnel notified the potential affected parties through mailing, media notification, and website notification. They also followed the procedure to file a Breach Notification Report with HHS. The CE implemented additional physical, technical, and administrative safeguards to ensure the security of ePHI. In addition, the CE immediately acted on the recovery plan, and has moved data to a cloud encrypted storage system.[source] | HP Enterprise Services, LLC had a data breach in 2016, in Texas. HP Enterprise Services, LLC, a business associate (BA) of the Indiana Family Social Services Administration, reported the theft of a laptop bag from an employee's vehicle. The bag contained an encrypted laptop computer and an unsecured printed report which contained the protected health information (PHI) of 1,235 individuals. The PHI included demographic information. The BA provided breach notification to HHS, affected individuals, and the media and offered the affected individuals free credit monitoring services. Following the breach, the BA sanctioned the employee responsible for the breach in accordance with its sanction policy. As a result of OCR's investigation, the BA updated its policies and procedures to prevent similar incidents. As a result of OCR's investigation, OCR provided technical assistance regarding breach notification requirements and the BA revised its breach notification template. [source] | |
Hubbard-Bert, Inc. had a data breach in 2014, in Pennsylvania. [source] | Huckstep Holdings Corp. d/b/a TechWise had a data breach in 2017, in Colorado. Name, address, ssn, w2 tax info were breached. [source] | |
Humana Inc [case # HU17001CC] had a data breach in 2017, in Kentucky. A business associate was not present. [source] | Humana Inc [case #15381] had a data breach in 2014, in Kentucky. On April 2, 2014, an unencrypted portable media device containing electronic protected health information (ePHI) was stolen from an employee's locked vehicle. The portable media device contained the demographic data (including some social security numbers), clinical, and health insurance information of 2,962 individuals. The CE provided breach notification to HHS, affected individuals, and the media. The offending employee was terminated as a direct result of violating the CE's policy prohibiting the use of unencrypted devices to store and transport PHI. In addition, the CE re-educated employees about this policy and instructed management teams to ensure that proper procedures were being followed. OCR obtained assurances that the corrective actions were taken. Location of breached information: Other Portable Electronic Device Business associate present: No [source] | |
Humana Inc [Case 18652] had a data breach in 2015, in Kentucky. Humana, Inc., the covered entity (CE), discovered that on August 20, 2015, a market staff employee's briefcase containing an encrypted laptop computer and unsecured paper documents was stolen from her locked vehicle. The CE investigated and determined that the stolen documents contained the protected health information (PHI) of 2,815 individuals, including full names, dates of birth, clinic names, and health insurance information. The CE issued new health insurance member identification numbers to affected individuals, and provided timely breach notification to HHS, to affected individuals, on its website and to the media. In response to the breach, the CE retrained its workforce, disseminated guidance material specifically addressing the proper handling and safeguarding of PHI, and revised procedures to eliminate transportation of PHI in paper format. O [source] | Humana Inc had a data breach in 2017, in Kentucky. A business associate was not present. [source] | |
Humana Inc. [case #HU16004F3] had a data breach in 2016, in Kentucky. The information was breached via Paper/Films . [source] | Hunt Regional Medical Partners had a data breach in 2015, in Texas. Vandals broke into a building storing paper protected health information (PHI) for the covered entity (CE), Hunt Regional Medical Partners. The types of PHI involved in the breach included patients' names, addresses, dates of birth, social security numbers, claims information, and patients' chart information. Approximately 3,000 individuals were affected. Upon discovering the breach, the CE filed a police report. The CE provided breach notification to HHS, affected individuals, and the media. The CE improved physical safeguards and retrained staff. OCR obtained assurances that the CE implemented the corrective actions listed. [source] | |
Huntington Medical Research Institutes had a data breach in 2015, in California. A workforce member took 4,300 patients' protected health information (PHI) with her on several external computer hard drives when her employment with the covered entity (CE), Huntington Medical Research Institutes was terminated. The types of PHI involved in the breach included, variously, financial, demographic and financial information. The CE provided substitute notice, notice to the media, and notice to OCR pursuant to the requirements of the Breach Notification Rule. Following the breach, the CE worked with the workforce member's counsel to recover the PHI in a secure manner and engaged a forensic expert to confirm that all PHI was recovered. The CE also reassigned privacy and security responsibilities and began considering the need to augment its privacy and security staff. The CE improved safeguards by encrypting all computer workstations, as well as phones that access PHI. In response to OCR's investigation, the CE developed a comprehensive enterprise-wide risk analysis report and corresponding risk management plan. [source] | ID Parts, LLC had a data breach in 2014, in Maryland. Name, payment card info were breached via Email . [source] | |
IHS had a data breach in 2014, in Maryland. A business associate was not present. [source] | Illinois Valley Podiatry Group had a data breach in 2016, in Illinois. Bizmatics, Inc., a business associate (BA) that provided online storage and management of patient health records for the covered entity (CE), Illinois Valley Podiatry Group, discovered an unauthorized access to the servers on which the CE's patient files were stored. The breach affected 26,588 individuals' electronic protected health information (ePHI). The types of ePHI involved in the breach included diagnoses and conditions, medications, and other treatment information. The CE provided breach notification to HHS and the media and posted substitute notice on its website. The BA provided breach notification to affected individuals at the direction of the CE. As a result of OCR's investigation, the CE executed a new BA agreement with Bizmatics with provisions regarding the use, disclosure, and safeguarding of protected health information (PHI). OCR obtained documented assurances that the BA and CE implemented the corrective actions noted above. [source] | |
Imhoff and Associates, P.C. had a data breach in 2014, in Maryland. Name, ssn, dln, contact info were breached via Portable device . [source] | Imperial Valley Family Care Medical Group, APC had a data breach in 2016, in California. The information was breached via Laptop . [source] | |
Implants, Dentures & Dental had a data breach in 2015, in Nevada. Implants, Dentures and Dental, Inc., the covered entity (CE), reported that on June 8, 2015, its computer server was removed from its facility without its consent. The CE reported that it worked with law enforcement to investigate the incident. The server contained the electronic protected health information (ePHI) of approximately 12,000 individuals. The types of ePHI involved in this incident included digital x-rays, demographic, financial, and clinical information. Following the removal of the server, the CE's employees were unable to access practice management software. In response to the incident, the CE reported that it adopted encryption technologies, changed passwords, and strengthened password requirements. Additionally, the CE revised its business associate (BA) contracts, as the removal of the server was related to a complicated BA arrangement. The CE also reported that it implemented new technical safeguards, improved physical security, performed risk assessments, and provided workforce members and business associates with additional HIPAA training. Following OCR's investigation of the incident, the CE reported that it had closed its business. [source] | Inclusion Research Institute had a data breach in 2014, in District Of Columbia. [source] | |
Independence Blue Cross and AmeriHealth New Jersey had a data breach in 2014, in Pennsylvania. The information was breached via Laptop. [source] | Indian Health Service Northern Navajo Medical Center had a data breach in 2016, in New Mexico. The information was breached via Paper/Films . [source] | |
Indian Health Service -Rosebud had a data breach in 2014, in Maryland. [source] | Indian Health Service, Aberdeen Area Office had a data breach in 2014, in South Dakota. A business associate was not present. [source] | |
Indian Health Service had a data breach in 2014, in Maryland. The information was breached via Laptop . [source] | Indiana State Medical Association had a data breach in 2015, in Indiana. The information was breached via Other Portable Electronic Device . [source] | |
Inogen, Inc. had a data breach in 2018, in California. The information was breached via Email . [source] | inSite Digestive Health Care had a data breach in 2018, in California. The information was breached via Paper/Films . [source] | |
Inspira Health Network Inc. had a data breach in 2014, in New Jersey. The information was breached via Desktop. [source] | Insulet Corporation had a data breach in 2017, in Massachusetts. A business associate was not present. [source] | |
Insurance Data Services had a data breach in 2015, in Michigan. The information was breached via Network Server. [source] | InSync Computer Solutions, Inc. had a data breach in 2014, in Alabama. The information was breached via Network Server . [source] | |
Integral Health Plan, Inc. had a data breach in 2015, in Florida. The covered entity (CE), Integral Health Plan, Inc., discovered on May 15, 2015, that its business associate (BA), Independent Living Solutions LLC, sent Explanation of Benefits (EOBs) information to incorrect network providers. The EOBs contained patients' names, dates of birth, Medicaid identification numbers (if applicable), and diagnosis and procedure codes, affecting 7,549 individuals. The CE had a BA agreement in place with the BA since July 2013. The CE provided breach notification to HHS, affected individuals, and the media, and also posted notice on its website. In response to the breach, the CE provided additional training material to its BA. In addition, the CE and BA revised payment processes to implement a two-step verification process before material is mailed. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Paper/Films Business associate present: No [source] | Integrated Rehab Consultants had a data breach in 2018, in Illinois. A business associate was present. [source] | |
Integrity Transitional Hospital had a data breach in 2016, in Texas. The information was breached via Network Server . [source] | International Dairy Queen, Inc. had a data breach in 2014, in Maryland. Name, payment card info were breached via Payment card system . [source] | |
International Dairy Queen had a data breach in 2014, in Ontario. Name, credit/debit card info were breached via Payment card system . [source] | International Union of Operating Engineers Local Unions 181, 320 & TVA Health and Welfare Trust Fund had a data breach in 2015, in Kentucky. The information was breached via Network Server . [source] | |
Intuit, Inc. had a data breach in 2014, in Maryland. Address, name, ssn FEINs, and bank account number were breached. [source] | Invest Financial Corporation had a data breach in 2014, in Maryland. The information was breached via Email. [source] | |
Iowa Health System d/b/a UnityPoint Health had a data breach in 2018, in Iowa. The information was breached via Email . [source] | Iowa Medicaid Enterprise had a data breach in 2014, in Iowa. The covered entity (CE), Iowa Medicaid Enterprise, erroneously mailed a patient listing of 862 individuals to a provider on February 26, 2014. The protected health information (PHI) involved in the breach included names and addresses. The CE stated that it discovered this breach was due to an error in its mailing process. The CE stated that it notified the affected individuals and the media. The CE also stated that it shall no longer mail patient listings to providers. OCR has consolidated this breach with another breach involving the Iowa Department of Human Services. Location of breached information: Paper/Films Business associate present: No [source] | |
Iowa Veterans Home had a data breach in 2017, in Iowa. The information was breached via Email . [source] | Iron Mountain Incorporated had a data breach in 2014, in Massachusetts. The information was breached via Paper/Films . [source] | |
Iron Mountain Records Management had a data breach in 2014, in California. A business associate was present. [source] | Iron Mountain had a data breach in 2014, in California. The information was breached via Paper/Films . [source] | |
J.M. Smucker Company had a data breach in 2014, in Maryland. Name, addrses, email addrses, phone, credit/debit card info were breached via Website . [source] | JASACare had a data breach in 2016, in New York. Unauthorized individuals hacked a workforce member's email account and accessed the electronic protected health information (ePHI) of 1,154 patients. The types of ePHI involved in the breach included names, addresses, phone numbers, dates of birth, social security numbers, insurance identification numbers, insurance information, and account balance information. The covered entity (CE), JASACare, provided breach notification to HHS, affected individuals, and the media and posted substitute notice on its website. The CE also provided one year free credit monitoring services for the affected individuals. Following the breach, the CE shut down the workforce member's email account and reset all login information. [source] | |
JCM Partners, LLC had a data breach in 2014, in Maryland. Name, ssn, DLN, email and mailing address were breached via unauthorized access to database . [source] | Jefferson Medical Associates, P.A. had a data breach in 2016, in Mississippi. The information was breached via Network Server . [source] | |
Jemison Internal Medicine, PC had a data breach in 2018, in Alabama. The information was breached via Network Server . [source] | Jennie Stuart Medical Center had a data breach in 2016, in Kentucky. The information was breached via Desktop Computer and Network Server. [source] | |
Jessie Trice Community Health Center, Inc. had a data breach in 2014, in Florida. The information was breached via Desktop Computer, and Network Server. [source] | Jewish Hospital had a data breach in 2014, in Kentucky. A small number of employees of the covered entity (CE), Jewish Hospital, responded to “phishing” emails that appeared legitimate and disclosed the demographic and clinical protected health information (PHI) of approximately 2,992 individuals. The PHI involved in the breach included names, addresses, birthdates, diagnoses, treatments received, health insurance information and the social security numbers of a few individuals. In response to the incident, the CE secured the affected email accounts and arranged for a forensic investigation. While the CE has no evidence that the electronic PHI in the employees' mailboxes was accessed or otherwise infiltrated by the phishing scheme, it nonetheless sent breach notification letters and offered one year of free credit monitoring and identity theft protection services to all potentially affected individuals. It also provided breach notification to HHS and the media and provided substitute notice. Following the breach, the CE deployed anti-phishing software, accelerated its employee phishing education campaign, established a quick reaction team for proactively blocking phishing or other web-based threats, and enhanced its auditing and logging controls. [source] | |
Jimmy John's Franchises LLC had a data breach in 2014, in Maryland. Name, payment card info were breached via Payment card system . [source] | John E. Gonzalez DDS had a data breach in 2016, in California. The information was breached via Other Portable Electronic Device . [source] | |
John J. Pershing VA Medical Center had a data breach in 2018, in Missouri. The information was breached via Paper/Films . [source] | Jones Family Practice, P.A. had a data breach in 2017, in North Carolina. The information was breached via Network Server . [source] | |
Joseph Michael Benson M.D had a data breach in 2014, in Texas. The information was breached via Desktop. [source] | Kaiser Foundation Health Plan of Colorado had a data breach in 2014, in Colorado. The covered entity (CE), Kaiser Foundation Health Plan of Colorado, reported that on July 24, 2014, it erroneously mailed letters containing protected health information (PHI) to incorrect recipients, affecting 11,551 individuals. Each letter contained the name of another program member in a chronic condition management program. The CE provided breach notification to HHS, affected individuals, and the media. As a result of OCR's investigation, the CE sanctioned and retrained the responsible employee. Location of breached information: Other Business associate present: No [source] | |
Kaiser Foundation Health Plan of the Mid-Atlantic States, Inc. had a data breach in 2015, in Maryland. The information was breached via Network Server. [source] | Kaiser Foundation Health Plan of the Northwest had a data breach in 2016, in Oregon. The information was breached via Network Server . [source] | |
Kaiser Foundation Health Plan, Inc. had a data breach in 2016, in California. The information was breached via Paper/Films . [source] | Kaiser Foundation Health Plan, Inc. had a data breach in 2017, in California. The information was breached via Email . [source] | |
Kaiser Foundation Health Plan, Inc. had a data breach in 2017, in California. The information was breached via Paper/Films . [source] | Kaiser Foundation Healthplan, Inc. of Southern California had a data breach in 2016, in California. The information was breached via Network Server . [source] | |
Kaiser Permanente Northern California had a data breach in 2016, in California. The information was breached via Other Portable Electronic Device . [source] | Kaleida Health had a data breach in 2017, in New York. The information was breached via Email . [source] | |
Kane Hall Barry Neurology had a data breach in 2015, in Texas. The information was breached via Desktop Computer. [source] | Kennebunk Center for Dentistry had a data breach in 2017, in Maine. The information was breached via Electronic Medical Record, Paper/Films . [source] | |
Kennewick General Hospital dba Trios Health had a data breach in 2017, in Washington. The information was breached via Electronic Medical Record . [source] | Kern County Mental Health had a data breach in 2016, in California. The covered entity (CE), Kern County Mental Health, discovered a 290-page paper printout of accounts receivables for the month of September 2006 in an open file container that was left in a vacated area of their facility on April 15, 2016. The protected health information (PHI) involved in the breach included patients' names, medical record numbers, dates of service, numerical service codes, and amounts billed. Approximately 1,212 individuals were affected by this breach. The CE initially provided substitute and media breach notifications and notification to HHS. After receiving technical assistance from OCR, the CE provided individual breach notification. Following the breach, the CE revised its policies and procedures for moving and vacating office space to ensure that a thorough walk-through of the area is completed prior to vacating an area. The CE also retrained staff on these revised policies and procedures to ensure they are implemented. [source] | |
KEYSTONE INSURERS GROUP had a data breach in 2014, in Indiana. On April 27, 2015, rioting broke out in Baltimore, MD and the covered entity (CE), Keystone Pharmacy, was broken into, vandalized and looted. Multiple prescriptions and stock bottles of narcotics were taken. About 150 prescription bags containing patient names and the medications were stolen. The types of protected health information (PHI) contained on the prescriptions included names, addresses, and prescription information. The CE provided breach notification to HHS, affected individuals, and the media, and offered credit monitoring. The location was immediately secured. The CE installed a new front door and upgraded the security system. OCR obtained assurances that the CE implemented the corrective actions listed. Location of breached information: Other, Paper/Films Business associate present: No [source] | Keystone Pharmacy, Inc. had a data breach in 2015, in Maryland. On April 27, 2015, rioting broke out in Baltimore, MD and the covered entity (CE), Keystone Pharmacy, was broken into, vandalized and looted. Multiple prescriptions and stock bottles of narcotics were taken. About 150 prescription bags containing patient names and the medications were stolen. The types of protected health information (PHI) contained on the prescriptions included names, addresses, and prescription information. The CE provided breach notification to HHS, affected individuals, and the media, and offered credit monitoring. The location was immediately secured. The CE installed a new front door and upgraded the security system. OCR obtained assurances that the CE implemented the corrective actions listed. Location of breached information: Other, Paper/Films Business associate present: No [source] | |
Keystone Rural Health Consortia, Inc. had a data breach in 2016, in Pennsylvania. [source] | Kimpton had a data breach in 2014, in Maryland. The information was breached via Website. [source] | |
Kindred Nursing Centers West, L.L.C. had a data breach in 2015, in California. On August 31, 2015, the covered entity (CE), Kindred Nursing Centers West, LLC, discovered that a password-protected office computer had been stolen from a locked office within its facility. The types of protected health information (PHI) contained in computer included the names of 1,125 patients and one or more of the following: admission and discharge dates, facility names, patient ID numbers, and certain accounting-related information. The CE provided breach notification to HHS, the affected individuals, and the media. OCR obtained assurances that the CE improved its physical safeguards, revised its encryption policy, strengthened its password requirements, and retrained workforce members. Location of breached information: Desktop Computer Business associate present: No [source] | Kinetorehab Physical Therapy, PLLC had a data breach in 2016, in New York. The information was breached via Laptop . [source] | |
King of Prussia Dental Associates had a data breach in 2016, in Pennsylvania. King of Prussia Dental Associates' network server was hacked. The breach affected the electronic protected health information (ePHI) of 16,768 individuals and included names, dates of birth, social security numbers, and addresses, as well as clinical information. The covered entity (CE) provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE strengthened its technical safeguards, including its firewalls and anti-virus protection. OCR reviewed the CE's risk analysis to ensure compliance with the Security Rule. The CE provided OCR with assurances it would continue to strengthen its technical safeguards. [source] | Kirkbride Center had a data breach in 2014, in Pennsylvania. Name, contact info, ssn, banking info were breached. [source] | |
Kleiner Perkins Caufield & Byers had a data breach in 2014, in Maryland. Name, contact info, ssn, banking info were breached via Laptop . [source] | Kmart Corporation had a data breach in 2014, in Illinois. Printed pharmacy reports containing protected health information (PHI) about patients' prescriptions was disclosed to an acquaintance of a former pharmacy employee in Sebring, Florida. The PHI involved in the breach included the names, addresses, prescribers, and medications for approximately 1,866 individuals. The CE provided breach notification to HHS, affected individuals, and the media. The CE also contacted law enforcement and reinforced with the pharmacy staff the CE's HIPAA policies and procedures pertaining to the appropriate use, disclosure, and the safeguarding of PHI. OCR obtained written assurances that the CE implemented the corrective actions listed above. [source] | |
Kmart Corporation had a data breach in 2014, in Illinois. The information was breached via Electronic Medical Record. [source] | Knoxville Heart Group, Inc. had a data breach in 2018, in Tennessee. The information was breached via Email . [source] | |
KP Northern CA Department of Research had a data breach in 2014, in California. [source] | Kraig R. Pepper, D.O., P.A. had a data breach in 2017, in Texas. A business associate was not present. [source] | |
L Brands, Inc. had a data breach in 2014, in Ohio. The information was breached via Website . [source] | Laborers Funds Administrative Office of Northern California, Inc. had a data breach in 2016, in California. On February 17, 2016, the covered entity (CE), Laborers Funds Administrative Office of Northern California, Inc, discovered that a tax sent to its clients and beneficiaries inadvertently contained protected health information (PHI) about unrelated individuals. The breach affected approximately 800 individuals and included names, social security numbers, and eligibility information. The CE provided breach notification to HHS, affected individuals, and the media. In response to the breach, the CE implemented new technical safeguards for creating and transmitting this type of data, conducted a new/updated security analysis, revised its HIPAA policies and procedures, and trained its workforce. The CE also provided OCR with additional documentation including its HIPAA Notice of Privacy Practices Policy, as relevant to this breach investigation. OCR obtained assurances that the CE implemented the corrective actions listed above.[source] | |
LaCie USA had a data breach in 2014, in Maryland. The information was breached via Website . [source] | Ladies First Choice, Inc. had a data breach in 2014, in Florida. [source] | |
Lafayette Pain Care PC had a data breach in 2016, in Indiana. The information was breached via Network Server . [source] | Lake Pulmonary Critical Care PA had a data breach in 2016, in Florida. The covered entity (CE), Lake Pulmonary Critical Care, PA, discovered that a former employee removed patient medical records from the office and took them home. The theft of this protected health information (PHI) affected 648 individuals. The medical information included patients' names, addresses, phone numbers, dates of birth, social security numbers, health insurance information, medical diagnoses, lab results, medications, and other treatment information. The CE provided timely breach notification to HHS, to affected individuals, and to the media. In response to the breach, the CE improved safeguards by installing employee lockers for all personal items and installing privacy walls at the nurses' stations. In addition, the CE arranged for HIPAA training for its employees and doctors. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Paper/Films Business associate present: No [source] | |
Lake Pulmonary Critical PA had a data breach in 2016, in Florida. [source] | Lancaster Cardiology Medical Group, and Sunder Heart Institute and Vascular Medical Clinic had a data breach in 2015, in California. [source] | |
Lancaster County EMS had a data breach in 2015, in South Carolina. A safe containing two unencrypted computer flash drives and two unencrypted hard drives went missing from the administration building of covered entity (CE), Lancaster County EMS. The protected health information (PHI) stored on the missing hard drives and flash drives included patients' names, addresses, dates of birth, social security numbers, medications, medical histories, medical treatment, and healthcare insurance information for 55,000 individuals. The CE provided breach notification to HHS, the 55,000 affected individuals, and the media. In response to the breach, the CE implemented universal controls to ensure that only the CE's devices can connect to its network.. The CE also implemented security controls and physical safeguards to further restrict access to its server room. In addition, the CE implemented video security system monitoring of its server room. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | Lane Community College Health Clinic had a data breach in 2017, in Oregon. The information was breached via Laptop . [source] | |
Larsen Dental Care LLC had a data breach in 2014, in Idaho. An unencrypted external hard drive containing the electronic protected health information (ePHI) of 6,900 individuals was stolen from a workforce member's vehicle. The ePHI involved in the breach included names, addresses, dates of birth, email addresses, telephone numbers, dental records, medical history, health insurance numbers, and social security numbers. The covered entity (CE), Larson Dental Care LLC, provided breach notification to HHS, affected individuals and the media, and also posted notice online. Following the breach, the CE terminated the employment of the responsible workforce member. It also conducted a new risk assessment, implemented new security and privacy policies, including device and media control policies, and retrained staff. The CE improved safeguards by encrypting all computers and mobile devices containing ePHI and installing comprehensive security upgrades to its computer network. OCR obtained assurances that the CE implemented these corrective actions. [source] | Lasair Aesthetic Health, P.C. had a data breach in 2016, in Colorado. The information was breached via Email . [source] | |
Laser & Dermatologic Surgery Center had a data breach in 2016, in Missouri. The information was breached via Network Server . [source] | Lawrence General Hospital had a data breach in 2015, in Massachusetts. [source] | |
LC&Z General and Cosmetic Dentistry had a data breach in 2017, in Florida. The information was breached via Email . [source] | LCS Westminster Partnership IV, LLP d/b/a Sagewood had a data breach in 2016, in Arizona. The information was breached via Email, Laptop, and Network Server . [source] | |
Lebanon Cardiology Associates, PC had a data breach in 2016, in Pennsylvania. The information was breached via Network Server. [source] | Ledet Family Chiropractic Cener had a data breach in 2014, in Pennsylvania. The information was breached via Network Server . [source] | |
Lee Memorial Health System had a data breach in 2015, in Florida. [source] | Lee Rice D.O., Medical Corp DBA Lifewellness Institute had a data breach in 2016, in California. [source] | |
Legacy Consulting LLC had a data breach in 2014, in Maryland. Name, address, ssn were breached via paper . [source] | Legal Sea Foods, LLC had a data breach in 2014, in Massachusetts. The information was breached via Laptop. [source] | |
Leo Edwards, Jr., M.D. had a data breach in 2017, in Texas. The information was breached via Network Server . [source] | Lewis J. Sims, DPM, PC dba Sims and Associates Podiatry had a data breach in 2014, in New York. The information was breached via Laptop . [source] | |
Liberty Tax had a data breach in 2014, in Maryland. Liberty Tax Services contacted customers to inform them of a data breach due to a burglary. The thieves took some files and electronic records that included personal information of their customers.The information included names, addresses, dates of birth, identification numbers, Social Security numbers, income documents and names of dependents, their dates of births, and their Social Security numbers. [source] | Life Care Center of Attleboro had a data breach in 2015, in Massachusetts. A business associate (BA), Iron Mountain, discovered that five boxes of archived paper records it was storing for the covered entity (CE), Life Care Center of Attleboro, were unaccounted for or lost. During the course of the investigation, the BA located two of the missing boxes, thus the loss affected the protected health information (PHI) of approximately 927 individuals. The records included demographic, financial, and clinical information. OCR obtained evidence of timely notification of the breach to individuals, the media and HHS and reviewed the BA agreement with Iron Mountain. Location of breached information: Paper/Films Business associate present: No [source] | |
LifeBridge Health, Inc had a data breach in 2018, in Maryland. The information was breached via Network Server . [source] | Lifespan Corporation had a data breach in 2017, in Rhode Island. The information was breached via Laptop . [source] | |
Lifestyle Therapy & Coaching had a data breach in 2017, in Alabama. A business associate was not present. [source] | Linda J White, DDS, PC had a data breach in 2016, in Virginia. On June 27, 2016, the covered entity (CE), Dr. Linda White, reported that an external hard drive device containing a backup of the dental practice's computer server was not returned for proper destruction by an employee. Approximately 2,000 individuals were affected by the breach and the types of protected health information (PHI) stolen included patients' names, dates of births, social security numbers, and limited medical information. The CE provided breach notification to HHS, affected individuals, and the media. The CE determined after a formal risk assessment that the level of risk was very low because the stolen hard drive required specific software to be utilized for the employee to gain access to the patients' PHI. OCR obtained assurances that the CE implemented the corrective actions listed. County officials initiated prosecution of the employee who possessed the hard drive device. [source] | |
Lindsay House Surgery Center, LLC had a data breach in 2016, in New York. The information was breached via Paper/Films . [source] | Lister Healthcare had a data breach in 2016, in Alabama. The information was breached via Laptop . [source] | |
Livongo Health, Inc. had a data breach in 2016, in Illinois. The information was breached via Portable Electronic Device. [source] | LKM ENTERPRISES, INC. had a data breach in 2017, in Oklahoma. The information was breached via Desktop Computer, Laptop . [source] | |
Local 693 Plumbers & Pipefitters Health & Welfare Fund had a data breach in 2017, in Vermont. The information was breached via Other Portable Electronic Device . [source] | Locust Fork Pharmacy had a data breach in 2016, in Alabama. On February 15, 2016, the covered entity (CE), Locust Fork Pharmacy, discovered the lock on one of their storage units was broken. The storage unit contained boxes of records for approximately 5,000 individuals. Protected health Information (PHI) in the records included names, addresses, and birth dates. The CE determined that all the boxes were stacked in sequence, none was missing, and all remained sealed. The CE worked with local police in the investigation of the incident, and updated its policies and procedures related to breach response, breach mitigation, and physical security of the storage unit. The CE provided breach notification to HHS and posted media notice in its geographic area for two weeks in March 2016. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Other Business associate present: No [source] | |
Logos Management Software, LLC had a data breach in 2014, in Maryland. Credit card info was breached via Website. [source] | Loi Luu had a data breach in 2014, in California. [source] | |
Lokai Holdings LLC had a data breach in 2014, in Maryland. Name, address, payment card info, userName and password were breached via Network Server . [source] | Longs Peak Family Practice, P.C. had a data breach in 2017, in Colorado. The information was breached via Desktop Computer, Network Server . [source] | |
LookingGlass Cyber Solutions Inc. had a data breach in 2017, in Virginia. Name, address, ssn, w2 tax info were breached via Email . [source] | Louisiana Health Cooperative, Inc. in Rehabilitation had a data breach in 2016, in Louisiana. OCR opened an investigation of the covered entity (CE), Louisiana Health Cooperative, Inc., after it reported a breach involving its business associate (BA), Summit Reinsurance Services, Inc. The BA discovered ransomware on a server containing the unencrypted electronic protected health information (ePHI) of approximately 8,000 members of the CE. The ePHI included social security numbers, insurance and treatment information, and other demographic information. Upon discovery of the breach, the BA initiated an investigation to determine the nature and extent of the attack as well as to assess the system vulnerabilities. The CE provided breach notification to HHS and posted substitute notice on its website. The BA provided breach notification to the affected individuals and the media. OCR verified that CE had a proper BA agreement in place, which restricted the BA's use and disclosure of PHI and required the BA to safeguard all PHI.[source] | |
Louisiana Healthcare Connections had a data breach in 2016, in Louisiana. A business associate was not present. [source] | LPL Financial LLC had a data breach in 2014, in Massachusetts. Name, account number, account balance were breached. [source] | |
LSU Healthcare Network had a data breach in 2017, in Louisiana. The information was breached via Other Portable Electronic Device . [source] | Luque Chiropractic, Inc. had a data breach in 2016, in California. The information was breached via Network Server . [source] | |
M&M Computer Services had a data breach in 2014, in Texas. [source] | M&T Bank had a data breach in 2014, in Maryland. Name, address, phone number, dob, ssn were breached via email . [source] | |
Maine General Health had a data breach in 2015, in Maine. The information was breached via Network Server . [source] | Man Alive, Inc. and Lane Treatment Center, LLC had a data breach in 2016, in Maryland. [source] | |
Managed Health Services had a data breach in 2016, in Indiana. The information was breached via Email and Laptop . [source] | Managed Health Services had a data breach in 2016, in Indiana. The information was breached via Paper/Films . [source] | |
Mann-Grandstaff VA Medical Center had a data breach in 2017, in Washington. A business associate was not present. [source] | Maricopa Special Health Care District - Maricopa Integrated Health System had a data breach in 2015, in Arizona. A medical resident lost an unencrypted thumb drive that contained the names, dates of birth, and clinical information or diagnoses of 633 patients selected for a chart review. The covered entity (CE), Maricopa Integrated Health System, provided breach notification to HHS, affected individuals, and the media. In response to the breach, the CE comprehensively reviewed its privacy and security practices and updated its HIPAA policies and procedures. It sanctioned and retrained the medical resident and retrained other workforce members on its HIPAA security procedures. OCR's investigation resulted in the covered entity improving its HIPAA practices. Location of breached information: Other Portable Electronic Device Business associate present: No [source] | |
Mark A. Gillispie had a data breach in 2014, in California. On June 5, 2014, the covered entity (CE), reported that a trusted physician who had worked in the office for four years left, and prior to leaving, copied patients' demographic information including names, social security numbers, addresses, dates of birth, phone numbers, emails, insurance information and recall dates. The protected health information (PHI) of 5,845 individuals was affected by the breach. Following the breach, the CE improved technical safeguards by installing a firewall, securing browser sessions, implementing strong authentication, antivirus software, and logical access control, and encrypting wireless connections. It also improved physical security and reported that it revised its HIPAA Privacy and Security policies and procedures. During the course of the investigation, OCR learned that the CE is no longer a CE. Location of breached information: Desktop Computer Business associate present: No [source] | Mark Anthony Quintero, M.D., L.L.C. had a data breach in 2016, in Florida. In January, 2015, a business associate (BA), Bizmatics, discovered that one of its computer servers was compromised by an unknown individual or individuals (hackers). The breach affected approximately 650 of the covered entity's (CE) patients. The CE cooperated with OCR and accepted the technical assistance provided until it closed for business in February 2017. Based on the foregoing, OCR decided not to further investigate. Location of breached information: Network Server Business associate present: No [source] | |
Marketing Clique had a data breach in 2015, in Texas. A business associate was not present. [source] | Martin Army Community Hospital had a data breach in 2016, in Georgia. In December 2013 The IRS notified the covered entity (CE), Martin Army Community Hospital,that one of its employees was involved in identity theft activities. This review was consolidated with another review of this CE. Location of breached information: Paper/Films Business associate present: No [source] | |
Mary Ruth Buchness, MD, Dermatologist, P.C. had a data breach in 2015, in New York. The information was breached via Email . [source] | Maryland Medical Center/Dr. Morrill had a data breach in 2016, in Maryland. The information was breached via Desktop Computer . [source] | |
Maschino, Hudelson & Associates had a data breach in 2014, in Oklahoma. A laptop was stolen from the trunk of a car. [source] | Massachusetts General Hospital had a data breach in 2016, in Massachusetts. The information was breached via Network Server . [source] | |
Matthews Carter and Boyce CPA Advisors had a data breach in 2017, in Virginia. Name and 1099 tax form were breached. [source] | Max M Bayard MD, PC had a data breach in 2015, in Vermont. The information was breached via Paper/Films. [source] | |
MAXIMUS, Inc. / Business Ink, Co. had a data breach in 2018, in Virginia. The information was breached via Paper/Films . [source] | Mayfield Clinic Inc had a data breach in 2016, in Ohio. An unauthorized person sent a fraudulent email with an attachment that triggered a download of a ransomware virus to 23,341 email addresses held by the covered entity's (CE's) business associate (BA) on its behalf. The protected health information (PHI) involved in the breach included email addresses. The CE sent an email notification to affected individuals on the day of the incident and sent another email notification two days later. The CE provided breach notification to HHS, affected individuals, and the media and also posted substitute notice on its web site. Following the breach, the CE assessed system controls, provided anti-scanning updates to its employees' email, deleted the email addresses it maintained on its BA's systems, and put a hold on the future electronic distribution of newsletters. OCR obtained written assurances that the CE implemented the corrective actions listed above. Location of breached information: Email Business associate present: No [source] | |
Mayo Clinic Health System- Red Wing had a data breach in 2015, in Minnesota. On May 18, 2015, an access audit revealed that the covered entity's (CE) employee accessed patients' electronic medical records beyond the scope of authorized access and assigned job responsibilities. The CE discovered that the unauthorized access dated back to 2009. The breach affected approximately 601 individuals and the types of protected health information (PHI) involved in the breach included patients' diagnoses and medical conditions. The CE provided breach notification to HHS, affected individuals, and the media. During OCR's investigation, the CE retrained the revenue department in its Red Wing SE Minnesota Region on its privacy rules. OCR obtained written assurances that the CE implemented the corrective action steps listed above. Location of breached information: Electronic Medical Record Business associate present: No [source] | McLaren Greater Lansing Cardiovascular Group had a data breach in 2016, in Michigan. The information was breached via Desktop Computer, Electronic Medical Record, Other . [source] | |
MD Manage (Vcarve LLC) had a data breach in 2014, in New Jersey. The information was breached via Network Server . [source] | MDeverywhere, Inc. had a data breach in 2017, in Texas. A business associate was present. [source] | |
MDF Transcription Services had a data breach in 2014, in Massachusetts. A business associate was present. [source] | mdINR LLC had a data breach in 2015, in Florida. The information was breached via Portable Electronic Device. [source] | |
Mecklenburg County, North Carolina had a data breach in 2017, in North Carolina. The information was breached via Other Portable Electronic Device . [source] | Med-Cert, Inc. had a data breach in 2017, in Florida. The information was breached via Network Server and Other. [source] | |
Medical Center of Plano had a data breach in 2014, in Texas. The information was breached via Email. [source] | Medical Colleagues of Texas, LLP had a data breach in 2016, in Texas. The information was breached via Network Server . [source] | |
Medical College of Wisconsin had a data breach in 2016, in Wisconsin. The information was breached via Network Server. [source] | Medical Information Management Systems, LLC had a data breach in 2017, in Florida. The information was breached via Network Server . [source] | |
Medical Mutual of Ohio had a data breach in 2014, in Ohio. The information was breached via Paper/Films . [source] | Medical Mutual of Ohio had a data breach in 2017, in Ohio. The information was breached via Email . [source] | |
Medical Oncology Hematology Consultants,PA had a data breach in 2017, in Delaware. The information was breached via Desktop Computer, Network Server . [source] | MedWatch LLC had a data breach in 2018, in Florida. The information was breached via Network Server . [source] | |
MemberClicks, Inc. d/b/a Moolah Payments had a data breach in 2014, in Maryland. Name, address, dob, ssn were breached via Laptop . [source] | Memorial Healthcare System had a data breach in 2014, in Florida. The information was breached via Email. [source] | |
Memorial Healthcare had a data breach in 2017, in Michigan. A business associate was not present. [source] | Memorial Hermann Health System had a data breach in 2014, in Texas. The information was breached via Paper/Films. [source] | |
Memorial Hospital at Gulfport had a data breach in 2018, in Mississippi. The information was breached via Email . [source] | Memphis VA Medical Center had a data breach in 2017, in Tennessee. The information was breached via Paper/Films . [source] | |
Mentor ABI, LLC had a data breach in 2018, in Massachusetts. The information was breached via Other Portable Electronic Device . [source] | Mercer HR Services, LLC had a data breach in 2014, in Maryland. [source] | |
Merchants Metals, Inc. had a data breach in 2017, in Georgia. Name, address, ssn, w2 tax info were breached via Email . [source] | Mercy Family Medicine had a data breach in 2017, in Colorado. The information was breached via Other Portable Electronic Device . [source] | |
Mercy Health Love County Hospital and Clinic had a data breach in 2017, in Oklahoma. The information was breached via Paper/Films . [source] | Mercy Health Services had a data breach in 2014, in Maryland. A memory stick containing patient information was found July 18 by a local citizen on the ground at the County Fairgrounds near the hospitals information booth. It was returned to the hospital four weeks later. Data included names, SSNs, dates of birth, and medical records. [source] | |
Mercy Hospital and Medical Center had a data breach in 2016, in Illinois. The information was breached via Paper/Films . [source] | Mercy Hospital Logan County had a data breach in 2017, in Oklahoma. The information was breached via Paper/Films . [source] | |
Mercy Iowa City had a data breach in 2016, in Iowa. The information was breached via Desktop Computer, Email, Network Server . [source] | Mercy Medical Center Redding - Oncology Clinic, Privacy Manager Breach had a data breach in 2014, in California. A former employee kept patient photographs, videos, memos, schedules, and forms. Some of the documents included patient Social Security numbers and other personal information. The employee is also being accused of voyeurism and possession of child pornography; though this is unrelated to these findings. [source] | |
Mercy Medical Center Redding had a data breach in 2016, in California. An employee of a business associate (BA), naviHealth, provided services to the covered entity's (CE) patients using an assumed name and nursing license from June 1, 2015, to May 13, 2016, and accessed protected health information (PHI) in the course of employment. The breach affected 520 individuals who were patients of the CE's Redding facility and a total of 1,253 Dignity Health patients in California and Nevada. The types of PHI involved in the breach included full names, addresses, dates of birth, social security numbers, claims information, diagnoses/conditions, lab results, and medications. The CE provided breach notification to HHS, affected individuals, and the media and also provided substitute notice. OCR reviewed the BA agreement in place between the CE and BA and obtained assurances that the CE implemented the corrective actions listed above. In response to the breach, the BA sanctioned the responsible employee, terminated the employee's access to all PHI, and contacted law enforcement to report the incident. The BA also reviewed recorded calls made by the employee and PHI accessed by the employee to ensure that PHI was accessed to provide patients with services according to the job function. In addition, the BA improved administrative safeguards by revising its workforce clearance policies and procedures. [source] | Merit Health Northwest Mississippi had a data breach in 2015, in Mississippi. An employee of Merit Health Northwest Mississippi, the covered entity (CE), impermissibly obtained protected health information (PHI) for identity theft and fraud purposes by photographing documents with a personal mobile device, writing patient information in a notebook, and removing paper medical records from the facility. After working with law enforcement and conducting an internal investigation, the CE determined that the stolen patient information included the names, dates of birth, addresses, social security numbers, medical record numbers, health insurance and clinical information of 847 individuals. The CE provided timely breach notification to HHS, to affected individuals and to the media. In addition, the CE offered free credit monitoring to the affected individuals and provided substitute notice on its website. In response to the breach, the CE re-trained its employees and revised its policy on the printing of social security numbers. The employee at fault for this incident is no longer employed by the CE. OCR obtained assurances that the CE has implemented the corrective actions listed above. [source] | |
Meritus Medical Center, Inc. had a data breach in 2015, in Maryland. Name, address, ssn, account number were breached. [source] | Merrill Lynch Wealth management had a data breach in 2014, in Maryland. Name, address, ssn, account number were breached via Website . [source] | |
MetroPlus Health Plan, Inc. had a data breach in 2017, in New York. The information was breached via Email . [source] | MetroPlus Health Plan, Inc. had a data breach in 2014, in New York. The information was breached via Email. [source] | |
MetroPlus Health Plan had a data breach in 2017, in New York. A business associate was not present. [source] | Metropolitan Companies, Inc. had a data breach in 2014, in Maryland. An unauthorized third party accessed computer systems and potentially removed documents. [source] | |
Metropolitan Government of Nashville and Davidson County (Metro) Public Health Department had a data breach in 2014, in Tennessee. The covered entity (CE), Metropolitan Government of Nashville and Davidson County Public Health Department, reported that on July 18, 2014, during the relocation of the Children's Special Services Clinic, two small metal filing units, holding standard sized paper index cards on patients seen in the CSS clinic, were inadvertently tipped over and the index cards fell out of the filing units. The index cards contained full names, addresses, dates of birth, social security numbers, and diagnosis codes of 1,717 patients. The CE provided breach notification to HHS, affected individuals, and the media, placed a conspicuous notice on its website, and offered credit monitoring and identity theft protection to all affected individuals. In response to the incident, the CE investigated, interviewed all relevant staff and the contractor's employees, and reviewed surveillance recordings. As a result of its investigation, the CE eliminated the index card system, re-evaluated its process on retention and use of paper records, created and implemented additional HIPAA policies and procedures, and retrained staff. OCR obtained assurances that the CE implemented the corrective actions listed. [source] | Metropolitan Hospital Center had a data breach in 2015, in New York. The information was breached via Email . [source] | |
Metropolitan Jewish Health System, Inc. d/b/a MJHS had a data breach in 2016, in New York. The information was breached via Email . [source] | MGA Home Healthcare Colorado, Inc. had a data breach in 2016, in Arizona. The information was breached via Laptop . [source] | |
MGA Home Healthcare Colorado, Inc. had a data breach in 2017, in Arizona. The information was breached via Email . [source] | MHC Coalition for Health and Wellness had a data breach in 2017, in Virginia. The information was breached via Laptop . [source] | |
Michael Benjamin, M.D., Inc. had a data breach in 2015, in California. The information was breached via Desktop Computer, Email, and Network Server. [source] | Michael Gruber DMD PA had a data breach in 2018, in New Jersey. The information was breached via Desktop Computer, Email, Network Server . [source] | |
Michaels Stores, Inc. had a data breach in 2014, in Maryland. The information was breached via Laptop. [source] | Michagan Facial Aesthetic Surgeons d/b/a University Physician Group had a data breach in 2017, in Michigan. The information was breached via Laptop . [source] | |
Middlesex Hospital had a data breach in 2015, in Connecticut. The information was breached via Email . [source] | Midland County Hospital District d/b/a Midland Memorial Hospital had a data breach in 2016, in Texas. The information was breached via Paper/Films . [source] | |
Midland Women's Clinic had a data breach in 2016, in Texas. On April 26, 2016, the covered entity (CE), Midland Women's Clinic, learned that patient documents had been discovered, unsecured, at an unauthorized offsite location. The documents contained the protected health information (PHI) of approximately 717 individuals and included names, dates of birth, social security numbers, addresses and zip codes, diagnoses/conditions, lab results, medications, and other treatment information. Following the breach, the CE secured the patient records, updated its policies and procedures, and provided additional HIPAA training to its employees. OCR reviewed the CE's breach notifications to the affected individuals and the media and provided technical assistance regarding the breach notification requirements. Location of breached information: Paper/Films Business associate present: No [source] | Midlands Orthopaedics, P.A. had a data breach in 2015, in South Carolina. [source] | |
Midwest Orthopaedic Center SC had a data breach in 2014, in Illinois. A former affiliate of the covered entity's (CE) former business associate(BA), McKesson Corporation, that provided specialized billing services, unintentionally made records containing patient information potentially accessible on the Internet. The protected health information (PHI) of approximately 680 individuals was accessible using very specific Google search terms between December 1, 2013 and April 17, 2014. The former BA immediately safeguarded the information and made it inaccessible on the Internet. The former BA confirmed that the web server was properly removed from public Internet access, confirmed from its former affiliate that the data at issue was destroyed, contacted Google to ensure all caches pages were destroyed, and confirmed the information could not be accessed through any web search. The former BA also confirmed with its former affiliate that no other information was available via the computer server at issue or any other server. The CE confirmed that the former BA's policies related to data security were in compliance with the CE's data security requirements. The CE provided breach notification to HHS, affected individuals, and the media, and offered credit monitoring to the affected individuals. OCR obtained written assurances that the CE and BA implemented the corrective actions listed above.[source] | Midwest Orthopaedics at Rush, LLC had a data breach in 2014, in Illinois. On February 10, 2014, an unknown party gained unauthorized access to the personal email account of a physician at Midwest Orthopaedics at Rush, the covered entity (CE), disclosing protected health information (PHI) that affected approximately 1,256 individuals. The emails contained electronic PHI including names, physicians' surgical schedules, surgical descriptions, codes, dates and instructions. The CE provided breach notification to HHS, affected individuals, and the media. The CE also conducted an investigation and determined the root cause of the breach. Additionally, the CE disabled the physician's Gmail account to which the PHI was sent, and trained the physician and his staff on the use of the secure email. The CE revised email procedures by eliminating all external email addresses from the CE's distribution list of physicians and support staff and discontinued the use of outside email addresses for sending or receiving of PHI. OCR obtained documented assurances that the CE implemented the corrective actions listed above. [source] | |
Midwest Orthopedic Pain and Spine had a data breach in 2016, in Missouri. The information was breached via Network Server . [source] | Midwest Urological Group had a data breach in 2014, in Illinois. On May 30, 2014, an unencrypted laptop computer was stolen from a company closet. The laptop contained the protected health information (PHI) of approximately 982 individuals, including names and data from medical tests. The covered entity (CE) provided breach notification to HHS, affected individuals, and the media and also notified police. Following the breach, the CE sanctioned and retrained the employee responsible for securing the computer and implemented new policies and procedures to improve safeguards to PHI. OCR obtained written assurances that the CE implemented the corrective actions listed above. Location of breached information: Laptop Business associate present: No [source] | |
Milligan Chiropractic Group, Inc. d/b/a Del Mar Chiropractic Sports Group had a data breach in 2018, in California. The information was breached via Laptop . [source] | Mimeo.com had a data breach in 2014, in Maryland. Name, DOB, SSN, address were breached via Desktop Computer . [source] | |
Min Yi, M.D. had a data breach in 2014, in California. A desktop computer hard drive and a backup external hard drive containing the electronic protected health information (ePHI) of 4,676 individuals were stolen from the office of the covered entity (CE), Dr. K. Min Yi. The ePHI on the external hard drive included names, addresses, phone numbers, insurance identification numbers, social security numbers, checking account information, medical and surgical information, diagnosis and procedure codes, and dates of birth. The CE provided breach notification to HHS, the media, and affected individuals, and provided credit monitoring to patients who contacted her with privacy concerns. In response to the breach the CE improved physical safeguards, implemented revised administrative policies and encrypted ePHI. OCR's investigation resulted in the CE improving its HIPAA practices. Location of breached information: Other Portable Electronic Device Business associate present: No [source] | Mind Springs Health had a data breach in 2016, in Colorado. On January 8, 2016 a foreign transcription services subcontractor to Mind Springs Health's former business associate (BA), Stratton Consulting Services, Inc., mistakenly published electronic protected health information (ePHI) on the internet during a software update. The types of ePHI involved in the breach included names, dates of birth, medications, and physicians' notes, affecting 2,147 individuals who received treatment from the covered entity (CE) between January 2009 and March 2010. Following the breach, the subcontractor removed the information from the internet. The CE provided breach notification to HHS, affected individuals, and the media. Subsequent to the breach, the CE established BA agreements with its contractors. OCR provided technical assistance regarding relevant issues pursuant to the Privacy and Security Rules. Location of breached information: Network Server Business associate present: No [source] | |
Minneapolis Clinic of Neurology, Ltd. had a data breach in 2015, in Minnesota. On July 8, 2015, the covered entity (CE), Minneapolis Clinic of Neurology, Ltd., discovered that a laptop computer was missing from one of its clinics. The breach affected approximately 1,450 individuals and the types of protected health information (PHI) involved in the breach included patients' names and addresses. The CE provided breach notification to HHS, affected individuals and the media. Following the breach, the CE sanctioned the involved employee with a written warning, distributed its computer network and internet access policy to all employees, and retrained all employees ahead of its annual training. The CE also implemented policies and procedures contained in a new HIPAA Privacy and Security Handbook, increased technical and security safeguards on its mobile electronic devices, and updated the security on its virtual private network software. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | Minneapolis VA Health Care System had a data breach in 2014, in Minnesota. [source] | |
Mission City Community Network had a data breach in 2014, in California. In violation of the employer's policies, a workforce member of the covered entity (CE), Mission City Community Network, Inc., sent an unsecured email to a business associate (BA) containing the protected health information (PHI) of 7,800 individuals. The PHI included names, addresses, dates of birth, and insurance information. During the investigation, OCR determined that the disclosure to the BA for payment purposes was permissible, as the email reached the intended BA, and there was no evidence that PHI was impermissibly disclosed to any other party. OCR provided technical assistance to the CE. As a result of OCR's investigation, the CE initiated a review and improvements to its HIPAA practices. [source] | Missouri Dept. of Mental Health had a data breach in 2018, in Missouri. A business associate was not present. [source] | |
Mkenna Long & Aldridge had a data breach in 2014, in District Of Columbia. Name, address, wages, tax and ssn information, DOB, age, gender, ethnicity, visa and passport info were breached via Website . [source] | MN Urology had a data breach in 2017, in Minnesota. The information was breached via Email . [source] | |
MobilexUSA had a data breach in 2014, in Ohio. The information was breached via Paper/Films . [source] | Modern Gun School had a data breach in 2014, in Maryland. Names, financial information were breached via Website . [source] | |
Molina Healthcare of New Mexico, Inc. had a data breach in 2014, in New Mexico. On behalf of the covered entity (CE), Molina Healthcare of California Partner Plan, Inc., a business associate (BA) subcontractor, printed and mailed postcards to the CE's former members addressed generically to “Resident” and containing a tracking number, that in some cases, was the member's social security number. Approximately 4,744 individuals were affected by this breach. The CE provided breach notification to HHS, affected individuals, and the media and posted substitute notification on its website. It also offered affected individuals one year of free identity theft protection services. As a result of the incident, the CE revised and developed HIPAA policies and procedures to better safeguard protected health information (PHI) during mailing projects. It also counseled the workforce members involved in the incident pursuant to its policies. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | Molina Healthcare had a data breach in 2015, in California. Molina Healthcare has communicated to former members about a data breach that included their Social Security numbers. Molina said it contracted with a printing company to print postcards that contained information about benefits offered. Unfortunately the postcards did not contain names of the individuals, but addresses and Social Security numbers of the individual. [source] | |
MorshedEye, PLLC had a data breach in 2018, in Kentucky. The information was breached via Email . [source] | Morton Medical Center, PLLC had a data breach in 2016, in Washington. In March 2016, the covered entity (CE), Morton Medical Center, reported that a virus encrypted many of its merge documents and held them for ransom, preventing the CE from printing any documents that required merging data. An internal investigation revealed that the ransomware had been introduced into its systems through an “add-on” through the Internet. After paying the ransom, the hacker(s) released the CE's entire electronic protected health information (ePHI). The breach affected the ePHI of approximately 3,000 individuals; however, there were no indications that ePHI was actually uploaded or accessed. If the hackers accessed the ePHI, it would have contained names, addresses, demographic information and, possibly, some diagnostic information. Following the breach, the CE conducted an enterprise-wide analysis of the various risks to its ePHI and developed a risk management plan. The CE then overhauled its entire information technology system, focusing on strengthening its physical, administrative, and technical safeguards. The CE also re-trained its workforce members and implemented a new policy that prohibits Internet access for other than business reasons. [source] | |
Mosaic Medical had a data breach in 2015, in Oregon. [source] | Mosaic Medical had a data breach in 2015, in Oregon. An intruder entered the administrative office of the covered entity (CE) through a window. Nothing was stolen; however, the protected health information (PHI) of 2,202 individuals was stored in the office. The PHI involved in the breach included names, medical information, medical insurance information, addresses, phone numbers, and email addresses. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE moved its administrative office to another location with improved physical safeguards. In addition, the CE instructed staff on its procedures for securely storing PHI. OCR obtained assurances that the CE implemented the corrective action listed above. Location of breached information: Paper/Films Business associate present: No [source] | |
Mount Carmel Health System had a data breach in 2017, in Ohio. The information was breached via Email . [source] | Mount Sinai Beth Israel had a data breach in 2014, in New York. The information was breached via Laptop . [source] | |
MultiCare Health System had a data breach in 2017, in Washington. The information was breached via Email . [source] | Multilingual Psychotherapy Centers, Inc had a data breach in 2014, in Florida. An encrypted server was stolen from the covered entity (CE), Multilingual Psychotherapy Centers, Inc., on October 20, 2014, as a result of a break-in. The server contained the protected health information (PHI) of 3,500 individuals and included patients' names, dates of birth, social security numbers, addresses, and Medicaid ID numbers. The CE provided notice to HHS and individuals whose information was contained in the stolen server. Following this incident, the CE increased its physical safeguards, modified its policies, and developed a plan to train its workforce specifically regarding data security breaches. OCR determined the CE had adequate policies and procedures in place for securing electronic information via encryption. Under OCR's guidance, the CE provided media notice and altered its procedures to ensure such notification is performed in the event of a breach affecting more than 500 individuals.[source] | |
Multnomah County had a data breach in 2017, in Oregon. The information was breached via Email . [source] | Murali Menon, Privacy Manager Breach had a data breach in 2014, in California. [source] | |
MVP Health Care, Inc. had a data breach in 2017, in New York. The information was breached via Paper/Films . [source] | My Pediatrician, PA had a data breach in 2016, in Florida. A hacker gained access to the protected health information (PHI) for 2,385 of the covered entity's (CE) patients. The CE's business associate (BA), Bizmatics, Inc., informed the CE, My Pediatrician, PA, about this incident. The CE provided breach notification to HHS, affected individuals, and the media. The CE also created a website with information about the breach and posted substitute notification about the breach. To mitigate harm, the CE sent notice of the breach to Equifax, Transunion, and Experian and provided affected individuals with instructions for registering a fraud alert with a credit reporting agency and instructions on how to obtain a free annual credit report. The CE also trained its staff on HIPAA awareness and retained outside counsel to provide further training and to review its policies. The CE did not have a BA agreement with the BA at the time of the breach, but entered into an agreement with the BA on July 12, 2016. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | |
Myriad Genetic Laboratories, Inc. had a data breach in 2014, in Utah. An employee of the covered entity (CE), Myriad Genetic Laboratories, Inc., emailed unsecured protected health information (PHI) to his personal email account as a means of storing the information he used to carry out his job functions. The PHI of the affected 643 individuals included patients' names, dates of birth, addresses, physicians' name, genetic test results, test identification numbers, family and personal medical histories, and family pedigree information. The CE provided breach notification to HHS and affected individuals and also posted substitute notice of the breach. It also provided one year of free identify theft protection services to affected individuals. Following the breach, the CE revised its procedures for encrypting emails containing PHI and retrained the employee who had caused the breach. OCR provided technical assistance regarding the risk analysis and risk management requirements of the Security Rule. [source] | Napa Valley Dentistry had a data breach in 2016, in California. A business associate was not present. [source] | |
National Counseling Group had a data breach in 2016, in Virginia. The information was breached via Email . [source] | National Credit Adjusters, LLC had a data breach in 2014, in Maryland. Name, address, debt balance, dob, and ssn were breached via Website . [source] | |
National Mentor Healthcare, LLC. had a data breach in 2018, in Massachusetts. The information was breached via Other Portable Electronic Device . [source] | National Pain Institute had a data breach in 2015, in Florida. From July 13, 2013, to August 13, 2013, the covered entity (CE), National Pain Institute, distributed outdated computers to its employees for their personal use without first deleting all electronic protected health information (ePHI) from the computers. The computers contained the PHI of approximately 500 individuals, including names, addresses, dates of birth, diagnoses, and other treatment information. The CE provided breach notification to HHS, affected individuals, and the media. In response to the incident, The CE tracked the computers, repossessed those computers that it was able to locate, and obtained written acknowledgement from the former employees that the PHI from the computers was not used or disclosed to others. In addition, the CE improved safeguards by encrypting all computers, upgrading the malware and software of desktop computers, improving network and email security, improving identity management, and automating and standardizing security for devices containing ePHI. The CE also updated its HIPAA policies and procedures, including a policy for responding to security incidents. OCR obtained assurances that the CE implemented the corrective actions listed. [source] | |
National Pain Institute had a data breach in 2015, in Florida. Name, address, ssn, and w2 tax info were breached. [source] | National Safety Council had a data breach in 2017, in Illinois. Name, address, ssn, w2 tax info were breached via Email . [source] | |
National Seating & Mobility, Inc. had a data breach in 2015, in Tennessee. On December 22, 2017, National Stores received an alert that its point-of-sale systems were affected by malware, and that customer payment card information may have been accessed without authorization. National Stores immediately launched an investigation and engaged digital cybersecurity firms to assist with the investigation. National Stores also contacted the Federal Bureau of Investigation and payment card brands to prevent fraudulent activity on payment cards that may have been affected. The affected payment card holders have not yet been identified, although National Stores is diligently attempting to do so. The number of affected North Carolina residents is therefore unknown. We have entered the number "1" as there is not a mechanism to submit the report with an unknown number. [source] | Nationstar Mortgage LLC d/b/a Champion Mortgage had a data breach in 2014, in Maryland. Name, address, and account number were breached via paper . [source] | |
Nephropathology Associates, PLC had a data breach in 2015, in Arkansas. The information was breached via Laptop. [source] | Network Health had a data breach in 2017, in Wisconsin. The information was breached via Email . [source] | |
Network Pharmacy Knoxville had a data breach in 2014, in Tennessee. The information was breached via Laptop . [source] | Neurology Physicians LLC had a data breach in 2016, in Maryland. A business associate was not present. [source] | |
New Dimension Group, LLC had a data breach in 2015, in North Carolina. The information was breached via Email. [source] | New England Baptist Health had a data breach in 2018, in Massachusetts. The information was breached via Email . [source] | |
New Jersey Spine Center had a data breach in 2016, in New Jersey. The information was breached via Electronic Medical Record, Network Server. [source] | New Mexico Heart Institute had a data breach in 2016, in New Mexico. The information was breached via Other Portable Electronic Device . [source] | |
New Mexico VA Health Care System had a data breach in 2014, in New Mexico. The information was breached via Paper/Films . [source] | New West Health Services d/b/a New West Medicare had a data breach in 2016, in Montana. OCR opened an investigation of the covered entity (CE), New West Health Services, dba New West Medicare, after it reported that an employee's unencrypted laptop computer was stolen from a hotel meeting room. The types of electronic protected health information (ePHI) involved in the breach included demographic information, social security numbers, Medicare claim numbers, financial information, diagnoses, medical histories, and prescription information, and affected 28,209 individuals. The CE provided breach notification to HHS, affected individuals, and the media and provided individuals' with free credit monitoring and identity theft protection services. Following the breach, the CE improved safeguards by recalling all of its laptops to ensure they were encrypted, installing geo-location capabilities on all of its laptops, and installing remote wiping software on all of its company-issued BlackBerry devices. The CE also sanctioned the employee whose laptop was stolen, retrained its staff on HIPAA privacy and security requirements, and created a new data incident response plan. OCR obtained assurances that the CE implemented the corrective actions noted above. Due to financial considerations, the CE announced that it will cease all operations in 2017 after it fulfills its 2016 insurance plan requirements. [source] | |
New York City Health & Hospitals Corporation had a data breach in 2014, in New York. The information was breached via Paper/Films . [source] | New York City Health and Hospitals Corporation - Coney Island Hospital had a data breach in 2017, in New York. The information was breached via Paper/Films . [source] | |
New York State Office of Mental Health had a data breach in 2015, in New York. The information was breached via Laptop . [source] | New York State Office of Mental Health had a data breach in 2016, in New York. The information was breached via Network Server . [source] | |
New had a data breach in 2015, in Florida. [source] | Newkirk Products, Inc. had a data breach in 2016, in New York. The information was breached via Network Server . [source] | |
NFP Maschino, Hudelson & Associates had a data breach in 2014, in Oklahoma. An unencrypted laptop was stolen from the vehicle of an employee of Maschino, Hudelson & Associates, a broker and business associate (BA) of the covered entity (CE), Aetna. The laptop contained the protected health information (PHI) of 3,814 of the CE's customers. The types of PHI involved in the breach included names, dates of birth, addresses, social security numbers and account information. The BA provided breach notification to affected individuals and the media. OCR provided technical assistance to the CE regarding the requirements for notification to HHS. OCR verified that the CE had a proper BA agreement in place at the time of this breach. [source] | Nielsen had a data breach in 2014, in New York. Name and ssn were breached via email . [source] | |
North American Title Company had a data breach in 2014, in Maryland. Information associated with loan documents was breached via paper. [source] | North Big Horn Hospital had a data breach in 2014, in Wyoming. [source] | |
North Dallas Urogynecology, PLLC. had a data breach in 2015, in Texas. The covered entity (CE), North Dallas Urogynecology, reported the theft of several items and four unencrypted laptops as a result of a break-in. The incident was immediately reported to the police and an investigation ensued. Approximately 678 patients' protected health information (PHI) was affected by the breach, which included patient's names, social security numbers, dates of birth, and lab results. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach the CE increased security within the office and implemented additional physical, technical, and administrative safeguards to ensure the security of electronic PHI. All laptops have encryption technology. In addition, all workforce members were trained or retrained concerning the requirements for compliance with the Privacy, Security, and Breach Notification Rules. OCR obtained assurances that the CE implemented the corrective actions listed. [source] | North East Medical Services (NEMS) had a data breach in 2015, in California. [source] | |
North Ottawa Medical Group had a data breach in 2016, in Michigan. The information was breached via Network Server . [source] | Northeast OB/GYN Associates had a data breach in 2017, in Texas. The information was breached via Desktop Computer, Laptop, Network Server. [source] | |
Northfield Hospital & Clinics had a data breach in 2014, in Minnesota. The information was breached via Paper/Films . [source] | Northstar Healthcare Acquisitions LLC had a data breach in 2016, in Texas. [source] | |
Northwest Community Healthcare had a data breach in 2016, in Illinois. The information was breached via Other Portable Electronic Device . [source] | Northwest Oncology & Hematology, S.C. had a data breach in 2016, in Illinois. The information was breached via Email . [source] | |
Northwest Primary Care Group had a data breach in 2015, in Oregon. The information was breached via Network Server. [source] | Northwest Rheumatology had a data breach in 2017, in Arizona. The information was breached via Network Server . [source] | |
Northwestern Memorial HealthCare had a data breach in 2014, in Illinois. A business associate was not present. [source] | NOVA Chiropractic & Rehab Center had a data breach in 2014, in Virginia. Novant Health Gaffney Family Medical Care informed patients of a data breach when their offices were broken into and two of the facilities laptops were stolen.The information on the laptops was not disclosed. [source] | |
Novo Nordisk Inc. had a data breach in 2014, in Maryland. Name, email address, ssn were breached via Desktop Computer . [source] | NRAD Medical Associates, P.C. had a data breach in 2014, in New York. The information was breached via Desktop Computer and Other Portable Electronic Device . [source] | |
NYC Health + Hospitals/Harlem had a data breach in 2018, in New York. The information was breached via Laptop . [source] | NYU Hospitals Center had a data breach in 2014, in New York. The information was breached via Laptop . [source] | |
NYU Urology Associates had a data breach in 2014, in New York. The information was breached via Other Portable Electronic Device . [source] | Oak Cliff Orthopaedic Associates had a data breach in 2016, in Texas. The information was breached via Email. [source] | |
Oceans Acquisition, Inc. had a data breach in 2015, in Texas. O'Charley's Restaurant and Bar notified customers of data breach when a third party security firm discovered unauthorized access to their payment card system. Between March 19, 2016 and April 8, 2016 customers who used their debit or credit card information could be the target of identity theft. The information compromised included data found on the magnetic strip of the card which would include the cardholder names and card numbers. The following locations were potentially compromised. O'Charley's Restaurants locatd at 930 Windham Court, Boardman Ohio and 2077 Interchange Drive, Erie Pennsylvania. The number of debit/credit cards affected has not yet been released. [source] | Office of Dr. David Elbaum had a data breach in 2017, in California. The information was breached via Paper/Films . [source] | |
OH Muhlenberg, LLC had a data breach in 2015, in Kentucky. The information was breached via Desktop Computer, Email, Laptop, Network Server, Other Portable Electronic Device. [source] | OhioHealth had a data breach in 2015, in Ohio. On May 29, 2015, the covered entity (CE), OhioHealth, discovered that an unencrypted portable computer drive (‘thumb drive”) was missing. This breach affected approximately 1,006 individuals. The types of protected health information (PHI) involved in the breach included patients' names, medical record numbers, names of insurance companies, addresses, dates of birth, physicians' names, referral and treatment dates, type of procedures, and in certain limited instances, clinical information and social security numbers. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE sanctioned and retrained the employee who lost the thumb drive, suspended use of thumb drives in the involved department, and retrained employees. The CE also revised its policies on mobile storage device security and usage and on disposition of thumb drives. Additionally, the CE encrypted mobile storage devices and revised and launched annual compliance education for its employees. OCR obtained documentation that the CE implemented the corrective actions steps noted above.[source] | |
Oklahoma City Indian Clinic had a data breach in 2014, in Oklahoma. The information was breached via Network Server. [source] | Onco360 and CareMed Specialty Pharmacy had a data breach in 2018, in Kentucky. The information was breached via Email . [source] | |
Oncology Consultants, P.A. had a data breach in 2017, in Texas. The information was breached via Desktop Computer, Email, Laptop, Network Server. [source] | Oneida Tribe of Indians of Wisconsin had a data breach in 2016, in Wisconsin. Password manager and single sign-on provider OneLogin has been hacked, the company has confirmed.In a brief blog post, the company's chief security officer Alvaro Hoyos said that it had detected unauthorized access to OneLogin data in our The blog post had no further information or technical details about the incident -- though, the post omitted that hackers had stolen sensitive customer data, which was only cursorily mentioned in an email to customers, seen by ZDNet.OneLogin believes that all customers served by our US data center are affected and customer data was potentially compromised, the email read.Hackers have the ability to decrypt encrypted data, says a support page, accessible only to OneLogin customers (a copy of the post was published online).The company has advised customers to change their passwords, generate new API keys for their services, and create new OAuth tokens -- used for logging into accounts -- as well as to create new security certificates. The company said that information stored in its Secure Notes feature, used by IT administrators to store sensitive network passwords, can be decrypted.But questions remain over how the hackers had access to data that could be decrypted in the first place. [source] | |
Onsite Health Diagnostics (OHD) had a data breach in 2014, in Texas. The information was breached via Network Server . [source] | Open Cities Health Center had a data breach in 2014, in Minnesota. The information was breached via Email. [source] | |
OppenheimerFunds Services had a data breach in 2014, in Maryland. Name, account number, ssn were breached. [source] | Options Counseling Center had a data breach in 2014, in New Jersey. The information was breached via Portable Electronic Device. [source] | |
OptumHealth New Mexico had a data breach in 2016, in Minnesota. The information was breached via Other Portable Electronic Device . [source] | OptumRx, Inc. had a data breach in 2016, in California. The information was breached via Laptop . [source] | |
Orchid MPS Holdings, LLC Welfare Benefit Plan had a data breach in 2016, in Michigan. The information was breached via Paper/Films . [source] | Orlando Health, Inc. had a data breach in 2014, in Florida. [source] | |
Orlantino Dyoco, M.D. had a data breach in 2015, in California. The office of Olartino Dyoco, M.D. notified patients of a data breach when his offices were burglarized and several computers were stolen that contained patient information used for billing. The information compromised included names, addresses, birth dates, telephone numbers, insurance numbers, treatment codes, and billing information. The incident has been reported to the authorities. [source] | Orleans Medical Clinic had a data breach in 2016, in Indiana. The information was breached via Network Server . [source] | |
Orthopedics NY, LLP had a data breach in 2017, in New York. A business associate was not present. [source] | OrthoWest, Ltd. had a data breach in 2018, in Ohio. The information was breached via Network Server . [source] | |
Otolaryngology Associates of Central New Jersey, P.C. had a data breach in 2017, in New Jersey. A business associate was not present. [source] | Our Lady of the Angels Hospital had a data breach in 2017, in Louisiana. The information was breached via Electronic Medical Record . [source] | |
P. F. Chang's China Bistro had a data breach in 2014, in Arizona. Name, credit card info were breached via Payment card system . [source] | P.F. Chang's had a data breach in 2014, in Maryland. Name, debit/credit card info were breached via Payment card system . [source] | |
Pacific Alliance Medical Center had a data breach in 2017, in California. The information was breached via Network Server . [source] | Pacific Gas and Electric Company had a data breach in 2016, in California. [source] | |
Pain Treatment Centers of America had a data breach in 2016, in Arkansas. OCR opened an investigation of the covered entity (CE), Pain Treatment Centers of America, after it reported a hacking attacking on its business associate's (BA), Bizmatics, data servers. This breach resulted in unauthorized access to the BA/s customer records including those of the CE. The breach encompassed 17,339 individuals' information, which included individuals' names, addresses, dates of birth, driver's license numbers, social security numbers, claims information, diagnoses/conditions, lab results, medications and other treatment information. The CE provided breach notification to HHS, affected individuals, and the media and also provided and identity theft and credit monitoring service to affected individuals. As a result of OCR's investigation, the CE updated its BA agreement with the BA to reflect all requirements of 45 C.F.R. §§ 164.314 (a) and 164.504(a). [source] | Pair Networks Inc. had a data breach in 2014, in Pennsylvania. A business associate was present. [source] | |
Palomar Health, Privacy Manager Breach had a data breach in 2014, in California. [source] | Papa John's USA, Inc. had a data breach in 2014, in Maryland. [source] | |
Park Hill School District had a data breach in 2014, in Maryland. Name, ssn, state identification number, and health plan insurance number were breached via Portable device . [source] | Park 'N Fly had a data breach in 2014, in Maryland. Name and payment card info were breached. [source] | |
Partners HealthCare System, Inc. had a data breach in 2015, in Massachusetts. The information was breached via Network Server . [source] | Partners HealthCare System, Inc. had a data breach in 2018, in Massachusetts. The information was breached via Desktop Computer . [source] | |
Partners In Nephrology & Endocrinology, P.C. had a data breach in 2014, in Pennsylvania. A business associate was not present. [source] | PathGroup had a data breach in 2016, in Tennessee. A business associate was not present. [source] | |
Pathway to Hope had a data breach in 2015, in Florida. The covered entity (CE), Pathway to Hope, discovered in January 2015, that a former employee emailed the protected health information (PHI) of 600 individuals to her personal email account, before her last day of employment with the CE for the purpose of building her own practice. The types of PHI in the email included the full names, referral sources, insurance information, and general diagnoses/conditions (i.e. mental health/substance abuse). The CE provided breach notification to HHS and to affected individuals. Media notice was not required. OCR provided technical assistance to the CE regarding the Privacy, Security and Breach Notification Rules. In response to the breach, the CE counseled workforce members, improved its training program, substantially revised its policies and procedures, hired a compliance officer, and began requiring that employees sign non-compete, non-solicitation confidentiality agreements. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | Pathways Professional Counseling had a data breach in 2015, in Alabama. Pathways Counseling Center has notified patients of a data breach when a company laptop assigned to an employee was stolen from the employees car on September 25, 2015.The information contained on the laptop included patient names, Social Security numbers, dates of birth, addresses, diagnoses and/or clinical information, names of treating physician names, phone numbers, email addresses, demographic information, insurance information, types of treatements, prescription medication.Pathways is offering one year free of credit monitoring services. [source] | |
Patients Choice had a data breach in 2017, in Texas. The information was breached via Network Server . [source] | Paul C. Gering, Jr., M.D. had a data breach in 2017, in Oregon. The information was breached via Desktop Computer . [source] | |
Paytime Harrisburg, Inc. DBA Paytime, Inc. had a data breach in 2014, in Pennsylvania. The information was breached via Website. [source] | PCA Skin had a data breach in 2017, in Arizona. Name, address, ssn, w2 tax info were breached via Email . [source] | |
Peabody Retirement Community had a data breach in 2014, in Indiana. The information was breached via Email and Network Server . [source] | PeaceHealth had a data breach in 2015, in Washington. A former PeaceHealth mployee continued to access the electronic protected health information (ePHI) of the covered entity's (CE) patients through websites used for third-party prior authorization and insurance verification. Approximately 1,407 individuals were affected by the breach. The types of ePHI involved in the breach included names, addresses, dates of birth, social security numbers, diagnoses/conditions, medications, medical record numbers, and payor identification numbers. In response to the breach, the CE implemented database tracking for employees who have third party portal access, so that the database will alert management when an employee leaves employment and the portal companies will be immediately contacted to terminate access. The CE provided breach notification to HHS, affected individuals, and the media. The CE also provided one year of free credit monitoring for those individuals whose social security numbers were included in the breach. OCR provided the CE with technical assistance regarding the risk analysis and risk management provisions of the Security Rule.[source] | |
PeaceHealth had a data breach in 2017, in Washington. The information was breached via Electronic Medical Record . [source] | Peachtree Neurological Clinic, P.C. had a data breach in 2017, in Georgia. The information was breached via Network Server . [source] | |
Peachtree Orthopaedic Clinic had a data breach in 2016, in Georgia. The information was breached via Network Server . [source] | Pediatric Associates had a data breach in 2015, in Florida. The covered entity (CE), Pediatric Associates, discovered that a binder containing paper logs of patient record releases was missing on January 24, 2015. After a search and investigation, the CE determined that most likely the binder was unintentionally discarded. The types of protected health information (PHI) contained in the logs included patients' names, internal chart numbers, recipients of releases, and explanations for the record release (i.e. “parent requested”). The CE provided breach notification to HHS, affected individuals, and the media. In response to the breach, the CE changed its procedures to require that record releases be logged electronically. The CE archived or shredded all paper record release logs. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Paper/Films Business associate present: No [source] | |
Pediatric Gastroenterology Consultants had a data breach in 2014, in Colorado. On October 16, 2014, an employee of the covered entity (CE), Pediatric Gastroenterology Consultants, P.C., discovered that a laptop owned by the CE had been stolen from his vehicle. The laptop was password-protected but unencrypted, and it contained the electronic protected health information (ePHI) of approximately 5,000 individuals. Specifically, it contained patients' first and last names, dates of birth, dates of service, and medical information including, medical histories, lab test results, diagnoses, and medical treatment recommendations. The CE provided breach notification HHS, affected individuals, the media. Following the breach, the CE implemented corrective actions, such as encryption and employee security training, to prevent similar breaches from occurring in the future. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Laptop Business associate present: No [source] | Pediatric Gastroenterology, Hepatology & Nutrition of Florida, P.A. had a data breach in 2015, in Florida. [source] | |
Pediatric Group LLC had a data breach in 2015, in Illinois. The information was breached via Network Server . [source] | Pediatric Healthcare Solutions, a Division of ProHEALTH had a data breach in 2014, in New York. The information was breached via Network Server . [source] | |
Penn Medicine had a data breach in 2018, in Pennsylvania. The information was breached via Laptop . [source] | Penn State Milton S. Hershey Medical Center had a data breach in 2014, in Pennsylvania. An employee of the covered entity (CE), Penn State Milton S. Hershey Medical Center, downloaded protected health information (PHI) onto an unsecured flash drive and used the device in his personal computer to complete work which he then emailed to the CE using his personal email account. The types of PHI involved in the breach included the demographic and clinical information for 1,801 individuals. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE performed a risk assessment and updated encryption measures. The CE also reminded all clinical laboratory staff and faculty of expected practices pertaining to safeguarding PHI, and provided staff a listing of the relevant policies concerning encryption and electronic messaging and links to the corresponding policies. As a result of OCR's investigation, the CE submitted to OCR copies of its policies regarding use of personal devices and emails, storing PHI on third party owned or managed media and use of approved electronic connections, systems and/or services. OCR verified that appropriate policy was in place at the time of the incident and the employee did not follow the policy. OCR obtained assurances that the CE has implemented the corrective actions listed above. [source] | |
Performance Physical Therapy and Wellness had a data breach in 2017, in Connecticut. The information was breached via Email . [source] | Phoenix Dental Care had a data breach in 2016, in Tennessee. The information was breached via Paper/Films . [source] | |
Physicians Health Plan of Northern Indiana, Inc. had a data breach in 2015, in Indiana. The covered entity (CE) mistakenly mailed protected health information (PHI) to unauthorized individuals following a folder/inserter machine error. Approximately 1,708 individuals that include all dependents of the CE's subscribers were affected by this breach. The erroneous billing statement mailing included names, addresses, PHP member identification numbers, and premium amounts. The CE provided breach notification to HHS, affected individuals, and the media. To prevent a similar breach from happening in the future, the CE implemented a formal audit checklist that requires independent verification by mailroom personnel. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Paper/Films Business associate present: No [source] | PIH Health Hospital - Whittier had a data breach in 2015, in California. Documents containing the protected health information (PHI) of 826 PIH Health Hospital patients were stolen from a resident doctor's private vehicle. The PHI involved in the breach included names, dates of birth, diagnoses, primary providers, hospital unist, and assigned nurses names. The covered entity (CE) provided breach notification to HHS, affected individuals, and the media. In response to the breach, the CE sanctioned and retrained the doctor responsible for the breach, trained all residents, developed a new policy prohibiting residents from taking PHI off-campus, and developed signage reminding residents of the new policy. OCR obtained written assurances of breach notifications provided and corrective actions taken. Location of breached information: Paper/Films Business associate present: No [source] | |
Pittman Family Dental had a data breach in 2015, in Ohio. An unauthorized third-party accessed protected health information (PHI), according to the forensic firm that the covered entity (CE), Pittman Family Dental, retained to investigate abnormal activity on its computer server. Approximately 8,830 individuals were affected by the breach. The server included full names, social security numbers (of 5,007 individuals), driver's license numbers, dates of birth, home addresses, treatment notes, and insurance information. The CE provided breach notification to HHS, affected individuals, and the media. To prevent a similar breach from happening in the future, the CE scrubbed and reinstalled its server, installed an anti-virus/malware solution, and contracted with a company to provide an updated risk analysis and additional training. OCR obtained written assurances that the CE implemented the corrective actions listed above. Location of breached information: Network Server Business associate present: No [source] | Placemark Investments, Inc. had a data breach in 2014, in Maryland. The information was breached via Website. [source] | |
Planned Parenthood of Greater Washington and North Idaho had a data breach in 2016, in Washington. In August 2016, the covered entity (CE), Planned Parenthood of Greater Washington and North Idaho (PPGWNI), reported that its business associate (BA), athenahealth, inc., inadvertently sent some e-mails, inviting individuals to the CE's online portal, to the wrong addresses, The e-mails included the first and last names of 10,700 individuals. Upon discovery of the breach, the CE and BA shut down the portal to determine the root cause of the breach and to implement additional safeguards. The CE provided breach notification to HHS, affected individuals, and the media. The BA and CE reestablished the online portal after re-confirming permissions and processes related to the business associate contract/relationship. OCR obtained documented assurances that the CE and BA implemented the corrective actions noted above. [source] | Planned Parenthood of the Heartland had a data breach in 2016, in Iowa. The information was breached via Paper/Films . [source] | |
Planned Parenthood Southwest Ohio had a data breach in 2015, in Ohio. Planned Parenthood mistakenly disposed of binders containing protected health information. The information included archived prescription dispending logs and lab test logs. [source] | Pointe Medical Services, Inc. had a data breach in 2016, in Florida. Name, contact info, tax info, ssn, bank info were breached. [source] | |
Policy Studies, Inc. / Postal Center International, Inc. had a data breach in 2014, in Florida. The information was breached via Paper/Films . [source] | Polish Falcons of America had a data breach in 2014, in Pennsylvania. Name, ssn, credit card info were breached via Laptop. [source] | |
Porter, MD, Steven had a data breach in 2014, in Utah. The information was breached via Network Server . [source] | Portland VA Medical Center had a data breach in 2014, in Oregon. [source] | |
Power Equipment Direct, Inc. had a data breach in 2014, in Maryland. The information was breached via Website . [source] | PracMan, Inc. had a data breach in 2014, in Alabama. [source] | |
PracMan, Inc. had a data breach in 2014, in Alabama. The information was breached via Network Server . [source] | Pratap S. Kurra, M.D. had a data breach in 2016, in California. The information was breached via Paper/Films . [source] | |
Precision Planting LLC had a data breach in 2014, in Maryland. An office burglary that occurred on or around January 24 resulted in the loss of a laptop. The laptop held client records. The company sent a breach notification through Facebook and email. No financial information was on the laptop, but Preferred Skin Solutions still warned their clients about the risk of identity theft. [source] | PREIT had a data breach in 2014, in Maryland. The information was breached via Website. [source] | |
Premier Family Care I, Inc. had a data breach in 2016, in Texas. The information was breached via Paper/Films . [source] | Premier Healthcare, LLC had a data breach in 2016, in Indiana. The information was breached via Laptop . [source] | |
Presence Health had a data breach in 2014, in Illinois. The information was breached via Paper/Films . [source] | Presence St. Joseph's Medical Center had a data breach in 2014, in Illinois. The information was breached via Paper/Films . [source] | |
Prestera Center for Mental Health Services, Inc. had a data breach in 2018, in West Virginia. The information was breached via Email . [source] | Preventice Services, LLC had a data breach in 2016, in Texas. A business associate was not present. [source] | |
Prima CARE, PC had a data breach in 2015, in Massachusetts. The information was breached via Email. [source] | Prima Medical Foundation had a data breach in 2016, in California. Medical Practice Concepts, Inc., a business associate (BA) that provides the covered entity (CE), Prima Medical Foundation, with business and health care system services, experienced a ransomware infection. A third party forensic firm hired to investigate this incident found no evidence that protected health information was accessed, viewed, or transferred. However, the BA informed the CE that during the data restoration process one of their backup systems failed, causing the loss of certain information documented by the CE's physicians during the period from July 11, 2016 through July 26, 2016. OCR has consolidated the review of this case into a review of the BA. [source] | |
Primary Care Specialists, Inc. had a data breach in 2017, in Tennessee. The information was breached via Network Server . [source] | Primary Health Care, Inc. had a data breach in 2018, in Iowa. The information was breached via Email . [source] | |
Primerica had a data breach in 2014, in Maryland. Name, dob, address, ssn, dln were breached via Laptop . [source] | PrimeWest Health had a data breach in 2016, in Minnesota. The information was breached via Network Server . [source] | |
Princeton Pain Management had a data breach in 2017, in New Jersey. The information was breached via Desktop Computer and Electronic Medical Record. [source] | ProAssurance Mid-Continent Underwriters, Inc. had a data breach in 2014, in Texas. Name and ssn were breached via Website . [source] | |
Professional Dermatology Care, P.C. had a data breach in 2016, in Virginia. The information was breached via Network Server . [source] | Project Vida Health Center had a data breach in 2015, in Texas. Encrypted servers containing the electronic protected health information (ePHI) of approximately 7,7A0 individuals were stolen from the covered entity's (CE), Project Vida Health Center facility. The thieves by-passed the locks and the sensors to the facility's security system by entering through a window that was secured with steel bars. The ePHI included patients' names, dates of birth, social security numbers, addresses, and zip codes. The CE provided breach notification to HHS, affected individuals and the media. Notices to the public were provided in English and Spanish. Following the breach incident, the CE transitioned from a server based systems to a cloud hosted system. The CE demonstrated that it immediately acted to recover data for the purpose of business continuity. The CE provided documentation of the new security measures implemented to sufficiently reduce the risks and vulnerabilities to ePHI. In addition the CE encrypted data and implemented access controls on its information systems. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Network Server Business associate present: No [source] | |
Prosthetic & Orthotic Care, Inc. had a data breach in 2016, in Missouri. The information was breached via Network Server . [source] | PruittHealth Home Health -- Low Country had a data breach in 2016, in South Carolina. [source] | |
PruittHealth Hospice Beaufort had a data breach in 2016, in South Carolina. On April 11, 2016, the covered entity (CE), PruittHealth Hospice, experienced a break-in at its Beaufort offices. The perpetrators entered the offices by breaking a side window and then broke into the file cabinets, although it did not appear that any medical records were disturbed or taken. The perpetrators had the opportunity to access the paper medical records for 1,437 individuals. The types of protected health information (PHI) contained in the paper medical records included patients' names, addresses, social security numbers, dates of birth, dates of service, service locations, and other clinical information. Following the breach, the CE reviewed its policies and trained staff on data privacy and information security. Additionally, the CE initiated a criminal investigation with local law enforcement. It improved physical safeguards by replacing the broken window, purchasing file cabinets with more secure locks, and purchasing a monitored security system. The CE provided breach notification to HHS, all patients it ever served, and the media. It also provided substitute notice on its website and set up a toll free information line for affected individuals. OCR obtained assurances that the CE implemented the corrective actions listed above.[source] | PruittHealth Pharmacy Services had a data breach in 2014, in Georgia. A manager's unencrypted laptop computer was stolen from the back seat of an employee's car. The laptop contained the protected health information (PHI) of 841 individuals and included names, possible diagnoses, prescription names, dates of service, and service locations. The covered entity (CE) has improved safeguards by encrypting devices and employing devices that do not allow local storage. The CE has also revised its privacy and security policies and re-trained employees. OCR has consolidated this review into a compliance review that involves the same corporate entity and another stolen unencrypted laptop. [source] | |
PST Services Inc, a McKesson Co. had a data breach in 2014, in Georgia. The information was breached via Network Server . [source] | PT Northwest, LLC had a data breach in 2015, in Oregon. The covered entity (CE), PT Northwest, LLC inadvertently emailed a questionnaire to patients that was copied to 1,500 patients. The e-mail should have been distributed to recipients as a blind carbon copy. Some of the e-mail addresses contained patients' names. Following the breach, the CE sanctioned the employee who was responsible for the impermissible disclosure. The CE provided breach notification to HHS, affected individuals, and the media. As a result of OCR's investigation, the CE conducted companywide annual HIPAA training, and started the process of conducting in person follow-up HIPAA trainings to be completed by December 2015. Location of breached information: Email Business associate present: No [source] | |
Public Education Employees' Health Insurance Plan had a data breach in 2016, in Alabama. Name, address, phone or email, ssn, financial account numbers were breached. [source] | PVHS-ICM Employee Health and Wellness, LLC as covered entity and business associate had a data breach in 2014, in Colorado. The information was breached via Network Server . [source] | |
Quad/Med, LLC had a data breach in 2018, in Wisconsin. The information was breached via Electronic Medical Record . [source] | QuadMed had a data breach in 2018, in Wisconsin. The information was breached via Electronic Medical Record . [source] | |
QUALITY-CARE PHARMACY had a data breach in 2018, in California. The information was breached via Desktop Computer, Other, Other Portable Electronic Device, Paper/Films. [source] | Quarles & Brady, LLP had a data breach in 2016, in Wisconsin. The information was breached via Laptop . [source] | |
Quraishi, Nisar A had a data breach in 2014, in New York. The covered entity (CE), Tribeca Medical Center, reported that on October 21, 2014, patients' medical records stored in the CE's storage shed were stolen. The breach affected potentially 20,000 patients and the protected health information (PHI) included names, addresses, zip codes, telephone numbers, dates of birth, social security numbers, health plan information, diagnoses, medical and clinical histories. The CE provided breach notification to HHS, affected individuals, and the media. As a result of OCR's investigation, the CE has ceased storing PHI in the storage unit. [source] | Radiology Regional Center, PA had a data breach in 2016, in Florida. The information was breached via Email. [source] | |
Rady Children's Hospital - San Diego had a data breach in 2014, in California. The information was breached via Email. [source] | Rainbow Children's Clinic had a data breach in 2016, in Texas. The information was breached via Network Server . [source] | |
Rainier Surgical, Incorporated had a data breach in 2015, in Texas. OCR opened an investigation of the covered entity (CE), Rainier Surgical, Inc., after it reported that a file drawer with explanations of benefits containing the protected health information (PHI) of 4,290 individuals was stolen from a warehouse. The PHI included names, addresses, dates of birth, health insurance information, explanations of benefits, and in some cases, credit card numbers and social security numbers. Upon discovering the breach, the CE filed a police report. The CE provided substitute notice and media notification in the localities with greater than 500 individuals affected. The CE offered one year of free credit monitoring services to individuals whose social security numbers may have been compromised. Following this breach, the CE retrained employees, reviewed its policies and procedures, and began storing some PHI with an on-site third party secure storage vendor. OCR confirmed that the CE took the actions described above.[source] | Raymond Mark Turner, M.D. had a data breach in 2015, in Nevada. One unencrypted laptop computer was stolen during business hours while the office of Dr. Robert Mark Turner was in the process of updating and encrypting its computers. A file on the stolen laptop contained the electronic protected health information (ePHI) of 2,153 individuals which included names, addresses, dates of birth, social security numbers, driver's license numbers, health insurance information, and records of medical treatment. The covered entity (CE) provided breach notification to HHS, affected individuals, and the media and provided credit monitoring and identity theft protection to affected individuals. In response to the breach, the CE improved physical safeguards and enhanced technical safeguards by implementing an encryption management program for all computer systems. OCR reviewed the CE's HIPAA risk assessment and provided technical assistance on the required elements of a risk analysis and risk management plan.[source] | |
ReachOut Home Care [Case #16687] had a data breach in 2014, in Kentucky. The information was breached via Laptop . [source] | Reading Health System had a data breach in 2014, in Pennsylvania. [source] | |
Reading Partners had a data breach in 2014, in Maryland. [source] | Record Assist, LLC had a data breach in 2014, in Maryland. The information was breached via Website. [source] | |
Rederal Direct Tax Services had a data breach in 2017, in Indiana. Name, dob, ssn were breached via Website . [source] | Reeves Inernational, Inc. had a data breach in 2014, in Maryland. Name, address, website userName, payment card info were breached via Website . [source] | |
REEVE-WOODS EYE CENTER had a data breach in 2014, in California. The information was breached via Laptop. [source] | Rentrak Corporation had a data breach in 2014, in Maryland. Name, address, social security number, and title and salary information were breached via Laptop . [source] | |
Republic Bank & Trust Company had a data breach in 2014, in Maryland. Name, address, telephone number, ssn, dln were breached via paper . [source] | Research Integrity, LLC had a data breach in 2014, in Kentucky. The information was breached via Other Portable Electronic Device . [source] | |
RevSpring, Inc. had a data breach in 2014, in Michigan. Due to a printing error at the covered entity's (CE) business associate (BA), RevSpring, Inc., patients received billing statements containing other patients' protected health information (PHI). The breach affected approximately 3,000 individuals. The types of PHI involved in the breach included names, account numbers, balances owed, procedure codes, procedure descriptions, providers' names, and dates of services. Following the breach, the CE obtained assurances from the BA that additional safeguards would be implemented to prevent future disclosures. OCR reviewed the CE's policies and procedures to ensure compliance with the Privacy and Security Rules. Location of breached information: Paper/Films Business associate present: Yes [source] | RGH Enterprises, Inc. had a data breach in 2018, in Ohio. The information was breached via Paper/Films . [source] | |
Riaz Baber, M.D., S.C. had a data breach in 2017, in Illinois. The information was breached via Paper/Films . [source] | RISE Wisconsin, Inc. had a data breach in 2018, in Wisconsin. The information was breached via Network Server . [source] | |
Rite Aid Store 01617 had a data breach in 2016, in New York. From November 19, 2014, through November 18, 2015, an employee of the covered entity (CE), Rite Aid Pharmacy Store 01617, obtained customers' credit card information along with other personal identifiers, which he used to commit credit card fraud. The incident affected 976 individuals. The electronic protected health information (ePHI) involved included patients' names, addresses, dates of birth, and credit card information. As a result of the breach, the CE conducted an internal investigation, sanctioned the employee responsible for the incident, and revised its policy regarding handling of payment cards. The CE provided breach notification to HHS, affected individuals, and the media and provided one year free of credit monitoring services. OCR provided the CE with technical assistance regarding the requirements of the HIPAA Security Rule with respect to risk analyses, development of risk management plans, and implementation of procedures to review records of information system activity, grant access to ePHI, and deploy audit controls. In this case, employee sanctions included termination of employment. [source] | Rite Aid Store 5256 had a data breach in 2014, in Washington. [source] | |
RiverMend Health, LLC had a data breach in 2017, in Georgia. The information was breached via Email . [source] | Riverside County Regional Medical Center had a data breach in 2014, in California. Riverside Regional Medical Center notified patients of a databreach when one of their employee laptops used in their Opthamology and Dermatology clinics was stolen that contained patient information. The information on the laptop included names, phone numbers, addresses, dates of birth, Social Security Numbers, and clinical information such as medical record numbers, physicians, diagnosis, treatments received, medical departments and health insurance information.The facility has set up 12 months free of Experian's ProtectMyID Alert for those affected. [source] | |
Riverside County Regional Medical Center had a data breach in 2015, in California. The information was breached via Laptop . [source] | Riverside Medical Center had a data breach in 2018, in Illinois. The information was breached via Desktop Computer, Other. [source] | |
Riverside Medical Group had a data breach in 2014, in California. A business associate was not present. [source] | RMA Medical Centers of Florida had a data breach in 2016, in Florida. RMA Medical Centers of Florida, the covered entity (CE), discovered that on February 6, 2016, a password protected company laptop computer was stolen from an employee's hotel room. The laptop was not encrypted. It contained 3,906 individuals' protected health information (PHI) and included patients' names, dates of birth, health plan identification numbers, diagnoses, and primary care physicians' names. The CE provided breach notification to HHS, affected individuals, and the media and posted substitute notice on its website. It also offered complimentary one-year identity theft protection to affected individuals. Following the breach, the CE encrypted all laptops containing PHI and revised certain HIPAA policies to improve safeguards. The CE educated and retrained its employees on its policies. Finally, the CE sanctioned the employee responsible for the breach. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | |
Roark's Pharmacy had a data breach in 2016, in Tennessee. The covered entity (CE), Roark's Pharmacy, discovered on January 13, 2016, that its facility had been broken into and computer hard drives containing the protected health information (PHI) of 3,000 individuals were stolen. The types of PHI on the hard drives included patients' names, dates of birth, addresses, diagnoses, conditions, medications, health insurance information, and social security numbers (when used as ID numbers for certain insurance carriers). The CE provided breach notification to HHS and to affected individuals. OCR provided technical assistance to the CE regarding the Breach Notification Rule and impermissible disclosures. In addition, OCR provided resource materials regarding small businesses and the Privacy and Security Rules. In response to the breach, the CE increased its physical security by installing a metal gate over its front door, improving its security alarm system, and physically hiding and securing sensitive equipment. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | Robert B. Neves, M.D. had a data breach in 2014, in California. The information was breached via Laptop . [source] | |
Robert E Torti, MD, PA dba Retina Specialists had a data breach in 2017, in Texas. The information was breached via Paper/Films . [source] | Robert Smith DMD, PC had a data breach in 2018, in Tennessee. The information was breached via Network Server . [source] | |
ROBERT SOPER, M.D. had a data breach in 2015, in California. On June 27, 2015, the covered entity (CE), Robert Soper, M.D., discovered that electronic protected health information (ePHI) he was maintaining had been breached when a desktop computer was stolen from the trunk of his car. Approximately 2,000 individuals' ePHI was affected by the breach. The breach affected the following types of ePHI: patients' names, dates of birth, phone numbers, clinical notes, and e-mails. The CE provided breach notification to HHS, affected individuals, and the media. OCR provided the CE with guidance materials and other technical assistance regarding HIPAA Security Rule compliance. In response to OCR's technical assistance, the CE implemented a security awareness training program and encryption technology within its medical practice. Location of breached information: Desktop Computer Business associate present: No [source] | Rocky Mountain Health Care Services had a data breach in 2017, in Colorado. The information was breached via Laptop . [source] | |
Rocky Mountain Health Maintenance Organization, Inc. had a data breach in 2017, in Colorado. The information was breached via Paper/Films . [source] | Rocky Mountain Women's Health Center, Inc. had a data breach in 2018, in Utah. The information was breached via Paper/Films . [source] | |
Ronald D. Garrett-Roe, MD had a data breach in 2015, in Texas. Alleged hackers gained unauthorized access to one or two hard drives on the desktop computers of the covered entity (CE), Dr. Ronald D. Garrett-Roe, affecting approximately 1,600 patients' protected health information. The CE reported that the hard drive had been removed, all of the files copied, and the hard drive formatted, which caused all of the computer programs, the operating system, and many patient records to be erased. Dr. Garrett-Roe is no longer a covered entity. Location of breached information: Desktop Computer Business associate present: No [source] | Ron's Pharmacy Services had a data breach in 2018, in California. The information was breached via Email . [source] | |
Roper St. Francis Healthcare had a data breach in 2017, in South Carolina. The information was breached via Other Portable Electronic Device . [source] | Rotech Healthcare Inc. had a data breach in 2016, in Florida. Rotech Healthcare, Inc., the covered entity (“CE”), discovered that medical records from its electronic medical records system were printed, removed from the office, and recovered by the Secret Service. The breach affected 957 patients in 27 states. There were less than 500 individuals affected in any given state. The records involved in the breach contained patients' names, social security numbers, patients' numbers, dates of birth, dates of death, addresses, phone numbers, and the names of the Rotech subsidiary companies from which the individual received healthcare services. The CE sent timely breach notification to HHS and to affected individuals, and posted notification to its website. The CE also offered two years of free identity protection to affected individuals. In response to the breach, the CE revised its data monitoring policies and procedures, revised physical safeguards in office locations with the highest risk factors for a future breach, and sanctioned the employees alleged to have been involved in the breach. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | |
Rowan Companies, Inc. had a data breach in 2014, in Maryland. The information was breached via Desktop Computer . [source] | Rubin Lublin, LLC had a data breach in 2014, in Georgia. [source] | |
Rush University Medical Center had a data breach in 2015, in Illinois. On September 9, 2015, a business associate (BA), Standard Register, erroneously mailed announcements concerning a retirement for the covered entity (CE), Rush University Medical Center, which resulted in misdirected letters being sent to the wrong patients associated with the clinic. The breach affected 1,529 individuals and included patients' names. The CE provided breach notification to HHS, the media, and affected individuals, and provided substitute notice on its website. The CE also entered into a BA agreement with Standard Register and created policies and procedures to establish quality measures for mass mailings. OCR obtained documentation confirming that the CE implemented the corrective actions listed above. Location of breached information: Paper/Films Business associate present: No [source] | Sacred Heart Health System, Inc had a data breach in 2016, in Florida. On February 16, 2016, the American College of Cardiology Foundation, a business associate (BA), notified the covered entity (CE), Sacred Heart Health System, Inc., that some of its protected health information (PHI) had been inadvertently transferred to a testing environment made accessible to four vendors who were working with a software developer of the BA. The CE conducted an internal investigation and determined that the names, dates of birth, social security numbers, and internal patient identification numbers for 532 individuals had been exposed as a result of the incident. The CE immediately terminated access to the database containing the PHI, and obtained assurances from the vendors and software developer that the PHI had not been retained, or made accessible to any other unauthorized individuals. In response to the breach, the CE reviewed its policies and procedures, retrained its staff. The BA revised its policies and procedures for transferring data and added additional safeguard controls to ensure the security of PHI. Additionally, the CE provided breach notification to HHS, to the affected individuals, to the media, and posted a notice on its website. OCR obtained assurances that the CE and BA implemented the corrective actions listed above. [source] | |
SafetyFirst had a data breach in 2014, in Maryland. [source] | SAGE DENTAL MANAGEMENT, LLC had a data breach in 2017, in Florida. A business associate was present. [source] | |
Saint Agnes Health Care, Inc. had a data breach in 2015, in Maryland. The information was breached via Email . [source] | Saint Francis Hospital had a data breach in 2018, in Georgia. A business associate was not present. [source] | |
Saint Louis County Department of Health had a data breach in 2015, in Missouri. The information was breached via Paper/Films. [source] | Saint Thomas Rutherford Hospital had a data breach in 2017, in Tennessee. The information was breached via Paper/Films . [source] | |
Saints Mary and Elizabeth Hospital had a data breach in 2016, in Kentucky. The information was breached via Email. [source] | Saliba's Extended Care Pharmacy had a data breach in 2017, in Arizona. The information was breached via Email . [source] | |
Salina Health Education dba Salina Healthcare Center had a data breach in 2014, in Kansas. [source] | San Franciso General Hospital and Trauma Center had a data breach in 2015, in California. A business associate was not present. [source] | |
San Juan County New Mexico had a data breach in 2016, in New Mexico. The information was breached via Desktop Computer . [source] | San Juan Oncology Associates had a data breach in 2016, in New Mexico. The information was breached via Network Server . [source] | |
Sands Casino Resort Bethlehem had a data breach in 2014, in Maryland. Name, ssn, dln, passport number, email address, job titles were breached via Payment card system . [source] | Sands had a data breach in 2014, in Nevada. Name, emails address, ssn, job titles were breached via hackers . [source] | |
Santander Bank, N. A. had a data breach in 2014, in Massachusetts. An employee improperly accessed and retained info rmation. [source] | SCAN Health Plan had a data breach in 2016, in California. [source] | |
Scenic Bluffs Health Center Inc had a data breach in 2018, in Wisconsin. The information was breached via Email . [source] | Schaeffler Group USA had a data breach in 2015, in South Carolina. The information was breached via Network Server . [source] | |
Seguin Dermatology, Office of Robert J. Magnon, MD had a data breach in 2016, in Texas. The information was breached via Network Server . [source] | SEIM JOHNSON, LLP had a data breach in 2016, in Nebraska. A business associate (BA), Seim Johnson, LLP, reported on behalf of 10 health care provider clients that its health care auditor took his firm-issued laptop computer on a non-business weekend trip. When the employee arrived home from this trip, he discovered the backpack containing the laptop was missing. The laptop contained the protected health information (PHI) of 30,972 individuals and included demographic, clinical, and financial information. The BA provided breach notification to HHS, affected individuals, and the media. After investigating this incident, the BA determined that the laptop may not have been effectively encrypted. Following the breach, the BA sanctioned the involved employee and its security officer, retrained employees on security risks involving portable devices, and implemented new policies and procedures. OCR obtained assurances that the BA implemented the corrective actions listed above.[source] | |
Self Regional Healthcare had a data breach in 2014, in South Carolina. The information was breached via Laptop and Other Portable Electronic Device. [source] | Senior Health Partners, a Healthfirst company had a data breach in 2015, in New York. The information was breached via Laptop and Other Portable Electronic Device . [source] | |
Sentara Healthcare had a data breach in 2015, in Virginia. The information was breached via Other Portable Electronic Device . [source] | Sentara Healthcare had a data breach in 2014, in Virginia. The information was breached via Portable Electronic Device. [source] | |
Sentara Healthcare had a data breach in 2017, in Virginia. The information was breached via Network Server . [source] | Serene Sedation, LLC had a data breach in 2018, in Maryland. The information was breached via Network Server . [source] | |
Service Alternatives, Inc. had a data breach in 2014, in Maryland. The breach occurred due to unauthorized access to payroll systems. [source] | Seterus had a data breach in 2014, in Maryland. laon number, borrower name, property address, and loan details were breached. [source] | |
Seterus had a data breach in 2014, in Oregon. A foreclosure correspondence was sent to the incorrect address . [source] | Seton Family of Hospitals had a data breach in 2015, in Texas. The information was breached via Email . [source] | |
Seven Counties Services, Inc. had a data breach in 2014, in Kentucky. The information was breached via Paper/Films. [source] | Shaker Clinic had a data breach in 2014, in Ohio. The information was breached via Paper/Films . [source] | |
Sharon J. Jones M.D. had a data breach in 2015, in California. OCR opened an investigation of the covered entity (CE), Sharon J. Jones, after it reported a breach of 1,342 patients' protected health information (PHI) when its office was burglarized on January 8, 2015. The CE immediately reported the incident to local law enforcement. The compromised PHI included a combination of first and last names, dates of birth, addresses, telephone numbers, social security numbers, medical insurance information, medical records, and the last four digits of credit card numbers. The CE provided breach notification to HHS, affected individuals, and the media and provided affected individuals with complimentary identity theft protection for one year. Following the breach the CE improved safeguards for paper PHI, especially after having a second burglary on March 20, 2015, which resulted in another breach that OCR investigated separately. The CE secured a new office lease and moved its operations to a more secure building and location. It drafted a facility security plan and implemented physical security enhancements, such as utilizing interior locks, installing alarms and cameras, and shredding unnecessary paper documents. The CE also updated its policies and procedures and provided additional training to its workforce members. OCR obtained assurances that the CE implemented the corrective action listed above.[source] | Sharon J. Jones, M.D. had a data breach in 2015, in California. The information was breached via Laptop and Other Portable Electronic Device. [source] | |
Sharp Memorial Hospital had a data breach in 2017, in California. The information was breached via Laptop and Other Portable Electronic Device . [source] | Sheldon M. Golden O.D., Optometric Corporation had a data breach in 2017, in California. The information was breached via Network Server . [source] | |
Shiel Sexton had a data breach in 2017, in Indiana. A business associate was not present. [source] | Signal Outdoor Advertising, LLC had a data breach in 2014, in Maryland. Credit card payment info was breached via email . [source] | |
Silver Creek Fitness & Physical Therapy, Silver Creek Physical Therapy Gilroy, Silver Creek Physical Therapy Sunnyvale, Silver Creek Physical Therapy had a data breach in 2016, in California. [source] | Silverberg Surgical and Medical Group had a data breach in 2015, in California. The information was breached via Network Server . [source] | |
Simms Fishing Products had a data breach in 2014, in Maryland. Name, address, payment card info were breached via Payment card system . [source] | SimplyWell had a data breach in 2018, in Texas. A business associate was present. [source] | |
Sinai Health System had a data breach in 2017, in Illinois. The information was breached via Email . [source] | Singh and Arora Oncology Hematology, P.C. had a data breach in 2016, in Michigan. The information was breached via Network Server . [source] | |
Sioux Falls VA Health Care System had a data breach in 2015, in South Dakota. The information was breached via Paper/Films . [source] | Siouxland Anesthesiology, Ltd. had a data breach in 2015, in South Dakota. The information was breached via Network Server . [source] | |
Six Continents Hotels, Inc. had a data breach in 2014, in Maryland. Name, payment card info were breached via Desktop Computer . [source] | Six Red Marbles had a data breach in 2014, in Maryland. Name, dob, address, ssn were breached via Email . [source] | |
Skin and Cancer Center of Arizona had a data breach in 2015, in Arizona. The information was breached via Network Server. [source] | Skin Cancer Specialists, P.C. had a data breach in 2017, in Georgia. The information was breached via Network Server . [source] | |
Sloane Stecker Physical Therapy, PC had a data breach in 2014, in New York. A workforce member, a physical therapist, accessed the electronic health record system and obtained 2,000 patients' names, addresses and telephone numbers for the purpose of contacting or soliciting these patients to join a new physical therapy practice. The covered entity (CE), Sloane Stecker Physical Therapy, PC, provided breach notification to HHS, affected individuals, and the media and posted substitute notice on its website. The also CE provided free credit monitoring for the affected individuals. Following the breach, the CE retrieved the patient information and retrained staff. As a result of OCR's investigation and technical assistance, the CE is expected to perform an enterprise-wide risk analysis and establish a risk management plan. It is also expected to implement mechanisms to record and examine activity in information systems that contain or use electronic PHI. Additionally, the CE is expected to implement a security incident policy and procedure, implement procedures for identity verification for access to electronic PHI, and provide training to all staff on the newly implemented policies and procedures. [source] | Snelling Staffing, LLC had a data breach in 2014, in Maryland. The information was breached via Website. [source] | |
Society for Science & the Public had a data breach in 2014, in Maryland. The information was breached via Website . [source] | Sonoma County Indian Health Project, Inc had a data breach in 2018, in California. The information was breached via Desktop Computer, Email . [source] | |
Sony Pictures Entertainment had a data breach in 2014, in Maryland. Name, address, ssn, dln, credit card info, userName/pw, compensation were breached via Website . [source] | Sound Community Services, Inc. had a data breach in 2017, in Connecticut. The information was breached via Email . [source] | |
Sourcebooks, Inc. had a data breach in 2014, in Maryland. Name, address, and payment card information were breached. [source] | South Bend Orthopaedic Associates Inc had a data breach in 2017, in Indiana. The information was breached via Laptop . [source] | |
South Suburban HIV/AIDS Regional Clinics had a data breach in 2014, in Illinois. The information was breached via Email. [source] | South Sunflower County Hospital had a data breach in 2015, in Mississippi. A local merchant sent a package with shredded documents containing protected health information (PHI) from the covered entity (CE), South Sunflower County Hospital, used as packing material. The PHI included the dates of service, providers' names, diagnoses, patients' names, social security numbers, and dates of birth of 19,345 individuals. The CE retrieved the remaining shredded documents and stored them in a locked room with limited access. The CE provided breach notification to HHS, affected individuals, and the media. The CE investigated and modified its policies and procedures. It contracted with a document shredding company to destroy all hospital paper waste containing PHI and initiated a process to convert health records to an electronic format. As a result of the investigation, OCR reviewed the CE's HIPAA policies and procedures. Location of breached information: Paper/Films Business associate present: No [source] | |
South Texas Veterans Health Care System had a data breach in 2014, in Texas. The South Texas Veterans Health Care System informed 4,000 patients of a data breach to their personal information. "South Texas Veterans Health Care tried to send veterans notices on September 15 to explain a new federal rule of Hydrocodone combination they need to be aware of. But in the process of printing the letters, they mistakenly came out double-sided and had one unique veteran's information on one side and another veteran's on the other. [source] | Southcentral Foundation had a data breach in 2016, in Alaska. The information was breached via Email . [source] | |
Southeast Eye Institute, P.A. dba eye Associates of Pinellas had a data breach in 2016, in Florida. Southeast Eye Institute, P.A., the covered entity (CE), discovered that its business associate (BA), Bizmatics Inc., suffered a breach after a hacker accessed its servers. The breach affected 87,000 individuals and included patients' names, addresses, social security numbers, and health visit information. The CE timely sent breach notification to HHS, to affected individuals, to the media, and posted notification on the main page of its website. The CE did not have a BA agreement with Bizmatics at the time of the breach, but following the breach, the CE decided to terminate its relationship with the BA. After terminating its relationship with the BA, the CE received a certificate of records destruction from the, which confirmed that all of the CE's patient records stored by the BA were destroyed. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | Southwest Community Health Center had a data breach in 2017, in Connecticut. The information was breached via Desktop Computer, Laptop . [source] | |
Southwest General Health Center had a data breach in 2014, in Ohio. The covered entity (CE) misplaced a binder containing the protected health information (PHI) of approximately 953 individuals from its Maternity Unit. The PHI involved in the breach included names, dates of birth, medical record numbers and limited clinical information. The CE provided breach notification to affected individuals, HHS, and the media. To prevent a similar breach from occurring in the future, the covered entity strengthened its physical safeguards and retrained employees on safeguarding PHI. OCR obtained assurances that the corrective actions listed above were completed. Location of breached information: Other Business associate present: No [source] | Southwest Virginia Physicians for Women had a data breach in 2014, in Virginia. [source] | |
Special Agents Mutual Benefit Association had a data breach in 2015, in Maryland. OCR closed this investigation and consolidated this review into a compliance review that involves the same hacking incident involving CareFirst BlueCross BlueShield. Location of breached information: Network Server Business associate present: No [source] | Special Agents Mutual Benefit Association had a data breach in 2018, in Maryland. The information was breached via Paper/Films . [source] | |
Specialty Clinics Of Georgia - Orthopaedics had a data breach in 2014, in Georgia. The information was breached via Paper/Films . [source] | Spine Specialist had a data breach in 2014, in New Jersey. The information was breached via Laptop . [source] | |
Spokane VA Medical Center had a data breach in 2017, in Washington. The information was breached via Laptop . [source] | Sports Medicine & Rehabilitation Therapy, Inc. had a data breach in 2017, in Massachusetts. The information was breached via Desktop Computer . [source] | |
SSM Dean Medical Group had a data breach in 2017, in Wisconsin. The information was breached via Email . [source] | SSM DePaul Medical Group (Dr. Syed Khader) had a data breach in 2017, in Missouri. A business associate was not present. [source] | |
SSM Health Cancer Care had a data breach in 2015, in Missouri. [source] | SSM Health had a data breach in 2017, in Missouri. The information was breached via Electronic Medical Record . [source] | |
St Joseph Health System had a data breach in 2014, in Texas. A computer server containing the records of 405,124 patients of the covered entity (CE), St. Joseph Health System, was hacked during a power surge. The electronic protected health information (ePHI) on the server included names, dates of birth, social security numbers, medical information, bank account information, and addresses. The CE provided breach notification to HHS, affected individuals, and the media. The CE improved administrative and technical security and developed and revised policies and procedures addressing the breach. OCR obtained assurances that the CE implemented the corrective actions listed. Location of breached information: Network Server Business associate present: No [source] | St. Charles Health System had a data breach in 2017, in Oregon. The information was breached via Electronic Medical Record . [source] | |
St. Elizabeth's Medical Center had a data breach in 2014, in Massachusetts. The information was breached via Laptop and Other Portable Electronic Device . [source] | St. Francis College had a data breach in 2014, in Maryland. Name, address, phone number, email address, ssn were breached via Portable device . [source] | |
St. Louis Children's Hospital had a data breach in 2017, in Missouri. The information was breached via Email . [source] | St. Luke's Cornwall Hospital had a data breach in 2015, in New York. The information was breached via Other Portable Electronic Device . [source] | |
St. Luke's Hospital had a data breach in 2017, in North Dakota. The information was breached via Network Server . [source] | St. Martin Parish School Based Health Centers had a data breach in 2015, in Louisiana. The information was breached via Network Server. [source] | |
St. Mary Mercy Hospital had a data breach in 2014, in Michigan. The information was breached via Email. [source] | St. Mary's Health had a data breach in 2015, in Indiana. The information was breached via Email . [source] | |
St. Peter's Health Partners had a data breach in 2015, in New York. The information was breached via Other Portable Electronic Device . [source] | St. Vincent Hospital and Health Care Center, Inc. had a data breach in 2014, in Indiana. The information was breached via Paper/Films . [source] | |
St. Vincent Hospital and Healthcare Inc had a data breach in 2014, in Indiana. The information was breached via Laptop . [source] | St.Vincent Hospital and Health Care Center, Inc. had a data breach in 2015, in Indiana. The information was breached via Paper/Films . [source] | |
St.Vincent Medical Group, Inc. had a data breach in 2015, in Indiana. The information was breached via Email . [source] | Stamford Podiatry Group .P.C had a data breach in 2016, in Connecticut. The information was breached via Network Server . [source] | |
Stanislaus Surgical Hospital had a data breach in 2015, in California. Stanislaus Surgical Hospital notified individuals of a data security breach that occurred on April 5, 2015. They do not state exactly how the breach occurred in their notification letter. The information compromised included names, addresses, account numbers, Social Security numbers and other personally identifiable information. The hospital is providing one year free of Experian's ProtectMyID Elite to those affected. [source] | Staples, Inc. had a data breach in 2014, in Maryland. Name, payment card info were breached via Website . [source] | |
StarCare Speciality Health System had a data breach in 2016, in Texas. The information was breached via Laptop and Paper/Films . [source] | StayWell Health Management, LLC had a data breach in 2014, in Minnesota. StayWell Health Management, a business associate (BA) for multiple covered entities (CE), reported that, from March 29, 2012, until January 21, 2014, spreadsheets containing the protected health information (PHI) of 19,474 individuals who participated in wellness programs were unintentionally available online when an internal administrative tool generated reports and placed those reports in a public facing folder. The types of PHI on the spreadsheets included the participants' names, email addresses, unique BA identification numbers, and information about participation in the program. The BA provided breach notification to HHS, affected individuals, and the media on behalf of the CEs affected by the breach: Regents of the University of Minnesota, Missouri Consolidated health Care Plan, Clorox Company Group Insurance Plan, Nissan North America, Inc., and QBE Holdings, Inc. Upon discovery of the breach, the BA upgraded its platform and revised and implemented its policies and procedures. OCR obtained assurances that the BA implemented the corrective actions listed above. Steps were also taken to restrict access to and to remove the data entirely from Google, Bing, Yahoo, and other search engines. Separate breach cases have been opened for each of the affected CEs. [source] | |
StayWell Health Management, LLC had a data breach in 2014, in Minnesota. The information was breached via Desktop Computer. [source] | StayWell Health Management, LLC had a data breach in 2014, in Minnesota. The information was breached via Network Server . [source] | |
Stephen J. Helvie, M.D. had a data breach in 2016, in California. The information was breached via Paper/Films . [source] | Stephenville Medical & Surgical Clinic had a data breach in 2017, in Texas. The information was breached via Desktop Computer . [source] | |
Sterne Agee had a data breach in 2014, in Alabama. [source] | Steven A. Goldman, MD Inc. had a data breach in 2014, in Ohio. The information was breached via Network Server . [source] | |
Steven Yang, D.D.S., INC. had a data breach in 2018, in California. The information was breached via Laptop . [source] | Stoetzel's Planet Chiropractic had a data breach in 2014, in Illinois. An unauthorized individual broke into the covered entity's (CE) facility and stole a laptop computer containing the electronic protected health information (ePHI) of approximately 1,000 individuals, including names, credit card numbers, bank account numbers, treatment information, and x-ray images. The CE provided breach notification to HHS, affected individuals, and prominent media outlets in Illinois. Following the breach, the CE reported the theft to the local police department, relocated to a new facility, and implemented facility security measures, including a security alarm system. It also enhanced its policies and procedures implementing the Privacy and Security Rules. OCR obtained assurances that the CE implemented the corrective actions listed. Location of breached information: Laptop, Other Portable Electronic Device Business associate present: No [source] | |
Stony Brook Internists, University Faculty Practice Corporation (UFPC) had a data breach in 2016, in New York. On May 19, 2016 the business associate (BA), Ambucor Health Solutions, notified the covered entity (CE), Stony Brook Internists, University Faculty Practice Corporation (a member of the Stony Brook Organized Health Care Arrangement), of an investigation into possible breach activities by a former employee affecting the protected health information (PHI) of 55 of the CE's patients, including demographic and clinical information. On November 18, 2016 the BA notified the CE that an additional 1,823 patients were affected by the breach. The CE and BA both provided breach notification to HHS. The investigation of this breach has been consolidated into an existing review of the BA. As of this submission, the BA has not reported misuse of the breached PHI. OCR obtained and reviewed a copy of the BA agreement between this CE and BA. Location of breached information: Email, Other Portable Electronic Device Business associate present: No [source] | Suburban Lung Associates had a data breach in 2015, in Illinois. The information was breached via Paper/Films . [source] | |
Success 4 Kids & Families, Inc. had a data breach in 2015, in Florida. On April 5, 2015, a Success 4 Kids & Family employee's laptop computer was stolen out of his vehicle while parked during non-work hours. The laptop contained the protected health information (PHI) of 506 individuals, and included clients' names, addresses, dates of birth, social security numbers, and limited treatment-related information. The laptop was password protected, but was not encrypted. The covered entity (CE) provided breach notification to HHS, affected individuals, and the media, and posted substitute notice on its website. In response to this incident, the CE contracted with an IT vendor to upgrade servers and provide cloud backup service, encrypted all computers, reviewed its policies and procedures, implemented an encryption policy, and trained staff. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Laptop Business associate present: No [source] | Summit Medical Group, Inc. dba St. Elizabeth Physicians had a data breach in 2016, in Kentucky. The covered entity (CE), Summit Medical Group, Inc. dba St. Elizabeth Physicians, discovered that an employee at its Weight Management Center (WMC) sent an email on July 12, 2016, notifying recipients of an upcoming vitamin presentation, but inadvertently failed to blind copy the recipients. Recipients were able to see all other recipients' email addresses. The email was sent to 811 addresses, but because some were undeliverable and some belonged to the CE's employees, the CE calculated the number of individuals affected as 674. On August 23, 2016, the CE provided breach notification to HHS, affected individuals, and the media. In response to the breach and as a result of OCR's investigation, the CE reviewed and adjusted its emailing procedures, sanctioned the WMC employee, and provided training to its leadership and the WMC workforce. Additionally, the employee who sent the email started a multi-session individual training program. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | |
Sunbury Plaza Dental had a data breach in 2016, in Ohio. OCR opened an investigation of the covered entity (CE), Sunbury Plaza Dental, after it reported that a secured storage unit containing paper protected health information (PHI) was burglarized. The storage unit contained PHI for 7,981 individuals. The medical records contained at this location included names, addresses, dates of birth, social security numbers, and treatment information. The CE provided breach notification to HHS, affected individuals, and the media, and also posted substitute notice on its website. The CE offered one year of identity monitoring to all affected individuals. Following the breach, the CE revised its records retention policies to minimize the number of paper records in storage. OCR obtained assurances that the CE implemented the corrective actions noted above. Location of breached information: Paper/Films Business associate present: Yes [source] | Sunquest Information Systems had a data breach in 2015, in Arizona. The information was breached via Laptop . [source] | |
SUNSHINE STATE HEALTH PLAN, INC. had a data breach in 2016, in Florida. [source] | SUPERVALU Group Health Plan had a data breach in 2015, in Minnesota. The information was breached via Network Server . [source] | |
SUPERVALU Inc. had a data breach in 2014, in Minnesota. Account numbers, and in some cases also the expiration date, other numerical information and/or the cardholder's name, from payment cards were breached. [source] | Supportive Concepts for Families, Inc. had a data breach in 2014, in Pennsylvania. The CE inadvertently made an internal database containing the electronic protected health information (ePHI) of 593 individuals accessible on the Internet. The ePHI involved in the breach included names, dates of birth, social security numbers, addresses, dates of services, and customer service notes. The CE immediately removed the database from the Internet and secured it against further unauthorized disclosures. The CE provided breach notification to affected individuals, HHS, and the media, and posted substitute notice online. Following the breach, the CE provided further HIPAA training to its staff and sanctioned the responsible employees. The CE also took measures to reduce the vulnerabilities identified its most recent risk analysis. [source] | |
Surgical Dermatology Group had a data breach in 2017, in Alabama. The information was breached via Network Server . [source] | Susan M Hughes Center had a data breach in 2016, in New Jersey. The information was breached via Network Server . [source] | |
Susquehanna Health had a data breach in 2014, in Pennsylvania. Information was included on an unencrypted email. [source] | Susquehanna Health had a data breach in 2014, in Pennsylvania. Information was included on unencrypted email . [source] | |
Sutherland Healthcare Solutions, Inc. had a data breach in 2014, in New Jersey. The information was breached via Email. [source] | Sutherland Healthcare Solutions had a data breach in 2014, in California. [source] | |
Sutter Medical Foundation had a data breach in 2015, in California. The information was breached via Email . [source] | Syed Ahmed, MD PA had a data breach in 2017, in Texas. The information was breached via Paper/Films . [source] | |
Synergy Specialists Medical Group, Inc / Jay S. Berenter, DPM had a data breach in 2017, in California. The information was breached via Email . [source] | T.J. Samson Community Hospital had a data breach in 2015, in Kentucky. The covered entity (CE), TJ Samson Community Hospital, discovered that on June 8, 2015, it had sent an advertisement email to 2,060 patients that inadvertently exposed the names and email addresses of the recipients. The CE provided breach notification to HHS, affected individuals, and the media. In response to the breach, the CE drafted a new policy which details the internal use of its patient portal to communicate with patients. It also counseled its marketing staff on disseminating information. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | |
Taconic Biosciences, Inc. had a data breach in 2017, in New York. Name, address, ssn, w2 tax info were breached via Email . [source] | Tallahassee Memorial HealthCare, Inc. had a data breach in 2016, in Florida. Tallahassee Memorial HealthCare, Inc., the covered entity (CE), discovered that an employee attempted to upload protected health information (PHI) containing patients' names, insurance numbers, payor financial information numbers, and account numbers to an unauthorized website. The breach affected 505 individuals. The CE sent timely breach notification to HHS and to affected individuals and provided free credit monitoring to affected individuals. In response to the breach, the CE sanctioned the responsible employee, flagged patient accounts in its internal billing system, revised its website filter to block additional web sites, and updated its employee training. OCR obtained assurances from the CE that it implemented the corrective actions listed above. Location of breached information: Other Business associate present: No [source] | |
Talyst had a data breach in 2014, in Washington. The information was breached via Laptop . [source] | Tampa Bay Surgery Center had a data breach in 2017, in Florida. A business associate was not present. [source] | |
TD Bank had a data breach in 2014, in South Carolina. Names and bank accounts were breached via email . [source] | Temple Physicians Inc. had a data breach in 2014, in Pennsylvania. A business associate was not present. [source] | |
Tennessee Rural Health Improvement Association had a data breach in 2015, in Tennessee. A business associate (BA), BlueCross BlueShield, created a mailing list of its members for the purpose of selling Medicare Advantage marketing products, an activity that was outside of that permitted by the BA agreement. This breached affected 79,000 individuals and included their demographic information. The covered entity (CE), Tennessee Rural Health Improvement Association, provided breach notification to its members that were enrolled in the Medicare supplement insurance plans and non-Medicare insurance plans, as well as to HHS and the media. Following the breach, the CE revised its policies, implemented new technical safeguards, and improved physical security. In addition, it retrained its workforce on the appropriate usage of protected health information (PHI), and minimum necessary determinations for the use and disclosure of PHI. OCR reviewed the BA agreement in place between the CE and BA and determined that it met the requirements of the HIPAA Breach Notification Rule. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | Tennessee Rural Health Improvement Association had a data breach in 2017, in Tennessee. The information was breached via Paper/Films . [source] | |
Test Effects, LLC (Wireless Emporium) had a data breach in 2014, in New Hampshire. The information was breached via Website . [source] | The Affiliated Sante Group had a data breach in 2017, in Maryland. The information was breached via Electronic Medical Record . [source] | |
The Ambulatory Surgery Center at St. Mary had a data breach in 2016, in Pennsylvania. The information was breached via Network Server . [source] | The Arc of Erie County had a data breach in 2018, in New York. A business associate was not present. [source] | |
The Biomechanics LLC had a data breach in 2016, in Arizona. A security researcher accessed the covered entity's electronic protected health information (ePHI) due to a vulnerability in a business associate's (BA) data storage system. The researcher reportedly did not intend to use or disclose the information. The breach affected 1,049 individuals and involved in the breach included names, addresses, birthdates, driver's license numbers, social security numbers, and clinical information such as diagnoses, lab results, and medications. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the BA returned the ePHI to the covered entity. The BA was closing its business at the time of the breach and is now out of business. OCR obtained a copy of the CE's BA agreement with this BA. As a result of OCR's investigation the CE increased its awareness of its responsibilities with respect to its BAs. Location of breached information: Other Business associate present: No [source] | The Brooklyn Hospital Center had a data breach in 2014, in New York. The information was breached via Other Portable Electronic Device . [source] | |
The Carle Foundation had a data breach in 2016, in Illinois. The information was breached via Network Server . [source] | The Coca Cola Company had a data breach in 2014, in Maryland. Name, ssn, dln, government identification numbers were breached via Laptop . [source] | |
The Corvallis Clinic, P.C. had a data breach in 2014, in Oregon. The Eye Institute of Corpus Christi, a full service eye care, diagnosis, and treatment clinic in Texas, has discovered that individuals gained access to the records of all of its patients, downloaded their protected health information from the EHR, copied those data, and provided them to two physicians formerly employed by the eye clinic.The disclosed data include the names of patients, their addresses, contact telephone numbers, Social Security numbers, dates of birth, medical diagnoses, details of treatment, and health insurance details. [source] | The Dermatology Center of Raleigh PA had a data breach in 2017, in North Carolina. The information was breached via Email . [source] | |
The Finley Center had a data breach in 2016, in Nevada. On February 22, 2013, the Guidance Center of Westchester discovered that a central processing unit (CPU) had been removed form a staff members office. The CPU was removed on February 21 and contained, names, Social Security numbers, dates of birth, dates of admittance to the Center, names of insurance carriers, home addresses, diagnoses, outpatient treatment authorization request, doctors names, case numbers, and whether or not a patient was prescribed medication. [source] | The Hearing Zone had a data breach in 2014, in Utah. The information was breached via Laptop . [source] | |
The Home Depot, Inc. had a data breach in 2014, in Maryland. [source] | The Johns Hopkins Hospital had a data breach in 2015, in Maryland. The information was breached via Electronic Medical Record. [source] | |
The Kroger Co., for itself and its affiliates and subsidiaries had a data breach in 2014, in Ohio. The information was breached via Electronic Medical Record. [source] | The Longstreet Clinic, P. C. had a data breach in 2014, in Georgia. A business associate was not present. [source] | |
The McLean Hospital Corporation had a data breach in 2015, in Massachusetts. The information was breached via Other Portable Electronic Device . [source] | The MetroHealth System had a data breach in 2015, in Ohio. The information was breached via Desktop Computer . [source] | |
The Neurology Foundation, Inc. had a data breach in 2017, in Rhode Island. The information was breached via Desktop Computer, Electronic Medical Record, Network Server, Other Portable Electronic Device, Paper/Films. [source] | The Northern Trust Company had a data breach in 2014, in Maryland. Name, address, ssn, benefits plan, payment information, banking info were breached via Website . [source] | |
The Oregon Clinic, P.C. (Š—_'Ü'_The Oregon ClinicŠ—_'Ü'_) had a data breach in 2018, in Oregon. The information was breached via Email . [source] | The Outer Banks Hospital had a data breach in 2016, in North Carolina. The covered entity (CE), Outer Banks Hospital, lost two unencrypted portable computer drives ("flash" drives) containing the protected health information (PHI) of approximately 1,000 individuals during a move. The types of PHI on the lost flash drives included names, addresses, birthdates, social security numbers, diagnoses/conditions, and other treatment information. The CE provided breach notification to HHS, affected individuals, and the media. In response to the breach, the CE retrained its workforce with respect to appropriate portable devices and media storage. Additionally, the CE initiated the deployment of new technology on all computer workstations to detect and prevent PHI from being downloaded to portable storage media devices. The CE also began using auto-encryption technology rather than relying on user actions to encrypt data and implemented related procedures. Further, the CE drafted a new procedure for physical practice acquisitions which includes a more thorough risk assessment of privacy and security components. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | |
The Pediatric Endocrinology and Diabetes Specialists had a data breach in 2018, in Nevada. The information was breached via Desktop Computer, Electronic Medical Record, Laptop . [source] | THE R.O.A.D.S. Foundation Inc. DBA R.O.A.D.S. Community Care Clinic had a data breach in 2017, in California. The information was breached via Paper/Films . [source] | |
The Seattle Indian Health Board had a data breach in 2016, in Washington. The information was breached via Email . [source] | The University of New Mexico had a data breach in 2016, in New Mexico. The information was breached via Portable Electronic Device. [source] | |
The University of Texas System Administration had a data breach in 2016, in Texas. The information was breached via Email. [source] | The Vein Doctor had a data breach in 2016, in Missouri. The information was breached via Electronic Medical Record, Network Server. [source] | |
The WellPoint Affiliated Covered Entities had a data breach in 2014, in Indiana. The information was breached via Paper/Films . [source] | Thomas Cristello, Chiropractor PC had a data breach in 2014, in New York. The information was breached via Other Portable Electronic Device . [source] | |
Thomas H. Boyd Memorial Hospital had a data breach in 2015, in Illinois. A facility where the covered entity (CE) had stored its medical records since 1994 was sold to a third party and possession of this property was given to the new owner for five days, unbeknownst to the CE. The protected health information (PHI) involved in the breach included the clinical, demographic and financial information of 8,300 individuals. Upon discovery of the breach, the CE immediately retrieved all records at the facility. There was no evidence that the records were otherwise compromised. The CE provided breach notification to HHS, affected individuals, and the media. The CE retrained employees on its revised policies and procedures, including the proper storage of PHI and distribution of its revised policies and procedures. OCR obtained assurances that the CE implemented the corrective actions listed. [source] | Thomasville Eye Center had a data breach in 2016, in Georgia. Name, address, ssn, and w2 tax info were breached. [source] | |
TIC Gums, Inc had a data breach in 2017, in Maryland. Name, address, ssn, w2 tax info were breached via Email . [source] | Tiger Vision, LLC had a data breach in 2018, in Louisiana. The information was breached via Laptop . [source] | |
Tim McCoy & Associates DBA NEAT Management Group had a data breach in 2014, in Texas. Name, ssn, dob, phone number, address, EIN, and email address were breached via Laptop . [source] | TJ Samson Community Hospital had a data breach in 2017, in Kentucky. The information was breached via Electronic Medical Record . [source] | |
TMA Practice Management Group had a data breach in 2014, in Texas. The covered entity (CE), McBroom Clinic, PA, signed a business associate (BA) agreement with TMA Practice Management Group to provide an operational assessment/audit. As part of the assessment the BA requested, and the CE provided, certain health information about patients. The protected health information (PHI) included clinical and insurance/payment information about patients. The CE copied some of the PHI to an unencrypted portable USB flash drive and sent it to the BA with other information in a package on January 7, 2014. Upon receipt of the empty package, the BA subsequently discarded it in the recycling receptacle. On or around February 21, 2014, the Clinic contracted with AllClear ID to assist with the patient notification and mitigation efforts. As a result of the breach, the CE instituted new procedures for extracting and sending PHI via portable media, including encryption. Due to OCR's investigation, the CE was made aware of the following areas of improvement: risk analysis and staff training on policies and procedures. [source] | Todd M. Burton, M.D. had a data breach in 2014, in Texas. A business associate was present. [source] | |
Tokyo Electric Power Company, Inc. had a data breach in 2014, in Maryland. Name and ssn were breached via email . [source] | Tomas, Arturo had a data breach in 2015, in Illinois. Name, address, ssn, and w2 tax info were breached. [source] | |
Toscano Clements Taylor had a data breach in 2017, in New York. Name, address, ssn, w2 tax info were breached via Email . [source] | Toth Enterprises II d/b/a Victory Medical had a data breach in 2017, in Texas. The information was breached via Email and Paper/Films . [source] | |
Touchstone Medical Imaging, LLC had a data breach in 2014, in Tennessee. The information was breached via Network Server . [source] | TREMEC had a data breach in 2014, in Maryland. The information was breached via Network Server. [source] | |
Tri Lakes Medical Center had a data breach in 2014, in Mississippi. The information was breached via Network Server . [source] | TriHealth, Inc. had a data breach in 2017, in Ohio. [source] | |
Triple-C, Inc. had a data breach in 2014, in Puerto Rico. The information was breached via Network Server . [source] | Triple-S Advantage, Inc. had a data breach in 2018. [source] | |
True Vision Eyecare had a data breach in 2014, in Ohio. A burglar stole two laptop computers from the covered entity's (CE) office. One of the stolen laptops contained the protected health information (PHI) of 542 individuals that included first and last names and eyeglass prescriptions. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE purchased new laptops that are password protected with automatic shut-off features, and also retrained staff on security. OCR obtained documentation that the CE implemented the corrective actions it took in this matter. Location of breached information: Laptop Business associate present: No [source] | Truman Medical Center, Incorporated had a data breach in 2015, in Missouri. An employee of the covered entity (CE), Truman Medical Center, found a list of patients on the internet. The list contained names, addresses, and internal identification numbers for 503 of the CE's patients. The CE determined that the list was posted to a file transfer protocol (FTP) site by the public relations department and was a mailing list used to notify patients that a clinic was moving to a new location. The list was available on the internet from September 2012 until March 2015. The CE provided breach notification to HHS, affected individuals and the media, and provided substitute notice on its website. Following the breach, the CE immediately removed and deleted the patient list from FTP site and reviewed the other information posted on the site. The CE improved safeguards by enabling the public relations employees to send encrypted emails and providing instructions on how to use secure email. The CE also required additional training for workforce members in the public relations department. OCR obtained written assurances that the CE implemented the corrective actions listed above.[source] | |
Tufts Associated Health Maintenance Organization, Inc. and Tufts Insurance Company had a data breach in 2014, in Massachusetts. A business associate was not present. [source] | Tufts Associated Health Maintenance Organization, Inc. had a data breach in 2018, in Massachusetts. The information was breached via Paper/Films . [source] | |
Tulare County Health & Human Services Agency had a data breach in 2015, in California. The covered entity (CE) reported a breach of 845 individuals' electronic protected health information (e-PHI), as a result of a workforce member e-mailing information regarding logging into CE's health care portal, without blind copying the patients, and encrypting the e-mails. This action, or lack thereof, left every patient's e-mail address exposed. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE improved safeguards by changing and strengthening password requirements, disabling all patients' health portal accounts, and implementing new technical safeguards. In addition, the CE required all affected patients to re-register with its online portal, and revised and implemented new policies and procedures. The CE sanctioned the workforce members involved and re-trained the entire workforce. OCR provided technical assistance regarding the HIPAA Security Rule and obtained documented assurances that the CE implemented the corrective actions listed above. [source] | U.S. Health Holdings, Ltd. o/b/o Macomb County, Michigan had a data breach in 2014, in Michigan. A business associate was not present. [source] | |
U.S. HealthWorks had a data breach in 2016, in California. The information was breached via Laptop . [source] | UC Davis Medical Center, Privacy Manager Breach had a data breach in 2014, in California. The information was breached via Email. [source] | |
UC Health, LLC had a data breach in 2015, in Ohio. The information was breached via Email . [source] | Ullico Inc. had a data breach in 2014, in Maryland. Name, ssn, dob, address were breached via Laptop . [source] | |
UMass Memorial Medical Group, Inc. had a data breach in 2015, in Massachusetts. A business associate was not present. [source] | UNC Health Care System had a data breach in 2017, in North Carolina. The information was breached via Desktop Computer . [source] | |
UNC Health Care had a data breach in 2017, in North Carolina. The information was breached via Paper/Films . [source] | Uncommon Care, P.A. had a data breach in 2016, in North Carolina. The information was breached via Paper/Films. [source] | |
Unconditional Love, Incorporated had a data breach in 2017, in Florida. The information was breached via Paper/Films . [source] | Union Lake Supermarket, LLC had a data breach in 2018, in New Jersey. The information was breached via Other Portable Electronic Device . [source] | |
United Air Temp Conditioning & Heating, Inc. had a data breach in 2014, in Maryland. Name, payment card info were breached via Credit Card . [source] | United Community & Family Services had a data breach in 2016, in Connecticut. United Community Family Services, the covered entity (CE), mistakenly sent an email blast that advertised dental services, to current and former patients, with email addresses visible to all of the other recipients of the email. The emails were encrypted so that that only the recipients could have accessed them. Approximately 1,095 individuals were affected by this breach. The types of protected health information (PHI) involved in the breach included some names as part of the email addresses and the implied suggestion that these individuals had received dental services from this CE. The CE provided breach notification to HHS, affected individuals, and the media. As a result of OCR's investigation, the CE implemented plans to review and revise its policies to ensure adequate safeguards of electronic PHI. Additionally, the covered entity re-trained staff on its HIPAA policies and issued periodic HIPAA reminders to staff. [source] | |
United Seating and Mobility, LLC d/b/a Numotion had a data breach in 2015, in Connecticut. On March 26, 2015, a break-in occurred at the Tacoma, Washington branch office of Numotion, the covered entity (CE). The items stolen included five laptop computers that accessed service work orders, quotes, labor guides and delivery checklists. The breach affected 2,722 individuals' protected health information (PHI) and included names, addresses, phone numbers, and the serial numbers of customer equipment. Some documents may have also contained dates of birth, insurance policy numbers, or diagnosis codes. The stolen laptops required a password to obtain access to information. The CE provided breach notification to HHS, affected individuals, and the media. It also offered affected customers one year of free credit monitoring. The CE was able to successfully wipe the data from two of the computers via remote access. As a result of this investigation, the CE updated its password policy and completed full disk encryption of computer hard drives in all its locations. OCR provided technical assistance to the CE on conducting a compliant Security Rule risk analysis.[source] | UnitedHealth Group Single Affiliated Covered Entity (SACE) had a data breach in 2016, in Minnesota. The information was breached via Paper/Films . [source] | |
UnitedHealth Group Single Affiliated Covered Entity had a data breach in 2018, in Minnesota. The information was breached via Paper/Films . [source] | UnitedHealth Group Single Affiliated Covered Entity had a data breach in 2016, in Minnesota. A business associate was not present. [source] | |
UnityPoint Health Affiliated Covered Entity had a data breach in 2016, in Iowa. The information was breached via Electronic Medical Record . [source] | University Health had a data breach in 2014, in Louisiana. On August 15, 2014, the covered entity (CE), University Health, reported a breach when a professor from City College of San Francisco notified them by email of security issues. Protected health information (PHI) from the E.A. Conway Medical Center was contained on an unsecured server that was accessible online. The types of PHI involved in the breach included financial and medical information and affected 6,075 individuals. The CE immediately took the server off-line, which discontinued any unauthorized access. The CE provided breach notification to HHS, affected individuals, and the media. Following the incident, the CE hired a third-party company to conduct and assess a thorough external penetration test. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Network Server Business associate present: No [source] | |
University of California San Francisco , Privacy Manager Breach had a data breach in 2014, in California. The information was breached via Laptop. [source] | University of Colorado Health had a data breach in 2015, in Colorado. On October 9, 2015, University of Colorado Health, the covered entity (CE) discovered that a nurse working in one of the CE's network hospitals impermissibly accessed 827 individuals' medical records between October 2014 and September 2015. The CE discovered the nurse's impermissible accesses after an anonymous individual telephoned the CE's privacy hotline regarding the nurse's suspected conduct. To carry out these impermissible accesses, the nurse utilized the CE's electronic health record (EHR) application. The CE provided breach notification to HHS, the media, and affected individuals. Based on the breach and OCR's investigation, the CE sanctioned the nurse and terminated her access to the EHR. The CE also retrained nursing staff regarding use of the EHR in accordance with HIPAA. The CE has reported similar breaches to OCR, and OCR has consolidated the unresolved issues from this breach into a review along with related compliance concerns arising from the CE's other breaches.[source] | |
University of Illinois at Chicago had a data breach in 2015, in Illinois. A physician's assigned laptop computer containing the electronic protected health information (ePHI) of approximately 3,000 individuals was stolen. The type of ePHI involved in the breach included diagnoses and conditions of the individuals. The covered entity (CE) provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE updated relevant HIPAA policies, including encryption, to ensure the safeguarding of ePHI and sanctioned the physician involved. OCR obtained assurances that the CE implemented the corrective actions listed above. The CE also notified the deans and directors of all the CE's healthcare components of the corrective actions taken in response to this incident. Location of breached information: Laptop Business associate present: No [source] | University of Oklahoma Department of Urology had a data breach in 2015, in Oklahoma. On October 10, 2015, the covered entity (CE), University of Oklahoma Health Sciences Center, reported a breach affecting approximately 9,300 individuals. An unencrypted laptop computer used by a former physician in the Pediatric Urology program was stolen from his vehicle. The laptop contained protected health information (PHI) including patients' first and last names, medical record numbers, and dates of birth, and in some cases, patients' age, physicians' names, and diagnosis, treatment, and/or billing codes. The CE provided the required breach notifications to HHS, affected individuals, and the media. Following discovery of the incident, the CE implemented additional technical safeguards for devices containing electronic PHI and retrained workforce members regarding safeguarding PHI. The CE also revised its physician exit interview to require physicians to attest that all PHI had been removed from personally owned devices at the time of departure. OCR obtained assurances the CE implemented the corrective actions listed above.[source] | |
University of Oklahoma, Department of Obstetrics and Gynecology had a data breach in 2015, in Oklahoma. The information was breached via Email. [source] | University of Pennsylvania Health System had a data breach in 2014, in Pennsylvania. A bag containing a compact disk - read only memory (CD-ROM) was stolen from the vehicle of a physician associated with the covered entity (CE). The CD-ROM involved in the breach contained names, dates of birth, social security numbers, medical histories, and the treatment information of approximately 2,046 individuals. Following the breach, the CE filed a police report and provided breach notification to affected individuals, HHS, and the media. The CE sanctioned and retrained the physician whose bag was stolen and implemented organization wide improvements to its compliance with the Privacy and Security Rules. As a result of OCR's investigation the covered entity posted substitute notification of the breach in the local paper and confirmed that corrective actions steps were taken. [source] | |
UPMC Health Plan had a data breach in 2015, in Pennsylvania. An employee of the covered entity (CE), UPMC Health Plan, inadvertently sent an unsecure email with protected health information (PHI) to an incorrect, third-party email address. The breach included the electronic PHI of 722 individuals and included names, dates of birth, member identification numbers, phone numbers, types of insurance, and members' primary care providers. The CE provided breach notification to HHS, affected individuals, and the media. Following the breach, the CE retrained staff members. OCR reviewed UPMC Health Plan's risk analysis to ensure compliance with the Security Rule and obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Email Business associate present: No [source] | UPMC Susquehanna had a data breach in 2017, in Pennsylvania. The information was breached via Email . [source] | |
Urgent Care Clinic of Oxford had a data breach in 2016, in Mississippi. The information was breached via Network Server . [source] | Urological Associates of Central Jersey P.A. had a data breach in 2017, in New Jersey. The information was breached via Desktop Computer, Network Server . [source] | |
Urological Associates of Southern Arizona, P.C. had a data breach in 2014, in Arizona. A business associate was not present. [source] | Urology Associates, Professional Corporation had a data breach in 2015, in Montana. The information was breached via Network Server. [source] | |
Urology Austin, PLLC had a data breach in 2017, in Texas. The information was breached via Network Server . [source] | US Investigations Services, LLC (USIS) had a data breach in 2014, in District Of Columbia. Name, dob, ssn, userName/passwords were breached via Website . [source] | |
USAA Federal Savings Bank had a data breach in 2014, in Texas. The information was breached via Network Server. [source] | USAA had a data breach in 2014, in Maryland. Name, address, ssn, member account number, and financial info were breached via paper . [source] | |
USACS Management Group, Ltd. had a data breach in 2018, in Ohio. The information was breached via Email . [source] | USC Keck and Norris Hospitals had a data breach in 2016, in California. The information was breached via Network Server . [source] | |
UW Health had a data breach in 2017, in Wisconsin. The information was breached via Email . [source] | VA Black Hills Health Care System had a data breach in 2015, in South Dakota. [source] | |
VA Corporate Data Center Operations/Austin Information Technology Center had a data breach in 2015, in Texas. The information was breached via Paper/Films. [source] | VA Eastern Colorado Health Care System(ECHCS) had a data breach in 2015, in Colorado. The information was breached via Paper/Films . [source] | |
VA Eastern Colorado Health Care System had a data breach in 2016, in Colorado. The information was breached via Email . [source] | VA Long Beach Healthcare System had a data breach in 2014, in California. The information was breached via Paper/Films . [source] | |
VA Palo Alto Health Care System had a data breach in 2018, in California. The information was breached via Paper/Films . [source] | VA St. Louis Health Care System had a data breach in 2017, in Missouri. The information was breached via Paper/Films . [source] | |
Val Verde Regional Medical Center had a data breach in 2016, in Texas. The information was breached via Electronic Medical Record. [source] | Valeritas had a data breach in 2014, in Maryland. Names, address, dob, ssn were breached via Network Server . [source] | |
Valesco Ventures had a data breach in 2014, in Florida. The information was breached via Electronic Medical Record. [source] | Valley Anesthesiology Consultants, Inc. d/b/a Valley Anesthesiology and Pain Consultants had a data breach in 2016, in Arizona. The covered entity (CE), Valley Anesthesiology Consultants, Inc., d/b/a Valley Anesthesiology and Pain Consultants, was acquired by Sheridan Healthcorp, Inc., and became its subsidiary. A third party may have gained unauthorized access to the CE's computer systems on March 30, 2016, affecting 88,590 individuals. The types of electronic protected health information (ePHI) that were potentially accessed included demographic and clinical information. In response to the breach, the CE immediately disabled the account through which unauthorized access was potentially gained. A forensics firm investigated the breach and reported that approximately nine additional foreign internet protocol (IP) addresses attempted to use remote desktop protocols to access various parts of the CE's computer systems using accounts with administrator privileges. The CE “blacklisted” these IP addresses as the investigation continued in order to allow the firewall to block any attempts to access the electronic health record program through the remote desktop protocol. The forensics firm also identified fifteen suspicious local accounts and three administration accounts that were potentially compromised. The CE provided breach notification to HHS, affected individuals, and the media, and posted substitute notice in accordance with the Breach Notification Rule. OCR provided technical assistance regarding the CE's obligations to conduct a comprehensive and current security risk analysis and implement a corresponding risk management/mitigation plan to address any findings. OCR also provided TA regarding the CE's obligations to document evidence of its implemented security awareness training program, to include training material (not just email reminders), and a record of completion by workforce and management. Additionally, OCR stated the expectation that the CE clarify why non-ePHI applications are not governed by the same user access review procedures. [source] | |
Valley Family Medicine had a data breach in 2017, in Virginia. The information was breached via Paper/Films . [source] | Valley Hope Association had a data breach in 2016, in Kansas. The information was breached via Laptop . [source] | |
Valley View Hospital Association had a data breach in 2014, in Colorado. The information was breached via Desktop Computer. [source] | Valley Women's Health, S.C. had a data breach in 2017, in Illinois. The information was breached via Electronic Medical Record, Network Server. [source] | |
Vancouver Radiologists, PC had a data breach in 2016, in Washington. The covered entity (CE), Vancouver Radiologists, PC, on January 4, 2016, received telephone calls from a few patients that they received a postcard mammogram reminder, but with another patients name. The CE mailed 603 postcards which contained names, addresses, and generic reminders to schedule a mammogram. The CE submitted a breach notification report to HHS, affected individuals, and the media. In response to the breach, the CE stopped mailing the postcard reminder and revised its mailng procedures. The CE provided OCR with additional documentation specifically its HIPAA Notice of Privacy Practices Policy, as relevant to this breach investigation. OCR obtained assurances that the CE implemented the corrective actions listed above. The CE also provided refresher reminders to all staff members about is HIPAA privacy policies and procedures.More Information: https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf [source] | Vancouver Radiologists, PC had a data breach in 2016, in Washington. The information was breached via Network Server. [source] | |
VARO Healthcare had a data breach in 2014, in Pennsylvania. The information was breached via Paper/Films . [source] | Vascular Surgical Associates had a data breach in 2016, in Georgia. The information was breached via Network Server . [source] | |
Vcarve LLC d/b/a MD Manage had a data breach in 2014, in New Jersey. The information was breached via Network Server . [source] | Ventura County Health Care Agency had a data breach in 2015, in California. An employee took home paperwork containing the protected health information (PHI) of 777 individuals that was later recovered by an acquaintance of the employee and returned to the covered entity (CE), Ventura County Health Care Agency. The CE provided breach notification to HHS, affected individuals, and the media. The CE also notified the California Department of Public Health. Following the breach, the CE assigned all necessary employees for retraining, sanctioned the responsible employee, and sent a memo to all necessary staff prohibiting the removal of PHI from the facility. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Paper/Films Business associate present: No [source] | |
Ventura County Health Care Agency had a data breach in 2016, in California. An employee took home paperwork containing the protected health information (PHI) of 777 individuals that was later recovered by an acquaintance of the employee and returned to the covered entity (CE), Ventura County Health Care Agency. The CE provided breach notification to HHS, affected individuals, and the media. The CE also notified the California Department of Public Health. Following the breach, the CE assigned all necessary employees for retraining, sanctioned the responsible employee, and sent a memo to all necessary staff prohibiting the removal of PHI from the facility. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Paper/Films Business associate present: No [source] | Verity Medical Foundation had a data breach in 2017, in California. The information was breached via Network Server . [source] | |
Vertiv Co. Health & Welfare Plan had a data breach in 2017, in Ohio. The information was breached via Paper/Films . [source] | Veterans of Foreign Wars of the U.S. (VFW) had a data breach in 2014, in Maryland. Name, address, SSN were breached via Website . [source] | |
VGM Homelink had a data breach in 2014, in Iowa. A business associate (BA), Tri State Adjustments, of the covered entity (CE), VGM Homelink, committed a programing error which resulted in individuals receiving the wrong billing statements. This breach affected approximately 1,400 individuals and included patients' names, addresses, insurance information, and the medical equipment provided to them. The CE provided breach notification to HHS, affected individuals, and the media, and placed a notification about the breach on its website. The CE required its BA to implement new safeguards to prevent a similar breach from occurring. As a result of OCR's investigation, the CE had its BA update its policy and procedures for Breach Rule notification. Location of breached information: Paper/Films Business associate present: Yes [source] | ViaTech Publishing Solutions, Inc. had a data breach in 2018, in Minnesota. The information was breached via Paper/Films . [source] | |
Vibram USA, Inc. had a data breach in 2014, in Maryland. Name, credit card info were breached via Website . [source] | Vibrant Body Wellness had a data breach in 2016, in California. On March 5, 2016, a password protected laptop computer and a backup computer drive were stolen from the covered entity (CE), Vibrant Body Wellness, as a result of a break-in. The laptop computer contained the protected health information (PHI) of 726 individuals, including patients' addresses, dates of birth, names, clinical diagnoses/conditions, and financial claims information. The CE provided breach notification to HHS, affected individuals, and the media. It also notified law enforcement. The PHI which was on the stolen external hard drive was encrypted. Following the breach, the CE trained staff regarding its policies and procedures for safeguarding electronic PHI. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Laptop, Other Portable Electronic Device Business associate present: No [source] | |
Vidant Health had a data breach in 2016, in North Carolina. Vidant Health, the covered entity (CE), discovered that it filed numerous bankruptcy documents, from December 1, 2007, through March 9, 2016, that listed protected health information (PHI) that was not necessary for the filing. The breach affected 897 individuals and included patients' billing account numbers, social security numbers, medical record numbers, dates of birth, telephone numbers, sex, marital status, names, service dates, and account balances. The CE sent timely breach notification to HHS, affected individuals, and the media and posted substitute notification on its website. The CE provided identity theft protection for affected individuals for one year. In response to the breach, the CE revised and redacted its bankruptcy filings, filed blanked protective orders, and sealed proofs of claims in the public record. It also retrained applicable staff. OCR obtained assurances that the CE implemented the corrective actions listed above. [source] | Village of Oak Park, Illinois had a data breach in 2016, in Illinois. The information was breached via Email . [source] | |
Vincent Vein Center had a data breach in 2016, in Colorado. This breach appears to be part of the third party vendor, Bizmatic breach. Bizmatic provides EMR/EHR software to 15,000 customers in the medical industry. The media report specifically states that Vincent Vein Centers breach included Social Security numbers as part of the breach. [source] | Virtua Medical Group had a data breach in 2016, in New Jersey. The information was breached via Network Server and Other. [source] | |
Vision Care Florida, LLC had a data breach in 2016, in Florida. The information was breached via Desktop Computer . [source] | VisionQuest Eyecare had a data breach in 2017, in Indiana. The information was breached via Network Server . [source] | |
Visionworks Inc. had a data breach in 2014, in Texas. [source] | Visionworks Inc. had a data breach in 2014, in Texas. The information was breached via Network Server . [source] | |
Visionworks had a data breach in 2014, in Maryland. Name, address, phone number, health insurance info, dates of visit, health information were breached via Servers . [source] | vonica chau DDS PA had a data breach in 2014, in Texas. The information was breached via Desktop. [source] | |
W. Christopher Bryant DDS PC had a data breach in 2016, in Michigan. The information was breached via Other Portable Electronic Device . [source] | W. W. Grainger, Inc. had a data breach in 2017, in Illinois. The information was breached via Laptop . [source] | |
WA State Department of Social & Health Services had a data breach in 2014, in Washington. The covered entity (CE) erroneously sent mail to 3,104 clients at incorrect addresses due to a coding error in an internal database. The protected health information (PHI) contained in the mailing may have included clients' names, addresses, and client identification numbers, and some letters also included dates of birth, social security numbers, diagnoses, and financial information. The CE provided breach notification to HHS, affected individuals, and the media, and posted substitute notice on its website. Following the breach, the CE hired a firm to conduct an independent evaluation of the data breach to identify and correct the root causes of this incident. The CE formed a Quality Improvement Team to increase oversight of production and ensure that quality assurance processes are strictly followed. As a result of OCR's investigation, OCR provided technical assistance on the timeliness of notifications and incident reporting and obtained assurances that the corrective actions listed above were completed. [source] | Waiting Room Solutions Limited Liability Limited Partnership had a data breach in 2016, in New York. The information was breached via Email . [source] | |
Walgreen Co. had a data breach in 2014, in Illinois. The information was breached via Desktop Computer and Paper/Films. [source] | Walgreen Co. had a data breach in 2014, in Illinois. The information was breached via Paper/Films. [source] | |
Walgreen Co. had a data breach in 2014, in Maryland. information was stolen by an employee. [source] | Walgreen Co. had a data breach in 2015, in Illinois. [source] | |
Walgreen Co. had a data breach in 2015, in Illinois. The information was breached via Paper/Films . [source] | Walgreen Co. had a data breach in 2016, in Illinois. The information was breached via Paper/Films . [source] | |
Walgreen Co. had a data breach in 2017, in Illinois. The information was breached via Paper/Films . [source] | Walgreen Co. had a data breach in 2018, in Illinois. A business associate was not present. [source] | |
Walgreen Co. had a data breach in 2018, in Illinois. The information was breached via Paper/Films . [source] | Walmart Inc. had a data breach in 2018, in Arkansas. The information was breached via Email and Other. [source] | |
Wal-Mart Stores, Inc. had a data breach in 2016, in Arkansas. [source] | Walmart Stores, Inc. had a data breach in 2016, in Arkansas. The information was breached via Electronic Medical Record . [source] | |
Wal-Mart Stores, Inc had a data breach in 2016, in Arkansas. The information was breached via Paper/Films . [source] | Walmart, Inc. had a data breach in 2018, in Arkansas. The information was breached via Electronic Medical Record . [source] | |
Walnut Place had a data breach in 2017, in Texas. The information was breached via Network Server . [source] | Warren Clinic had a data breach in 2016, in Oklahoma. The information was breached via Network Server . [source] | |
Washington Health System Greene had a data breach in 2017, in Pennsylvania. The information was breached via Other Portable Electronic Device . [source] | Washington Health System had a data breach in 2016, in Pennsylvania. The information was breached via Portable Electronic Device. [source] | |
Washington National Insurance Company had a data breach in 2016, in Indiana. The information was breached via Paper/Films . [source] | Washington State Health Care Authority (HCA) had a data breach in 2016, in Washington. The information was breached via Email. [source] | |
Watsonville Chiropractic, Inc. had a data breach in 2016, in California. The information was breached via Network Server . [source] | Weekends Only, Inc. had a data breach in 2017, in Missouri. Name, payment card info, address were breached via Website . [source] | |
WellCare Health Plans, Inc. had a data breach in 2017, in Florida. The information was breached via Network Server . [source] | Wellmont Health System had a data breach in 2015, in Tennessee. On March 1, 2015, the covered entity (CE), Wellmont Health System, discovered that one of its employees had disposed of hand-written notes containing protected information (PHI) for 1,726 individuals at a local recycling center. The types of PHI involved in the breach included demographic and clinical information. The employee voluntarily resigned from her position. The CE provided breach notification to HHS, to affected individuals, to the media, and on its website. In response to the breach, the CE retrained its workforce to emphasize the importance of safeguarding and properly disposing of PHI. In addition, the CE reported that employees now utilize laptops and other mobile devices to create notes in patient records, making paper notes virtually nonexistent. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Other, Paper/Films Business associate present: No [source] | |
WellSpan Health had a data breach in 2017, in Pennsylvania. The information was breached via Paper/Films . [source] | West Kendall Baptist Hospital had a data breach in 2018, in Florida. A business associate was not present. [source] | |
Western Health Screening had a data breach in 2017, in Montana. The information was breached via Other Portable Electronic Device . [source] | Western Montana Clinic had a data breach in 2015, in Montana. A business associate was not present. [source] | |
Western Regional Center for Brain and Spine Surgery had a data breach in 2014, in Nevada. The information was breached via Network Server . [source] | Western Washington Medical Group Inc. had a data breach in 2018, in Washington. The information was breached via Paper/Films . [source] | |
Westminster Ingleside King Farm Presbyterian Retirement Communities, Inc. had a data breach in 2018, in Maryland. The information was breached via Desktop Computer, Network Server . [source] | White Blossom Care Center had a data breach in 2017, in California. A business associate was not present. [source] | |
White Coats Wellness had a data breach in 2017, in Florida. The information was breached via Email . [source] | White Lodging Services Corporation had a data breach in 2014, in Indiana. Names, credit and debit card information were breached via hackers . [source] | |
WhiteGlove Health had a data breach in 2015, in Texas. The information was breached via Email . [source] | Wm. Jennings Bryan Dorn VA Medical Center had a data breach in 2014, in South Carolina. The information was breached via Paper/Films . [source] | |
Women's Care of Somerset had a data breach in 2017, in Kentucky. The information was breached via Email . [source] | Women's Health Care Group of PA, LLC had a data breach in 2017, in Pennsylvania. The information was breached via Desktop Computer, Network Server . [source] | |
Woodhull Medical and Mental Health Center had a data breach in 2015, in New York. The information was breached via Laptop . [source] | Worldwide Insurance Services, LLC had a data breach in 2018, in Pennsylvania. The information was breached via Email . [source] | |
Wyndham Vacation Resorts, Inc. had a data breach in 2014, in Maryland. Name, address, ssn, financial account info were breached via Desktop Computer . [source] | Xand Corporation had a data breach in 2014, in New York. The information was breached via Network Server . [source] | |
Xerox State Healthcare, LLC had a data breach in 2014, in Texas. The information was breached via Desktop Computer, Email, Laptop, Network Server, Other and Other Portable Electronic Device. [source] | Yandy.com had a data breach in 2014, in Arizona. Name, address, credit/debit card info were breached via Website . [source] | |
Yellowstone Boys and Girls Ranch had a data breach in 2014, in Montana. Sometime between July 11, 2013, and January 27, 2014, the covered entity (CE), Yellowstone Boys and Girls Ranch, lost a resource notebook for on-call staff in its Lewiston office. The notebook included documents containing the protected health information (PHI) of 543 individuals including clients' names, addresses, dates of birth, schools, treatment providers, and community-based program information. The CE provided breach notification to HHS, affected individuals, and the media. The CE immediately stopped storing PHI in the on-call resource book and sanctioned the responsible personnel. As a result of OCR's investigation, and with substantial technical assistance from OCR, the CE began developing and revising necessary policies and procedures governing the storage, transportation, and handling of PHI. Additionally, the CE provided OCR with written assurance that it will train its staff on the new policies and procedures.[source] | You and Your Health Family Care, Inc. had a data breach in 2016, in Florida. [source] | |
Young Adult Institute, Inc. had a data breach in 2016, in New York. [source] | Zachary E. Adkins, DDS had a data breach in 2018, in New Mexico. The information was breached via Other Portable Electronic Device . [source] | |