Documenting all the places
personal data goes.
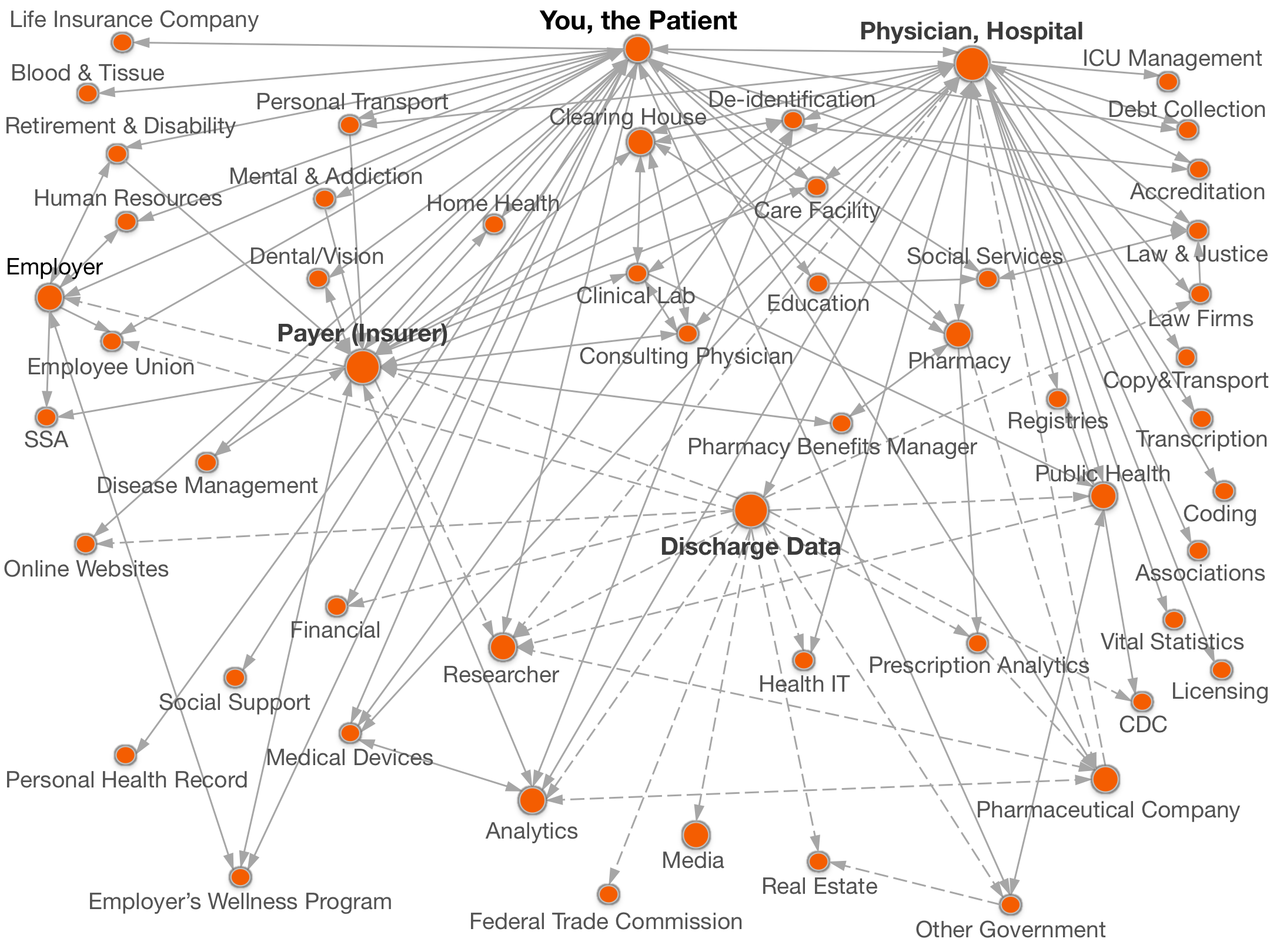
Legend:  with your name,
with your name, without your name.
without your name.
Click on a circle above for names of organizations and details of data shared.
A researcher receives data from many possible sources, including:
from health payers (e.g. insurance companies) for outcomes studies and economic analyses;
from pharmaceutical companies for clinical trials and drug studies,
from healthcare providers (e.g., hospitals) for outcomes studies and workflow analyses,
from discharge data for a variety of studies (see below),
from public health for a variety of population-based studies,
from you for various forms of consent-based research, and
from combinations of these.
Examples
National Bureau of Economic Research is a private, nonprofit research organization focused on the economy. The National Bureau of Economic Research purchases Discharge Data from at least 3 states: CA, MA, NY [source]. | Advanced Clinical Research Institute had a data breach in 2012, in California. A vehicle containing paper records was impounded overnight. Some papers with the sensitive information of research participants were discovered missing when the vehicle was reclaimed. The breach occurred on or around January 26. [source]. | |
Pacific Institute for Research and Evaluation is a research organization focused on health and social issues, including criminal justice. The Pacific Institute for Research and Evaluation purchases Discharge Data from at least 3 states: CA, NY, WA [source]. | Aegis Science Corporation had a data breach in 2011, in Georgia. A laptop and external hard drive containing patient information were stolen from a locked vehicle owned by an Aegis employee on November 22, 2011. The external hard drive contained names and Social Security numbers. It may have also contained drivers license numbers, dates of birth, and phone numbers. Though Aegis provides lab tests, results and medical records were not exposed. [source]. | |
Yale University is an Ivy League university in New Haven, Connecticut. Yale University purchases Discharge Data from at least 3 states: CA, MA, NY [source]. | Feinstein Institute for Medical Research had a data breach in 2012, in New York. A laptop stolen on or around September 2, 2012 contained current and former patient names, Social Security numbers, and other personal information. The laptop was taken from the car of a contractor or employee and may have also contained current and former patient mailing addresses, dates of birth, and medical information. Participants in about 50 different research studies that date back an unknown number of years were affected. (13000 records involved) [source]. | |
Health Council Of South Florida purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Kansas University had a data breach in 2007, in Kansas. A number of documents containing kansas University student, faculty and staff personal information were recovered from the recycling and trash in the Mathematics Department at Kansas University. The information included student exams, student change of grade forms, class rosters, copies of health insurance cards, copies of immigration forms as well as a copy of a Social Security card. [source]. | |
John Snow, Inc Karen Schnieder purchases statewide personal hospital discharge data from at least NJ [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Morris Heights Health Center had a data breach in 2011, in New York. A laptop was stolen from the area of MS 399/MS 459. It contained student information from the 2009-2010 school year such as names, dates of birth, genders, heights, weights, body mass indexes, ethnicity, asthma diagnoses, and influenza vaccination information. [source]. | |
Abt Associates Inc purchases statewide personal hospital discharge data from at least CA WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | New York Academy of Medicine had a data breach in 2007, in New York. A computer was stolen during an office burglary in October 28. The last four digits of research participants Social Security numbers, full names and dates of birth were on a database on the computer. Some participants also had their addresses and laboratory data exposed. [source]. | |
Advancement Project, Healthy City purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Radford University, Waldron School of Health and Human Services had a data breach in 2007, in Virginia. A computer security breach exposed the personal information, including SSNs, of children enrolled in the FAMIS program, Family Access to Medical Insurance Security. (2400 records involved) [source]. | |
Albert Einstein College Of Medicine purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | St. Louis University had a data breach in 2011, in Missouri. The Universitys network was hacked on December 12, 2010. The breach was discovered on December 13 and a statement was available on the Universitys website on January 31, 2011. Eight hundred students and 12,000 current and former employees and contractors were affected. Only people who worked for Saint Louis University at some point had their Social Security numbers exposed. Some students who received counseling through the Universitys Student Health Services may have had their names, dates of birth, tests, diagnosis and treatment information exposed. (12000 records involved) [source]. | |
Arizona State University purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Temple University School of Medicine had a data breach in 2011, in Pennsylvania. A former Chair of the Universitys Department of Ophthalmology and Assistant Dean for Medical Affairs faces 144 counts of health care fraud and making false statements in health care matters. The former faculty member and doctor is accused of causing thousands of false claims to be submitted to health care benefits programs between 2002 and 2007. The former faculty member allegedly instructed staff members to bring patient charts from other doctors to his office. Patient charts were improperly stored outside of his office and then fraudulently edited to make it seem as though the former faculty member had seen and evaluated the patients. The prosecution claims that after falsifying the documents, the former faculty member collected fees for services he had never performed. The former faculty member is also accused of falsifying the records of patients he had seen. The false claims may total more than $3,000,000. [source]. | |
Baker Institiute/Rice University purchases statewide personal hospital discharge data from at least NJ [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | University of Alabama had a data breach in 2009, in Alabama. Seventeen of 400 databases were tapped by hackers. Personal information may have been stolen. One of those computers contained lab results for people tested at the campus medical center. The servers had a database containing 37,000 records of lab data. They contain the names, addresses, birthdates and Social security numbers of each person who has had lab work, such as a blood or urine test, done on the UA campus since 1994. (37000 records involved) [source]. | |
Baylor College Of Medicine purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | University of California, Berkeley had a data breach in 2009, in California. Hackers infiltrated restricted computer databases. Personal information of 160,000 current and former students and alumni may have been stolen. The University says Social Security numbers, health insurance information and non-treatment medical records dating back to 1999 were accessed. The breach was discovered April 21, 2009, when administrators performing routine maintenance identified messages left by the hackers. They found that restricted electronic databases had been illegally accessed by hackers beginning on October 9, 2008 and continued until April 6, 2009. All of the exposed databases were removed from service to prevent further attacks. (160000 records involved) [source]. | |
Baylor University purchases statewide personal hospital discharge data from at least CA NJ WA IL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | University of California, San Francisco (UCSF) had a data breach in 2007, in California. A computer file server containing names, contact information, and Social Security numbers for study subjects and potential study subjects related to research on causes and cures for different types of cancer was stolen from a locked UCSF office. For some individuals, the files also included personal health information. (3000 records involved) [source]. | |
Biddle Law Library, University Of Pennsylvania purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | University of Florida had a data breach in 2010, in Florida. Social Security numbers or Medicaid identification numbers were shared with a telephone survey company and included on address labels sent out to request research participation. The letters were sent through the U.S. Postal Service on May 24th and the issue was discovered on June 6th. (2,047 records involved) [source]. | |
Boston University purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | University of Iowa Department of Psychology had a data breach in 2006, in Iowa. A computer containing SSNs of 14,500 psychology department research study subjects was the object of an automated attack designed to store pirated video files for subsequent distribution. (14500 records involved) [source]. | |
Boston University School Of Medicine purchases statewide personal hospital discharge data from at least CA FL ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | University of Mississippi Medical Center and Mississippi State Department of Health had a data breach in 2011, in Mississippi. Research study participants may have had their personal information exposed by the theft of a laptop. The laptop was stolen when UMMC employees left the laptop unsecured for a short period of time against departmental guidelines. It was reported stolen on October 31, and the employees who left it unsecured were disciplined. Two databases with research related health information were on the laptop. One had the age, sex, race, medical record number, zip code, and lab results of 1,400 patients. The other database contained unspecified protected health information from 75 patients. [source]. | |
Brown University purchases statewide personal hospital discharge data from at least FL CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | University of North Carolina, Chapel Hill had a data breach in 2009, in North Carolina. A hacker has infiltrated a computer server housing the personal data of 236,000 women enrolled in a UNC Chapel Hill research study. The Social Security numbers of 163,000 participants were among the information exposed. The data is part of the Carolina Mammography Registry, a 14-year-old project that compiles and analyzes mammography data submitted by radiologists across North Carolina.UPDATE (10/6/10): A lead researcher at the University is fighting a demotion and pay cut that resulted from the data breach in the medical study she directs. It appears that the incident firstoccurred in 2007 and was not discovered until 2009. An attorney representing the researcher claims that his client is not at fault because the University knew that the programs computer system had security deficiencies in 2006. The Universityclaims that the researcher acted negligently,butthe attorney claims that the researcher was not alerted to the security flaws and there is no evidence that the researcher violated or ignored rules in obtaining patient information.UPDATE (5/9/2011): The researcher and University reached a settlement. The researcher agreed to retire at the end of 2011 and will receive her full rank and salary until that time. (163,000 records involved) [source]. | |
Cal State Fresno/Central Valley Health Policy Inst purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | University of Washington Hospital had a data breach in 2011, in Washington. A customer purchased a piece of furniture from the Universitys Surplus Store that had the medical records of patients. The information in the records was mostly x-ray and MRI images of spines. [source]. | |
California Healthcare Foundation purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Wentworth Institute of Technology had a data breach in 2011, in Massachusetts. On December 22 of 2010, Wentworth became aware of a breach that left sensitive student information online. A file was accidentally placed on Wentworths website at some point. Current and former students may have had their names, Social Security numbers, dates of birth and medical information exposed. (1300 records involved) [source]. | |
Advanced Fertility Center of Chicago had a data breach in 2016, in Illinois. The information was breached via Desktop Computer, Electronic Medical Record, Network Server . [source] | Advanced Spine & Pain Center had a data breach in 2017, in Texas. The information was breached via Electronic Medical Record, Network Server. [source] | |
American Health Inc. had a data breach in 2014, in Puerto Rico. [source] | Andrea Yaley, DDS had a data breach in 2017, in California. The information was breached via Desktop Computer, Electronic Medical Record, Email, Network Server . [source] | |
Anne M. Cummings, M.D. F.A.C.P had a data breach in 2016, in California. On August 22, 2016, I received confirmed notice from my electronic medical record provider that their electronic system was subject to a malware attack on July 26, 2016. They became aware of the incident on July 27, 2016, and I am informed that they promptly took action to secure their systems.I immediately requested further information to understand what happened and to determine which, if any, of my patients were affected. On September 14, 2016, I was provided further detail of the events, and learned that the company, Marin Medical Practice Concepts, Inc. (MMPC), experienced a ransomware infection. Ransomware is a type of malware which restricts access to the computer system that it infects, and demands that a ransom be paid to the creator of the malware to remove the restriction. The third party forensic IT firm hired to investigate this incident found no evidence that patient information was viewed, transferred or accessed. However, during the restoration process of their system, MMPC has informed me that one of their backup systems failed causing the loss of consultation notes between July 11, 2016 and July 26, 2016. Given these events, I wanted to notify you of this matter. [source] | Arkansas State University College of Education and Behavioral Science's Department of Childhood Services had a data breach in 2014, in Arkansas. Arkansas State University was notified by the Arkansas Department of Human Services of a data breach in their College of Education and Behavioral Science's Department of Childhood Services database, potentially exposing personally identifiable information. According to A-State's Chief Information Officer Henry Torres, “we have confirmed unauthorized access to data, but we have no reports regarding illegal use of the information in these files,” Torres said. [source] | |
AspiraNet had a data breach in 2016, in California. AspiraNet notified individuals of a databreach when a spoofing email went out on March 21, 2016. The spoofing email that resulted in W-2 information being disclosed. The information compromised included names, residential addresses, and Social Security numbers. [source] | Asset Marketing Services, LLC d/b/a GovMint.com had a data breach in 2014, in Maryland. Name, address, email address, and credit card info were breached via Website . [source] | |
Athens Heart Center, P.C. had a data breach in 2018, in Georgia. The information was breached via Electronic Medical Record . [source] | AU Medical Center, Inc. had a data breach in 2017, in Georgia. The information was breached via Email . [source] | |
Azusa Pacific University had a data breach in 2014, in Maryland. Name and ssn were breached via Laptop . [source] | BayBio had a data breach in 2014, in California. BayBio.org has notified individuals of a data breach to their online payment system. The non-profit organization has notified that the hacking to their payment system compromised credit card numbers in process.The hacker inserted files that captured keystrokes of visitors to their site which included credit card numbers when individuals were either paying for a membership or an event being held by the non-profit. Payments are being taken by phone until the breach has been repaired. [source] | |
Baylor Medical Center at Carrollton had a data breach in 2014, in Texas. The information was breached via Electronic Medical Record. [source] | Baylor Medical Center at Irving had a data breach in 2014, in Texas. The information was breached via Email. [source] | |
Baylor Medical Center at McKinney had a data breach in 2014, in Texas. The information was breached via Email. [source] | Baylor Regional Medical Center at Plano had a data breach in 2014, in Texas. The information was breached via Email. [source] | |
Berea College had a data breach in 2014, in Kentucky. The information was breached via Electronic Medical Record. [source] | Berkeley Endocrine had a data breach in 2016, in California. On April 22, 2016, my office was subject to a spam email which we believe went to many patients. Though no patient information was affected by that correspondence, we sent a notification email to al individuals on our email list, informing them of the spam. Inadvertently, the recipient list for the notificaation email on April 22, 2016 was not hidden.The information compromised included first and last names, email addresses. [source] | |
Butler University had a data breach in 2014, in Indiana. [source] | Butler University had a data breach in 2014, in Maryland. The information was breached via Website. [source] | |
California Health & Longevity Institute had a data breach in 2016, in California. [source] | California State University, East Bay had a data breach in 2014, in California. California State University, East Bay has notified individuals of a data breach that has occurred on August 11, 2014 when the University discovered unauthorized access to individuals information when an overseas IP address appears to have used a software tool designed to access information on a server without being detected. The server targeted contained personal information on various employment record transactions and some extended learning course information. The specific information breached included names, addresses, Social Security Numbers and dates of birth. The University has set up 12 months free of Experian's ProtectMyID for those affected. For additional questions or concerns individuals can contact (888) 738-3759 a toll free number specifically set up to deal with questions/concerns regarding this breach. [source] | |
California State University, East Bay had a data breach in 2014, in Maryland. Name, ssn, address were breached via Website . [source] | Carson Valley Medical Center had a data breach in 2017, in Nevada. The information was breached via Email . [source] | |
Center for Orthopaedic Specialists - Providence Medical Institute (PMI) had a data breach in 2018, in California. The information was breached via Network Server . [source] | CHI Franciscan Healthcare Highline Medical Center had a data breach in 2016, in Washington. The information was breached via Network Server . [source] | |
City College of San Francisco had a data breach in 2016, in California. Name, dob, ssn, record identifier were breached. [source] | Columbia Southern University had a data breach in 2014, in Maryland. Name, address, ssn were breached via email . [source] | |
Covenant Medical Center, Inc. had a data breach in 2017, in Michigan. The information was breached via Electronic Medical Record . [source] | Dr. Zain Kadri had a data breach in 2017, in California. The theft of confidential files from a prominent Beverly Hills surgeon could affect the privacy and financial security of as many as 15,000 patients, according to a spokesman for the doctor and law enforcement officials.A statement issued by Dr. Zain Kadri’s office said a former staff member “stole credit card information, debit card information, IDs, copies of checks, usernames, passwords” and photographed patients before and during surgery. A spokesman for Kadri’s office, who declined to be identified, said the theft might affect patients in at least 17 states and seven countries outside the United States. [source] | |
Duke University Health System had a data breach in 2014, in North Carolina. The information was breached via Other Portable Electronic Device . [source] | EASTCONN had a data breach in 2017, in Connecticut. In Dec. 2017 EASTCONN suffered a data breach affecting 194 records, incl. Driver's license and SSN. [source] | |
Evolution Nature Corp., d/b/a The Evolution Store had a data breach in 2014, in Maryland. Name, email address, phone number, billing address, shipping address, order info, user Name, credit/debit card data, were breached via Website . [source] | Eye Institute of Corpus Christi had a data breach in 2016, in Texas. After review of the response from the entity, OCR determined that a breach of protected health information did not occur. Location of breached information: Electronic Medical Record Business associate present: No [source] | |
Eye Institute of Marin had a data breach in 2016, in California. On or about August 22, 2016, we received confirmed notice from our electronic medical record provider that their electronic system was subject to a malware attack on July 26, 2016. They became aware of the incident on July 27, 2016, and we are informed that they promptly took action to secure their systems. We immediately requested further information to understand what happened and to determine which, if any, of our patients were affected. On September 14, 2016, we were provided further detail of the events, and learned that the company, MMPC, experienced a ransomware infection. Ransomware is a type of malware which restricts access to the computer system that it infects, and demands that a ransom be paid to the creator of the malware to remove the restriction. The third party forensic IT firm hired to investigate this incident found no evidence that patient information was viewed, transferred or accessed. However, during the restoration process of their system, MMPC has informed us that one of their backup systems failed causing the loss of consultation notes between July 11, 2016 and July 26, 2016. Given these events, we wanted to notify you of this matter. [source] | Fast Forward Academy had a data breach in 2015, in Florida. The information was breached via Network Server. [source] | |
Fort Hays State University had a data breach in 2014, in Kansas. Fort Hays State University has notified 138 of it's graduates that their personal information may have been compromised when personal information was "accidentally" exposed on the Internet. The information exposed included Social Security Numbers and various other pieces of personal information.The university stopped storing Social Security Numbers of students five years ago, however anyone who attended the university prior to 5 years ago, their SSN information is still part of the university database. [source] | Glendale Adventist Medical Center had a data breach in 2016, in California. The information was breached via Electronic Medical Record . [source] | |
Group Health Plan of Hurley Medical Center had a data breach in 2014, in Michigan. The information was breached via Email. [source] | Heart Center of Southern Maryland, L.L.P. had a data breach in 2016, in Maryland. The information was breached via Electronic Medical Record . [source] | |
ICANN.org had a data breach in 2015. [source] | Institute for Women's Health had a data breach in 2017, in Texas. The information was breached via Network Server . [source] | |
International Code Council had a data breach in 2016, in California. Name and payment card info were breached. [source] | Iowa State University had a data breach in 2014, in Iowa. [source] | |
Jacobi Medical Center had a data breach in 2015, in New York. The information was breached via Email . [source] | Jefferson Medical Associates, P.A. had a data breach in 2016, in Missouri. A Laurel clinic has issued a warning to a small group of their patients after a recent data breach of their systems. Jefferson Medical Associates issued a press release stating that privacy events may have compromised certain personal information. [source] | |
Jersey City Medical Center had a data breach in 2015, in New Jersey. The information was breached via Email . [source] | Johns Hopkins University (Identity Theft) had a data breach in 2014, in Maryland. files inadvertently made accessible on the internet Location of breached information: Website Business associate present: No [source] | |
Legal Aid Society of Orange County (LASOC) had a data breach in 2017, in California. [source] | Louisiana State University Health Sciences Center-New Orleans had a data breach in 2015, in Louisiana. The information was breached via Laptop . [source] | |
Massac County Surgery Center dba Orthopaedic Institute Surgery Center had a data breach in 2018, in Illinois. The information was breached via Email . [source] | McLaren Medical Group, Mid-Michigan Physicians Imaging Center had a data breach in 2017, in Michigan. The information was breached via Network Server . [source] | |
Medical Informatics Engineering had a data breach in 2015, in Indiana. The information was breached via Electronic Medical Record, Network Server. [source] | Memorial Hermann Health System, reporting on behalf of Memorial Hermann Health System Employee Group Health Plan had a data breach in 2016, in Texas. The information was breached via Paper/Films . [source] | |
Middletown Medical P.C. had a data breach in 2018, in New York. The information was breached via Electronic Medical Record . [source] | Momentum for Mental Health had a data breach in 2016, in California. On June 3, 2016, Momentum was targeted by an e-mail scam called spoofing. We discovered this incident within hours of it taking place. Nonetheless, it resulted in Momentum inadvertently making person information from your Form W-2 available to an unknown third party.The information compromised included Social Security numbers, information, wage information, tax deductions.More Information: http://oag.ca.gov/ecrime/databreach/reports/sb24-62338 [source] | |
Mount Pleasant School District had a data breach in 2015, in Texas. [source] | N. Fred Eaglstein, D.O. d/b/a Dermatology and Laser Center had a data breach in 2017, in Florida. The information was breached via Electronic Medical Record . [source] | |
North Dakota University had a data breach in 2014, in North Dakota. North Dakota University System has notified individuals of a security breach of a computer server that stores personal information on students, staff and faculty. On February 7, 2014 the server was hacked into and more than 209,000 current and former students and 780 faculty and staff had personal information stored on thus server that included names and Social Security numbers according to Larry Skogen, the Interim Chancellor. The university has notified officials and has set up a website www.ndus.edu/data with information and is organizing a call center for questions from those who were affected.Authorities have announced that "an entity operating outside the Unites States apparently used the server as a launching pad to attack other computers, possibly accessing outside accounts to send phishing emails" [source] | NorthShore University Healthsystem had a data breach in 2014, in Maryland. Name, address, email address, dob, marital status, benefits info, ssn were breached via email . [source] | |
Nova Southeastern University had a data breach in 2014, in Maryland. Name, dob, address, email address, phone number, NSU identification number, SSN were breached via Website . [source] | Nova Southeastern University had a data breach in 2017, in Florida. The information was breached via Other Portable Electronic Device . [source] | |
Occidental College had a data breach in 2017, in California. What Happened?The college has reason to believe that on or around June 1, 2017, an unauthorized person may have gained access to a computer file containing a limited amount of personality identifiable information. The college has conducted a thorough investigation into what happened. The file in question included names, Oxy ID numbers and associated encoded data that enables Oxy ID cards to function as on-campus debit cards. The file did NOT include Social Security numbers, driver's license or other state-issued ID numbers, financial information (Such as credit card or banking information), or other sensitive personal data. [source] | Oklahoma State University Center for Health Sciences had a data breach in 2018, in Oklahoma. The information was breached via Network Server . [source] | |
Oklahoma University had a data breach in 2017, in Oklahoma. [source] | Pace University had a data breach in 2016, in New York. The information was breached via Network Server. [source] | |
Palomar College had a data breach in 2017, in California. On January 19, 2017, we learned that an unauthorized individual may have accessed part of our network that contained IRS Form W-2s for some of our employees. Upon learning of this, we immediately began an investigation and contacted law enforcement. What Information Was Involved Our ongoing investigation has determined that the unauthorized individual may have accessed your IRS Form W-2. The information that could have been accessed included your name, address, and Social Security number. [source] | Palomar Health (Palomar Medical Center (Escondido) had a data breach in 2018, in California. The information was breached via Electronic Medical Record . [source] | |
Penn State College of Engineering had a data breach in 2015, in Pennsylvania. Penn State's College of Engineering announced that their servers were hacked in two different intrustions. The hackers are believed to be based in China and may have exposed "at least 18,000 people and possibly other sensitive data". Penn State's President sent a letter out to students and faculty informing them that the college's network had been disconnected to the Internet while they investigate the intrusio. The information compromised has not yet been made public, all College of Engineering faculty, staff and students were affected. Those who also had taken at least one engineering class would be affected as well. The university is requiring those who meet this criteria change their username and password. They have set up a VPN and will be required to use two-factor authentication. [source] | Point Loma Nazarene University had a data breach in 2014, in Maryland. Names,SSN, credit card numbers and CVV code or expiration date, usernames and passwords, dln were breached via Email . [source] | |
Point Park University had a data breach in 2014, in Pennsylvania. On Wednesday March 5, 2014 Point Park University in Pittsburgh Pennsylvania notified employees of a possible data breach that included names, home addresses, Social Security numbers, wage information, birthdates, bank accounts and routing numbers.The Point Park President stated that as many as 1,800 employees could have been affected by this breach."The university was expecting a package from its payroll processing vendor Ceridian, but when the package arrived to campus it was missing all of the accompanying reports, according to an internal email obtained by the Pittsburgh Post-Gazette."The university is working with authorities and an investigation has been launched. The law firm that represents the university is currently putting a letter together to those who were affected that will include call-center information and other services offered. [source] | Recovery Institute of the South East P.A. had a data breach in 2017, in Florida. The information was breached via Desktop Computer, Electronic Medical Record, Email, Laptop, Network Server, Other, Other Portable Electronic Device, and Paper/Films. [source] | |
Ridgeview Medical Center had a data breach in 2017, in Minnesota. The information was breached via Email . [source] | Riverside Community College had a data breach in 2014, in California. Riverside Community College has suffered a data breach affecting 35,212 students. On May 30th, a district employee emailed a file containing information about all students who were enrolled in the spring term to a colleague working at home due to illness, for a research report that was on a deadline. The district employee used a personal email account to send the data because the file was too large for the district's secure email to send. The employee then typed in the incorrect email address.The information contained in the file included names, addresses, birth dates, Social Security numbers, email addresses, student ID numbers, and telephone numbers. T [source] | |
Ron's Pharmacy Services had a data breach in 2017, in California. The information was breached via Email. [source] | Rosalind Franklin University of Medicine had a data breach in 2014, in Illinois. The information was breached via Email . [source] | |
Rutgers University had a data breach in 2017, in New Jersey. [source] | San Jose Evergreen Community College District had a data breach in 2016, in California. On November 7, 2016, we learned that an SJECCD employee had inadvertently uploaded a file containing the personal information of certain SJECCD students to a publicly accessible folder on the SJECCD website. The file was temporarily stored on the webserver and could be retrieved in search results. Upon learning this, we promptly removed the file from the website and began an investigation into the incident. Our investigation indicates that the incident was an accident, and not the result of any kind of malicious attack.What Information Was Involved?The personal information contained in the file may have included your name, date of birth, and Social Security number. Although we are not aware at this time of any third party misusing your personal information, we take privacy and security very seriously and wanted to inform you about this situation, the steps we are taking to protect your information, and steps you may take to help protect yourself. [source] | |
Seattle University had a data breach in 2014, in Maryland. Name, bank routing and checking account info were breached via Website . [source] | Seattle University had a data breach in 2014, in Washington. The information was breached via Website . [source] | |
Southern New Hampshire University had a data breach in 2016, in New Hampshire. [source] | Summit Reinsurances Services had a data breach in 2017, in Indiana. OCR opened an investigation of the covered entity (CE), Sunbury Plaza Dental, after it reported that a secured storage unit containing paper protected health information (PHI) was burglarized. The storage unit contained PHI for 7,981 individuals. The medical records contained at this location included names, addresses, dates of birth, social security numbers, and treatment information. The CE provided breach notification to HHS, affected individuals, and the media, and also posted substitute notice on its website. The CE offered one year of identity monitoring to all affected individuals. Following the breach, the CE revised its records retention policies to minimize the number of paper records in storage. OCR obtained assurances that the CE implemented the corrective actions noted above. Location of breached information: Paper/Films Business associate present: Yes [source] | |
Temple University School of Medicine had a data breach in 2011, in Pennsylvania. A former Chair of the Universitys Department of Ophthalmology and Assistant Dean for Medical Affairs faces 144 counts of health care fraud and making false statements in health care matters. The former faculty member and doctor is accused of causing thousands of false claims to be submitted to health care benefits programs between 2002 and 2007. The former faculty member allegedly instructed staff members to bring patient charts from other doctors to his office. Patient charts were improperly stored outside of his office and then fraudulently edited to make it seem as though the former faculty member had seen and evaluated the patients. The prosecution claims that after falsifying the documents, the former faculty member collected fees for services he had never performed. The former faculty member is also accused of falsifying the records of patients he had seen. The false claims may total more than $3,000,000. [source] | The Center for Election Systems at Kennesaw State University had a data breach in 2017, in Georgia. The City of Beaumont has suspended its online water bill payment system due to a potential data breach, chief technology officer Bart Bartkowiak said.Bartkowiak said the City of Beaumont received several notifications of unauthorized iTunes charges on bill-payers' accounts. Bartkowiak suggested any residents who have paid their water bills online between Aug. 1 and Aug. 24 to check their accounts for suspicious activity. He said that anyone who finds suspicious activity on their account should report it to their credit card issuer and their bank, to ask that their card be deactivated, to request that a fraud alert be placed on their account, and to request copies of all credit reports. [source] | |
The Medical College of Wisconsin, Inc. had a data breach in 2017, in Wisconsin. The information was breached via Email . [source] | The Trustees of Purdue University had a data breach in 2018, in Indiana. The information was breached via Desktop Computer . [source] | |
The University of Texas MD Anderson Cancer Center had a data breach in 2014, in Texas. The information was breached via Other Portable Electronic Device . [source] | The University of Vermont Medical Center had a data breach in 2017, in Vermont. The information was breached via Email . [source] | |
The University of Wisconsin-Parkside had a data breach in 2014, in Wisconsin. Students were notified by officials from The University of Wisconsin-Parkside of a data breach that occured to their system by hackers that installed malware on one university server. The information that is at risk includes names, addresses, telephone numbers, email addresses and Social Security numbers. The breach affects students who were either admitted or enrolled at the university since the fall of 2010. The server was shut down and the hacking was reported to local authorities. After launching an investigation it appears the malware was searching for credit card information and they show no evidence that any Social Security numbers were compromised. The university has set up a website with information for those who may have been affected http://www.uwp.edu/explore/contactus/index.cfm [source] | Thomas Edison State University had a data breach in 2018, in New Jersey. [source] | |
Townsend Enterprises, Inc. d/b/a The Sinclair Institute had a data breach in 2014, in Maryland. Name, credit card info were breached via Payment card system . [source] | Tribeca Film Institute had a data breach in 2014, in New York. [source] | |
Triple-S Salud had a data breach in 2014, in Puerto Rico. [source] | Triple-S Salud, Inc. - Breach Case#2 had a data breach in 2014. [source] | |
UC Davis Health had a data breach in 2017, in California. A phishing attack on the University of California Davis Health may have compromised the personal health information of 15,000 patients.Officials discovered the breach on May 15, when an employee responded to a phishing email with his or her email account login credentials. The hacker proceeded to access that account.Once inside, the hacker was able to access the employee’s email messages and both view and or obtain patient PHI. However, officials said the investigation did not find evidence the hacker viewed the information, but it could not rule out the possibility. [source] | UC Davis Medical Center, Privacy Manager Breach had a data breach in 2014, in California. The information was breached via Email. [source] | |
UCDC, Washington Center had a data breach in 2014, in District Of Columbia. [source] | UCLA had a data breach in 2017, in California. More than 30,000 current and former UCLA students are being warned Saturday about a potential security breach.The university said someone hacked into a server containing some students' personal data.Officials don't believe the hacker obtained any sensitive information, though UCLA is offering one year of free identity-protection services to anyone affected. [source] | |
UHHS Geauga Medical Center had a data breach in 2016, in Ohio. The information was breached via Electronic Medical Record . [source] | Uniformed Services University had a data breach in 2015, in Maryland. A hacker by the name of Kuroi SH infiltrated the United States based Uniformed Services University (USU) leaking 2014 login credentials online.USU educates service members in for the military's medical corps in the US and abroad. The university also provides training to military physicians, nurses and educators. \"The hacker uploaded a deface page on 8 of the USU websites on which a database of all the websites, names, emails and clear-text passwords of those working for the university are held.\" [source] | |
Unity Recovery Group, Inc.,Starting Point Detox LLC, Lakeside Treatment Center LLC, Changing Tides Transitional Living LLC, Unity Recovery Center, Inc had a data breach in 2015, in Florida. Unity Recovery Group, Inc. (Unity) shared patient information with other covered entities for continuation of substance abuse treatment. It erroneously believed this practice to be an impermissible disclosure and filed a breach report with HHS. After OCR determined that no breach had occurred, OCR provided technical assistance to Unity regarding permissible disclosures for treatment purposes, the difference between “consent” and “authorization” under HIPAA, the definition of a breach of protected health information, when notification must be provided, and when notification is not required. Further, Unity and its affiliates permanently closed on December 31, 2015 with no intention to resume future operations in the same legal entity name. [source] | University at Buffalo had a data breach in 2018, in New York. WIVB4 is reporting:University at Buffalo leaders, along with their security team, are investigating a data breach of external third-party accounts. They say it's affected more than 25-hundred accounts campus wide. About 18-hundred of those are student accounts. [source] | |
University California Berkeley had a data breach in 2015, in California. Campus officials are alerting nearly 80,000 current and former faculty, staff, students and vendors about a criminal cyber security breach on a campus system, making vulnerable thousands of Social Security or bank account numbers.The data breach occurred Dec. 28 to a portion of Berkeley Financial System, or BFS, a software used by the campus for financial management.“We don’t see any evidence that this is the kind of attacker that actually did access the data or did anything to take that data from the system,” said campus Chief Information Security Officer Paul Rivers in a phone press conference Friday.The system that houses BFS is large and complicated, Rivers said, containing numerous machines and various types of software packages. When the campus detected a vulnerability in one of these areas in November, the campus began installing and testing a security fix — known as a patch — which can take weeks, Rivers said during the press call. During this process, attackers were able to discover a security flaw and gained access to the system.BFS contains the information of about 50 percent of current students and 65 percent of active employees. Affected individuals largely include students, faculty and staff who received payments from the campus, mainly through electronic fund transfers. Those who received paper payments, however, may have also been affected. [source] | University California Santa Barbara had a data breach in 2014, in California. [source] | |
University Development and Alumni Relations at the Penn State College of Medicine had a data breach in 2014, in Pennsylvania. Penn State has notified 1,176 individuals that a data breach of their personal information had been breached. The Office of University Development and Alumni Relations at the Penn State College of Medicine was found to be infected with malware that enabled it to communicate with an unauthorized computer outside the network. The university used Social Security numbers as a personally identifiable number for students and these SSNs were found in an archived College of Medicine alumni list last used in 2005. [source] | University Gastroenterology, Inc. had a data breach in 2016, in Rhode Island. The information was breached via Network Server . [source] | |
University Gastroenterology had a data breach in 2016, in Rhode Island. [source] | University Hospitals had a data breach in 2015, in Ohio. The information was breached via Electronic Medical Record . [source] | |
University of Alaska had a data breach in 2018. [source] | University of California Davis Health had a data breach in 2017, in California. The information was breached via Email . [source] | |
University of California Davis Medical Center had a data breach in 2014, in California. The information was breached via Electronic Medical Record. [source] | University of California Irvine Medical Center had a data breach in 2015, in California. The information was breached via Electronic Medical Record . [source] | |
University of California, Berkeley had a data breach in 2009, in California. Hackers infiltrated restricted computer databases. Personal information of 160,000 current and former students and alumni may have been stolen. The University says Social Security numbers, health insurance information and non-treatment medical records dating back to 1999 were accessed. The breach was discovered April 21, 2009, when administrators performing routine maintenance identified messages left by the hackers. They found that restricted electronic databases had been illegally accessed by hackers beginning on October 9, 2008 and continued until April 6, 2009. All of the exposed databases were removed from service to prevent further attacks. [source] | University of California, Los Angeles Health had a data breach in 2015, in California. The information was breached via Laptop . [source] | |
University of California, Los Angeles Health had a data breach in 2015, in California. The information was breached via Network Server . [source] | University of California, Riverside Graduate Division offices had a data breach in 2015, in California. [source] | |
University of Central Florida had a data breach in 2016, in Florida. The University of Central Florida notified current and former students of a data breach when they discovered unauthorized access into the university system.The information compromised included financial records, medical records, grades and Social Security numbers. [source] | University of Connecticut had a data breach in 2015, in Connecticut. [source] | |
University of Idaho had a data breach in 2017, in Idaho. The university detected that one of their accounts was being used to send phishing email. An investigation determined that the employees email messages contained personal information for 257 individuals. Information included names, addresses and social security numbers. [source] | University of Illinois, Chicago had a data breach in 2014, in Illinois. [source] | |
University of Maryland Orthopaedic Associates, P.A. had a data breach in 2017, in Maryland. The information was breached via Email . [source] | University of Maryland had a data breach in 2014, in Maryland. The information was breached via Email. [source] | |
University of Mississippi Medical Center had a data breach in 2017, in Mississippi. The information was breached via Electronic Medical Record, Network Server. [source] | University of Northern Iowa had a data breach in 2016, in Iowa. Over 100 University of Northern Iowa employees reported that their tax returns had been rejected in 2014 because someone had filed a return fraudulently on their behalf, collecting their refund. After further investigation, a 45 year old man, Bernard Ogie Oretekor has been charged with the tax indentity theft when computers belonging to Oretekor in connection with a separate investigation, uncovered the information on the employees. It is still not clear how Oretekor gained this information on the employees. More information: http://www.kcrg.com/content/news/Suspect-Charged-in-University-of-Northe... [source] | |
University of Oklahoma, OU Physicians had a data breach in 2017, in Oklahoma. The information was breached via Email . [source] | University of Rochester Medical Center & Affiliates had a data breach in 2015, in New York. The information was breached via Paper/Films . [source] | |
University of Utah Health had a data breach in 2018, in Utah. The information was breached via Laptop and Other Portable Electronic Device . [source] | University of Virginia Medical Center had a data breach in 2018, in Virginia. The information was breached via Desktop Computer, Laptop . [source] | |
University of Virginia had a data breach in 2015, in Virginia. The University of Virginia has notified employees of a data breach, when a cyber attack of their human resources system was discovered. The attack was initiated by a phishing email asking for usernames and passwords to their HR system and one or more employees fell for the phishing scam. The information compromised included 1,400 W2's (which includes names, addresses, Social Security numbers,etc) of employees and direct deposit banking information of an additional 40 employees. According to the university the attackers gained access to the system sometime in early November 2014 and continued through February 2015. The FBI led investigation has resulted in the arrest of suspects who are currently being held in custody, no names have been released. [source] | University of Virginia had a data breach in 2016, in Virginia. The University of Virginia has notified individuals of a hacking originating from China and accessed the IT systems of the university. The university has stated that no Social Security numbers or banking information was compromised. [source] | |
University of Wisconsin - Madison had a data breach in 2017, in Wisconsin. The information was breached via Paper/Films . [source] | University of Wisconsin Hospitals and Clinics Authority had a data breach in 2016, in Wisconsin. The information was breached via Paper/Films . [source] | |
University of Wisconsin-Madison School of Pharmacy had a data breach in 2014, in Wisconsin. The information was breached via Other Portable Electronic Device . [source] | University Urology, P.C. had a data breach in 2014, in Tennessee. [source] | |
Urology Austin had a data breach in 2017, in Texas. On January 22, 2017, Urology Austin was the victim of a ransomware attack that encrypted the data stored on our servers. Within minutes, we were alerted to the attack, our computer network was shut down, and we began an investigation. We also began to take steps to restore the impacted data and our operations. What information was involved? Our investigation indicates that your personal information may have been impacted by the ransomware, including your name, address, date of birth, Social Security number, and medical information. [source] | VA Corporate Data Center Operations/Austin Information Technology Center had a data breach in 2015, in Texas. According to the Health and Human services website the VA Corporate Data Center suffered a data breach when they discovered their network server was hacked compromising personal information. The types of information compromised was not communicated. [source] | |
Wabash College had a data breach in 2015, in Indiana. [source] | Washington University School of Medicine had a data breach in 2017, in Missouri. The information was breached via Email . [source] | |
Wayneburg University had a data breach in 2014, in Maryland. Information was saved to drive that was capable of being accessed through the internet. [source] | West Virginia University Hospitals-East, Inc. DBA University Healthcare had a data breach in 2017, in West Virginia. The information was breached via Electronic Medical Record . [source] | |
Wyoming Medical Center had a data breach in 2016, in Wyoming. The information was breached via Email . [source] | ||