Documenting all the places
personal data goes.
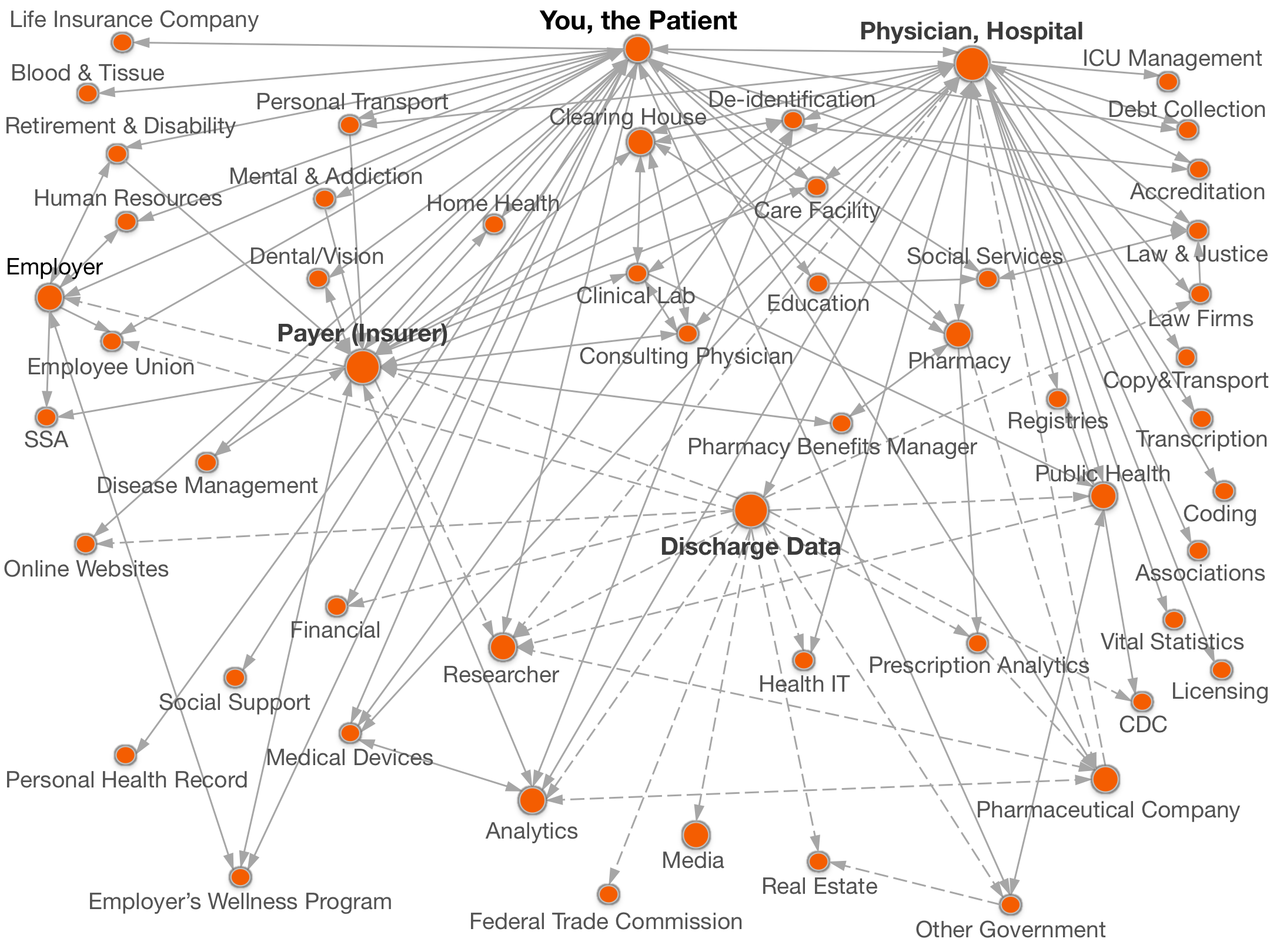
Legend:  with your name,
with your name, without your name.
without your name.
Click on a circle above for names of organizations and details of data shared.
Your healthcare provider (e.g., your physician or hospital) provides you with direct medical care, may store records with a health information technology company, and submit bills to your insurance company for payment using coding services and clearing houses.
A Physician may send your bodily samples to a clinical laboratory for assessment, information about your case to a consulting physician, and voice recordings of notes about your case to a transcription service.
Healthcare Providers have to be accredited, and accrediting organizations often require a sample of patient files for review.
Public Health Laws require healthcare providers to report details of some diseases directly to public health.
Healthcare providers are required by law to report births and deaths to vital statistics offices.
Most states have a state law that requires a copy of some information about your visit to a healthcare provider be sent to the State. This state discharge data includes your demographics, diagnoses, procedures, and a summary of payments and charges.
Hospitals may share patient data with suppliers for equipment manufacturers and intensive care unit management, or with other companies for analytics. The data are sometimes provided to de-identification companies for certification of HIPAA compliance.
Researchers may receive some patient data from Healthcare Providers.
Pharmaceutical companies may send salespeople to your provider with information about your prescriptions.
Malpractice lawyers may also demand patient information, even beyond the patient who may be the subject of the lawsuit, from healthcare providers.
See also: dental and vision and consulting physician.
Examples
Bon Secours Health System is a private $3.3 billion not-for-profit Catholic health system based in Marriottsville, Maryland. They purchase statewide personal hospital discharge data from at least 3 states: NJ, NY, PA [source]. The purchased data does not contain the person's name, but it is possible to match some people by name [source]. | A Honolulu hospital had a data breach in 2009, in Hawaii. In June 2009, a Hawaii woman was sentenced to a year in prison for illegally accessing another womans medical records and posting on MySpace that she had HIV. The State of Hawaii brought charges under a state law that criminalizes unauthorized access to a computer as a class B felony. The defendant was employed by a hospital and had access to patient medical records. [source]. | |
The Hospital Corporation of America, or HCA, is a Nashville, Tennessee-based company that has more than 160 hospitals and 11 surgery centers throughout the U.S. and England. HCA purchases statewide personal hospital discharge data from at least 3 states: CA, FL, WA. [source]. The purchased data does not contain the person's name, but it is possible to match some people by name [source]. | ABQ Health Partners had a data breach in 2012, in New Mexico. A laptop computer was discovered lost or stolen. It contained a spreadsheet of patient names, dates of birth, health plan ID numbers, and diagnosis information. [source]. | |
21St Century Oncology purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Affordable Medical and Surgical Services had a data breach in 2012, in Kansas. A woman found over 1,000 detailed abortion records in a dumpster when she went to dump her recycling near a local elementary school. The records included names, Social Security numbers, birth dates, telephone numbers, emergency family contacts, patient health histories, number of children, term of pregnancies, number of previous abortions, reasons for failing to go through with the abortion procedures, and fees paid for the procedures. Many of the records were from 2001 and 2002. The physician who ran the practice admitted to dumping the records without attempting to properly destroy them. His clinic had closed in 2005 after he lost his medical license. The county district attorney commented that he will most likely not pursue a criminal case against the former physician. (1000 records involved) [source]. | |
Academic Medical Center Information System purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Akron Childrens Hospital had a data breach in 2009, in Ohio. A 38-year-old Avon Lake, Ohio, man is set to plead guilty to federal charges after spyware he allegedly meant to install on the computer of a woman hed had a relationship with ended up infecting computers at Akron Childrens Hospital. He allegedly sent the spyware to the womans Yahoo e-mail address, hoping that it would give him a way to monitor what she was doing on her pC. But instead, she opened the spyware on a computer in the hospitals pediatric cardiac surgery department, creating a regulatory nightmare for the hospital. Between March 19 and March 28 the spyware sent more than 1,000 screen captures via e-mail. They included details of medical procedures, diagnostic notes and other confidential information relating to 62 hospital patients. He was also able to obtain e-mail and financial records of four other hospital employees as well, the plea agreement states. [source]. | |
Alameda Hospital purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Akron Childrens Hospital had a data breach in 2006, in Ohio. Overseas hackers broke into two computers at Childrens Hospital. One contains private patient data (including Social Security numbers) and the other holds billing and banking information. (235903 records involved) [source]. | |
Albany Medical Center purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Albany Medical Center had a data breach in 2007, in New York. A laptop was stolen from the Employee Health Services center. It contained software used to track information required for N95 fit testing at Albany Med. Staff names and Social Security numbers were also exposed. Anyone who had N95 fit testing at Albany Med between January 2005 and February 2007 may have had their personal information exposed. [source]. | |
All Childrens Hospital purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Albert Einstein Healthcare Network had a data breach in 2010, in Pennsylvania. The October 21 theft of a desktop computer may have exposed the protected health information of patients. [source]. | |
Altamed Health Services Corp. purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Allina Hospitals and Clinics had a data breach in 2011, in Connecticut. Twenty-eight employees from Unity Hospital and four from Mercy Hospital were fired for snooping. The employees each accessed patient medical information without authorization. Eleven teens and young adults were taken to the two hospitals on March 17 after overdosing at a party. Allegations that employees were accessing electronic medical records for no legitimate reason first surfaced in April.UPDATE(6/1/2011): It appears that a total of 32 employees, including 15 nurses, were fired in a single day for snooping. [source]. | |
Archbold Medical Center purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Allina Hospitals and Clinics had a data breach in 2006, in Minnesota. A laptop stolen from a nurses car on October 8 contains the names and SSNs of individuals in approximately 17,000 households participating in the Allina Hospitals and Clinics obstetric home-care program since June 2005. (17000 records involved) [source]. | |
Arrowhead Orthopaedics purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Amerigroup Community Care of New Mexico, Inc. had a data breach in 2011, in New Mexico. Papers were discovered stolen on or around July 15, 2011. [source]. | |
Ascent Surgical Partners purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Ankle and Foot Center of Tampa Bay, Inc. had a data breach in 2011, in Florida. The Center experienced a hacking or IT incident on or around November 10 of 2010. The protected health information of patients was exposed.UPDATE (2/3/2011): Names, Social Security numbers, dates of birth, home addresses, account numbers, and health care services and related diagnostic codes may have also been exposed. (156000 records involved) [source]. | |
Atlantic Health System purchases statewide personal hospital discharge data from at least NJ [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Apothecary of Colorado had a data breach in 2010, in Colorado. A man handling recyclables near his home found a conspicuous binder in a dumpster. It turned out that medical marijuana records had been placed there. The names, Social Security numbers, dates of birth, addresses and phone numbers of patients were in the binder. The current owners believe the records are from the previous owner or owners. Dozens of people were affected. [source]. | |
Auburn Regional Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Applegate Valley Family Medicine had a data breach in 2012, in Oregon. A stolen laptop contained patient information. The theft occurred sometime between December 1, 2011 and December 17, 2011. [source]. | |
Banner Health purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Arista OB-GYN Clinic had a data breach in 2010, in Georgia. Private medical records were dumped outside a closed office. A news team found several hundred documents that appeared to mostly be patient records with names, addresses, sonograms, copies of checks and detailed medical information. The dumpster was confiscated and searched by police. Files were also found under the dumpster. The doctor could face felony charges. [source]. | |
Baptist Health purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Arizona Biodyne had a data breach in 2005, in Arizona. A safe with computer backup tapes containing financial, personal and medical records was stolen from Arizona Biodyne. Policyholders addresses, phone numbers, dates of birth and Social Security numbers were among the personal information lost. Partial treatment histories and doctor information for some patients was also lost. (57000 records involved) [source]. | |
Bassett Healthcare purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Arizona Oncology had a data breach in 2012, in Arizona. A dishonest employee obtained and misused the personal information of patients during her employment. She pleaded guilty to one count of aggravated identity and will be sentenced in October. She faces between two and 8.75 years in prison for using the credit card information of cancer patients to make fraudulent purchases. (15 records involved) [source]. | |
Bay Care Health System purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Ashley and Gray DDS had a data breach in 2010, in Missouri. Patients were notified on that a computer or laptop was stolen. The protected health information of patients was on the computer. The location of the theft was not reported. [source]. | |
Baylor Health Care System purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Athens Regional Health Services had a data breach in 2007, in Georgia. A computer missing from a Regional First Care clinic in Watkinsville held the personal information of more than 1,400 people, according to Athens Regional Health Services. Workers first noticed on Sept. 24 that the computer was missing. The computer held Social Security numbers for 85 people, some health information for 545 people and the name, address and/or telephone numbers of 811 people. No credit card or other financial information was stored on the computer, which was a backup server for the Watkinsville clinic. (85 records involved) [source]. | |
Bellevue Hospital (Nyc) purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Atlanta Perinatal Associates had a data breach in 2011, in Georgia. A former employee hacked into APAs database, copied patient information, and deleted APAs list. It is not clear exactly how the former employee was able to access the database, but the purpose was to benefit the former employees new employer. Names, telephone numbers, and addresses of APA patients were taken. APAs competitor, SeeBaby, used the information to create a direct-mail marketing list.UPDATE(1/10/2012): The former employee was sentenced to serve 13 months in prison for hacking into the competitors computer in order to lure away patients. [source]. | |
Bert Fish Medical Center purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Atlanta Veterans Affairs Medical Center had a data breach in 2010, in Georgia. An assistant allegedly recorded two sets of patient data on to a personal laptop for research purposes. One set included three years worth of patient data and another held 18 years of medical information. The physician assistants laptop was never connected to the VA network and any data she recorded on her laptop was hand entered. The department has not disclosed the number of patients involved in the incident, what kind of personal data was copied, or whether it plans to notify the veterans whose records were downloaded. [source]. | |
Beth Israel Deaconess Medical Center purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Ault Chiropractic Center had a data breach in 2010, in Indiana. The September 15 theft of a computer may have resulted in the exposure of the protected health information of patients. [source]. | |
Bethesda Healthcare System purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Aultman Health Foundation had a data breach in 2010, in Ohio. On June 7, a laptop was stolen. Patient information from the Aultman Healthcare in Your Home program may have been exposed. This information included names, insurance identification numbers, health information, telephone numbers, addresses, dates of birth and Social Security numbers. (13,800 records involved) [source]. | |
Bjc Health System purchases statewide personal hospital discharge data from at least IL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Aurora St. Lukes Medical Center had a data breach in 2009, in Wisconsin. 6,400 people who were in-patients at St. Lukes are being warned that their name, Social Security number and other information may have landed in the hands of thieves, due to a stolen laptop computer. All of the at-risk individuals were cared for there at some point by a hospitalist, a physician other than the patients primary care doctor, who works for an independent physician group called Cogent Healthcare. The computer was stolen from a locked office in a secure physician office building that is located adjacent to the hospital; the computer belonged to an employee of Cogent Healthcare of Wisconsin. (6,400 records involved) [source]. | |
Boca Raton Community Hospital purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Avalon Center had a data breach in 2010, in New York. Sensitive medical information was dumped outside of a DMV office. The medical information came from a eating disorder clinic that had recently closed. Patient information such as medical treatment and Social Security number was exposed. It is unknown how the information ended up in the dumpster. [source]. | |
Borland-Groover Clinic purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Awklein had a data breach in 2012, in California. Sensitive health information in an unspecified format was stolen or discovered stolen on or around February 1, 2011.The incident was posted on the HHS website on June 8. (Dr. Arnold William Klein http://drarnoldklein.com/) [source]. | |
Boston Medical Center purchases statewide personal hospital discharge data from at least NJ [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Back and Joint Institute of Texas had a data breach in 2007, in Texas. Twenty boxes containing Social security numbers, photocopies of drivers license numbers, addresses, phone numbers and private medical history of chiropractic patients were found in a dumpster. [source]. | |
Bringham Womens Hospital purchases statewide personal hospital discharge data from at least NJ [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Baptist Health had a data breach in 2008, in Arkansas. Due to a breach by an unauthorized person in its information systems, there is a possibility that personal information, such as name, address, date of birth, Social security number, and reason for coming to Baptist Health were compromised. Apparently, no information in the patients medical records and no information about the patients diagnoses or prognoses was accessed. A former employee was arrested for attempting to open a credit account at a retail merchant. (1800 records involved) [source]. | |
Bronx-Lebanon Hospital Center purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Baptist Medical Center had a data breach in 2009, in Alabama. Many folders that were found in a landfill dump site were labeled Radiology Department, Baptist Medical Center. Hundreds of medical records were out in the open, all with sensitive information. Sensitive patient information that was thrown out included names, x-rays, ultrasounds, MRIs, and Social Security numbers. Files from at least five other facilities were found at the same site; however Baptist Medical Center is believed to be the source of the breach.UPDATE (8/5/08):A former employee of Baptist Hospital has been sentenced to two years and one day in federal prison for wire fraud and stealing the identities of patients, according to a Department of Justice press release. Adrienne Denise Stovall, 30, pled guilty in January to one count of wire fraud and one count of aggravated identity theft, which carries a mandatory sentence of two years. Stovall worked at Montgomerys Baptist Hospital from August 2006 to early 2007. Her position gave her access to the hospitals computer system. The system contained confidential information including patient names, dates of birth, and Social Security numbers. Stovall used the information to apply for credit lines and credit cards. http://www.justice.gov/usao/alm/press/currentpress/20100505stovall.pdf [source]. | |
Broward Health/North Broward Hosp. Dist. purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Baptist Memorial Hospital had a data breach in 2011, in Tennessee. A number of patients were notified after a breach occurred on November 27, 2010. [source]. | |
Cary Medical Center purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Baptist Physicians Lexington had a data breach in 2012, in Kentucky. A device with patient information was discovered lost or stolen on August 15. [source]. | |
Cascade Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Barnes-Jewish Hospital, The Siteman Cancer Center, Washington University had a data breach in 2011, in Montana. A laptop containing unencrypted patient information was stolen during the weekend of December 4, 2010. It contained the names, Social Security numbers, dates of birth, addresses, phone numbers, email addresses, medical records, diagnoses, lab results, insurance information and employment information. The Siteman Cancer Center is a joint venture between Washington University and Barnes-Jewish Hospital. A group of patients is suing all three groups for notifying patients eight weeks after the theft. At least one patient experienced identity theft as a result of the breach. [source]. | |
Cascade Valley Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Battleground Urgent Care/Prompt Med had a data breach in 2009, in North Carolina. Medical files were found in a dumpster. It seems a third party moving company was hired to transfer the boxes from one warehouse to another. It is unknown at this time how the files ended up in the dumpster. The information in the files contained Social Security numbers, drivers license copies, medical histories, and employers.UPDATE (5/24/10): Prompt Med agreed to pay a $50,000 fine to the state of North Carolina. (623 records involved) [source]. | |
Catholic Health Services purchases statewide personal hospital discharge data from at least FL NY ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Bay Pines VA Medical Center had a data breach in 2010, in Florida. Up to 800 police files were left in an area where the general public could easily access them. Some of the files contained Social Security numbers, patient addresses, and treatment information. [source]. | |
Cedars-Sinai Medical Center purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Baylor Health Care System Inc. had a data breach in 2008, in Texas. A laptop computer containing limited health information on 100,000 patients was stolen from an employees car. Included were 7,400 patients whose Social Security numbers were stored on the computer. (100000 records involved) [source]. | |
Central & Western Maine Regional PHO purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Baylor Health Care Systems, Baylor Heart and Vascular System, Baylor University Medical Center had a data breach in 2011, in Texas. A portable ultrasound machine was stolen from the Baylor Jack and Jane Hamilton Heart and Vascular Hospital in Dallas. The machine was stolen from a patients room sometime between December 2 and December 3. Patients who were seen at the hospital between December 26 of 2006 and the date of the theft may have had their names, dates of birth, blood pressure, height, weight and ultrasound images of their hearts on the machine. It is believed that only a fraction of the 8,000 patients who are at risk actually had their information on the machine at the time of the theft. [source]. | |
Central Maine Health Care Corporation purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Baystate Medical Center had a data breach in 2009, in Massachusetts. Several laptops were stolen from baystate Medical Centers Pediatrics department. Some of those computers had patient information on them. All of the information is password protected and the computers had no financial or Social Security information on them. [source]. | |
Central Washington Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Beacon Medical Services had a data breach in 2007, in Colorado. Detailed, personally identifiable medical records of thousands of Colorado residents were viewable on a publicly accessible Internet site for an uncertain period of time. the data included details of patients visits to emergency rooms -- what ailments they complained of, diagnoses, treatments, and medical histories, along with the patients names, occupations, addresses, phone numbers, insurance providers, and in some cases, Social Security numbers. The company is trying to determine the exact number of patients affected, but Beck says the number looks to be fewer than 5,000. [source]. | |
Childrens Hospital & Research Center- Oakland purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Beacon Medical Services had a data breach in 2007, in Colorado. Private medical and financial information including patient records from at least 10 Colorado clinics and hospitals, and one hospital in Peoria, Illinois that should have been only accessible through VPN access were inadvertently available on the Internet. (5000 records involved) [source]. | |
Childrens Hospital DC purchases statewide personal hospital discharge data from at least MD [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Bear Valley Community Hospital had a data breach in 2012, in California. An employee was fired after an investigation revealed that patient records were accessed without legitimate cause. The breach was discovered during a routine audit. (102 records involved) [source]. | |
Childrens Hospital KC purchases statewide personal hospital discharge data from at least MD [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Beebe Medical Center had a data breach in 2011, in Florida. An employee placed a briefcase with sensitive documents in her car. The briefcase was stolen from the employees car on January 1. It contained the names and Medicaid numbers of patients seen at the Beebe Medical Center in Lewes, Delaware. Only a small number of people who were seen between 2005 and 2009 were affected. Around 35 of the patients affected by the breach are deceased. (113 records involved) [source]. | |
Childrens Hospital Of Central California purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Behavioral Health Services of Pickens County had a data breach in 2011, in South Carolina. A man who purchased a used computer hard drive discovered that it had detailed clinical assessments for patients referred to Behavioral Health Services of Pickens County and a monthly monitoring list of patient referrals from the Pickens County Department of Social Services. Information about patient drug and emotional problems and pending litigations was on the hard drive. (200 records involved) [source]. | |
Childrens Hospital PA purchases statewide personal hospital discharge data from at least MD NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Bellin Health had a data breach in 2008, in Wisconsin. Patients received notification that their Social Security numbers may have been exposed. Invoices mailed from Bellin Healths unnamed bill processor had viewable Social Security numbers. (650 records involved) [source]. | |
Childrens Medical Center TX purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Bend Ophthamology had a data breach in 2011, in Oregon. Five desktop computers were stolen from the Bend office during a robbery sometime between January 26 and 27. The office is located in the Pilot Butte Medical Clinic. How much information and the kinds of information exposed were not reported. [source]. | |
Childrens Hospital Boston purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Beth Israel Deaconess Medical Center had a data breach in 2011, in Massachusetts. A vendor failed to restore computer security controls following routine maintenance. A virus was later discovered on a computer that contained names, medical record numbers, genders, dates of birth, and the date and name of radiology procedures for patients. The virus transmitted encrypted data files to an unknown location. The computer was cleaned and had its software re-installed to clear the virus. [source]. | |
Childrens Hospital La purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Beth Israel Deaconess Medical Center, Affiliated Physicians Group (APG) had a data breach in 2007, in Massachusetts. On October 20, a briefcase was stolen from the vehicle of a physician. The briefcase contained patient encounter forms with names, addresses, Social Security numbers, telephone numbers and insurance information. (53 records involved) [source]. | |
Chilton Hospital purchases statewide personal hospital discharge data from at least NJ [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Blount memorial Hospital had a data breach in 2012, in Tennessee. A password-protected laptop was stolen from an employees home on August 25. It contained two groups of patient data. Patient names, dates of birth, responsible party names, patient addresses, physician names, and billing information for 22,000 patients were on the laptop. An additional 5,000 patients had similar information exposed as well as their Social Security numbers and other non-medical information. (5000 records involved) [source]. | |
Choc Childrens Hospital purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Boca Raton Regional Hospital had a data breach in 2013, in Florida. Eight people were charged for participating in an identity theft ring. One of the members was employed as a scheduler at Boca Raton Regional Hospital. She passed along patient information in exchange for payments. One member allegedly filed 57 fraudulent tax returns with the stolen information in attempt to get $306,720 in refunds. Another member is accused of filing 75 fraudulent returns for $750,469 in refunds. [source]. | |
Cincinnati Childrens Hospital Medical Center purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Bon Secours Hampton Roads Health System, Bon Secours Mary Immaculate Hospital had a data breach in 2013, in Virginia. An April 2013 audit revealed that a patients medical record had been accessed in a way that was inconsistent with hospital policy. A further investigation revealed that two team members of the patient care team had accessed the records of multiple patients in ways that were inconsistent with their job function. The employees were fired. Patient names, dates and times of service, provider and facility names, Social Security numbers, internal hospital medical records and account numbers, dates of birth, diagnosis, medications, vital signs, and other treatment information may have been accessed. (5,000 records involved) [source]. | |
Citrus Valley Medical Center purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Bonney Lake Medical Center had a data breach in 2011, in Washington. An August 12 office burglary resulted in the loss of several computers and a main computer server with patient information. Patient names, Social Security numbers, addresses, insurance information, and medical records may have been exposed. (2,370 records involved) [source]. | |
City Of Hope National Medical Center purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Boston Childrens Hospital had a data breach in 2012, in Argentina. A Boston Childrens Hospital employee misplaced an unencrypted laptop during a conference in Buenos Aires. It contained the names, dates of birth, diagnoses, and treatment information of patients were exposed. [source]. | |
Clallam County Hospital District #1 purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Boulder Community Hospital had a data breach in 2011, in Colorado. A contract nurse is accused of accessing patient information without authorization. He faces a 90-count felony indictment. He allegedly used the Social Security numbers and other private information found in patient files to open credit cards in patients names. The nurse was hired through a staffing agency. He worked at Boulder Community between May 1, 2010 and January 7, 2011. Police later notified Boulder Community on May 11, 2011 that the former employee was suspected of stealing patient demographic information from other hospitals.UPDATE(9/27/2011): The nurse faces five counts of identity theft and 46 counts of theft of medical records in connection to this incident. The former employee worked at a staffing agency and performed work for numerous Centura Health facilities, the Platte Valley Medical Center, and Boulder Community Hospital. UPDATE (12/6/2011): The nurse was sentenced to six years probation after being charged with multiple felony counts of identity theft and theft of medical records. It was also revealed that the dishonest employee worked at St. Anthonys Hospital in Lakewood, Colorado. (74 records involved) [source]. | |
Cleveland Clinic purchases statewide personal hospital discharge data from at least MD [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Boulder Community Hospital, Family Medical Associates had a data breach in 2010, in Colorado. Anonymous letters were sent to at least 14 patients of the Family Medical Associates clinic in Lafayette. The letters contained Social Security numbers, medical records, dates of birth and names. The sender claimed that the clinic was improperly disposing patient personal information. (14 records involved) [source]. | |
College Hospital Cerritos purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Brandywyne Healthcare Center had a data breach in 2011, in Florida. A nurse was arrested and charged with grand larceny, ID theft, and scheming to defraud several elderly patients. The nurse collected patient information and texted it to a co-conspirator. The co-conspirator then used the information to obtain fraudulent tax returns in the names of the victims. Over 30 of the 83 victim records found at the co-conspirators home were from the Brandywyne Health Center. (83 records involved) [source]. | |
Columbia Valley Community Health purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Brentwood Primary Care Clinic had a data breach in 2013, in Florida. A dishonest intern was caught using a cell phone to illegally photograph patient Social Security numbers and names. The photos were then sent to another person; presumably for fraudulent activity. The office intern was charged with fraudulent use of personal identification information. It is unclear when the breach was discovered since the photos were taken between May 7 and June 19. (261 records involved) [source]. | |
Community Hospital Of The Monterey Peninsula purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Brigham and Womens Hospital had a data breach in 2012, in Massachusetts. The October 16 theft of a desktop computer may have resulted in the exposure of patient information.UPDATE(12/28/2012): The computer was stolen from the Brigham and Womens Hospital office. Medical record numbers, age, medications, laboratory values and other clinical information may have been on the computer. Up to 615 people may have been affected by the theft. (615 records involved) [source]. | |
Community Oriented Correctional Health Services,In purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Brooke Army Medical Center had a data breach in 2010, in Texas. An Army three-ring binder that may have included detailed information on soldiers and families being treated at Brooke Army Medical Center was stolen on Oct. 16 from a car belonging to a case manager. Names, phone numbers and health information of 1,272 patients being treated at hospitals may have been breached by the car break-in. (1,272 records involved) [source]. | |
Community Regional Medical Center purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Broward County School Board, Private Medical Practices had a data breach in 2011, in Florida. Two former employees from different private medical practice offices were charged with providing confidential patient information to other members of an identity theft and fraud ring. Both of these people participated in the identity theft and fraud ring from early 2009 until February 2, 2011. A former employee who worked for the Broward County School board passed along information from a teacher certification database, which included names, Social Security numbers and dates of birth. The information was used to fraudulently add people as authorized users to the victims credit card and bank accounts. The bank accounts of victims were depleted and one person discovered fraudulent credit card charges of $128,000. In addition to the three former employees, eight other people and the ringleader were also indicted on March 15, 2011.UPDATE(9/30/2011): The former Broward School District employee was sentenced to just over five years in federal prison for accessing and selling teacher personal information to identity theives. At least 42 people in Florida had their information stolen; the fraudulent credit card charges that resulted totalled $408,000. The former employee admitted to selling five to 10 Social Security numbers and dates of birth at a time for $100. [source]. | |
Community Regional Medical Center-Fresno purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | California Therapy Solutions had a data breach in 2011, in California. The November 15 theft of a device resulted in the exposure of protected patient health information. [source]. | |
Connally Memorial Medical Center purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Cancer Care Group had a data breach in 2012, in Indiana. An employees computer bag was stolen on July 19. The bag contained a computer server back-up that had patient and employee names, Social Security numbers, dates of birth, insurance information, medical record numbers, limited clinical information, and addresses. (55000 records involved) [source]. | |
Cook Childrens Health Care System purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Cancer Care Northwest had a data breach in 2011, in Washington. A January mistake in mailing led to brochures being mailed to the wrong current and former patients. Everyone who was meant to receive a brochure did; but patients were able to see the name and address of another patient. The brochure and letter provided information on a breast education and support program. [source]. | |
Coral View Surgery Center, Llc purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Capron Rescue Squad District had a data breach in 2011, in Illinois. Unauthorized access or disclosure of patient information resulted after a breach involving a laptop. The breach was discovered on or around February 5, 2011. [source]. | |
Coulee Community Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Cardiology Consultant Inc. had a data breach in 2010, in Florida. Cardiology Consultants Inc. today reported that a laptop used to process ultrasound images was stolen from one of its Pensacola offices. The computer did not contain patient financial information or Social Security numbers. The stolen computer did contain the first and last names, dates of birth, medical record numbers, exam dates and in some cases, the reason for the ultrasound. [source]. | |
Crozer-Keystone purchases statewide personal hospital discharge data from at least MD [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Carle Clinic Association had a data breach in 2010, in Illinois. An impostor posing as a representative of the organizations recycling service removed several barrels of purged x-ray films and film jackets. The health information included approximately 1,300 patient names, dates of birth, gender, clinic medical numbers, internal accession numbers, site locations, physician or provider names, and internal provider numbers. [source]. | |
Dallas Regional Medical Center purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Carolinas HealthCare System had a data breach in 2012, in North Carolina. An unauthorized electronic intrusion may have affected up to 6,300 patients from Carolinas Medical Center-Randolph. The intruder accessed a providers email account and could have obtained patient names, dates and times of service, dates of birth, diagnosis and prognosis information, medications, results, and referrals. The Social Security numbers of five patients who had their Social Security numbers sent through or received by the email account may have also been obtained.The issue was discovered on October 8 and the intruder is believed to have accessed emails from the account between March 11, 2012 and October 8, 2012. (5 records involved) [source]. | |
Dartmouth-Hitchcock Medical Center purchases statewide personal hospital discharge data from at least NY ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Carrell Clinic had a data breach in 2009, in Texas. An Arlington security guard was arrested on federal charges for hacking into hospitals computer system. The defendant allegedly posted video of himself compromising a hospitals computer system on YouTube. The system and computers contained confidential patient information.UPDATE (3/18/2011): Phiprivacy.net reports that the former security guard was sentenced to nine years in prison for installing malware. Jesse William McGraw was employed by the security company United Protection Service while working as a security guard for Carrell Clinic. He was also the leader of a hacker gang. [source]. | |
Dayton General Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | CBIZ Medical Management Professionals had a data breach in 2009, in Tennessee. The office of CBIZ Medical was broken into on Feb. 23. Among the items stolen was a computer belonging to the hospital with stored radiology reports related to some patients. patients between December 2007 and Feb. 23, 2009, may have had records saved on the stolen computer. [source]. | |
Deaconess Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | CCS Medical had a data breach in 2012, in Georgia. An employee reported that another employee appeared to have been misusing patient information. The dishonest employee may have accessed, recorded, and disclosed Social Security numbers and other personal information for the purpose of obtaining fraudulent tax returns. The employee was reported on September 20 and the possibility that the employee had engaged in dishonest behavior was confirmed on October 17. Patient information that was maintained by CCS Medical between May 1, and September 21, 2012 may have been accessed. Notifications were sent to patients on December 7, 2012. At least 23 New Hampshire residents may have been affected. The total number of affected patients nationwide was not reported. (23 records involved) [source]. | |
Doctors Hospital At Renaissance purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Cedars-Sinai Medical Center had a data breach in 2008, in California. A former billing department employee is in custody on $895,000 bail for allegedly stealing the personal information of 1,000 hospital patients and using it to bilk insurance companies. (1000 records involved) [source]. | |
Driscoll Childrens Hospital purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Central Brooklyn Medical Group PC, Preferred Health Partners had a data breach in 2011, in New York. On August 3, 2010 paper records were discovered stolen. It is not clear who the paper records belonged to, where they were stolen from, and what type of information the records contained. [source]. | |
East Adams Rural Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Central Florida Regional Hospital had a data breach in 2008, in Florida. The medical records of Central florida Regional Hospital patients were sold last month at a Salt lake City surplus store for about $20. The records were sold to a local school teacher looking for scrap paper for her fourth-grade class. The records contained detailed medical histories, phone numbers, addresses, Social Security numbers and insurance information. They were lost en route to a Medicare auditor in Las Vegas, NV. (28 records involved) [source]. | |
East Texas Medical Center purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Central New England HealthAlliance had a data breach in 2008, in Massachusetts. Personal data could be at risk of exposure after a home health nurse reported that her handheld computer was missing. The unencrypted data include names, Social Security numbers, and health insurance records. (384 records involved) [source]. | |
Eastern Maine Health Systems purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Centro de Ortodancia had a data breach in 2011, in Puerto Rico. Paper records were found to have been exposed to unauthorized parties on or around May 6, 2010. [source]. | |
Eastside Midwives purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Charleston Area Medical Center (CAMC) had a data breach in 2011, in West Virginia. Someone discovered that they could find information about a relatives name, address, patient ID, date of birth, Social Security number and other sensitive information through an online search that brought up WVChamps.com. WVChamps.com is a CAMC website relating to respiratory and pulmonary rehabilitation for seniors. The information was accidentally posted in a report on September 1, 2010 and appears to have been accessed a total of 94 times. The error was discovered on February 8 of 2011. The breach occurred within the CAMC subsidiary CAMC Health Education Research Institute.UPDATE(5/5/2011): Five patients who were affected by the breach filed a lawsuit seeking class action status for all affected patients. The lawsuit alleges four counts against the hospital: breach of the duty of confidentiality, invasion of privacy by intrusion upon the seclusion of the plaintiffs, invasion of privacy by unreasonable publicity into the plaintiffs private life, and negligence. (3655 records involved) [source]. | |
Enumclaw Community Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Charlie Norwood VA Medical Center had a data breach in 2012, in Georgia. The March 30 theft of a physicians laptop resulted in the exposure of personal information. The physician had violated VA policy by placing the personal information on his own laptop. Veterans may have had the last four digits of their Social Security number, discharge date, and medical provider name exposed. [source]. | |
Evergreen Healthcare purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Chattanooga Family Practice Associates had a data breach in 2010, in Tennessee. A missing portable device had the names, dates of birth and purposes of visits for a limited number of patients. [source]. | |
Evergreen Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Chesapeake Wound Care Center had a data breach in 2012, in Maryland. A podiatrist licensed in the state of Maryland operated a podiatry practice called Chesapeake Wound Care Center from his home. Between April 1, 2002 and October 11, 2004, he submitted 80 fraudulent claims to Medicare for podiatry services that had not been performed at nursing facilities. The podiatrist signed a Settlement Agreement with the government on October 30, 2007 after being caught, but then fraudulently billed Medicare advantage plans between October 31, 2007 and July 20, 2010. The podiatrist admitted to submitting false bills for podiatry care by misusing the names and personal information of about 200 nursing home patients. He was subsequently charged with health care fraud and aggravated identity theft. He was sentenced to 54 months in prison, three years of supervised release, and ordered to pay $1,122,992.08 in restitution for the fraudulent billing of Medicare. (200 records involved) [source]. | |
Fairchild Medical Center purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Childrens Health Council had a data breach in 2005, in California. A tape containing sensitive information was stolen from a Childrens Health Council office. The tape contained names, Social Security numbers, and detailed medical information for around 6,000 current and former clients. Payroll information for 700 current and former employees was also on the tape. The agency alerted those who may be at risk of identity theft. (6,700 records involved) [source]. | |
Faith Health Care purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Childrens Hospital and Research Center at Oakland had a data breach in 2010, in California. Approximately 1,000 patients received information about themselves and other patients in the mail. According to the Hospitals website equipment designed to generate, fold and stuff documents for mailing was programmed to fold and stuff two pages rather than one. This programming error caused guarantor billing statements prepared on May 25 and May 26 to be collated and mailed incorrectly. [source]. | |
Ferry County Public Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Childrens Hospital of Orange County had a data breach in 2010, in California. The Hospital is checking its database for accuracy after discovering that patient files have been faxed to the wrong location at least twice. Patient records were faxed to an auto shop in 2009, and the wrong doctor on a separate occasion. [source]. | |
Floria Hospital purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Childrens Hospital of Philadelphia had a data breach in 2009, in Pennsylvania. A laptop computer containing Social Security Numbers and other personal information was stolen from a car outside an employees home on Oct. 20. The billing information on the computer was password-protected, but an analysis found it was possible to decode the security controls on the laptop and gain access to the personal information. (942 records involved) [source]. | |
Florida Hospital purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Christus Health Care had a data breach in 2008, in Texas. Two computer back-up tapes were stolen. Someone broke into a car in a Houston parking lot and took the tapes. The information on the tapes included patient names, Social security numbers, demographic information, and in some cases, diagnosis codes. [source]. | |
Florida Hospital - Heartland Division purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | CHRISTUS St. John Hospital had a data breach in 2012, in Texas. An unencrypted flash drive was discovered lost or stolen on September 25. It contained patient names, Social Security numbers, dates of birth, health insurance information, diagnoses, and progress notes. The information came from patients who participated in the St. John Sports Medicine Program and were treated between January 1, 2011 and July 31, 2012. [source]. | |
Florida Hospital Memorial Medical Center purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Christus St. Josephs Hospital had a data breach in 2005, in Texas. Two computers used for converting paper medical records into digital files were stolen. One of the computers contained Social Security numbers and medical records for hundreds of patients. Letters were sent to about 16,000 patients. (16,000 records involved) [source]. | |
Florida Hospital Waterman, Accounting Dept. purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Cincinnati Childrens Hospital Medical Center had a data breach in 2010, in Ohio. A laptop containing the names, medical record numbers, and medical services provided of patients was stolen from an employees car while it was parked at his or her home. As a precaution, no additional laptops will be allowed outside the hospital unless they are encrypted. [source]. | |
Forks Community Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Cleveland Clinic had a data breach in 2006, in Florida. A clinic employee stole personal information from electronic files and sold it to her cousin, owner of Advanced Medical Claims, who used it to file fraudulent Medicare claims totaling more than $2.8 million. Information included names, sSNs, birthdates, addresses and other details. Both individuals were indicted. (1100 records involved) [source]. | |
Franklin Memorial Hospital purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Coliseum Hospital had a data breach in 2010, in Georgia. A former employee was able to enter a secured area and log onto a hospital computer while attending a social event. The former employees access code had been left active and patient records were viewed during the incident. [source]. | |
Garfield County Hospital District purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Colorado Mental Health Institute Fort Logan had a data breach in 2006, in Colorado. A briefcase with paper files was taken from an employees car while it was at a park on April 21. The briefcase contained paper files with the information of 40 employees and 247 patients. Only 29 employees and 40 patients had their Social Security numbers exposed. Other information included names, addresses, gender and birth dates. Those affected were notified in early June. (69 records involved) [source]. | |
Good Samaritan purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Colorado Springs Hospital - Memorial Health System had a data breach in 2011, in Colorado. A nurse from the occupational health clinic accessed the records of 2,500 Memorial Hospital patients without cause. The nurse had access to patient records through Physician Link, but was not a Memorial employee, and had no medical or work-related reason for accessing the records. She was fired and claims to have used the database to look up contact information for family and friends, as well as for other reasons. The nurse also feels that she was singled out and claims that many other employees in the medical community use databases in this way. [source]. | |
Good Shepherd Medical Center purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Columbia University Medical Center had a data breach in 2010, in New York. Patients treated in the Intensive Care Unit at New York-Presbyterian Hospital and Columbia University Medical Center may have had their information accessed on the Internet during July. The personal information may have included name, age, surgical status, medications and lab results. It appears that a hospital employees computer files were Internet accessible. (10 records involved) [source]. | |
Goodall Hospital purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Columbia-St. Marys Ozaukee Hospital had a data breach in 2011, in Wisconsin. A janitor sold patient records to gang members. The janitor was able to use a master key to access boxes of sensitive information that were due to be shredded. Some of the locks to the restricted boxes were also broken. The scheme went on for up to eight months and investigators were able to seize nearly 30 patient records. [source]. | |
Grays Harbor Community Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Community Health Network, Community Health Medcheck had a data breach in 2013, in Indiana. A dishonest employee of Community Health Medcheckaccessed the medical records of up to 180 people between mid-March and mid-April. Social Security numbers, dates of birth, credit card numbers, and other information may have been exposed. (180 records involved) [source]. | |
Gritman Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Compass Health had a data breach in 2006, in Washington. Compass Health notified some of its clients that a laptop containing personal information, including SSNs, was stolen June 28. The agency serves people who suffer from mental illness. [source]. | |
Group Health Cooperative purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Concentra Medical Center, Concentra Health had a data breach in 2012, in Missouri. An office burglary resulted in the theft of an unencrypted laptop. It contained the names, Social Security numbers, and pre-employment work-fitness tests of Concentra patients from the Springfield area. The Concentra Springfield Medical Center will not encrypt all equipment as a result of this breach. (870 records involved) [source]. | |
Hackensak University Medical Center purchases statewide personal hospital discharge data from at least NJ NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Concord Hospital had a data breach in 2011, in New Hampshire. An audit of Concords system revealed that an employee accessed the records of 40 patients without proper authorization. It appears that the employee was checking the files of friends and family. Concord discovered the breach on May 11. (13 records involved) [source]. | |
Halifax Health - Finance Dept. purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Conway Regional Medical Center had a data breach in 2011, in Arizona. CDs with personal information were discovered lost on or around August 24, 2011. Other items with personal information may have been lost as well. [source]. | |
Halifax Medical Center purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Cook County Health and Hospital Systems had a data breach in 2010, in Illinois. A desktop computer was found to be missing on or around November 1. It contained the medical record identification numbers, names, dates of birth, clinic names, physician names, and lab results of some patients. [source]. | |
Harbor-University Of Californiala Pediatric Cardiology purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Cook County Health and Hospital Systems (CCHHS) had a data breach in 2010, in Illinois. On June 1, a laptop with patient information was stolen from a locked office in an administration building. The password protected-computer included names, dates of birth and Social Security numbers. (7,000 records involved) [source]. | |
Harborview Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Cumberland County Emergency Medical Service had a data breach in 2006, in North Carolina. Portable computer containing personal information of more than 24,000 people was stolen from ambulance of Cumberland Co. Emergency Medical Services on June 8th. It contained information on people treated by the EMS, including names, addresses, and birthdates, plus SSNs of 84% of those listed. (24,350 records involved) [source]. | |
Harris County Hospital Dist purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Cumberland Gastroenterology P.S.C. had a data breach in 2010, in Kentucky. Paper records were stolen on September 18. The records contained protected health information. [source]. | |
Harrison Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Dayton VA Medical Center had a data breach in 2012, in Ohio. Documents with Social Security numbers, dates of birth, and other sensitive information were found in the home of a deceased VA employee in May. The records were found in a box in the attic of the home. It is unclear why the employee took the information home. (16 records involved) [source]. | |
Hca Far West Division purchases statewide personal hospital discharge data from at least CA FL WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Deaconess Hospital had a data breach in 2006, in Indiana. A computer missing from the hospital holds personal information, including SSNs, of 128 respiratory therapy patients. (128 records involved) [source]. | |
Health Trends purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Dean Clinic and St. Marys Hospital had a data breach in 2010, in Wisconsin. A laptop was stolen during a home invasion on or around November 8. Patient names, dates of birth, medical record numbers, dates and types of procedures, diagnoses, and some pathology data were on the laptop. [source]. | |
Helen Ellis Memorial Hospital purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | DeKalb Medical - Hillandale had a data breach in 2011, in Georgia. Patient information was stolen from the Hillandale facility and used to file fraudulent tax returns with the Internal Revenue Service. Patients who visited DeKalbs Hillandale facility between July and October 2010 may have had their information exposed. It appears that affected individuals between the ages of 17 and 20 were the group affected by the filing of fraudulent tax returns. The United States Secret Service alerted DeKalb and it is believed that the breach was just one of many similar breaches in Georgia and Alabama. DeKalb did not reveal how the information was taken. (7,500 records involved) [source]. | |
Henry Mayo Memorial Hospital purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Delta Dental had a data breach in 2012, in California. The unauthorized disclosure of paper records sometime around December 22, 2011 may have resulted in the exposure of protected health information. [source]. | |
Hernando Endoscopy & Surgery Center purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | DENT Neurologic Institute of Amherst had a data breach in 2013, in New York. An administrative error led to the personal information of 10,200 patients being emailed to 200 patients. Names, addresses, date of last appointment, visit type, primary care physician, referring physician, email addresses, and whether or not the patient was actively receiving treatment were in an Excel attachment of an email that was sent to unspecified parties. The recipients were called and instructed to delete the email. [source]. | |
Highline Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | DENT Neurological Institute had a data breach in 2013, in New York. DENT Neurological Institute accidentally emailed the private information of more than 10,000 patients. No sensitive medical files or Social Security numbers were involved. [source]. | |
Hoag Memorial Hospital Presbyterian purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Dentistry at the Crest had a data breach in 2011, in Colorado. Hundreds of sensitive dental patient records were found by a street sweeper. They were scattered near a dumpster behind a shopping center. The records appear to be from a dental practice in Lone Tree, a 20 mile journey. The party responsible for the breach is unknown. Billing records with patient names, Social Security numbers, dates of birth, and addresses were exposed. [source]. | |
Holy Family Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Department of Veterans Affairs had a data breach in 2011, in District Of Columbia. The inspector general at the VA found that IT contractors had accessed the VAs electronic health record system without appropriate security clearances. An tipster had left a message about the situation on a departmental hotline in the summer of 2010. Contractor personnel were found to be improperly sharing user accounts when accessing VA networks and the Veterans Health Information System and Technology Architecture systems. Employees of the contracting company were unaware of proper IT security protocol. [source]. | |
Homestead Hospital purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Department of Veterans Affairs had a data breach in 2011, in North Carolina. A dishonest VA worker used his tax return preparation business to submit fraudulent tax returns. VA patient personal information such as names, Social Security numbers and birth dates were used to create fake dependents on peoples tax returns. The VA worker then collected fees from customers in exchange for fraudulently increasing the dollar amount of their tax returns. He was convicted in February and sentenced to 11 years in federal prison. The employee handled information from VA patients in North Carolina and Virginia. [source]. | |
Hospital For Joint Diseases purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | DePaul Medical Center, Radiation Therapy Department had a data breach in 2006, in Virginia. Two computers were stolen, one on August 28 and the other Sept. 11. Personal data included names, date of birth, treatment information, and some SSNs. (100 records involved) [source]. | |
Inland Counties Regional Perinatal Prgm purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Dermatology Clinic had a data breach in 2011, in North Carolina. A log book with patient appointment information was discovered missing. Patients had their names, last four digits of Social Security number, telephone numbers and names of procedures scheduled exposed. Two searches did not lead to the recovery of the log book; there is a possibility that a patient took the book. [source]. | |
Inland Northwest Health Services purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Desert AIDS Project (D.A.P.) had a data breach in 2012, in California. An April 12, 2012 office burglary resulted in the theft of a laptop with sensitive information. The computer assigned to the receptionist was stolen and contained a spreadsheet with client name, client status (active, discharged, etc.), internal client identification number, date of birth, and assigned staff person. However the document was not labeled as a D.A.P. document. If someone saw the spreadsheet by itself they would not know it was linked to D.A.P.UPDATE(05/30/2013): Approximately 4,400 patients were affected. [source]. | |
Inland Northwest Health Services & St Lukes Rehab purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Diabetes Direct Inc had a data breach in 2010, in Florida. A former employee is accused of stealing patient information to commit identity theft. The former employee also had multiple drivers licenses and was able to open utility, bank and credit accounts. [source]. | |
Inova Health purchases statewide personal hospital discharge data from at least MD [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Doshi Diagnostic Center had a data breach in 2012, in New York. Sensitive documents were placed in public trash bags. The bags were opened and the documents were found scattered across a sidewalk. Confidential patient records which included names, Social Security numbers, unemployment compensation records, copies of benefits cards, and other patient personal information were exposed. Patients dating back to 2006 were affected. [source]. | |
Intuitive Surgical Inc purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Dr, Charles Kay of Orchard Family Practice had a data breach in 2006, in Colorado. Sheriffs deputies evicting dr. Charles Kay put files from his office in a nearby parking lot. in a news report, Dr. Kay said he had removed the patient files but not the business files. (100 records involved) [source]. | |
Jackson Health System purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Dr. Baceskis office, internal medicine had a data breach in 2007, in Pennsylvania. A hard drive was stolen containing personal information on hundreds of patients. [source]. | |
John C. Fremont purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | DRC Physical Therapy Plus had a data breach in 2010, in New York. Officials have seized hundreds, perhaps thousands, of files containing Social Security numbers and other private patient information found dumped outside the shuttered office of DRC Physical Therapy Plus. The manila folders, dating back to at least 1998, include information sheets showing the names, addresses and birth dates of patients and, in some cases, Social Security numbers. Deputies impounded a dump truck loaded with patient files and about a dozen or so boxes stacked inside the bucket of a front-loader. [source]. | |
John Muir Health purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Duke University Health System (DUHS) had a data breach in 2012, in North Carolina. ON or around January 25, DUHS received notice that its billing subsidiary staff attached copies of outstanding billing statement(s) for services provided by DUHS facilities and/or DUHS-affiliated physicians to support proofs of claim filed in Chapter 13 bankruptcy actions by patients of DUHS. Patient and patient dependent names, addresses, DUHS medical record number, health insurance carriers, and clinical information were exposed. Some patients and patient dependents had their Social Security numbers and dates of birth exposed as well. Notification letters were mailed on March 23 and again on May 18. [source]. | |
Kadlec Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Duke University Medical Center had a data breach in 2005, in North Carolina. A hacker broke into the computer system, stealing thousands of passwords and fragments of Social Security numbers. Fourteen thousand affected people were notified, including 10,000 employees of Duke University Medical Center. [source]. | |
Kaiser Permanante purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Dunes Family Health Care P.C. had a data breach in 2011, in California. The March 11 theft of an external hard drive used for backing up the Clinics electronic files may have exposed patient information. The hard drive was stored in a locked, fire-protected building with very limited access. Many of the files contained patient Social Security numbers in addition to names, dates of birth, addresses and other clinical information. There was a delay in notification due to the fact that there were duplicate files and patient contact information had to be updated. The Clinic has begun to encrypt records and raised the physical security of the files since the incident. [source]. | |
Kaweah Delta Healthcare District purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | E-Pro Tax Service, Emory Healthcare had a data breach in 2011, in Illinois. An investigation into a few stolen Social Security checks that had been fraudulently deposited into Duluth banks uncovered three separate identity theft rings. At least six conspirators managed to defraud 5,779 people. A former real estate broker created a tax service company in order to access credit reports from a third-party credit reporting agency. Names, dates of birth and Social Security numbers were exposed. The former real estate agent then made about $2.5 million by stealing Social Security checks, filing 393 fraudulent tax returns and passing counterfeit checks. After police linked her to the stolen Social Security checks, they searched her home and found boxes of financial documents which included old mortgage applications, tax forms and HUD documents. Investigators have not charged any other conspirators and do notbelieve that the woman was the head of the operations.UPDATE (10/24/2011): More organizations were linked to the breach when investigators searched the dishonest employees home. The dishonest employee had a connection with a someone who used to work as a clerk at the hospital. More than 3,000 patient bills containing names, Social Security numbers, dates of birth, and other confidential information were printed by the inside contact. The hospital bills of at least 32 Emory orthopedic clinic patients were stolen and used to file fraudulent tax returns. Nine patients became identity theft victims. Emory notified 7,300 employees of the breach and had fired the dishonest clerk in July. (13,079 records involved) [source]. | |
Kennewick General Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Eastmoreland Surgical Clinic and Vein Center had a data breach in 2010, in Oregon. Desktop computers were stolen from the office around July 5. The computers had patient names, addresses, Social Security numbers, phone numbers, reason for visit and insurance carrier information. (4,328 records involved) [source]. | |
Kitsap Couty Health District purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Ecco Health, LLC, Colon & Digestive Health Specialists had a data breach in 2012, in Arizona. A vendor working with patient data for digital conversion from Colon & Digestive lost a flash drive on or around July 16. It contained patient names, Social Security numbers, dates of birth, addresses, telephone numbers, account numbers, diagnoses, and other protected health information. [source]. | |
Kittitas Valley Community Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Eisenhower Medical Center (EMC) had a data breach in 2011, in California. The March 11 theft of a desktop resulted in the exposure of patient names, dates of birth, ages, Eisenhower medical record numbers and the last four digits of patient Social Security numbers. A television was also stolen during the burglary. Patient information from as far back as the 1980s may have been exposed. (514,330 records involved) [source]. | |
Klickitat Valley Health Service purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | El Centro Regional Medical Center had a data breach in 2012, in California. El Centro Regional Medical Center is claiming that they were defrauded by an unnamed company. The company was responsible for digitizing El Centro Regionals x-rays, but never returned the digitized version. The process should have been completed by the end of July. The original x-rays were most likely taken and destroyed to extract silver.UPDATE(05/18/2013): The information on the records was as recent as February 2011. El Centro Regional Medical Center learned of the issue on March 22, 2013. Patients were notified on May 13. (189,489 records involved) [source]. | |
Lake Chelan Community Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Emory Healthcare had a data breach in 2011, in Georgia. Seventy-seven patients had their Social Security numbers stolen and used for fraudulent tax returns. Patient names and possibly addresses, dates of birth, clinic numbers, limited health information and health insurance companies were exposed. Patients who were seen in orthopaedics between May of 2008 and January of 2009 for something other than physical therapy were affected. (2400 records involved) [source]. | |
Laser & Surgery Center Of The Palm Beaches purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Emory Healthcare, Emory University Hospital had a data breach in 2012, in Georgia. Emory Healthcare revealed that 10 backup discs that contained patient information are missing from a storage location at Emory University Hospital. The discs were determined to have been removed sometime between February 7, 2012, and February 20, 2012. The patient information was related to surgery and included names, Social Security numbers, diagnoses, dates of surgery, procedure codes or the name of the surgical procedures, surgeon names, anesthesiologist names, device implant information, and other protected health information. Patients treated at Emory University Hospital, Emory University Hospital Midtown (formerly known as Emory Crawford Long Hospital) and Emory Clinic Ambulatory Surgery Center between September of 1990 and April of 2007 were affected.UPDATE(6/09/2012): A suit seeking class action status was filed on June 4. The suit seeks unspecified damages over the loss of 10 computer disks containing the personal and health information of between 250,000 and 315,000 patients treated between 1999 and 2007. (228,000 records involved) [source]. | |
Lawrence Hospital Center purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Ephrata Community Hospital had a data breach in 2013, in Pennsylvania. An employee inappropriately accessed patient information. The incident or incidents were discovered on April 16. Patient clinical and other medical information may have been exposed. No Social Security numbers were exposed. [source]. | |
Legacy Health System purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Erlanger Health System, Erlanger Hospital had a data breach in 2013, in Tennessee. Erlanger Health System sent notes to 87 families and apologized for an incident that left the patient records of children exposed. The records contained names, Social Security numbers, phone numbers, and dianosis information. Erlanger has not been made aware of the records being used in an unauthorized manner. (87 records involved) [source]. | |
Lehigh Valley Health Network purchases statewide personal hospital discharge data from at least NJ [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Excela Health had a data breach in 2011, in Pennsylvania. A computer was stolen from the radiology department of the Jeannette campus of Excela. It contained patient names, dates of birth and types of exam performed. [source]. | |
Leiden University Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Fairview and North Memorial Hospitals, Accretive had a data breach in 2011, in Minnesota. The July 25 theft of a laptop resulted in the exposure of patient information. It was stolen from a rental car parked in the parking lot of a Minneapolis restaurant. The laptop was in the possession of an employee of the contractor Accretive. It contained the names, addresses, dates of birth, medical information, and Social Security numbers of patients. A total of 14,000 Fairview patients were affected. Approximately 2,800 North Memorial patients were affected, but did not have their Social Security numbers exposed.UPDATE(1/20/2012): A lawsuit was filed against Accretive Health, Inc. as a result of the breach.Approximately 23,500 patients in Minnesota were affected by the breach.The Minnesota Attorney General claims that Accretive failed to protect patient health care records and failed to disclose its extensive involvement in patient health care. According to the Minnesota Attorney General, Accretive gained access to sensitive patient data through contracts with the two hospitals and numerically scored patients risk of hospitalization and medical complexity, graded their frailty, compiled per-patient profit and loss reports, and identified patients deemed to be outliers. The physical and mental health information included a checklist of 22 different chronic medical conditions that patients did or did not have. This was without the knowledge or consent of patients and the Attorney General argues that patients had the right to know how their information was being used and to have it kept confidential.Accretive tells investors that its contracts with hospitals include risk scoring patients, reducing avoidable hospital admissions, identifying the sickest and most impact-able patients for proactive management, and identifying real-time interventions with significant revenue or cost impact. The lawsuit alleges that Accretive violated state and federal health privacy laws, state debt collection laws, and state consumer protection laws. It seeks an order requiring Accretive to fully disclose to patients: 1) what information it has about Minnesota patients; 2) what information it has lost about Minnesota patients; 3) where and to whom it has sent information about Minnesota patients; and 4) the purposes for which it amasses and uses information about Minnesota patients. In addition, the lawsuit asks Accretive to disclose whether it has sent health data about Minnesota patients to an offshore site in new Delhi, India and requests that restrictions be applied to how Accretive treats and uses patient data.The press release from the Office of Minnesota Attorney General Lori Swanson can be found here.UPDATE(08/24/2012): A settlement agreement with Accretive Health was announced at the end of July. The settlement requires Accretive to stop doing business in Minnesota for two years and to pay approximately $2.5 million to the State of Minnesota, a portion of which will be used to compensate patients. (14000 records involved) [source]. | |
Lincoln Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Fairview Health Services had a data breach in 2011, in Minnesota. About 1,200 patient records were stored in a box and marked for shipping to a new office location. The box never arrived and was reported missing on February 21, 2011. Patient billing records with names, dates of birth and medical information may have been exposed. The records are used to process insurance claims. Any patient admitted to Fairview Southdale Hospital in Edina between April of 2010 and February of 2011 may have had their information exposed. [source]. | |
Loma Linda University Medical Center purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Family Care Center had a data breach in 2010, in Washington. A thief or thieves entered the physical therapy office on June 12th. Cash, other items, and a laptop containing encrypted patient information such as names and account numbers were stolen. It appears that a door was left unlocked. [source]. | |
Long Island Health Network purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Family Chiropractic Center had a data breach in 2012, in Indiana. Between 400 and 450 medical records were stolen from a chiropractic clinic during a January 2 burglary. Files for patients with last names ending in DOD through DRI; ending in ELL through GAT; and ending in GIF through HAL and who had been to the clinic since January 1, 2008 were taken. [source]. | |
Long Island Jewish Medical Center purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Family Health Center had a data breach in 2010, in Virginia. Boxes containing patient information ended up in a dump. The easily accessible information included health history, surgeries performed, test results, pictures, insurance cards, bank account information and addresses. The boxes were traced back to Family Health Center on Town Center Parkway. [source]. | |
Los Angeles Brain & Spine Institute purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Family Health Center of Clark County had a data breach in 2006, in Indiana. Two computers stolen from an Indiana state health department contractor, the Family Health Center of Clark Count, contained the names, addresses, birth dates, SSNs and medical and billing information for more than 7,500 women. The data were collected as part of the states Breast and Cervical Cancer Program. (7700 records involved) [source]. | |
Lourdes Health Network purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Fayetteville Veterans Affairs Medical Center had a data breach in 2013, in North Carolina. Optical shop consultation reports were placed in a publicly accessible recycling bin over a period of three months rather than properly disposed. The documents contained names, Social Security numbers, addresses, dates of birth, and prescriptions. The issue was discovered on April 17 and most likely started in January of 2013. (1,093 records involved) [source]. | |
Lucile Packard Childrens Hospital purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Fletcher Allen Health Care had a data breach in 2011, in Vermont. A physician pleaded guilty to unlawfully obtaining the private medical information of another person. The former employee accessed the records of several women who were not his patients. In one case, he was in a sexual relationship with a woman and accessed her information to check if she carried sexually transmitted diseases. The crime occurred in 2008. The physician is scheduled to be sentenced on March 26, 2012 and faces a maximum sentence of one year in prison and a $50,000 fine. [source]. | |
Maine Coast Memorial Hospital purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Flex Physical Therapy had a data breach in 2012, in Washington. Three computers were stolen on December 30, 2011. One of the computers contained the protected health information of patients. [source]. | |
Maine Medical Center purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Florida Hospital had a data breach in 2011, in Florida. Patients who visited emergency departments of three Central Florida county Florida Hospitals between January 1, 2010 and August 15, 2011 may have had their information improperly accessed by one or more employees. Patient names, Social Security numbers, dates of birth and insurance information were exposed. Several employees were fired for misconduct, but one employee was fired for viewing patient information without authorization for the purpose of identifying motor vehicle accident victims. The hospital launched an investigation after a car-accident victim felt that a soliciting attorney had somehow obtained his medical information.UPDATE (10/19/2011): The FBI is now investigating the disclosure of patient information. It appears that three employees sold accident victim data to an attorney referral service. Former patients have also been contacted by funeral homes and at least one patient became an identity theft victim.UPDATE(08/18/2012): One dishonest employee who worked at Florida Hospital Celebration allegedly viewed the emergency room records of 763,000 patients. A total of 12,000 patients from the group of 763,000 were contacted by the Hospital and notified of the risk of identity theft.UPDATE(10/22/2012): The former employee worked at Florida Hospital from July 2006 until July 2011 and was responsible for registering emergency patients. The scam involved patient phone referrals to a lawyer or chiropractor who knew details about car accidents and hospital treatments. The dishonest employee had illegally gathered the patient information during emergency visits. He pleaded guilty to conspiracy to obtain health information and wrongful disclosure of health information.UPDATE(01/07/2013): A man associated with Metro Chiropractic and Wellness Center and City Lights Medical Center pleaded guilty to charges related to illegally obtaining patient information from two spouses who worked at Florida Hospital Celebration. He was charged with one count of conspiracy to defraud the United States and four counts of makinga payment to a non-licensed physician.UPDATE(04/12/2013): One former patient affected by the breach has brought a lawsuit against Adventist Health System/Sunbelt, Inc. Florida Hospital Celebration and 36 other hospitals compose the Adventist network. The former patient is alleging that their privacy rights as a patient were violated when Adventist Health System/Sunbelt Inc. failed to prevent emergency room works from selling access to their medical records. (12000 records involved) [source]. | |
MaineCoast Memorial Hospital purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Florida Hospital Tampa (formerly University Community Hospital Medical Center), Crothall Healthcare, Naval Medical Center (Bob Wilson Naval Hospital) had a data breach in 2012, in Florida. Three people were arrested for their roles in filing 225 fraudulent tax returns. They face charges of conspiracy, theft of government property, and aggravated identity theft. About $555,000 in refund money was obtained. One of the defendants worked at Florida Hospital Tampa through a maintenance and housekeeping company. Information came from a variety of medical centers in California and Florida. There was an incident where the dishonest worker provided her co-conspirators with a list of names and Social Security numbers from patients seen at Florida Hospital Tampa on January 17 of 2012 and another incident where ER patient names, Social Security numbers, and other information was stolen from Crothall Healthcare in January. (45 records involved) [source]. | |
MaineGeneral Medical Center purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Foothills Nephrology Associates had a data breach in 2011, in South Carolina. A company laptop was stolen from physicians vehicle on the night of April 27. Patient names, dates of birth and clinical information were on the laptop. It did not contain Social Security numbers or financial information. [source]. | |
Marin General Hospital purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Fort Worth Allergy and Asthma Associates had a data breach in 2010, in Texas. The June 29th theft of four computers resulted in patient records being exposed. The patient records contained addresses, Social Security numbers and dates of birth. (25,000 records involved) [source]. | |
Marshall Medical Center purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Foundation Medical Partners had a data breach in 2012, in New Hampshire. A total of 771 patient records may have been exposed as a result of a breach that occurred on November 19, 2011. No further details were disclosed. [source]. | |
Martins Point purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Franciscan Medical Group had a data breach in 2011, in Washington. A computer that contained the protected health information of patients was stolen on or around November 18, 2010. [source]. | |
Mason General Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Freda J. Bowman MD, PA had a data breach in 2011, in Texas. Protected health information from a network server was breached on or around August 8, 2011. The incident may have been an unintended disclosure which allowed unauthorized users to view information, or it may ahve been a hacking attack. [source]. | |
Mayo Clinic purchases statewide personal hospital discharge data from at least CA ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Friendship Center Dental Office had a data breach in 2011, in Florida. A laptop that contained the protected health information of patients was stolen on or around December 20, 2010. [source]. | |
Mcgee Medical purchases statewide personal hospital discharge data from at least NJ [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Froedtert Health had a data breach in 2013, in Wisconsin. A computer virus was discovered on an employees work computer account on December 14, 2012. One of the files on the employees computer contained patient names, addresses, telephone numbers, dates of birth, medical record numbers, names of health insurers, diagnoses, and other clinical information. A limited number of Social Security numbers were also exposed. (800 records involved) [source]. | |
Medstar Health purchases statewide personal hospital discharge data from at least MD [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Gail Gillespie and Associates, LLC had a data breach in 2011, in Texas. On or around June 25, 2011, a breach involving a laptop, a computer, and a network server was discovered. Patient information was exposed as a result of the breach. [source]. | |
Memorial Hermann purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Gastroenterology Consultants had a data breach in 2010, in Nebraska. A local news station responded to a report about patient files being left in a recycling dumpster outside of the clinic. Hundreds of documents with patient names, Social Security numbers, addresses and detailed medical information were found and secured by KMTV Action 3 News. The files appear to be from 2002 and 2003. [source]. | |
Memorial Medical Center purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Geisinger Health System had a data breach in 2010, in Pennsylvania. A former physician emailed patient medical information to his home email account in an unencrypted manner. The information included patient names, medical record numbers, procedures and indications. The physician deleted the information from his computer, home network and servers. The incident occurred on or around November 3. [source]. | |
Memorial Sloan-Kettering Cancer Center purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | General Internal Medicine of Lancaster had a data breach in 2008, in Pennsylvania. A laptop was stolen from a doctors office containing the Social Security numbers of patients. The clinic is notifying 12,000 potential-affected patients. [source]. | |
Mercy Hospital purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Georgetown University Hospital had a data breach in 2012, in District Of Columbia. A technicians USB thumb drive with patient information was misplaced at Georgetown University Hospital. People who were associated with the Department of Laboratory Medicine and visited the Hospital between September of 2004 and September of 2009 may have had their names, medical record numbers, dates of birth, blood types, dates of blood tests, blood test results, summary of clinical histories, and clinician names exposed. The thumb drive was last seen on September 9, 2011, and was discovered missing on the morning of September 14, 2011. [source]. | |
Meridian Health (Jersey Sh. Umc, Ocean Mc & Riverview Mc) purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Georgia Health Sciences University had a data breach in 2012, in Georgia. A laptop was stolen from the home of a nurse on January 18, 2012. It contained the names, dates of birth, partial diagnosis information, and internal codes associated with patients laboratory tests. The information is from patients of the Adult Sickle Cell Clinic. [source]. | |
Methodist Health System purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Georgia Obstetrical and Gynecological Society had a data breach in 2012, in Georgia. Two laptops with member information were stolen during an office burglary. Financial and other administrative information were also on the laptops. The laptops did not contain any patient information. It is unclear if the theft of the equipment was politically motivated.UPDATE(3/26/2012): The breach appears to have been politically motivated. Two other OB-GYNs had laptops stolen from their offices after speaking out against a controversial Georgia bill. [source]. | |
Mid Coast Health Services purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Gibson General Hospital had a data breach in 2012, in Indiana. The November 27 theft of a laptop may have resulted in the exposure of patient information. Names, Social Security numbers, addresses, and clinical information may have been exposed. Patients who have received services since 2007 may have been affected. (29,000 records involved) [source]. | |
Mid Coast Hospital purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Good Samaritan Hospital had a data breach in 2011, in Maryland. A man posing as a vendor took two barrels of old X-ray film. The film contained medical data from over five years ago. It had been put aside for destruction or recycling. Authorities believe the thief wanted to extract the silver contained in the films. [source]. | |
Mid-Valley Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Grady Memorial Hospital had a data breach in 2008, in Georgia. Hospital records were stolen, although it remains unknown how many patient records were compromised, which patients were affected or how the records were stolen. The records pertained to recorded physician comments that Grady sent to a vendor to transcribe into medical notes. The records were stolen from a subcontractor employed by the vendor. [source]. | |
Midland Memorial Hospital purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Granger Medical Clinic had a data breach in 2013, in Utah. A total of 2,600 medical appointment records disappeared before they could be shredded. The records contained patient names, dates of appointments, times of appointments, and reason for appointment. No medical claim information, financial information, or Social Security numbers were exposed. [source]. | |
Morton General Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Grays Harbor Pediatrics had a data breach in 2011, in Washington. A backup tape was stolen from an employees car sometime around November 23. The device was used for storing copies of paper records. Patients may have had their names, Social Security numbers, insurance details, drivers license information, immunization records, medical history forms, previous doctor records and patient medical records scanned and placed on the backup tape. (12000 records involved) [source]. | |
Mount Desert Island Hospital purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Greater Detroit Hospital had a data breach in 2007, in Michigan. Its a repeat of a problem that emerged late last year at the Greater Detroit Hospital where metal thieves stripped everything from copper piping to windows, exposing rows of abandoned patient files. Neighbors said there are hundreds of boxes of patient files and payroll records inside, full of credit card and Social Security numbers. [source]. | |
Mount Sinai purchases statewide personal hospital discharge data from at least MD [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Greensboro Gynecology Associates had a data breach in 2008, in North Carolina. A backup tape of patient information was stolen from an employee who was taking the tape to an off-site storage facility for safekeeping. The stolen information included patients names, addresses, Social Security numbers, employers, insurance companies, policy numbers and family members. (47000 records involved) [source]. | |
Mountainside Hospital purchases statewide personal hospital discharge data from at least NJ [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Greenville Hospital System University Medical Center, Allen Bennett Memorial Hospital had a data breach in 2011, in South Carolina. Exposed boxes of patient information were reported to Greenville Hospital System on December 31, 2010 by someone wishing to remain anonymous. The boxes were in a storage structure behind the building of an abandoned hospital. The hospital was Allen Bennett Memorial Hospital; it closed in August of 2008. Greenville Hospital System collected the boxes and notified patients in February. The 22 boxes contained information from Allen Bennett Memorial dating from 1990 to 1999. The information in the boxes included patient names, reasons and dates for visits, amount paid, patient insurance information with diagnosis and treatment, and admission reports with patient dates of birth and some Social Security numbers. An investigation revealed that the information in the boxes was probably not used for criminal purposes and that no one was sure how the boxes had gotten there. [source]. | |
Multicare Good Samaritan Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Greil Memorial Psychiatric Hospital had a data breach in 2008, in Alabama. Index cards containing patients personal information, names, dates of birth, even Social Security numbers are gone. Hundreds of records have simply disappeared. [source]. | |
Multicare Health Systems purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Gressler Clinic had a data breach in 2012, in Florida. A May 3 office burglary resulted in the theft of sensitive documents. The stolen documents were charge tickets and contained Social Security numbers, addresses, phone numbers, dates of birth, insurance information, and diagnosis and treatment information. (1,400 records involved) [source]. | |
Nemours Childrens Hospital purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Griffin Hospital had a data breach in 2010, in Connecticut. A former employee appears to have continued accessing patient names, medical information, dates of birth and medical record numbers. Patients received soliciting phone calls from a physician at another hospital.UPDATE(06/212012): The physician and radiologist responsible for the breach has been fined $20,000 for downloading patient information and using it to promote radiology services at Advanced Mobile Imaging Radiology. [source]. | |
Nemours Foundation purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Group Health Cooperative Health Care System had a data breach in 2007, in Washington. Two laptops containing names, addresses, Social Security numbers and Group Health ID numbers of local patients and employees have been reported missing. (31000 records involved) [source]. | |
New York Presbyterian Hospital purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Gulf Coast Health Care Services had a data breach in 2012, in Florida. A network security incident resulted in the expose of patient information. The breach occurred on August 17.UPDATE(11/26/2012): An employee accessed and downloaded patient information without authorization or a legitimate purpose on five occasions between June 29 and September 20 of 2012. Gulf Coast Health Care Services discovered the issue on September 26. Patients who were seen between 1992 and September 20, 2012 may have had their names, addresses, dates of birth, and phone numbers accessed. It appears that the employee was accessing the data for the purpose of helping outside practitioners recruit patients to their own practices. The incident was reported to the FBI, the Sarasota Police Department, and the Florida Department of Law Enforcement.This entry on the Privacy Rights Clearinghouse Chronology of Data Breaches was previously listed as a hack and was reclassified as an insider breach based on new information. [source]. | |
Newport Community Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Gulf Coast Medical Center had a data breach in 2007, in Florida. Patient information including names and Social Security numbers were compromised when a computer went missing in February in Tallahassee, FL. A very similar and previously uncovered breach happened in November of 2006. (8000 records involved) [source]. | |
North Bay Healthcare purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Gulf Coast Medical Center had a data breach in 2007, in Tennessee. Patient information including names and Social Security numbers were compromised when a computer went missing in November 2006 from Nashville, TN. This breach drew media attention when an additional 8,000 patients information was compromised during a February 2007 breach in Tallahassee, FL. (1,900 records involved) [source]. | |
North Broward Hospital District purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Gulf Pines Hospital had a data breach in 2010, in Florida. Former employees are concerned that the hospital was not properly cleared before being sold. People reported abandoned files in the middle of the hospital. An emergency room log, drivers license information, Social Security numbers and other personal files were left in the hospital. Patient medical records were removed. The buyer of the property was contacted, but did not return phone calls. [source]. | |
North Florida Surgery Center purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Gundersen Lutheran Medical Center had a data breach in 2006, in Wisconsin. A Medical Center employee used patient information, including SSNs and dates of birth, to apply for credit cards in their names. As patient liaison, her duties included insurance coverage, registration, and scheduling appointments. She was arrested for 37 counts of identity theft, and was convicted of identity theft and uttering forged writing, according to the criminal complaint. [source]. | |
North Valley Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Hackensack University Medical Center had a data breach in 2012, in New Jersey. On September 26, 2011, Hackensack University Medical Center became aware that a dishonest employee had accessed patient information prior to September 1, 2011. A former employee working as a clerk took confidential patient files from an outpatient clinic. The files contained names, Social Security numbers, addresses, dates of birth, drivers license numbers, health insurance cards, and other insurance information. No medical records were taken. (445 records involved) [source]. | |
Northwest Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Halifax Health had a data breach in 2009, in Florida. A laptop computer from a Halifax health employees vehicle in Orange County was stolen -- which might have contained password protected patient information. (33,000 records involved) [source]. | |
Northwestern University Feinberg School Of Medicin purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Hanger Prosthetics and Orthotics Group had a data breach in 2010, in Texas. A laptop was stolen from a human resources employee on November 4. The laptop contained employee names, Social Security numbers, health information and addresses.UPDATE(2/15/11): HHS shows that the breach affected 4,486 people. (4486 records involved) [source]. | |
Ny Downtown Hospital purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Harris County Hospital had a data breach in 2008, in Texas. A lower-level Harris County Hospital district administrator downloaded medical and financial records for patients with HIV, AIDS and other medical conditions onto a flash drive that later was lost or stolen. This may have been a violation of law. The data on the device included the patients names, medical record numbers, billing codes, the facilities where the office visits occurred and other billing information. It also included the patients medicaid or Medicare numbers, which can indicate their Social Security numbers or those of their spouses. (1200 records involved) [source]. | |
Nyu Medical Center purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Harris County Hospital District had a data breach in 2012, in Texas. The Harris County Hospital District was alerted to an issue when they received a grand jury subpoena on February 11, 2011. A dishonest employee was immediately fired for viewing and possibly sharing patient names, Social Security and member numbers, medical record numbers, addresses, phone numbers, dates of birth, sexes, emergency contact information, payer information, and other medical care information. The Harris County Hospital District decided to send patients notifications on July 20, 2012 after receiving additional information about the breach. The former employee was indicted and will be tried on criminal charges related to the stolen and misused information on September 24, 2012. [source]. | |
OConnor Hospital purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Hartford Hospital, VNA HealthCare, Greenplum had a data breach in 2012, in California. An employee of Greenplum was robbed of a laptop during a home burglary on or around June 26. Greenplum is a subsidiary of a hospital vendor known as EMC Corp. The laptop contained the information of 7,461 VNA HealthCare patients and 2,097 Hartford Hospital patients. Patients had their names, Social Security numbers, addresses, dates of birth, marital status, Medicaid and Medicare numbers, medical record numbers, and certain diagnosis and treatment information exposed. (9,558 records involved) [source]. | |
Ocean Beach Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Harvard University Health Services, Anna Jacques Hospital, Lowell General Hospital, Saints Medical Center had a data breach in 2011, in Massachusetts. Two men were arrested for posing as employees of an X-ray removal company in order to steal old X-ray films. The two men hit multiple locations. It is believed that their primary focus was the silver contained in the films, however patient medical and personal information was also linked to the X-ray films. Around 1,000 X-rays were stolen from Harvard University Health Services and a barrel of X-rays was taken from Anna Jaques Hospital. The men were charged with conspiracy and larceny from a building. The thefts occurred in August, but it is unclear how many other organizations were affected. The men were also linked to a crime or crimes in New Hampshire.UPDATE(03/05/2012): The men were tied to thefts and theft attempts at Anna Jaques Hospital in Newburyport and Saints Medical Center in Lowell. [source]. | |
Olympic Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Hazleton Community Ambulance Association had a data breach in 2011, in Pennsylvania. Hundreds of sheets were found inside of folders in improperly discarded boxes. The sheets were easily visible and accessible through sliding doors on either side of the dumpster and a firefighter alerted a local newspaper to the incident. The records contained names, Social Security numbers, payroll information, addresses, phone numbers, insurance information, dates of birth, and medical histories from employees and former patients of the Ambulance Association. It appears that all of the records are from 2003 and 2004. An Ambulance Association officer admitted to placing the boxes in a dumpster rather than following usual procedure and shredding them. [source]. | |
Orange Coast Memorial Medical Center purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | HCA, Inc. Hospital Corporation of America had a data breach in 2006, in Tennessee. 10 computers containing medicare and Medicaid billing information and records of employees and physicians from 1996-2006 were stolen from one of the companys regional offices. Some patient names and SSNs were exposed, but details are vague. Records for patients in hospitals in the following states were affected: CO, KS, LA, MS, OK, OR, TS, WA. [source]. | |
Orlando Health purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Head Injury Association had a data breach in 2012, in New York. A former manager was indicted for stealing the identities of patients. He faces a 48-count indictment alleging grand larceny in the third degree, identity theft in the second degree, offering a false instrument for filing in the first degree, and possession of a forged instrument in the second degree. He allegedly used the names and Social Security numbers of patients to e-file fraudulent tax returns and obtain over $200,000 in federal, New York, and New Jersey tax refunds. The scam occurred in 2006 and 2007. It was not discovered until recently since those who were affected were unable to work with investigators. The manager was convicted for similar crimes in the past. He used the information of a deceased and developmentally disabled individual froma Nassau County group hometo obtain a fraudulent debit card and was also arrested for credit card fraud near Atlanta, Georgia.UPDATE(12/19/2012): The former manager pleaded guilty to 20 counts of second-degree identity theft and offering a falseinstrument for filing, as well as six counts of criminal possession of a forged instrument and additional charges. He will pay $20,000 in restitution. His sentencing is expected to be on January 25, 2013 and he faces up to four years in prison. (56 records involved) [source]. | |
Othello Community Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Healing Hands Chiropractic had a data breach in 2007, in Colorado. Hundreds of medical records containing the personal information of chiropractic patients including Social Security numbers, birth dates, addresses and, in some cases, credit card information were thrown into a dumpster ã–due to lack of office space.ãù [source]. | |
Overlake Hospital Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Health and Sports Rehab, Inc. had a data breach in 2012, in Massachusetts. A dishonest intern stole personal information while working at the clinic. The information was used to create and cash fraudulent checks and the dishonest intern pled guilty. [source]. | |
Palo Alto Va Healthcare System purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Health Research Institute, Inc., Pfeiffer Treatment Center had a data breach in 2011, in Illinois. The July 1, 2011 theft of a desktop computer and network server resulted in the exposure of patient information. [source]. | |
Paris Regional Medical Center purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Healthcare Partners had a data breach in 2011, in California. Nineteen computers were stolen during an office burglary on Monday, April 18. Administrative information such as names, addresses, dates of birth, medical record numbers, and health insurance plan ID numbers were exposed. Sensitive medical information such as treating physician names, diagnoses, treatment plans, progress notes, prescriptions, referrals, and authorizations were also exposed. A safe with 16 patient checks and 60 patient credit card receipts was also stolen. (16 records involved) [source]. | |
Parrish Medical Center purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Henry Ford Health Center had a data breach in 2011, in Michigan. An employee misplaced a flash drive with sensitive patient information. The flash drive was lost on January 31 and investigators began the process of determining what happened and what information was on the flash drive on February 8. Patients tested for urinary tract infections between July and October of 2010 may have had their names, medical record numbers, test information and results exposed. [source]. | |
Peacehealth purchases statewide personal hospital discharge data from at least WA NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Henry Ford Health System had a data breach in 2011, in Michigan. A computer with sensitive patient information was stolen sometime between August 5 and August 7. It held patient names, physician names, medical record numbers, and genotype test results. [source]. | |
Penobscot Bay Medical Center purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Henry Ford Health System had a data breach in 2010, in Michigan. An employees laptop was stolen on September 24. It contained the information of patients who received prostate services between 1997 and 2008. The laptop was stolen from an unlocked urology medical office. No Social Security numbers, full medical records or health insurance identification numbers were on the stolen laptop. Patient names, medical record numbers, dates of birth and treatment information were on the laptop.UPDATE (11/23/10): The breach affected 3,700 patients. [source]. | |
Phoebe Putney Memorial Hospital purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Heyman HospiceCare, Floyd Medical Center had a data breach in 2013, in Georgia. The theft of a password-protected laptop from an employees car may have resulted in the exposure of patient information. The theft occurred on January 4, 2013 and was reported immediately. Patients who were treated between July 1, 2006 and January 3, 2013 may have had their names, Social Security numbers, addresses, phone numbers, dates of birth, insurance policy numbers, diagnoses, visit notes, physician names, caregiver names, and advance directives exposed. [source]. | |
Pmmc purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | High Point Regional Health System, Premier Imaging LLC had a data breach in 2011, in North Carolina. A former employee was fired after taking patient files home sometime between September 14 and October 6. The files contained patient names, Social Security numbers, dates of birth, addresses, drivers license numbers and insurance information. A total of 47 patient records were returned, but it is unclear if the employee may still have others. (47 records involved) [source]. | |
Pomona Valley Hospital Medical Center purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Highland Hospital (Rochester, NY) had a data breach in 2007, in New York. Two laptop computers, one containing patient information including Social Security numbers, were stolen from a business office. The computers were sold on eBay, and the one containing personal information was recovered. (13000 records involved) [source]. | |
Portsmouth Regional Hospital purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Highlandtown Community Health Center, Johns Hopkins Hospital had a data breach in 2012, in Maryland. At least four people were involved in an identity theft ring that affected over 250 people. One member of the ring was employed by Highlandtown Community Health Center and provided personal and financial patient information that he accessed through his position. The information was used by other ring members to create counterfeit checks and fraudulent state identification cards. The fraud occurred between August and October of 2009.Another member of the ring was employed by Johns Hopkins Hospital and provided the information of doctors who applied for fellowships there. Several ring members rented apartments under the identities of doctors. Two of the members pleaded guilty to conspiring to commit wire fraud and aggravated identity theft. The four members of the ring are required to collectively pay restitution for fraudulently obtained cash, merchandise, and services worth over $188,000. (250 records involved) [source]. | |
Prosser Memorial Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Holy Cross Hospital, Office of Dr. Elliot Stein had a data breach in 2010, in Florida. A criminal investigation uncovered 38 patient files. The files contained names, addresses, Social Security numbers, dates of birth and descriptions of initial diagnosis from Emergency Room visits. An investigation that began in June showed that an employee was responsible; that employee was fired. The employee may have inappropriately accessed 1,500 patient files between April 2009 and September of 2010. The Hospital now limits the amount of key personal data included in the type of documents involved in the incident.UPDATE(2/17/2011): Five other suspects have been arrested within the past month. Authorities learned of the fraud ring in May of 2010.UPDATE(4/15/2011):A former Holy cross Hospital employee was sentenced to prison for disclosing patient information. The woman was sentenced to 24 months in prison with 12 months of home confinement, followed by three years of supervised release. after being caught selling patient information from her employer, she pleaded guilty to disclosing individually identifiable health information.UPDATE(6/21/2011): It was revealed that one of the other suspects is being charged with selling information from the office of Dr. Elliot Stein in Aventura. A criminal investigation uncovered lists of patient information from Dr. Stein that included names, Social Security numbers, addresses, dates of birth, and health information. (1500 records involved) [source]. | |
Providence Everett Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Hospital Auxilio Mutuo had a data breach in 2010, in Puerto Rico. The Hospital experienced a breach of one or more computers on or around November 19. The exact nature of the breach was not reported and could have been theft, unauthorized access, hacking, or an IT incident. [source]. | |
Providence Health Services purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Howard University Hospital had a data breach in 2012, in District Of Columbia. A dishonest employee working as a technician in the surgery department at Howard University Health Sciences sold patient information between August 2010 and December of 2011. The employee was charged with one count of wrongful disclosure of individually identifiable health information. Patient names, Medicare numbers, addresses, and dates of birth may have been exposed.UPDATE(09/24/2012): The dishonest employee was sentenced to 100 hours of community service and three years of probation. The probation term includes six months in a halfway house followed by six months of home confinement. She was also fined $2,100. Her illegal activities involved taking the records of hospital patients, selling their names, addresses, dates of birth, and medical numbers to an unauthorized party, and providing blank hospital prescription forms as well. The dishonest employee was paid between $500 and $800 in cash for each transaction. The information was used for fraudulent oxycodone prescriptions. (40 records involved) [source]. | |
Providence Hospital purchases statewide personal hospital discharge data from at least MD [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Howard University Hospital had a data breach in 2012, in District Of Columbia. The January 27 theft of a laptop from a former contractors vehicle resulted in the loss of patient information. The patient files included Social Security numbers, names, addresses, identification numbers, medical record numbers, dates of birth, admission dates, diagnosis-related information, and discharge dates. The majority of those affected were patients who were treated at the Hospital between December 2010 and October 2011. Some patients who received treatment as far back as 2007 were also affected. The patient files had been downloaded onto the contractors personal laptop in violation of the Hospitals policy. The contractor stopped working for the hospital in December of 2011.UPDATE(09/21/2012): The number of patients who were notified was revised from 34,503 to 66,601. (66601 records involved) [source]. | |
Providence Saint Peter Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Huntsville Hospital had a data breach in 2012, in Alabama. A thief or thieves entered Huntsville Hospital and impersonated a vendor in order to collect old barrels of X-rays. Thieves commonly use this tactic to obtain X-rays. The X-rays are then stripped for silver. The X-rays contained patient names, dates of birth, and medical records. There were over 1,000 X-rays, but only 125 to 175 patients were affected. [source]. | |
Providence Sw Washington Service Area purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Hurley Medical Center had a data breach in 2011, in Michigan. A laptop was discovered missing in May. It was held in a locked room in Hurley, but it was not encrypted or password protected. The laptop contained the names, heights, weights, dates of birth, medical record numbers and lung function test results of 1,938 patients who visited Hurley between 2007 and May of 2011. A total of 10 out of 150 of Hurleys laptops were not encrypted at the time of the discovery. [source]. | |
Puget Sound Health Alliance purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Hutcheson Medical Center had a data breach in 2010, in Tennessee. Anyone who peered inside the mixed paper bin at the Dupont Recycling Center in May of 2009 got an eyeful. Files, in plain sight, which contained sensitive medical and identity information. Authorities dont know how those thousands of files got there. Some of the records came from Hutcheson and a plastic surgery office in the area. The information inside those files included graphic photos, and Social Security numbers. [source]. | |
Puget Sound Surgical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Independence Physical Therapy had a data breach in 2012, in Connecticut. A desktop computer was stolen or discovered stolen on August 1, 2011. It contained protected health information. The incident was disclosed on July 3. [source]. | |
Pullman Regional Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Indiana Internal Medicine Consultants had a data breach in 2012, in Indiana. The February 11, 2012 theft of a laptop resulted in the exposure of protected health information. [source]. | |
Quincy Valley Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Indiana Regional Medical Center had a data breach in 2011, in Pennsylvania. A former employee stole more than 500 patient records for the purpose of using them as evidence in a legal dispute with a physician. The theft occurred in September of 2010 and included the medical information of three or four patients, as well as administrative information related to hundreds of other patients. [source]. | |
Redington Fairview General Hospital purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Indiana University Health Arnett had a data breach in 2013, in Indiana. The theft of an employees unencrypted laptop resulted in the exposure of patient information. The laptop was stolen from an employees car on April 9 and contained email records. Patient names, medical record numbers, dates of birth, physician names, diagnoses, and dates of service may have been exposed. [source]. | |
Redwood Regional Medical Group purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Indiana University Medical Group had a data breach in 2012, in Indiana. A concerned citizen found a box of sensitive medical documents in a dumpster and contacted a local news team. The box contained hundreds of documents that included copies of drivers licenses, prescriptions, signatures, and other patient information. The box was removed by Indiana University Medical Group before investigators arrived. Indiana University Medical Group claimed that the information was accidentally discarded rather than shredded. The documents were properly disposed after being collected. [source]. | |
Rhode Island Hospital purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Indiana University School of Medicine had a data breach in 2011, in Indiana. A laptop with sensitive information was stolen from a physicians car on Tuesday, August 16 of 2011. It contained patient information such as name, age, sex, diagnosis, medical record number, and in 178 cases, Social Security numbers. Individuals were notified on September 2. (178 records involved) [source]. | |
Sacred Heart Health System purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | InStep Foot Clinic had a data breach in 2011, in Minnesota. Electronic medical records may have been exposed as a result of the theft of a laptop on or around August 28, 2011. [source]. | |
Sacred Heart Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | IntraCare North Hospital had a data breach in 2012, in Texas. A former employee used patient information to file false income tax returns. The information of 741 patients was accessible in a binder. The employee worked as an intake coordinator at the Hospital from March 15 to August 18 of 2011. The breach was not discovered until April 18 of 2012. [source]. | |
Samaritan Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Israel Deaconess Medical Center had a data breach in 2012, in Massachusetts. The May 22 office theft of a physicians laptop resulted in the exposure of patient information. It is unclear what type of information was on the laptop, but the chief information officer said that nothing that would be used from an identity theft perspective was on the laptop. [source]. | |
Samaritan Medical Cener purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Jackson health System had a data breach in 2013, in Florida. A box that contained patient medical records was determined to have been missing since January. Patient medical diagnoses, surgical procedures, and other personal health information may have been exposed. The missing records were either on their way to be electronically scanned or returning from being scanned. [source]. | |
San Antonio Community Hospital purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Jackson Memorial Hospital had a data breach in 2009, in Florida. A Miami man was charged with buying confidential patient records from a Jackson Memorial Hospital employee over the past two years, and selling them to a lawyer suspected of soliciting the patients to file personal-injury claims.UPDATE (10/26/10): Ruben E. Rodriquez was sentenced to 11 years in prison for selling patient records to lawyers for injury claims. Rodriquez stole 3,350 patient records in 2008 and 2009. He may have also sold information in 2007. The information included name, contact information and medical diagnoses. [source]. | |
Santa Barbara Cottage Hospital purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Jackson Memorial Hospital, Jackson Health System had a data breach in 2011, in Florida. An unidentified former employee inappropriatelyaccessed the the financial information of hospital patients. The employee was fired and the department they worked in was not revealed. (1,800 records involved) [source]. | |
Santa Clara Valley Medical purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Jackson North Medical Center, Jackson Health System had a data breach in 2012, in Florida. A dishonest volunteer was caught passing patient information to people who used it to file fraudulent tax returns. The volunteer used his smart phone to capture patient records while working in an emergency room. Around 1,200 photos of 566 patient records were found on his phone. The breach was discovered when three men were caught using free wi-fi at McDonalds to file fraudulent tax returns in March.UPDATE(01/11/2013): Jackson Health banned volunteers from using cell phone in patient areas in order to prevent similar events from occurring. (566 records involved) [source]. | |
Santa Rosa Memorial Hospital purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Jacobi Medical Center, North Central Bronx Hospital, Tremont Health Center, and Gunhill Health Center had a data breach in 2011, in New York. The New York City Health & Hospitals Corporations North Bronx Healthcare Network experienced a breach. Backup tapes were stolen from an unsecured and unlocked van during transport by GRM Information Management Services. The theft occurred during December of 2010. The information on the tapes was from patients, staff members and associated employees and dated back to 1991. Names, Social Security numbers, addresses, patient health information and other patient and employee information may have been exposed. (1700000 records involved) [source]. | |
Sarasota Memorial Hospital purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Jacobs Neurological Institute had a data breach in 2006, in New York. The laptop of a research doctor was stolen from her locked office at the Institute. It included records of patients and her research data. [source]. | |
Scripps Health purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | James A. Haley VA Hospital had a data breach in 2011, in Florida. A camera from the Plastic Surgery Clinic was discovered missing in November of 2010. It contained Social Security numbers and graphic photos of female patients before and after surgery for breast cancer. The same investigation that uncovered the missing camera also revealed that laptops, televisions, thumb drives, microscopes, a hospital surveillance system, and other equipment had been lost or stolen within the past two years. One missing thumb drive contained additional patient information. [source]. | |
Seattle Cancer Care Alliance purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | James A. Haley Veterans Hospital had a data breach in 2011, in Florida. Hundreds of paper patient forms were compromised in May. An off-duty Tampa police officer discovered the records in a Motel 6 in May. The occupants of the motel room were detained on identity theft charges. The forms contained patient names, Social Security numbers, and dates of birth. The papers included Turbo Tax cards, receipts, and medical records from the Veterans Affairs hospital. At least one veteran had a fraudulent debit card charge. [source]. | |
Seattle Childrens Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Jefferson Center for Mental Health had a data breach in 2011, in Colorado. A list with patient information was stolen from an employees locked car on December 13, 2010. The employees purse and work bag were also stolen. [source]. | |
Sentara purchases statewide personal hospital discharge data from at least MD [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Jewish Hospital Catheterization Lab had a data breach in 2010, in Kentucky. Two stolen laptops contained personal information on patients who were treated between June 2, 2009 and July 16. 2010. Patient names, Social Security numbers, dates of birth, medical record numbers, addresses, phone numbers, patient account numbers, and insurance carriers. (2,089 records involved) [source]. | |
Seton Healthcare Family purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | John Muir Physician Network had a data breach in 2010, in California. John Muir Health, the Walnut Creek-based hospital system, has begun notifying 5,450 patients by mail of a potential breach of their personal and health information. Two months ago two laptop computers at the John Muir Physician Network Perinatal office in Walnut Creek were stolen. The laptops were password protected and contained data in a format that would not be readily accessible. External vendors and internal experts discovered that the missing laptops contained personal and health information going back more than three years. (5,450 records involved) [source]. | |
Shands Healthcare Planning purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Johns Hopkins Hospital had a data breach in 2009, in Maryland. An investigation suggests a former employee who worked in patient registration may have been linked to a scheme to create fake drivers licenses in Virginia. The employee had access to information such as name, address, telephone number, mother and fathers names, dates of birth and Social Security numbers, but not to any health or medical information.UPDATE (10/1/10 via PHIPrivacy.net): The former employee and four others were indicted for fraud and aggravated identity theft. They are charged with using patient information to create fraudulent credit accounts. The former employee worked at the hospital between August 2007 and March of 2009. It is believed that around 600 patients may have been targets for identity theft, but only 50 incidents were linked to the former employee. (10200 records involved) [source]. | |
Shannon Medical Center purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Johns Hopkins Hospital had a data breach in 2008, in Maryland. On December 21, a briefcase with sensitive documents was stolen from an employees car. The documents included names, Social Security numbers, addresses, dates of birth, phone numbers, physical and mental health information, medical ID numbers and demographic information. Current and former members of a program called Creative Alternatives were affected. (190 records involved) [source]. | |
Sharp Healthcare purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Johns Hopkins Hospital had a data breach in 2007, in Maryland. A desktop computer containing the personal information of 5,783 Johns Hopkins Hospital patients was stolen. The computer included patients names, Social security numbers, birth dates and medical histories. (5,783 records involved) [source]. | |
Sherman/Grayson Hospital, Llc purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Johns Hopkins Medicine had a data breach in 2009, in Maryland. A woman who worked as a patient services coordinator for Johns Hopkins Medicine has been sentenced to 18 months in prison for stealing patient information. The 31 year-old woman of Baltimore was also ordered to pay more than $200,000 in restitution. According to her plea agreement and court documents, from August 2005 to April 2007, the woman provided a conspirator with names, Social Security numbers and other identifying information of more than 100 current and former patients of Johns Hopkins. That information was used to apply for credit. (100 records involved) [source]. | |
Shriners Hospital - Spokane purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Johns Hopkins University and Johns Hopkins Hospital had a data breach in 2007, in Maryland. Johns Hopkins reported the disappearance of 9 backup computer tapes containing personal information of employees and patients. Eight of the tapes contained payroll information on 52,000 past and present employees, including sSNs and in some cases bank account numbers. The 9th tape contained less sensitive information about 83,000 hospital patients. (135000 records involved) [source]. | |
Shriners Hospital For Children N Ca purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Julie A. Kennedy, D.M.D. had a data breach in 2011, in Florida. A network server was discovered to have been stolen on or around September 30, 2011. It may have contained patient information. [source]. | |
Skagit Valley Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Kadlec Regional Medical Center had a data breach in 2011, in Washington. A computer server that contained brain scan and other patient studies was hacked sometime around September 15. Patient names, dates of birth, ages, genders, medical record numbers and doctors names were exposed. The breach was discovered on November 11 during routine monitoring of computer network backups. The server was removed from service and a firm was hired to investigate the issue. [source]. | |
South Lake Hospital purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Kaiser Medical Center had a data breach in 2007, in California. A doctors laptop was stolen from the Medical Center containing medical information of 22,000 patients. but only 500 records contained SSNs. (500 records involved) [source]. | |
Southeast Georgia Health System purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | KCI USA, Inc. had a data breach in 2012, in Texas. A portable electronic device was discovered to have been stolen on or around September 8, 2011. The device may have contained health and/or other personal information. [source]. | |
Southern Maine Medical Center purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Keck School of Medicine, University of Southern California (USC) had a data breach in 2005, in California. A computer server containing names and Social Security numbers of patients, donors and employees was stolen from a campus computer room. (50,000 records involved) [source]. | |
Spine Centers Of America purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Keith & Fisher, DDS, PA had a data breach in 2011, in North Carolina. On February 16, 2011, an IT incident caused patient information to be exposed. It is not known if the breach resulted from a hack or an accidental release of information. The type of patient information exposed was not revealed. [source]. | |
St Agnes Medical Center purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Kern Medical Center had a data breach in 2012, in California. A resident physician printed out the records of 1,500 patients for research purposes. The paper records were stored in a computer bag and the bag was stolen from the physicians car on February 25. The records contained names, health information, and test results. They may have also contained the insurance information of some patients.UPDATE(4/20/2012): Medical record numbers, dates of treatments, diagnoses sites, cocci clinical numbers, and test results for HIV, AIDS, Hepatitis, and pregnancy may have also been exposed. [source]. | |
St Davids Healthcare purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Kern Medical Center had a data breach in 2010, in California. The California Department of Public Health fined Kern Medical Center in Bakersfield, CA, $250,000 for allegedly keeping patient records in an outside, unlocked locker, allowing for the theft of 596 patient records in 2009. For several months in 2009 a Kern Medical Center employee placed the daily lab reports in the broken locker outside the hospital until they were stolen one night. Six additional health facilities were also fined: Biggs Gridley Memorial Hospital, Gridley, Butte County; Childrens Hospital of Orange, Orange, Orange County; Delano Regional Medical Center, Delano, Kern County; Kaweah Manor Convalescent Hospital, Visalia, Tulare County; Oroville Hospital, Oroville, Butte County; Pacific Hospital of Long Beach, Long Beach, Los Angeles County. The total amount of fines for the seven health facilities was $792,000. (596 records involved) [source]. | |
St Joseph Hospital purchases statewide personal hospital discharge data from at least WA CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Kern Medical Center had a data breach in 2010, in California. An employee opened an email that subsequently affected the entire hospital system in late July. The Kern Medical Center temporarily removed itself from the county computer network to prevent the spread of the attack. Patient records were eventually secured, but it is unknown if any were affected by the 16-day malware attack. [source]. | |
St Jude Medical Center purchases statewide personal hospital discharge data from at least CA WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Kindred Healthcare Inc. (Kindred Transitional Care and Rehabilitation) had a data breach in 2012, in Indiana. An office burglary sometime around June 4 resulted in the theft of a safe. The safe held tapes used for backing up Kindred data related to past, present, and prospective patients. Diagnosis information, Social Security numbers, clinical information, bank account and other financial information, addresses, dates of birth, insurance numbers, dates that services were received from Kindred, discharge locations, daily activities, collections letters, and medications received may have been exposed. People admitted between 2009 and 2012 may have been exposed. (1504 records involved) [source]. | |
St Louise Regional Hospital purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Kindred Transitional Care and Rehabilitation-Highgate had a data breach in 2012, in Massachusetts. An office burglary resulted in the theft of a safe on January 26. The safe contained unencrypted backup tapes that require specialized software and equipment to read. The tapes contained patient names, dates of birth, genders, diagnoses, and progress notes. [source]. | |
St Luke Rehabilitation Institute purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Kings County Hospital Center had a data breach in 2010, in New York. The August 22 theft of a desktop computer may have exposed the protected health information of patients. [source]. | |
St Lukes Hospital Roosevelt purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Kingsbrook Jewish Medical Center had a data breach in 2006, in New York. A personal computer was stolen from the Hospitals outpatient billing office on December 26, 2005. It is likely that the computer contained spreadsheets with patient names and Social Security numbers embedded in insurance numbers. Those affected were notified May 26, 2006. (34863 records involved) [source]. | |
St. Joseph Regional Health Center purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Knox Community Hospital had a data breach in 2011, in Ohio. X-ray records were discovered to have been improperly disposed of on or around October 1, 2011. Patient information may have been exposed. [source]. | |
St. Lukes Episcopal Hospital purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Knoxville Medical Clinic, DRD Management had a data breach in 2012, in Tennessee. A former employee took paper documents with patient information without permission. It is unclear if the former employee meant to use the information for fraud purposes. Patient names, dates of clinic visits, dates for scheduled opiate addiction dosages, and the dosage amounts were in the paper documents. The documents were recovered. [source]. | |
St. Marys Health System purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Kunz Opera House had a data breach in 2011, in Illinois. A physician kept 14 boxes of medical records from former patients in the front window of his building. A fire that struck the building, the Kunz Opera House, damaged the records and personal property. Some records were found in the street. An unspecified number of the damaged records were then buried in a secure location. (4200 records involved) [source]. | |
St. Vincents Healthcare purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Lady of the Lake Regional Medical Center had a data breach in 2012, in Louisiana. A laptop went missing from a physicians office sometime between March 16 and March 20 of 2012. The laptop contained patient outcomes data from patients in the adult ICU from 2000 to 2008. Patient names, race, age, dates of admission and discharge from the Intensive Care Unit, and results of treatment may have been exposed. [source]. | |
Stanford Hospital & Clinics purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Lahey Clinic had a data breach in 2012, in Massachusetts. The loss of a physicians unencrypted, password-free Blackberry at an airport on July 1 resulted in the exposure of patient names, dates of birth, medical record numbers, diagnosis information, procedure names, and test results. Lahey Clinic was able to remove all data from the device remotely on July 6. Affected patients were notified in late August. [source]. | |
Sunnyside Community Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Lake Woods Nursing and Rehabilitation Center had a data breach in 2011, in Michigan. The December 28 theft of a computer may have exposed the health information and other types of information of certain individuals. [source]. | |
Suny Downstate Medical Center purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Lakeview Medical Center had a data breach in 2012, in Wisconsin. More than 500 patients of Lakeview Medical Center homecare and hospice programs had their personal information exposed by the theft of a laptop. The laptop was stolen from a car belonging to a Lakeview nurse. It contained names, Social Security numbers, dates of birth, home addresses, medicare ID numbers, and diagnostic information. It is unclear when the laptop was stolen, but the nurse who was involved no longer works for Lakeview. (500 records involved) [source]. | |
Swedish Edmonds purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Lana Medical Care had a data breach in 2012, in Florida. The August 18th theft of a laptop resulted in the exposure of patient information. [source]. | |
Swedish Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Landmark Medical Center had a data breach in 2012, in Rhode Island. The office theft of a laptop resulted in the exposure of patient information. A spreadsheet with sensitive information that could be easily accessed was on the stolen laptop. It is unclear what type of information was exposed, but Social Security numbers, addresses, and medical information were not involved.UPDATE(12/21/2012): A Health and Human Services (HHS) notice reveals that the theft occurred on October 1. A total of 683 patients were affected by the breach. (683 records involved) [source]. | |
Tacoma General Allenmore/Mary Bridge purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Lebanon Internal Medicine Associates, P.C. had a data breach in 2011, in Pennsylvania. Contractors responsible for cleaning out the medical office after a storm improperly disposed of a computer that contained sensitive patient information. Lebanon Internal Medicine Associates left no specific instructions for the removal of the damaged computer. Patient information dating between November 1999 and August 25, 2011 was exposed and included full names, Social Security numbers, dates of birth, home addresses, account numbers, diagnoses, laboratory test results, and medical insurance information. It is believed that the information was inaccessible due to security measures within the server and flood damage. [source]. | |
Texas Health Resources purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Lee Miller Rehab Associates had a data breach in 2013, in Maryland. A network server was stolen or discovered stolen on January 15, 2012. The incident appeared on the HHS website in February of 2013. [source]. | |
Texoma Medical Center purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Legacy Health System had a data breach in 2007, in Oregon. A primary care physician practice has discovered the theft of $13,000 in cash and personal data for patients. Patient receipts, credit card transaction slips and checks are also missing, in addition to Social Security numbers and dates of birth for patients. The investigation indicated it was a dishonest insider. (747 records involved) [source]. | |
The Methodist Hospital System purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Lexington Clinic had a data breach in 2012, in Kentucky. A December 7 overnight office burglary resulted in the theft of a laptop with patient data. It contained names, contact information, and diagnoses of patients receiving services within the neurology department. The locks to the neurology department were changed after the theft was discovered. [source]. | |
Titus Regional Medical Center purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Lincoln Medical and Mental Health Center had a data breach in 2010, in New York. Multiple CDs containing patient personal information were lost in transit by FedEx. Information included dates of birth, drivers license numbers, descriptions of medical procedures, addresses, and Social Security numbers. Siemens Medical Solutions USA, the Hospitals billing contractor, shipped the CDs around March 16th. They were never received. (130,495 records involved) [source]. | |
Tri State Memorial Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Littleton Regional Hospital had a data breach in 2009, in New Hampshire. A patient complaint in March of 2009 resulted in the firing of an employee. An audit revealed that the employee inappropriately accessed patient records for unknown reasons at least three times between 2008 and May of 2009. The records contained names, contact information, dates of birth, insurance information and other health information. uPDATE (8/10/10): Another employee was fired for a similar unauthorized access incident during May of 2010. [source]. | |
University Medical Center purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Living Healthy Clinic, University of Wisconsin - Oshkosh College of Nursing had a data breach in 2011, in Wisconsin. A computer security breach that occurred in July may have exposed the information of uninsured Winnebago County residents who sought health services. The information included names, Social Security numbers, addresses, and the health records of a limited number of people. The breach was discovered when University technology staff identified evidence of a computer virus on a desktop computer. There was no indication that unauthorized parties attempted to download information. (3,000 records involved) [source]. | |
University Medical Center Of El Paso purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Lockerman Family Chiropractic had a data breach in 2011, in Louisiana. Dr. Christopher Lockerman was arrested and charged with eight counts of financial identity fraud and one count of theft by deception. Victims lost over $264,000 due to identity theft. Patients of Lockermans clinic had fraudulent J.P. Morgan Chase lines of credit established in their names. The period during which this took place was not revealed. [source]. | |
University of Connecticut Health Center purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Logan County Emergency Ambulance Service Authority (LEASA) had a data breach in 2011, in West Virginia. A laptop was discovered missing on October 1, 2011. It was either lost or stolen. It contained names, Social Security numbers, addresses, and health information from patients. The laptop appears to have not been used to connect to the internet since October 1 and LEAS is attempting to block potential use of the device. (12563 records involved) [source]. | |
University Of Miami, Sylvester Cancer Center purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Logic World Medical had a data breach in 2010, in Texas. The owner and operator of Logic World Medical used the names, addresses, and account numbers of Medicaid beneficiaries to file false claims for payment of services and goods that he never provided. Approximately $1,101,865.37 was fraudulently claimed between April of 2004 and August of 2006. [source]. | |
University Of Washington Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Loma Linda Medical University had a data breach in 2011, in California. An employee was fired after taking sensitive documents home on or around December 19. Medical records and other documents with patient dates of birth, addresses, drivers license numbers, medical record numbers, and in some cases, Social Security numbers were removed from the hospital against hospital policy. The records were recovered. [source]. | |
Va Boston Healthcare System purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Loma Linda University Medical Center had a data breach in 2010, in California. A thief has stolen personal information regarding more than 500 surgical patients of Loma Linda University Medical Center, according to hospital officials. A desktop computer containing the information disappeared April 5 from the department of surgerys administrative office on Campus Street. The missing information includes each patients name, medical record number, diagnosis, surgery date, and the type of procedure. (584 records involved) [source]. | |
VA Medical Center purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | LoneStar Audiology Group had a data breach in 2010, in Texas. The August 11 theft of a laptop resulted in the exposure of patient health information. [source]. | |
Valley General Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Long Chiropractic had a data breach in 2012, in Ohio. A November 26 office burglary may have resulted in the theft of patient records. A safe with computer disks and a laptop computer were stolen. It is unclear if either contained sensitive patient information. The burglars were in the office for 15 minutes and may have taken or viewed sensitive patient information in other areas. [source]. | |
Valley Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Louisiana State University (LSU) Hospital System had a data breach in 2012, in Louisiana. A dishonest employee working in the billing department used her position to access account information. She scanned checks and identification information from the LSU hospital system database and passed them on to at least four women. The scheme was discovered when the four women were allegedly caught on camera making purchases with fake checks. Handwritten Social Security numbers, check and ID card printing items, computers, and copies of scanned checks were found when the womens homes were searched.At least seven people face charges that include identity theft, conspiracy to commit identity theft, conspiracy to commit monetary abuse, and possession of fraudulent documents for identification purposes. The dishonest employee was charged with 377 counts of identity theft.UPDATE(01/02/2013): LSU Health notified 416 patients after a hospital employee discovered fraudulent activity on her checking account. (416 records involved) [source]. | |
Veterans Hospital/Ucla purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Loyola University Medical Center had a data breach in 2011, in Illinois. A flash drive was stolen from an employees car. It contained the names, dates of birth, Social Security numbers, addresses and phone numbers of fewer than 100 patients. [source]. | |
Virginia Mason Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | LSU Health Shreveport, Siemens Healthcare had a data breach in 2013, in Louisiana. A computer data entry error resulted in a mailing error that exposed patient information. The names and treatment information of certain patients were mistakenly mailed to other patients. No Social Security numbers, dates of birth, or financial account numbers were exposed. [source]. | |
Virtua purchases statewide personal hospital discharge data from at least MD [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Lucile Packard Childrens Hospital had a data breach in 2013, in California. Between May 2 and May 8, a non-functional laptop computer was stolen from a secured area of the hospital. The laptop was password protected and contained names, ages, medical record numbers, telephone numbers, scheduled surgical procedures, and names of physicians involved in procedures between 2009 and 2012. [source]. | |
Walla Walla Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Lucile Packard Childrens Hospital at Stanford University had a data breach in 2010, in California. A former employee took a hospital desktop computer with patient records home around January 11 of 2010. In February it was determined that the computer could not be recovered and patients were notified of the incident. The hospital was fined $250,000 by the California Department of Public Health for the delay in reporting the incident. As of September 9 2010, the hospital was in the process of appealing the fine.UPDATE(9/10/10): The desktop did contain patient Social Security numbers, medical record numbers, names, insurance information, diagnoses and treatment information. (532 records involved) [source]. | |
Wellspan purchases statewide personal hospital discharge data from at least MD [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Lutheran Community Services Northwest had a data breach in 2012, in Washington. An office burglary that occurred on or around March 30, 2012 resulted in the theft of several computers and electronic devices. The computers and devices may have contained the names, Social Security numbers, addresses, phone numbers, email addresses, dates of birth, drivers license numbers, Washington state ID numbers, income or payment information about services, conditions, treatments, or diagnosis information about clients, volunteers, and staff. (756 records involved) [source]. | |
Wenatchee Valley Medical Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Madrona Medical Group had a data breach in 2006, in Washington. On Dec. 17, 2005, a former employee accessed and downloaded patient files onto his laptop computer. files included name, address, SSN, and date of birth. The former employee has since been arrested. (6,000 records involved) [source]. | |
Whidbey General Hosptial purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Mahaska County Hospital had a data breach in 2010, in Iowa. Two patient-orders coordinators were fired for separate incidents of snooping. One inappropriately accessed at least two patients data. The other employee inappropriately accessed the data of multiple family members. [source]. | |
Willapa Harbor Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Manhattan Veterans Affairs Medical Center, New York Harbor Health Care System had a data breach in 2006, in New York. On Sept. 6, an unencrypted laptop computer containing veterans names, Social Security numbers, and medical diagnosis, was stolen from the Hospital. Veterans who receive pulmonary care were affected. (1600 records involved) [source]. | |
Yakima Regional Medical & Cardiac Center purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Mankato Clinic had a data breach in 2010, in Minnesota. A laptop was stolen from the car of a registered nurse sometime between November 1 and 2. It contained a spreadsheet with patient names, dates of birth, medical record numbers, health provider names and diagnosis information. Patients were notified in late December because it took nearly two months to notify patients because the Clinic was determining what was on the laptop. [source]. | |
Yakima Valley Memorial Hospital purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Manor Care of Indy (South), LLC had a data breach in 2010, in Indiana. The protected health information of 845 individuals may have been viewed or obtained by an unauthorized person or persons. [source]. | |
Yale New Haven Health System purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Marian Medical Center had a data breach in 2009, in California. Recent patients of the emergency room and Urgent Care Center have been alerted that a Blackberry containing patient information was stolen from the hospital. The Blackberry contained an email message that included patient information, such as Social Security numbers, dates of birth and medical histories. (3200 records involved) [source]. | |
York Hospital purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Martin Luther King Jr. Multi-Service Ambulatory Care Center had a data breach in 2010, in California. A janitor removed 14 boxes of patient records and sold them to a recycling center. The records had names, genders, dates of birth, addresses, medical record numbers and financial batch numbers. Patients who received services from the outpatient facility between January and October of 2008 were affected. The files were discovered missing on July 29 of 2010 and the custodial worker admitted to selling them. The custodian is being charged with one count of felony commercial burglary. Those affected will be mailed notifications during the week of September 20 of 2010. [source]. | |
21st Century Oncology had a data breach in 2016, in Florida. 21st Oncology notified individuals of a data breach of patient information via unauthorized access to their database. The information compromised included names, Social Security numbers, physician's name, diagnosis and treatment information, and insurance information. The company is offering Experian's Protect My ID to those who were affected. [source] | Academy of Art University had a data breach in 2016, in California. Academy of Art University suffered a data breach when hackers posing as an executive at the university asked for employee W2 information.The information compromised included names, residential addresses and Social Security numbers. [source] | |
Affy Tapple, LLC dba Affy Tapple had a data breach in 2017, in Illinois. Names, addresses, payment card information was compromised via unauthorized access. [source] | Albertina Kerr Centers had a data breach in 2014, in Oregon. The Albertina Kerr Centers have notified individuals of a breach when two of their laptop computers and a cell phone were stolen from the Albertina Kerr's campus. The laptops contained medical information identifying individuals, the diagnoses they received and treatements applied. The theft took place in August of 2014 when an individual or individuals broke into one the facilities offices at the Kerr's crisis psychiatric care facility. According to the facility these laptops did not contain Social Security numbers or financial information. The center is offering a year of free identity theft security monitoring. [source] | |
AltaMed Health Services had a data breach in 2014, in California. AltaMed Health has notified patients of a data breach when a temporary employee and other individuals were reported to be under investigation for an identity theft scheme, according to Arcadia law enforcement agents. No arrests have been made currently, but the investigation is continuing."Law enforcement disclosed it recovered a hard drive and other evidence during its investigation, that this hard drive and evidence may include the organization’s records, and that it believes this information may have been misused by participants in the identity theft ring currently under investigation". The investigation has shown that this temporary employee accessed electronic and paper records for individuals that attended community events in Orange and Los Angeles counties from October 24, 2013 through June 6, 2014. The temporary employee was hired to help with patient enrollment.The records this person had access to included names, email addresses, telephone numbers, Social Security numbers, provider information, insurance information, dates of birth, and addresses. [source] | American Esoteric Laboratories had a data breach in 2018, in Alabama. A data breach may have resulted in the exposure of the personal and protected health information of patients of a medical lab chain with multiple Alabama locations.American Esoteric Laboratories announced Friday that it had become aware of a "data security incident" that could impact patients' data security.An AEL employees' company-issued laptop was stolen on Oct. 15, the company said in a press release. The laptop may have contained sensitive information about "some AEI patients and their payment guarantors," according to the company.Upon learning of the incident, AEL disabled the affected employee's email account, disabled the stolen laptop's access to its computer network, and reported the laptop theft to the local police," the press release stated.An internal AEL investigation found that a wide range of personal information about patients may have been stored on the laptop, including "names, addresses, Social Security numbers, dates of birth, health insurance information, and/or medical treatment information." [source] | |
American Sleep Medicine had a data breach in 2015, in California. American Sleep Medicine has notified patients of a data breach that has occurred when an external hard drive was stolen from a locked server room at their facility. The hard drive contained patient data from previous sleep studies. The specific information included names, dates of birth, name of referring doctor, name of interrpreting doctor, medical history and sleep study results. According to the facility no Social Security numbers or financial information was on the external hard drive. [source] | Apple Valley Christian Care Center had a data breach in 2014, in California. Apple Valley Christian Care Center has notified individuals of a security breach of their system when a "technical glitch" occurred. The center communicated that the compromised data varied greatly.The information included Social Security numbers, dates of birth, home addresses, dates of stays, Medi-Cal ID numbers, Medicare ID numbers, and/or other insurance information such as Medi-Cal appeals, diagnosis codes, treatment information and medical history. [source] | |
Arkansas Oral Facial Surgery had a data breach in 2017, in Arkansas. A ransomware attack on Fayetteville-based Arkansas Oral Facial Surgery Center has potentially breached the data of 128,000 of its patients.An investigation found the cyberattack occurred between July 25 and 26, and while quickly detected, the virus encrypted x-ray images, files and documents. Fortunately, the patient database was not encrypted.However, hackers managed to infect the data of a small number of patients who visited the provider within three weeks prior to the incident. [source] | Augusta University and Augusta University Medical Center had a data breach in 2017, in Georgia. Augusta University says a phishing attack hit faculty email accounts containing the health information of patients. A spokesperson for A-U confirms less than one percent of patients are impacted by the security breach. Officials say an unauthorized third party broke into the medical faculty email accounts.The breach happened between September 7th and September 9th of last year. In addition to patients’ full names, the e-mail accounts may have contained any of the following patient information: home address, date of birth, Social Security number, financial account information, medical record number, insurance information.Forensics investigators cannot say for sure if any patient information was shared or downloaded. Augusta University says it sent letters to all patients whose information is at risk. [source] | |
Aventura Hospital and Medical Center had a data breach in 2014, in Florida. The information was breached via Desktop Computer . [source] | Aventura Hospital and Medical Center had a data breach in 2015, in Florida. The information was breached via Desktop Computer and Electronic Medical Record. [source] | |
Barrington Orthopedic Specialists had a data breach in 2015, in Illinois. Barrinton Orthopedic Specialists notified patients of data breach when a laptop and EMG machince was stolen from their offices. The information compromised included patient names, dates of birth and EMG results and reports. [source] | Bay Area Children's Association had a data breach in 2016, in California. Bay Area Children's Network notified individuals of a data breach, when an unauthorized person (s) accessed their patient account records. The patient information acquired was due to the result of malware installed sometime in January 2015.The information compromised included names, addresses, telephone numbers, dates of birth, Social Security numbers, medical inurance and health visit information. [source] | |
Bay Area Pain Medical Associates had a data breach in 2014, in California. Bay Area Pain Medical Associates have notified patients of a data breach when several of their desktop computers were stolen. There were approximately 2,780 patients first and last names, number of years the patients had been seen at their practice. The are reporting that the computer data was encrypted and inaccessible, there was an Excel spreadsheet that containing this information that could have possibly been accessed. No Social Security numbers, dates of birth, financial information, contact information or medical information was exposed.The facility is offering 12 months free of AllClearID. [source] | Baylor Regional Medical Center had a data breach in 2014, in Texas. Baylor Regional Medical Center at Plano communicated to patients a data breach that occured when a "phishing" email went out to affiliated physicians. The physicians may have been unaware that is was a "phishing" scam and inadvertently created unauthorized access to their email accounts. The email accounts may have included emails that contained patient information, including names, addresses, dates of birth, or telephone numbers, some clinical information such as treating physician, department, diagnosis, treatment received, medical record number, medications, medical service code or health insurance information and Social Security numbers. [source] | |
Baystate Health had a data breach in 2016, in Massachusetts. [source] | Beachwood-Lakewood Plastic Surgery had a data breach in 2014, in Ohio. Beachwood-Lakewood Plastic Surgery and Dr. Stevem A. Golman, notified patients of a data breach when their office in the Parkway Medical complex were burglarized. The theives stole computer hardware that inlcuded patient information that included names and limited medical information.[source] | |
Berkeley Medical Center had a data breach in 2017, in California. A Berkeley Medical Center employee has been discovered to have inappropriately accessed the electronic protected health information of more than 7,400 patients over a period of 10 months.WVU Medicine University Healthcare discovered the inappropriate accessing of ePHI by an employee of the Berkeley Medical Center on January 17, 2017 after being alerted to potential data theft by law enforcement. A joint investigation into the employee had been conducted by the FBI and the Berkeley County Sheriff’s Department.As soon as WVU Medicine University Healthcare became aware of the incident, an internal investigation was launched. Two days later, the employee was suspended pending the outcome of the investigation. Information provided to the healthcare provider from law enforcement linked the employee with 113 former patients who had suffered identity theft.The healthcare worker had been employed by WVU Medicine University Healthcare since March 2004 and was required to schedule appointments for patients at both the Berkeley Medical Center in Martinsburg, WV and Jefferson Medical Center in Ranson, WV. The investigation revealed that the inappropriate accessing of medical records first occurred on March 1, 2016. Inappropriate access continued until the notification was received by law enforcement.No evidence was uncovered to suggest that the employee copied ePHI onto a portable device, although Teresa McCabe, vice president of marketing and development, said the employee manually copied data from computer screens and removed that information from the premises. A link between 113 patients and the employee was found, although in total, 7,445 breach notification letters were sent to patients informing them of unauthorized ePHI access. [source] | Bezop had a data breach in 2018, in California. On Mar 30, researchers at Kromtech Security identified a database open to the public containing full names, addresses, email addresses, encrypted passwords, wallet information, along with links to scanned passports, driver's licenses, and other IDs for over 25,000 investors of the newly created Bezop. The information was found within a MongoDB database without any security.John Mcafee, an adviser on the board for Bezop, described Bezop as “a distributed version of Amazon.com” in a recent Twitter post. It is that, but it's also a cryptocurrency. Bezop is adding, and has in fact already added, it's own cryptocurrency, which they call “Bezop tokens”, into the stream of transactions. [source] | |
BioReference Laboratories, Inc./CareEvolve, Inc. had a data breach in 2014, in Michigan. CareEvolve Inc, a subsidiary of BioReference Laboratories, Inc. have notified patients of a data breach to their system that may have inadvertently exposed personal information of patients. CareEvolve, Inc. was reconfiguring a test server and accidentally exposed the server, making it accessible via the Internet. This particular server included patient names, home addresses, telephone numbers, ages, patient/medical record numbers, clinical tests, collection dates, dates of birth and Social Security numbers (196 SSN's exposed according to CareEvolve Inc). Automated search engine data mining applications did access this information starting on February 2, 2014 and ended when the breach was discovered on March 19, 2014. [source] | BJC HealthCare Raising St. Louis had a data breach in 2017, in Missouri. BJC HealthCare Raising St. Louis recently became aware of a data breach potentially impacting 644 current and former Raising St. Louis participants, according to a recent post on the healthcare organization’s website.On January 9, 2017, BJC Raising St. Louis became aware of an incident in which sensitive patient information was left potentially vulnerable in a series of unencrypted email exchanges between participating program partners.Upon discovering the security breach, BJC staff went through its required protocol for emailing data securely to mitigate further issues.After an investigation, BJC confirmed no unauthorized individuals read or accessed the unencrypted emails at any time. Additionally, the healthcare organization determined no Social Security numbers or financial information were contained within the emails.In an effort to avoid similar incidents in the future, BJC intends to re-educate staff members on the proper way to send securely encrypted emails and have notified potentially impacted participants of the event. [source] | |
BJC Healthcare had a data breach in 2017, in Missouri. The information was breached via Email. [source] | Boston Baskin Cancer Foundation had a data breach in 2015, in Tennessee. Boston Baskin Cancer Foundation notified individuals of a data breach when a laptop computer and external hard drive were stolen. The hard drive contained personal information of patients. The information included patient names, dates of birth, Social Security numbers, addresses, phone numbers, clinic medical record numbers and the last dates seen by the clinic. [source] | |
Boulder Community Health had a data breach in 2014, in Colorado. [source] | Brian D. Halevie-Goldman, M.D. had a data breach in 2016, in California. On July 19, 2016 two laptop computers belonging to the medical offices of Dr. Brian Halevie-Goldman were stolen. The laptops were password protected, secured in a carrying case and locked inside a vehicle when the theft occurred. It is not known whether the information contained on the laptops was or will be accessed by the thief. It is possible that the laptops themsleves and not the information they contained were the target of the thief.The information compromised included names, birthdate and patient charts. [source] | |
BroadSoft had a data breach in 2017, in Maryland. Time Warner Cable, now known as Spectrum, became the latest company to realize exactly how vulnerable its data is when a third-party vendor entrusted with its safety made an error exposing millions of records.Kromtech Security Center researchers discovered late last week that about four million Time Warner customer records were exposed when it found two cloud-based AWS S3 buckets, connected to software and service provider BroadSoft, open to the public. The information compromised spanned the period from November 10, 2010 to July 7, 2017, and included transaction numbers, MAC numbers, user names, account numbers types of service purchased along with internal development information like SQL database dumps and code with login credentials, Kromtech said. [source] | Bronx Lebanon Hospital Center had a data breach in 2017, in New York. Medical records of at least 7,000 people compromised in a data breach involving Bronx Lebanon Hospital Center in New York disclosed patients' mental health and medical diagnoses, HIV statuses and sexual assault and domestic violence reports, according to records reviewed by NBC News.Other information in the compromised records, which online security experts said spanned 2014 to 2017, included names, home addresses, addiction histories and religious affiliations.Bob Diachenko, a security researcher with MacKeeper Security Research Center, told NBC News on Tuesday the leak was caused by a misconfigured Rsync backup server hosted by iHealth, a Louisville, Kentucky-based company that offers records management technology.It's unclear how long the records were exposed, but if you visited BLHC during that period of time, your patient history was probably there, Diachenko said. [source] | |
California Pacific Medical Center/Sutter Health had a data breach in 2015, in California. The information was breached via Email. [source] | California Pacific Medical Center had a data breach in 2015, in California. California Pacific Medical Center through an audit discovered that one its employees accessed medical records of 13 coworkers. A subsequent audit showed that this same employee accessed records of an additional 845 individuals. The information compromised included patient demographics, last four digits of a Social Security numbers, clinical information about diagnoses, clinical notes, physician order information, laboratory and radiological data, and prescription information. [source] | |
Cameron County had a data breach in 2017, in Texas. [source] | Cardon Outreach had a data breach in 2016, in Texas. A health care revenue company says one of its employees looked at nearly two dozen patient records without authorization.Cardon Outreach does contract work for AnMed Health, and has employees on site at the hospital. AnMed said in a release that a Cardon Outreach employee opened 22 patient files without authorization, including her own file.Cardon Outreach fired the employee immediately after learning of the breach, according to the release. [source] | |
Carite Inc. had a data breach in 2018, in Michigan. [source] | Catalina Post-Acute and Rehabilitation had a data breach in 2017, in Arizona. [source] | |
Catholic Charities of the Archdiocese of Galveston-Houston had a data breach in 2016, in Texas. The information was breached via Network Server. [source] | Cedars-Sinai Medical Center, Los Angeles had a data breach in 2014, in California. [source] | |
Central City Concern had a data breach in 2014, in Oregon. Central City Concern in Oregon suffered a data breach when an unauthorized access resulted in the breach of clients data. "On April 2, 2014, a federal law enforcement official notified Central City Concern that a former Central City Concern employee has been accused of improperly copying information from approximately 15 Central City Concern clients from its Employment Access Center (EAC) program with the intent of processing fraudulent tax returns in their names". The information breached included names, dates of birth, Social Security numbers, addresses, and health information of EAC clients. [source] | Central Dermatology Center had a data breach in 2014, in North Carolina. The information was breached via Network Server. [source] | |
CertifiKid LLC had a data breach in 2016, in District Of Columbia. On March 25, 2016, CertifiKid discovered malicious software code that was inserted by unknown individuals into the server of its e-commerce website between the dates of January 25, 2016 and March 19, 2016.The information compromised included names, credit card numbers, expiration dates and security code information. [source] | CFG Community Bank had a data breach in 2017, in Maryland. The information was breached via Electronic Medical Record. [source] | |
CHI Franciscan Health St. Clare Hospital and St. Joseph Medical Center had a data breach in 2016, in Washington. The information was breached via Electronic Medical Record . [source] | Children's Hospital of Los Angeles had a data breach in 2017, in California. The covered entity (CE) reported that a hard drive was missing that contained approximately 1,800 hours of voice recordings that were communications between dispatchers and medical staff prior to or during medical transport between September 18, 2014, and June 3, 2015. The hard drive was not searchable without a separate application and many of the recordings did not contain protected health information The hard drive was missing from the CE's locked, secure area. The breach affected 7,664 individuals and included clinical and demographic information. The CE provided breach notification to HHS, affected individuals, and the media. Upon discovery of the breach, the CE installed a security camera in the area the hard drive was located, ceased storing back-up transport voice recordings on a mobile device, encrypted all mobile devices, and retrained staff. OCR obtained documentation that the CE implemented the compliance actions listed. [source] | |
Claremont University Consortium had a data breach in 2016, in California. The information was breached via Laptop. [source] | Community Hospital of Bremen had a data breach in 2018, in Indiana. On 1/17/2018, suffered a breach affecting 115 records. Acquired information includes SS numbers and names. [source] | |
Complete Medical Homecare had a data breach in 2014, in Kansas. The information was breached via Portable Electronic Device. [source] | Cone Health had a data breach in 2014, in North Carolina. Cone Health notified patients to a data breach when after letters sent from one of its facilities were addressed to the wrong patients. The information on 2,076 patients included names, Social Security numbers, dates of birth and insurance information. [source] | |
Cornerstone Health Care had a data breach in 2014, in North Carolina. Cornerstone Health Care reported a laptop containing information for 548 patients was stolen from Cornerstone Neurology sometime between December 31, 2013 and January 6, 2014. The laptop contained protected health information such as patient names, dates of birth, physician names and nerve conduction scan summaries. The laptop did not contain any addresses, billing information, or Social Security numbers. The laptop was not connected to their third party billing company or their electronic health records. Since the theft the medical practice has revised its procedures and policies, retrained the staff on securing patient information and replaced locks on rooms with electronic medical devices. [source] | Cottage Health had a data breach in 2015, in California. Cottage Health is notifying patients of a data breach when the personal health information was exposed inadvertently online from October 26, 2015 to November 8, 2015. The information included patient and/or guarantor names, addresses, Social Security numbers, health insurance information and account numbers. Some medical and diagnosis information was also exposed. The breach affects the following affiliated hospitals in the healthcare system:- Goleta Valley Cottage Hospital- Santa Ynez Valley Cottage Hospital- Santa Barbara Cottage HospitalThe healthcare company is providing 12 months free of single- Bureau Credit Monitoring through TransUnion credit bureau.For those with questions call 1-877-866-6056 Monday through Friday 6 am- 6 pm Pacific Time. [source] | |
Cuddl Duds (Komar & Sons, Inc) had a data breach in 2016, in New Jersey. Name, address, ssn, financial info. [source] | Deconess Hospital had a data breach in 2017, in Indiana. On 12/08/2017, as a result of insider wrong-doing, Deaconess Hospital suffered a breach that resulted in the exposure of 4 records including Social Security numbers. [source] | |
Denton Heart Group had a data breach in 2017, in Texas. [source] | Detroit Medical Center-Harper University Hospital had a data breach in 2014, in Michigan. A former Detroit Medical Center-Harper University Hospital employee was found with the personal information of 1,087 patients by West Bloomfield police. The documents included patients health information, names, dates of birth, reasons for patient visits and Social Security numbers.When the hospital learned of the breach they immediately revoked the employee's access to its computer systems and all of the Detroit Medical Center hospitals.For patients that were affected they can call 1-855-830-9731 with questions. [source] | |
Dignity Health St. Joseph's Hospital and Medical Center had a data breach in 2017, in Arizona. [source] | Division of Adult Institutions Folsom State Prison had a data breach in 2016, in California. [source] | |
Dr. Arturo Tomas had a data breach in 2015, in Illinois. On February 2, 2014, Arturo D. Tomas, MD LTD's office, the covered entity (CE), discovered that a package containing the protected health information (PHI) of approximately 680 individuals had been lost in the process of shipment to its billing company through the U.S. Postal Service (USPS). The PHI included individuals names, addresses, phone numbers, dates of birth, referring physician names, medical record numbers, diagnoses, and clinical information. [source] | Dr. Hal Meadows had a data breach in 2016, in California. On July 27, 2016, Dr. Meadows found that his patient file had been unlawfully accessed. The patient file contained information used for billing, which included: Names and addresses, birth dates, telephone numbers, insurance numbers, treatment codes, billing information. [source] | |
Dr. Robert E. Soper M.D had a data breach in 2015, in California. Dr. Robert Soper's office notified patients of a data breach when the doctors laptop was stolen out of his car when visiting San Francisco. The computer contained patient names, dates of birth, some phone numbers, and clinical notes and emails. According to the doctor no addresses, Social Security numbers or insurance information was stored on this laptop. Additionally, " the clinical notes were protected by two passwords, and were maintained in a format unique to the software used to prepare them. The software program itself was not on the computer, making the data almost impossible to decipher." [source] | Earbits.com had a data breach in 2016, in California. [source] | |
East Bay Perinatal Medical Associates had a data breach in 2015, in California. The information was breached via Network Server. [source] | East Valley Community Health Center, Inc. had a data breach in 2016, in California. [source] | |
eHealth Insurance had a data breach in 2017, in California. On January 20, 2017, we learned that one of our employees had received a phishing email, which the employee mistakenly believed to be legitimate email from an eHealth executive. As a result of the phishing email, copies of 2016 employee W-2 forms were provided before we discovered that the request was made from a fraudulent account. Since we discovered this incident, we have been working to investigate the mitigate its potential impact. What Information Was Involved? A file containing a copy of your IRS Tax Form W-2, was sent in response to the fraudulent email. An IRS Tax Form W-2 includes the following types of information (1) the employee's name; (2) the employee's address; (3) the employee's Social Security number; and (4) the employee's wage information. No other types of information, such as a bank account information or credit card information, were exposed. [source] | Emergence Health Network had a data breach in 2015, in Texas. Emergence Health Network has notified patients of a data breach to their system when a server was accessed without authorization. \"It is not apparent that any medical information was disclosed based upon a third-party audit of the computer server and EHN does not have any proof that information such as social security number, date of birth, home address, was accessed or otherwise misused\" [source] | |
Emory Dialysis Center, part of Emory Clinic had a data breach in 2014, in Georgia. An employee of Emory Dialysis Center, notified the center that his work laptop had been stolen out of his car on February 7, 2014.The laptop was protected by a password but was not encrypted. The laptop contained information for 826 patients which included dates of services, blood flow test graphs, first and last names for approximately half of the patients, the rest were the patients initials. They center has stated that the laptop did not contain dates of birth, addresses, billing information or Social Security numbers.HSM (Health Systems Management) who runs the clinic is now password protecting all laptops and encrypting patient information. [source] | Empathia Inc had a data breach in 2016, in Wisconsin. Name or other personal identifier in combination with SSN and Driver's license number or non-driver ID number for one Maine citizen breached. [source] | |
Engle Martin & Associates had a data breach in 2018, in Georgia. Engle Martin & Associates suffered a breach affecting 2508 records, including account # and SSN. [source] | Epic Games Forums had a data breach in 2016, in North Carolina. Epic Games has temporarily shut down some of its user forums for maintenance after data on about 808,000 accounts was stolen, marking the second data breach of the game maker in 13 months.The compromise involved several forums maintained by Epic Games, based in Cary, N.C., that center on games and developer tools.The most affected forums are Infinity Blade, UDK, Gears of War archives and those for previous Unreal Tournament games. Email addresses, hashed and salted passwords and data entered into forums were leaked.[source] | |
Episcopal Health Services Inc. d/b/a St. John's Episcopal Hospital had a data breach in 2015, in New York. OCR opened an investigation of the covered entity (CE), Episcopal Health Services Inc., d/b/a St. John’s Episcopal Hospital, after it reported that its business associate's (BA) employee sold 509 patients' data to unknown persons. The protected health information (PHI) included patients' names, addresses, dates of birth, gender, email addresses, social security numbers, account numbers, dates of service, medications, insurance information, diagnoses, billing codes, and reasons for treatment. The BA, Zotec Partners, LLC, d/b/a Medical Management LLC, also filed a separate breach report. As a result of the breach, the BA transitioned to an improved billing system that offers more security controls, implemented software for tracking and monitoring access and user activity, and masked social security numbers from employees whose job duties do not require full access. In addition, the BA conducted updated training on the Privacy and Security Rule standards for all employees. OCR obtained assurances for this case that the BA implemented the corrective actions noted above and also opened a separate investigation of the BA. [source] | E-Pro Tax Service, Emory Healthcare had a data breach in 2011, in Illinois. An investigation into a few stolen Social Security checks that had been fraudulently deposited into Duluth banks uncovered three separate identity theft rings. At least six conspirators managed to defraud 5,779 people. A former real estate broker created a tax service company in order to access credit reports from a third-party credit reporting agency. Names, dates of birth and Social Security numbers were exposed. The former real estate agent then made about $2.5 million by stealing Social Security checks, filing 393 fraudulent tax returns and passing counterfeit checks. After police linked her to the stolen Social Security checks, they searched her home and found boxes of financial documents which included old mortgage applications, tax forms and HUD documents. Investigators have not charged any other conspirators and do notbelieve that the woman was the head of the operations. [source] | |
E-Sports Entertainment Association (ESEA) had a data breach in 2017, in Berlin. E-Sports Entertainment Association (ESEA), one of the largest competitive video gaming communities on the planet, was hacked last December. As a result, a database containing 1.5 million player profiles was compromised.On Sunday, ESEA posted a message to Twitter, reminding players of the warning issued on December 30, 2016, three days after they were informed of the hack. Sunday’s message said the leak of player information was expected, but they’ve not confirmed if the leaked records came from their systems. [source] | Florida Hospital Medical Group had a data breach in 2016, in Florida. [source] | |
For the Inspiration and Recognition of Science and Technology had a data breach in 2017, in New Hampshire. [source] | Friedman & Perry, CPA's had a data breach in 2017, in California. Names, dates of birth, telephone number(s), addresses, social security numbers, employment (W-2) information, and 1099 information was compromised via a hacking incident. [source] | |
Ginger Blossom had a data breach in 2015, in Massachusetts. The owner of a Chines restaurant called the Ginger Blossom discovered that one of her employees stealing customer credit and debit card information. The employee was caught on surveillance video with a skimming device. The police recovered a bag that was hidden in a planter outside of the restaurant that contained the scanner and numerous pre-pad gift cards and credit cards. [source] | GOLFTEC had a data breach in 2017, in Colorado. [source] | |
Great America PAC had a data breach in 2016, in Virginia. [source] | Greensboro Gynecology Associates had a data breach in 2008, in North Carolina. A backup tape of patient information was stolen from an employee who was taking the tape to an off-site storage facility for safekeeping. The stolen information included patients names, addresses, Social Security numbers, employers, insurance companies, policy numbers and family members. [source] | |
Hamilton Zanze Real Estate Investments had a data breach in 2017, in California. [source] | Harrisburg Endoscopy and Surgery Center had a data breach in 2017, in Pennsylvania. A doctor's office in Dauphin County is notifying patients of a potential records breach.Harrisburg Endoscopy and Surgery Center on Union Deposit Road says it's just precautionary and a cyber forensics team didn't find evidence that information was stolen.The data that could be affected includes names, addresses, birth date and health information. [source] | |
HealthSouth Rehabilitation Hospital had a data breach in 2015, in Texas. HealthSouth Rehabilitation Hospital of Round Rock put out a notification on their site regarding a data breatch after a laptop was stolen."HealthSouth Rehabilitation Hospital of Round Rock, previously Reliant Rehabilitation Hospital Central Texas, is currently notifying potentially affected individuals that a laptop containing unsecured protected health information was stolen from the trunk of an employee’s vehicle on or around Oct. 21, 2015. The information on the laptop varied by individual but may have included an individual’s name, address, date of birth, Social Security number, phone number, insurance number, diagnosis, referral ID number or medical record number. At this time, the hospital is working to notify the 1,359 potentially affected individuals via letter." [source] | Heartland Health Clinic had a data breach in 2015, in Virginia. [source] | |
Highlands-Cashier Hospital had a data breach in 2014, in North Carolina. [source] | Hillsides had a data breach in 2015, in California. Hillsides is notifying individuals of a data breach when an employee send internal files that included personal information on both employees of the organization and patients of the organization.The information included names, hiring dates, job titles, division descriptions, Social Security numbers, home addresses, zip codes and home phone numbers. In some instances the emails also included therapists names, Integrated System numbers, stard dates for services, outcome dates, parent partner names, names of rehabilitation specialists, rehab clinics, and gender. [source] | |
Hilton/Hilton Honors Program had a data breach in 2014, in Virginia. Hilton HHonors is at the center of a security crisis. According to reports and testaments from FlyerTalk readers, hackers are finding their way into HHonors member accounts, stealing points, and using registered credit cards to make unauthorized purchases of more points and hotel stays.One of the worst incidents so far involved a Canadian man, Brendan Brothers. According to a report from Krebs on Security, a security and cybercrime news site run by former Washington Post staffer Brian Krebs, Brothers’ account was hacked in the last week of September. Brothers claims the hackers stole about 250,000 points and used his account to redeem hotel stays on the east coast. Brothers’ stored credit card was then allegedly used to purchase more rewards points. [source] | Hollywood Presbyterian Hospital had a data breach in 2016, in New York. Hollywood Presbyterian Hospital paid $17,000 in bitcoin in order to retrieve records they held for ransom against the hospital. The hackers installed a malicious ransomware on their server to hold patient records hostage so the hospital staff could not access any record. [source] | |
Home Box Office (HBO) had a data breach in 2017, in New York. The information was breached via Laptop. [source] | Hospital for Veterans Affairs, Denver had a data breach in 2014, in Colorado. [source] | |
Houston Astros had a data breach in 2015, in Texas. [source] | Hunt Regional Medical Partners had a data breach in 2015, in Texas. Vandals broke into a building storing paper protected health information (PHI) for the covered entity (CE), Hunt Regional Medical Partners. The types of PHI involved in the breach included patients' names, addresses, dates of birth, Social Security numbers, claims information, and patients' chart information. Approximately 3,000 individuals were affected. [source] | |
iDressup.com had a data breach in 2016, in California. [source] | Indiana University Health Arnett Hospital had a data breach in 2016, in Indiana. Indiana University Health Arnett Hospital notified patients of a data breach when the hospital became aware of a missing unencrypted flash drive from their emergency department. The information compromised included patient information from emergency department visits, names, dates of birth, ages, home telephone numbers, medical record numbers, dates of service, diagnoses and treating physicians. [source] | |
Indiana University Health Arnett Hospital had a data breach in 2016, in Indiana. Tens of thousands of subscriber accounts for media company Infowars are being traded in the digital underground.Infowars, created by famed radio host and conspiracy theorist Alex Jones, produces radio, documentaries and written pieces. The dumped data relates to Prison Planet TV, which gives paying subscribers access to a variety of Infowars content. The data includes email addresses, usernames, and poorly hashed passwords.The administrator of breach notification site Databases.Land provided a copy of 100,223 records to Motherboard for verification purposes. Vigilante.PW, another breach notification service, also has the Infowars dump listed on its site, and says the data comes from 2014. However, every record appearsto have been included twice in the data, making the actual number ofuser accounts closer to 50,000. [source] | Jamaica Hospital Medical Center had a data breach in 2014, in New York. The information was breached via Desktop. [source] | |
Jemison Internal Medicine, PC had a data breach in 2017, in Alabama. The information was breached via Network Server. [source] | Jessie Trice Community Health Center had a data breach in 2014, in Florida. Jessie Trice Community Health Center announced a data breach when members of an identity theft ring accessed the personal information of 8,000 patients.The informaton accessed included names, dates of birth and Social Security Numbers. No medical information was compromised according to the facility. The FBI and the IRS are currently investigating the breach. [source] | |
Jive Software/Producteev had a data breach in 2016, in California. [source] | Joan Jett's BlackHeart Records had a data breach in 2016, in California. This week legendary rocker and Rock and Roll Hall of Fame Member Joan Jett had an unfortunate reminder of how important cyber security and data protection is in today’s digital world. On Dec 1st the MacKeeper Security Research Center discovered Joan Jett’s BlackHeart Records leaking hundreds of gigabytes of data online. BlackHeart Records is an Independent label founded by Joan Jett and Kenny Laguna and has a good reputation as an established label with a range of well known artists.The data breach is a massive treasure trove for fans and cyber criminals alike. There are unreleased tracks, never before seen pictures, even rejection letters from 1980 when Joan Jett was trying to get a record deal. There are also social security numbers of label employees and band members, internal memos and scanned checks of royalty payments and much more.From the entertaining obsessed fan emails to lawsuits and arrest records of the label manager, this database is a look inside of how the record label is operated and the communication between rock and roll royalty.Although there are no naked pictures or Hollywood style tabloid drama in the hundreds of gigabytes and countless thousands of files, there is a complete view of the many aspects of being a famous rockstar, operating a record label, and the meticulous documentation of every achievement, failure, or internal and external communications. [source] | |
John D Williamson had a data breach in 2017, in California. [source] | John E. Gonzalez DDS had a data breach in 2016, in California. [source] | |
Kaiser Permanente Northern California Division of Research had a data breach in 2014, in California. Kaiser Permanente's Northern California Division of Research informed research patients of a data breach to their system. The company discovered that a server was infected by a malicious software that caused a breakdown in the server's security barriers allowing the hackers to obtain personal information. The information included firs names, last names, dates of birth, ages, genders, addresses, race/ethnicities, medical record numbers, lab results all associated with research provided by individuals as part of research studies.Currently the company has stated that no Social Security numbers or their Kaiser electronic medical record information used for ongoing medical care was not affected. [source] | Kaleida Health had a data breach in 2017, in New York. Kaleida Health, New York’s largest provider, is once again notifying patients of a phishing incident. This one involves 744 patients.The organization discovered the incident on June 26, when it found an unauthorized third-party gained access to an employee’s email account. Officials said that after an investigation, the hacker was able to access a “small number of Kaleida Health email accounts.”Included in those accounts were patient names, medical record number, diagnoses, treatment information and other clinical data. For some patients, it also included Social Security numbers. Officials said the financial information wasn’t included. [source] | |
Keck Medical Center of USC had a data breach in 2016, in California. On February 16, 2011, an IT incident caused patient information to be exposed. It is not known if the breach resulted from a hack or an accidental release of information. The type of patient information exposed was not revealed. [source] | Kevin Harrington, CPA had a data breach in 2017, in California. On November 11, 2016, I detected that someone may have accessed my computer without authorization. I immediately informed my information technology provider and disabled online access to my computer. I immediately began an investigation, and on November 18, 2016, the information technology firm confirmed that someone accessed client files on my computer without authorization. I immediately notified the Internal Revenue e-File Services Department, the Internal Revenue Service/Criminal Investigation, and the California Franchise Tax Board to prevent any fraudulent activity. Although I am not aware of any fraudulent use of information associated with the event, I encourage you to utilize the services referenced below to monitor your personal information.What Information Was Involved? The following information appears to have been accessed: tax return information which included names, addresses, dates of birth, and Social Security numbers. [source] | |
Kimberly-Clark had a data breach in 2017, in Wisconsin. [source] | La Quinta Center for Cosmetic Surgery had a data breach in 2014, in California. [source] | |
Lafler, Moore, Connerty & Webb, LLP had a data breach in 2016, in California. On March 11, 2016, an employee was on a work computer when unusual cursor behavior was observed. The computer was immediately taken off-line and our IT consultant was contacted. The consultant confirmed suspicious activity and changed potentially impacted passwords. That same day, a forensic data analysis company was also hired to investigate and determine what, if any, information was breached. On April 8, 2016, we learned with a high level of confidence that information on our network was breached by an unauthorized individual starting on or about January 27, 2016, and who was potentially impacted.The information compromised included names, gender, dates of birth, telephone numbers, addresses, social security numbers, all employment (W-2) information, a bank account and routing numbers, mortgage documentation, charitable contributions, casualty and theft losses, investment information, health coverage documentation, and medical expenses. [source] | LendKey Technologies, Inc. had a data breach in 2018, in New York. LendKey Technologies, Inc. suffered a breach affecting 6403 records, including Account Numbers, Driver's Licenses, and SSN. [source] | |
Livestream had a data breach in 2015, in New York. Live video streaming platform Livestream has discovered that an unauthorised person may have accessed its customer accounts database.The database holds information such as a user's name, email address, an encrypted version of their password, as well as phone numbers and the customer's date of birth. [source] | Long Beach Internal Medical Group had a data breach in 2014, in California. Name, address, ssn, and w2 tax info were breached. [source] | |
LSU Health New Orleans School of Medicine had a data breach in 2015, in Louisiana. A doctor associated with the LSU Health New Orleans School of Medicine had his laptop stolen which may have exposed 5,000 patients personal information.The laptop computer was stolen from the doctors vehicle when it was parked in front of his home on July 16th or 17th. The theft was reported but has not yet been recovered.The information contained on this laptop included names, dates of birth and medical information. It did not contain Social Security numbers, credit card or banking information. [source] | Lucile Packard Children's Hospital had a data breach in 2013, in California. Between May 2 and May 8, a non-functional laptop computer was stolen from a secured area of the hospital. The laptop was password protected and contained names, ages, medical record numbers, telephone numbers, scheduled surgical procedures, and names of physicians involved in procedures between 2009 and 2012. [source] | |
Luque Chiropractic, Inc. had a data breach in 2016, in California. Dozens of boxes of files from medical offices that hired LV to collect unpaid bills were found in an Orlando public dumpster. The files contained names, addresses, Social Security numbers, drivers license copies and credit reports. The collection agency went out of business in 2005 and the location of the files prior to this incident is unknown. [source] | ManagedMed Inc (A Psychological Corporation) had a data breach in 2014, in California. ManagedMed Inc.(A Psychological Corporation) notified patients and the Attorney General's office of a data breach of their patient scheduling system. According to the facility patient scheduling information was viewed via an unsecured webpage by at least two non-ManagedMed individuals. This information was visible from March, 2013 through May 15, 2014. The breach allowed unauthorized persons to access the facilities calendaring system and view the information. This information included patient scheduling information, patient names, telephone numbers, names of providers, notes on the patient which could have included information on the type of visit scheduled or medication/test scheduled for the patient, and dates of appointments. According to the facility no SSN's, credit card or medical records information were exposed. [source] | |
Marin Medical Practice Concepts had a data breach in 2016, in California. Marin Medical Practice Concepts, a Novato company that provides medical billing and electronic medical records services to many Marin physicians, had its computer system hacked and paid a ransom to regain access to its own data. There is no evidence that any patient data were compromised, according to a company official.As a result of the security breach, many Marin doctorrs have been unable to access patients' electronic medical records for more than a week. [source] | Mary Washington Hospital had a data breach in 2008, in Virginia. A security breach in an online computer system exposed the private medical information of some of its maternity patients. Social Security numbers, phone numbers, address, insurance carrier, birth dates and doctors names were exposed. [source] | |
Massachusetts eHealth Collaborative had a data breach in 2011, in Massachusetts. A briefcase was stolen from an employees car during lunch sometime during the spring of 2011. The briefcase contained a company laptop that had not yet been encrypted and paper copies of appointment schedules. The laptop contained the information of patients and providers from 18 practices. A recent backup of the laptop files revealed that 5,338 subscriber numbers, 2,777 names with no other information, and 222 names with associated Social Security numbers, dates of birth, subscriber numbers, and phone numbers had been on the laptop. Seventy of the 222 who had their names, Social Security numbers, dates of birth, subscriber numbers, and phone numbers exposed also had their addresses exposed. [source] | Massachusetts General Hospital had a data breach in 2009, in Massachusetts. Massachusetts General Hospital has put dozens of patients on notice that it has lost some of their confidential medical records, which were left on an MBTA Red Line train by a hospital employee. The MGH employee left the hospital, taking the records with her to do billing work on them over the weekend. The records belonged to at least 66 patients and included private information such as the patients diagnoses, their names, birth dates and billing information.UPDATE(2/24/2011): Massachusetts General Hospital agreed to pay one million dollars to settle violation of privacy charges. UPDATE(6/08/2012): The lost documents consisted of a patient schedule with names and medical record numbers for 192 patients. There were also billing encounter forms with names, dates of birth, medical record numbers, health insurer and policy numbers, diagnoses, and provider names for 66 of those patients. [source] | |
Matson Navigation Company (Horizon Lines) had a data breach in 2015, in Arizona. Name, 1099 tax form were breached. [source] | Mayo Clinic had a data breach in 2010, in Arizona. An employee was fired after it was learned that the employee accessed patient records without authorization. The employee repeatedly accessed information at a location in Arizona between 2006 and 2010, but the Mayo Clinic system allows employees to access patient records from across the country. [source] | |
McAlester Clinic and Veterans Affairs Medical Center had a data breach in 2006, in Oklahoma. Three disks containing billing information, patient names and Social Security numbers, were lost in the mail. [source] | McKesson Specialty, AstraZeneca had a data breach in 2007, in Arizona. McKesson Health-care services company alerted thousands of its patients that their personal information was at risk after two of its computers were stolen from an office. [source] | |
McLaren Medical Group (MMG) had a data breach in 2017, in Michigan. [source] | Med Center Health had a data breach in 2017, in Kentucky. [source] | |
Medcenter One had a data breach in 2011, in North Dakota. [source] | Medical Colleagues of Texas, LLP had a data breach in 2016, in Texas. The information was breached via Network Server. [source] | |
Medical College of Wisconsin had a data breach in 2017, in Wisconsin. The Medical College of Wisconsin has notified thousands of patients their confidential information may have been compromised.The information includes addresses, bank accounts and Social Security numbers.The Medical College has disclosed 9,500 of its patients are now victims of a targeted attack that happened sometime in late July.An unauthorized third party accessed employee email accounts, which contained private patient information such as their date of birth, home address, medical record numbers and diagnosis. [source] | Medical Informatics Engineering had a data breach in 2015, in Indiana. Medical Informatics Engineering has notified individuals of a data breach when they noticed suspicious activity on one of their servers. The company has determined that some protected health information was exposed including names, home addresses, email addresses, dates of birth, Social Security numbers, lab results, dictated reports and medical conditions. ): Medical Informatics Engineering put out a notification on their website regarding the data breach to their system in June. The company is claiming that only certain clients were affected by their breach and notifications went out. Two class action status lawsuits have been filed against Medical Informatics Engineering regarding the data breach that affected 3.9 million people (this article shares the total numbers and PRC has updated the total number affected according to this article). [source] | |
Memorial Health Services, MemorialCare Health System had a data breach in 2011, in California. [source] | Memorial Healthcare System (MHS) had a data breach in 2012, in Florida. On January 27, 2012, MHS learned that at least one employee may have accessed patient information in order to receive fraudulent tax returns. A second employee was later identified and both employees were terminated. Patient names, Social Security numbers, and dates of birth may have been accessed between 2011 and early 2012. Medical information was not involved. Law enforcement requested that MHS delay notifying patients. On April 12, 2012, letters were mailed to patients who may have been affected. [source] | |
Memorial Hermann Hospital had a data breach in 2014, in Texas. [source] | Memorial Hospital Clinic South had a data breach in 2014, in Texas. Memorial Hospital Clinic South reported a breach when computer malware (i.e.,ransomware) was found on its network server. This breach affected the protected health information (PHI) of 842 individuals, and included clinical and demographic information. The specific types of PHI involved in the breach included addresses, birthdates, driver's license numbers, names, social security numbers, diagnoses/conditions, lab results, medications, and other treatment information. This review has been consolidated with another review of this covered entity.[source] | |
Memorial Hospital of Gardena had a data breach in 2010, in California. The information was breached via Paper/Films. [source] | Memorial Hospital had a data breach in 2012, in Colorado. Laboratory reports for about 6,400 patients were discovered missing. The reports contained bill processing information and charges for laboratory services. Patients who had lab work done between May 1, 2012 and August 31, 2012 had their names, Memorial internal account numbers, lab work dates, and types of lab work exposed. [source] | |
Memorial Sloan-Kettering Cancer Center had a data breach in 2012, in New York. A routine check for sensitive information by Memorial Sloan-Kettering revealed that a PowerPoint presentation that was posted on two medical professional websites in 2006 contained embedded private information. The information included patient names, phone numbers, addresses, and in some cases, Social Security numbers. Anyone who accessed and manipulated the PowerPoint presentation could have viewed the information that was used to create certain graphs. A total of five PowerPoint files contained sensitive information. The largest file had data from 568 patients from various states; the second largest contained 112. Three others contained the data of 37, 59, and 112 individuals. [source] | Mercy Medical Center Redding had a data breach in 2016, in California. On June 6, 2016, Dignity Health learned your information was accessed inappropriately. Our business partner, naviHealth employed a person as a case manager who was working under a false name and nursing license. This case manager was employed by naviHealth from June 2015 to May 2016. When naviHealth discovered the problem, it immediately severed ties with the case manager and prevented further computer access. Law enforcement was contacted, and naviHealth is cooperating in the on-going investigation.Unfortunately, the case manager accessed your patient informattion as part of his work. The information accessed includes the following:your standard clinical information, such as diagnosis, lab results, medications, dates of treatment, and provider notes;your individual information, such as name, address, phone number, social security number, date of birth, email, medical record number, account number, dates of service; andyour health insurance account information, such as group health plan number and member ID. [source] | |
Mercy Medical Center had a data breach in 2006, in California. A memory stick containing patient information was found July 18 by a local citizen on the ground at the County Fairgrounds near the hospitals information booth. It was returned to the hospital four weeks later. Data included names, SSNs, dates of birth, and medical records. [source] | Mercy Willard Hospital had a data breach in 2010, in Ohio. A former employee kept patient photographs, videos, memos, schedules, and forms. Some of the documents included patient Social Security numbers and other personal information. The employee is also being accused of voyeurism and possession of child pornography; though this is unrelated to these findings. [source] | |
Methodist Charlton Medical Center had a data breach in 2011, in Texas. The April 16 theft of a laptop resulted in the exposure of patient information. Multiple items were taken during the office burglary. Patients who were part of Methodist Charltons palliative care program between June 6, 2006, and September 30, 2010 were affected. Patient names, ages, sexes, race, marital status, admission and discharge information, hospital account number, physician, insurance company, date of death, chief complaint and type of cancer may have been revealed. Patient religion may have also been exposed. It does not appear that any Social Security numbers were attached to hospital account number or insurance company information. [source] | Methodist Hospital had a data breach in 2010, in Texas. Methodist Hospital notified people that someone stole a laptop from an office at the Smith Tower in the Texas Medical Center. A thief took the laptop on January 18. The computer was attached to a medical device that tests pulmonary function and contained private health information and Social Security numbers. [source] | |
Methodist Hospital had a data breach in 2011, in Texas. [source] | Metropolitan Urology Group had a data breach in 2017, in Wisconsin. The information was breached via Laptop. [source] | |
Mid America Health had a data breach in 2013, in Indiana. The theft of a laptop resulted in the exposure of patient information. Names, Social Security numbers, dates of birth, residential facility names, and digital oral x-ray images may have been exposed. Specific details of the case are being withheld until the breach investigation has concluded. The location of the breach is listed as the corporate headquarters of MAH. [source] | Middlesex Hospital had a data breach in 2015, in Connecticut. Middlesex Hospital has notified patients of a data breach when four of its employees were victims of a phishing scam that enabled hackers to get into hospital records compromising patient information.The information compromised included names, addresses, dates of birth, medical record numbers, medications they took, dates of service and diagnosis. [source] | |
Mid-Florida Urological Associates had a data breach in 2013, in Florida. A dishonest employee misused patient information in order to claim them as her children and receive insurance compensation. The dishonest employee was charged with insurance fraud and ID theft.UPDATE(02/22/2013): Orlando Health patient records were accessed. The Orlando Health hospitals include MD Anderson Cancer Center Orlando, Orlando Regional Medical Center, Winnie Palmer Hospital for Women and Babies, Dr. P. Phillips Hospital, Arnold Palmer Hospital for Children, South Seminole Hospital, South Lake Hospital, and Health Center Hospital. [source] | MidState Medical Center had a data breach in 2011, in Connecticut. A former Hartford Hospital employee misplaced a computer hard drive on February 15. It contained patient names, Social Security numbers, addresses, dates of birth and medical record numbers. Not all of the patients who were affected had their Social Security numbers exposed.UPDATE(04/07/2011): Connecticuts Attorney General and Consumer Protection Commissioner are investigating the breach and data security policies of Hartford Medical Center andMidstate Medical Center. Additional details reveal that the hospital employee misplaced the computer hard drive after taking it home. The Connecticut Attorney General is asking that affected patients receive two years of credit monitoring services, identity theft insurance and reimbursement for placing and lifting security freezes.UPDATE(07/10/2012): The Connecticut Attorney General has decided to end an investigation of MidStates practices. The Attorney General claimed to base his decision to close the investigation with no further action on the fact that the Hospital had taken significant actions on behalf of the affected patients. [source] | |
Midwest Orthopedic Group had a data breach in 2016, in Missouri. The information was breached via Network Server. [source] | Midwest Urological Group had a data breach in 2014, in Illinois. Midwest Urological Group notified patients of a data breach when a laptop was reported stolen when an employee may have inadvertently forgot to lock the cabinet that housed the laptop. According to authorities the laptop contained patient information that included treatment information on the patients at the facility. No specific details were released as to the type of information involved. [source] | |
Midwest Womens Healthcare Specialists had a data breach in 2014, in Missouri. [source] | Mills-Peninsula Medical Center had a data breach in 2011, in California. A relative of a mail room employee discovered sensitive documents at the employees residence and returned them in June of 2011. The employee had taken home medical documents between November of 2009 and September of 2010. The records consisted of patient names and diagnostic test results. Fifteen of the documents included patient addresses and insurance identification or Social Security numbers. The employee was fired. UPDATE (10/22/2011): A total of 1,438 people were affected by the breach. The former employee was charged with embezzlement and forgery. She claims that she was overwhelmed with sorting the documents at work and that she planned to dispose of them properly. [source] | |
Mindlance, Inc. had a data breach in 2017, in New Jersey. On 12/28/2017, Mindlance, Inc. suffered a system breach (hack) that affected 3085 records, including SS numbers and names. [source] | Minor Family Clinic had a data breach in 2010, in Arizona. An insurance fraud scheme used medical information from the Clinic. Fraudulent charges to patients insurance companies totaled $108,000. Two people have been indicted, but their method for accessing patient information has not been reported. [source] | |
Mission Hospital, St. Joseph Health had a data breach in 2013, in California. Name, address, wages, tax and ssn information, DOB, age, gender, ethnicity, visa and passport info were breached. [source] | Molina Healthcare of California had a data breach in 2012, in California. An unauthorized disclosure of paper documents occurred on January 31, 2011. The breach may have affected records that date from September 23, 2009 through October 18, 2011. No further details are available. [source] | |
MolinaHealthcare.com had a data breach in 2017, in California. [source] | Montefiore Medical Center had a data breach in 2015, in New York. The information was breached via Desktop Computer and Electronic Medical Record. [source] | |
Montefiore Medical Center had a data breach in 2010, in New York. A laptop containing private health information was stolen on February 20th. [source] | Montefiore Medical Center had a data breach in 2010, in New York. Name or other personal identifier in combination with SSN for 2 Maine citizens breached. [source] | |
Moore Business Solutions had a data breach in 2018, in North Carolina. The information was breached via Email. [source] | Moores Cancer Center had a data breach in 2009, in California. A hacker breached the Centers computers and gained access to patients personal information. A letter was sent to 30,000 patients informing them that their personal information may have been in the compromised databases. Types of information in breach included names, dates of birth, medical record number, diagnosis and treatment dates and some Social Security numbers. The majority of patients information did not include Social Security numbers. [source] | |
Moses Cone Hospital had a data breach in 2009, in North Carolina. Moses Cone Hospital is offering free credit monitoring to 14,380 patients after a laptop computer containing confidential information was stolen from a VHA employees car. The information on the laptop, including patients Social Security numbers. [source] | Mount Sinai Beth Israel had a data breach in 2014, in New York. Mount Sinai Beth Israel announced a data breach when a laptop computer was stolen from a staff room. According to the facility the laptop was password-protected but not encrypted.The patient information housed on the laptop included patient names, dates of birth, medical record numbers, dates of service, procedure codes and description of procedures along with clinical information about patient care received. The facility has stated that patient Social Security numbers, insurance information, addresses and phone numbers were not stored on this particular laptop. [source] | |
Mount Sinai Hospital had a data breach in 2012, in Florida. Eleven computer screen printouts of personal information and seven credit cards of Mount Sinai patients were found in a vehicle that was searched after a motorist was stopped for reckless driving. An employee of Mount Sinai was linked to patient personal information that was found during the traffic stop. She is was arrested and accused of accessing and printing the names, Social Security numbers, and dates of birth of 340 patients for identity theft purposes. [source] | Mount Sinai Medical Center had a data breach in 2006, in New York. A flash drive that contained visitor names, Social Security numbers, childrens names, childrens dates of birth and dates of visit was lost or stolen during an emergency evacuation. A researcher working with data from New York Childrens Environmental Study conducted in Community Medicine reported that the flash drive she left in her computer was missing after she returned sometime around October 5. [source] | |
Mount Sinai Multispecialty Physicians Practice had a data breach in 2011, in New York. [source] | Mount Sinai School of Medicine had a data breach in 2010, in New York. A hard drive from the World Trade Center Medical Monitoring and Treatment Program at Mt. Sinai Hospital was lost or taken from a computer in the Mental Health Center. The information included emails with protected health information, patients names, and possibly treatment and contact information. [source] | |
Mount St. Mary's Hospital had a data breach in 2006, in New York. [source] | Mountain Medical Center had a data breach in 2009, in Utah. Names, credit card numbers, Social security numbers were found in a dumpster. A man was throwing away some stuff in a dumpster and found it was chock full of medical records. Theres everything in there from canceled checks to routing numbers, he said. Salt Lake Police packed away perhaps twenty boxes of papers, and said they would protect the documents, as they dug into the matter. [source] | |
Mountain Vista Medical Center had a data breach in 2010, in Arizona. On October 13, multiple memory data cards were discovered to be missing from two endoscopy machines. The information of patients who had procedures performed between January of 2008 and October 12 of 2010 was on the data cards. The information included full name, hospital record number, date of birth, gender, age, date and type or procedure and image(s) related to the procedure. [source] | Mrs. Prindables had a data breach in 2017, in Illinois. Names, addresses, payment card information was compromised via unauthorized access. [source] | |
Muir Orthopaedic Specialists had a data breach in 2011, in California. The information was breached via Email. [source] | Multi-State Billing Services had a data breach in 2014, in New Hampshire. Multi-State Billing Services LLC has let 19 school districts that they service, that a laptop that was stolen from an employee's locked vehicle contained records on nearly 3,000 students in 19 different school districts in Central and Eastern Massachusetts. The Central districts include Uxbridge, Ashburnham-Westminster Regional, Milford, Northboro, Northboro-Southboro Regional, Southboro and Sutton. Information on which Eastern school districts is currently unknown.The information on the laptop included names, addresses, Medicaid ID numbers and Social Security numbers. Multi-State Billing will reimburse costs related to security freezes for the next three years.[source] | |
Muskogee Regional Medical Center had a data breach in 2012, in Oklahoma. A binder containing forms with flu test results for 2011 went missing sometime around December 5, 2011. It contained the information of patients who received a flu test between January 1, 2011, and December 5, 2011. patient names, internal hospital department and internal account numbers, gender, medical record numbers, dates of birth, age, dates of tests, and flu test results. [source] | Nakawatase & Kaminsky, CPS's, LLP had a data breach in 2017, in California. [source] | |
National Institutes of Health had a data breach in 2008, in Maryland. A laptop was stolen from the trunk of a car. It contained information about heart disease patients, including their names, dates of birth and diagnoses of their medical conditions. uPDATE (4/14/08): ongoing review of the computers last-known contents, performed on data backed up from the laptop before it was stolen, has found a file that, unbeknownst to the lead researcher, had been loaded onto the laptop by a research associate.That file included Social Security numbers for at least 1,281 of the 3,078 patients enrolled in the multi-year study, which is sponsored by the NIHs National Heart, Lung and Blood institute. [source] | Naval Hospital Pensacola had a data breach in 2009, in Florida. Naval Hospital Pensacola will be notifying thousands of beneficiaries who use its pharmacy services, following the disappearance of a laptop computer. The computers database contains a registry of 38,000 pharmacy service customers names, Social security numbers and dates of birth on all patients that used the pharmacy in the last year. It does not contain any personal health information. [source] | |
NEA Baptist Clinic had a data breach in 2011, in Arkansas. NEAs former public website was compromised by a hacker or hackers on July 12, 2011. People who previously registered with the website in order to use the websites special functions may have had their email addresses and user name and password combinations exposed. Some individuals also had their names, addresses, and dates of birth compromised. Since passwords may have been obtained, individuals who may have been affected should not use their NEA website password for any other accounts. [source] | NEO Tech had a data breach in 2017, in California. On Friday, January 27, 2017, NEO Tech was the victim of an email “phishing” incident that resulted in the release of employee W-2 wage and tax data to an unauthorized email recipient outside the company. This was an isolated incident that did not involve an intrusion into our computer systems or network. What information was involvedThe following NEO Tech employee information: a copy of your 2016 Form W-2, which includes your name, address, 2016 income information and Social Security Number. [source] | |
Neurological Institute of Savannah and Center for Spine (NIOS) had a data breach in 2011, in Georgia. [source] | Nevro had a data breach in 2017, in California. Nevro was recently the victim of a criminal break-in at their corporate headquarters in which several laptop computers were stolen. Nearby businesses were also targeted by the same perpetrators, who stole laptops from those businesses as well. Nevro has been unable to recover the stolen laptops. [source] | |
Nevro had a data breach in 2017, in Ohio. [source] | New Hampshire's Lakes Region General Hospital had a data breach in 2008, in New Hampshire. A package containing personnel medical information on patients is missing. UPS recently shipped the parcel from a Woburn, Mass. central processing agent to the hospital, but the package never arrived. Information contained in the package includes patient names, possible Social Security numbers, dates of service and diagnosis code numbers for different diagnosis or medical procedures. [source] | |
New River Health Association had a data breach in 2011, in West Virginia. The disclosure of sensitive paper records resulted in unauthorized access to personal information. The breach either occurred or was discovered around April 1, 2011. [source] | New York University Langone Medical Center Hospital for Join Diseases (HJD) had a data breach in 2011, in New York. Paper tracking records of tissue issued in orthopaedic surgeries performed at HJD in 2009 and 2010 were mistakenly discarded on or around June 23. It appears that the papers were then compacted and buried in a landfill rather than properly disposed. Patients who were affected had their name, date of birth, gender, hospital, date of surgery, and clinical surgery information exposed. [source] | |
New York University Langone Medical Center, Office of Dr. Eric C. Parker, Office of Dr. Patrick J. Kelly had a data breach in 2012, in New York. [source] | New York University School of Medicine Aging and Dementia Clinical Research Center had a data breach in 2010, in New York. A portable electronic device was lost or stolen on April 3. The health information of 1,200 patients was lost. The incident was reported to the Department of Health and Human Services in September. [source] | |
New York Urology Associates had a data breach in 2010, in New York. [source] | New York-Presbyterian Hospital, Weill Cornell Medical Center had a data breach in 2008, in New York. An admissions employee is accused of selling 2,000 patients data in an identity theft scheme and accessing nearly 50,000 records illegitimately. Records contained names, phone numbers and, in some cases, Social Security numbers of patients. The employee has since been charged with one count of conspiracy involving computer fraud, identity document fraud, transmission of stolen property and sale of stolen property. [source] | |
Newark Beth Israel Medical Center, Professional Transcription Company (PTC), Inc. had a data breach in 2010, in New Jersey. Clinical reports with patient names, medical record numbers, hospital account numbers, physician names, dates of birth, diagnosis and other clinical information were accidentally placed on a website by PTC. It is possible that the reports were accessible from January 1 through September. PTC assists the Medical Center in transcribing dictated physician reports. [source] | Newland Medical Associates had a data breach in 2010, in Michigan. A former employee is accused of stealing patient information and using it to commit identity theft. The former employee is charged with 15 counts of identity theft and criminal enterprise. Investigators believe the employee stole the information of cancer patients and used it to obtain credit cards. [source] | |
Norman Pediactric Associates and Norman Urology had a data breach in 2010, in Oklahoma. Hundreds of intact medical records and Social Security numbers of oncology patients were found at the Norman Recycling Center. Both organizations believe a common paper shredding company is at fault. The files were returned to the organizations and affected patients will be contacted. [source] | North Bay Regional Health Centre had a data breach in 2011, in California. A privacy audit uncovered a breach caused by an employee. The employee accessed health information for persons other than those with whom they provided care. These inappropriate accesses date back to 2004. Only affected patients received a letter notifying them of the breach and offering suggestions for personal security.UPDATE(03/02/2013): The employee was a registered nurse and will receive a hearing in June of 2013. No prosecution has occurred. [source] | |
North Country Health Services had a data breach in 2010, in Minnesota. North Dallas Urogynecology notified patients of a data breach when a laptop was stolen from their offices that contained personal information of patients.No specifics were provided as to what kind of personal information the laptop contained.More information: https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf;jsessionid=9BF4AF... [source] | North Dallas Urogynecology had a data breach in 2015, in Texas. North Dallas Urogynecology notified patients of a data breach when a laptop was stolen from their offices that contained personal information of patients.No specifics were provided as to what kind of personal information the laptop contained.More information: https://ocrportal.hhs.gov/ocr/breach/breach_report.jsf;jsessionid=9BF4AF... [source] | |
North East Medical Services had a data breach in 2015, in California. North East Medical Services notified patients of a security breach when an employees laptop was stolen from the trunk of the employees car. The information compromised included names, dates of birth, gender, contact information, payer/insurer and limited personal health information. According to the medical office no Social Security number or credit card information or actual medical record was involved. [source] | North Lincoln Community Health Center Clinic had a data breach in 2013, in Oregon. An April 17 burglary resulted in the possible exposure of patient information. Someone entered locked rooms and cabinets in order to take money. No records or electronic devices were taken; however the room where client medical charts were stored was accessed. Social Security numbers, health information, and other personal information may have been exposed. [source] | |
North Shore University Hospital, North Shore - Long Island Jewish Health System had a data breach in 2012, in New York. A licensed nurse who may or may not have been affiliated with North Shore University Hospital was indicted for identity theft and possessing computer data from North Shore containing information on over 900 people. It is unclear when the breach that allowed the nurse and an accomplice to access the information first occurred. Social Security numbers, dates of birth, addresses, phone numbers, medical record numbers, insurance information, and medical histories could have been accessed. North Shore University Hospital notified 50 patients of a potential breach in 2011 and may have experienced a separate system breach in early January of 2012. UPDATE(04/12/2012): The nurse also had the information of an unspecified number of U.S. Nippon Express employees.UPDATE(02/05/2013): A lawsuit has been filed by a group of people who claim that the breach allowed identity thieves to access and misuse their information. Many, but not all, of twelve people who filed the lawsuit claim to have been victims of identity thieves.UPDATE(03/04/2013): North Shore Long Island Jewish Health System faces a $50 million class action lawsuit. It was also revealed that thefts of patient face sheet information for identity theft purposes have occurred at least three times in a matter of just a few years. [source] | Northeast Orthopaedics, MRecord had a data breach in 2009, in North Carolina. Records of more than 1,000 patient visits to Northeast Orthopaedics, a large Albany surgical practice, have been posted on the Internet. The records appeared on the Web site visvabpo.com, which seems to be a defunct outsourcing company in India called visva BPO. Those records include patient names, birth dates and Social security numbers. [source] | |
Northridge Hospital Medical Center had a data breach in 2010, in California. A package sent through a national courier was damaged during transit. Because of this damage, patient names, Social Security numbers, addresses, phone numbers, dates of birth, dates of death, physician, financial account number, insurance ID, Medicare and Medicaid charges billed and paid, hospital room and board charges and guarantor Social Security number may have been exposed. People who were patients between September of 2004 and June of 2006 were affected. [source] | Northstar Healthcare had a data breach in 2012, in Illinois. An email that was sent to patients displayed the names of all patients who received the email. The email was sent to patients being treated for HIV or AIDS and inadvertently revealed names and HIV status. [source] | |
Northwest Primary Care had a data breach in 2015, in Oregon. Northwest Primary Care is notifying patients of a data breach when a former employee stole patient information. The information compromised patient names, dates of birth, Social Security numbers, and credit card numbers. The employee took the information from April 2013 and December 2013. [source] | Northwestern Medical Faculty Foundation had a data breach in 2010, in Illinois. [source] | |
Northwestern Memorial Hospital had a data breach in 2012, in Illinois. A Northwestern Memorial Hospital employee was charged with one count of aggravated identity and one count of identity theft. The dishonest employee is accused of stealing the identities of patients to pay off personal bills. Paperwork with the Social Security numbers, credit card numbers, and dates of birth of over 50 patients was found in the employees home. The dishonest employees scheme was discovered when suspicious credit card activity related to the opening of utilities in the employees name. [source] | Novant Health Gaffney Family Medical Care had a data breach in 2014, in South Carolina. Novant Health Gaffney Family Medical Care informed patients of a data breach when their offices were broken into and two of the facilities laptops were stolen.The information on the laptops was not disclosed. [source] | |
NRAD Medical Associates had a data breach in 2014, in New York. The information was breached via Desktop Computer and Other Portable Electronic Device. [source] | Nuance Communications had a data breach in 2018, in California. Bank Info Security reports:Nuance Communications, which specializes in speech recognition software, says an unauthorized third party accessed one of its medical transcription platforms, exposing 45,000 individuals' records.See Also: Matching Application Security to Business NeedsSo far, it appears only one of its customers, the San Francisco Department of Health, has reached out to affected patients. Breach victims include patients who visited Zuckerberg San Francisco General Hospital and Laguna Honda Hospital. The health department says in a news release that it delayed notifying patients at the request of the FBI and Justice Department, which have been investigating the breach.Their investigation "determined that a former Nuance employee breached Nuance's servers and accessed the personal information of thousands of individuals from several contracted clients, including the San Francisco Department of Public Health," the department says. [source] | |
Nursing Visioned Medical Services had a data breach in 2010, in Tennessee. Names, address, email address, phone number, ssn, and certain financial info were breached. [source] | NYU Langone Medical Center Hospital for Joint Diseases had a data breach in 2010, in New York. An unencrypted portable USB was lost or stolen sometime around May 12th. It contained patient names, medical record numbers, sex, age, procedure, attending physician, time of arrival in recovery room and time of discharge from recovery room. [source] | |
NYU Langone Medical Center had a data breach in 2011, in New York. A desktop computer was stolen from an NYU School of Medicine Faculty Group Practice physicians office on January 27, 2011. It contained names, dates of birth, medical record numbers, home addresses and patient occupations. Information from 670 patients who visited the Langone Medical Center between April 4, 1999 and September 30, 2008 was stored on the computer. [source] | Oak Park Medical Center had a data breach in 2014, in Michigan. Medical files were found by a former customer of a Dr. Pramod Raval, who was indicted in a Medicare home health care fraud scheme. Boxes of full files were dumped outside with massive amounts of patient data still intact.The medical files included files that contained names, Social Security numbers, X-rays, blood types and addresses.The local police were notified and the files were scheduled to be shredded. [source] | |
Ocean Acquisitions, Inc. had a data breach in 2015, in Connecticut. In December 2015, Oceans Acquisitions, Inc. began notifying patients in the Abilene area about a possible data security breach that may have resulted in exposure of a limited amount of protected health information (PHI). The potential exposure occurred when a laptop was stolen from an employee’s car. The laptop stored emails that potentially contained PHI such as names, dates of birth, medical record numbers, diagnoses, payer information and admission dates. No patient social security numbers or bank account information was included in the emails. Upon learning PHI may have been present on the device, Oceans immediately took steps to identify the individuals with the potential to be impacted. [source] | Ocean Acquisitions, Inc. had a data breach in 2015, in Connecticut. The theft of a laptop computer from the vehicle of an Oceans Acquisitions employee has resulted in the protected health information of 659 patients from the Abilene region of Texas being exposed.In May 2015, Oceans Acquisitions confirmed that all portable devices, including laptop computers, had sensitive data encrypted. In the event of theft or loss of a device, all PHI stored on that device would be protected. The encryption would prevent any unauthorized individual from being able to access stored data. However, the laptop theft occurred on April 9, 2015, a month before Oceans Acquisitions ascertained that all devices were protected. While the healthcare provider believed the laptop computer theft did not place any data at risk of exposure, this has turned out not to be the case. According to a substitute breach notice issued on February 2, 2016, Oceans Acquisitions determined that the laptop in question did contain the PHI of 659 individuals, and that those patients potentially had their PHI exposed. This came to light during an unrelated systems review, which was not linked to the laptop computer theft.The data were stored in an email account that could be accessed through the computer. The data exposed included names of patients, medical record numbers, dates of birth, payer information, medical diagnoses, and admission dates. No financial information, insurance data, or Social Security numbers were stored in the email account or on the laptop. [source] | |
Ocean Acquisitions, Inc. had a data breach in 2016, in Louisiana. The theft of a laptop computer from the vehicle of an Oceans Acquisitions employee has resulted in the protected health information of 659 patients from the Abilene region of Texas being exposed. In May 2015, Oceans Acquisitions confirmed that all portable devices, including laptop computers, had sensitive data encrypted. In the event of theft or loss of a device, all PHI stored on that device would be protected. The encryption would prevent any unauthorized individual from being able to access stored data. However, the laptop theft occurred on April 9, 2015, a month before Oceans Acquisitions ascertained that all devices were protected. While the healthcare provider believed the laptop computer theft did not place any data at risk of exposure, this has turned out not to be the case. According to a substitute breach notice issued on February 2, 2016, Oceans Acquisitions determined that the laptop in question did contain the PHI of 659 individuals, and that those patients potentially had their PHI exposed. This came to light during an unrelated systems review, which was not linked to the laptop computer theft. The data were stored in an email account that could be accessed through the computer. The data exposed included names of patients, medical record numbers, dates of birth, payer information, medical diagnoses, and admission dates. No financial information, insurance data, or Social Security numbers were stored in the email account or on the laptop. [source] | Ochsner Health System , H.E.L.P. Financial Corporation had a data breach in 2010, in Louisiana. [source] | |
Ochsner Medical Center had a data breach in 2012, in Louisiana. A hard drive was discovered missing on February 19. It contained patient personal and medical information related to a bone density machine. Medical information, names, dates of birth, addresses, medical record numbers, and medications from patients who had bone density scans between November 2005 and January 2012 were exposed. The hard drive was designed to work with the bone density machine and specialized software would be needed to extract information. [source] | Ochsner Medical Center had a data breach in 2012, in Louisiana. A janitor who worked at the Ochsner Medical Center in new Orleans and his girlfriend have pleaded guilty to charges related to stealing patient information for personal gain. The janitor stole printouts containing patient names, Social Security numbers, dates of birth, and other types of personal information. The stolen information was then used by the janitors girlfriend to open online accounts under the patients names. The online accounts were used to make thousands of dollars in fraudulent purchases. The date of the breach is unknown, but the janitor was employed between November of 2008 and June of 2009. Federal prosecutors first brought charges in early December of 2011. [source] | |
Office of Brian J. Daniels, D.D.S. and Paul R. Daniels D.D.S. had a data breach in 2011, in Arizona. [source] | Office of Dr. Calvin L. Schuster had a data breach in 2013, in California. A computer was stolen during an office burglary that occurred sometime around November 5, 2012. The computer contained patient names, dates of birth, and a minimal amount of patient medical information. [source] | |
Office of Dr. Clark-Neitzel had a data breach in 2012, in Washington. A July 24 office burglary resulted in the theft of medical bags and a laptop. Affected patients were mailed notification letters on September 7. Patient names, Social Security numbers, addresses, dates of birth, and medical information was exposed. [source] | Office of Dr. David Turner had a data breach in 2012, in Oregon. An office burglary in October of 2011 resulted in the theft of a laptop and other items. The laptop contained the information of current and former patients. It is unclear what type of information the laptop contained. A widespread notification of the breach was released in March after many patients could not be reached by mail. [source] | |
Office of Dr. Edalji and Dr. Komer had a data breach in 2011, in Massachusetts. [source] | Office of Dr. Gloria Traje-Quitoriano had a data breach in 2012, in California. A physicians laptop was stolen from her husbands car. The laptop contained patient names, Social Security numbers, dates of birth, phone numbers, and addresses. The laptop was not encrypted. [source] | |
Office of Dr. Jeffrey Paul Edelstein had a data breach in 2012, in Arizona. [source] | Office of Dr. Jeffry Barnes had a data breach in 2011, in Illinois. A woman found the sensitive information of more than 60 people in a recycling bin. Social Security numbers, prescription information, patient names and medical histories were all easily accessible. The employee responsible for the incident resigned after the mistake and Dr. Barnes agreed to upgrade his shredding practices. [source] | |
Office of Dr. Jeremiah J. Twomey had a data breach in 2012, in Texas. An office burglary that occurred sometime during the weekend of December 31, 2011 resulted in the theft of an external hard drive. The hard drive contained patient names, addresses, medical conditions, and diagnoses. The hard drive also held an unspecified number of patient Social Security numbers and dates of birth. [source] | Office of Dr. Lee D. Pollan, DMD, PC. had a data breach in 2013, in New York. [source] | |
Office of Dr. Leslie Coleman, Staff Providers had a data breach in 2011, in Georgia. A temporary employee from Staff Providers misused patient information. The temporary employee took co-payments from patients while the manager was out of the office. The temporary employee did not have authorization to collect the financial information and made print copies of each customers credit card during transactions. Patients later called the medical office and complained about fraudulent charges. The temporary employee made at least $1,400 worth of fraudulent charges, but was caught and charged with 11 counts of third-degree identity theft, illegal use of a credit card, and sixth-degree larceny almost immediately. [source] | Office of Dr. Luz Colon, DPM Podiatry had a data breach in 2012, in Florida. [source] | |
Office of Dr. Morgan Camp and Associates had a data breach in 2011, in California. An office computer was discovered missing on the morning of June 6. A burglar entered the office and searched through papers and equipment. There was no sign of forced entry. A credit card verification machine and approximately $150 in cash were also taken. Patient information, credit card information and other personal details were stored on the computer. Patients are advised to cancel any cards they had on file with Dr. Camps office. [source] | Office of Dr. Philip P. Corneliuson had a data breach in 2012, in California. An office burglary resulted in the theft of a computer. The incident was discovered on September 15, 2012. Patient names and Social Security numbers were on the computer.UPDATE(10/24/2012): The computer contained medical records and insurance information. [source] | |
Office of Dr. Rex Smith had a data breach in 2012, in Oregon. An office burglary that occurred on or around February 19 resulted in the theft of medications and a computer. The computer contained patient names, Social Security numbers, and dates of birth. It is unclear if the computer was encrypted. The total number of patients affected and all types of information exposed are also unclear. [source] | Office of Dr. Robert Witham had a data breach in 2012, in Washington. An April 16 office burglary resulted in the theft of two computers that contained sensitive patient information. Patient names, Social Security numbers, addresses, medical billings, ICD-9 diagnosis codes, and dates of birth were exposed. It is unclear if patients who saw the doctor as far back as 1979 were affected by the breach. Letters to patients who were affected were mailed on June 7. [source] | |
Office of Dr. Roy E. Gondo had a data breach in 2012, in Washington. A desktop computer and electronic medical records were stolen or discovered stolen sometime around February 21, 2012. They contained sensitive information.The incident was reported on the HHS website. [source] | Office of Dr. Sharon L. Rogers had a data breach in 2012, in Texas. [source] | |
Office of Dr. Stephen Haggard, DPM Podiatry had a data breach in 2011, in Washington. A theft, possibly of a network server, resulted in the exposure of sensitive patient health information. The theft occurred on or around March 4, 2012 and notifications were available for a limited time after April 22.The incident was posted on the HHS website on June 8. [source] | Office of Dr. William F. DeLuca Jr. had a data breach in 2012, in New York. [source] | |
Office of Gene S. J. Liaw, MD. had a data breach in 2011, in Washington. An unencrypted USB drive was determined to be missing on April 4, 2011. It contained patient names, Social Security number, addresses, phone numbers, dates of birth, diagnosis codes, and insurance information. [source] | Office of Paul C. Brown, M.D., P.S. had a data breach in 2011, in Washington. An October 14, 2011 office burglary resulted in the exposure of patient information dating from 1993 to 2004. Office equipment and CDs with patient information were discovered missing on October 17. Affected patients were mailed notification letters on December 13, 2011 and informed that their names, Social Security numbers, dates of birth, addresses, diagnoses, medical conditions, lab results, medications, surgery records, radiological tests, and other clinical treatment information could have been on the stolen CDs. The office now plans to install encryption technology and update physical security systems in order to protect patient data from more breaches. [source] | |
Office of Robert S. Smith, M.D., Inc. had a data breach in 2012, in Georgia. An October 17 office burglary resulted in the theft of a laptop. The laptop contained patient names, dates of birth, physicians, and diagnosis information. [source] | Ohio State University Medical Center had a data breach in 2005, in Ohio. Appointment information including Social Security numbers, birth dates, addresses, phone numbers, medical record numbers, reasons for appointments, and physicians was exposed online. [source] | |
Ohio State University Medical Center had a data breach in 2012, in Ohio. A hacker or hackers outside of the US attempted to gain access to an OSU Internet server. Information on the server included names, medical record numbers, and dianoses of 30 patients who visited the pathology department between the late 1980s and 2004. A roster of students who had received training at the medical center in 2006 was also on the server. Officials do not believe that any personal information was taken during the attempt. A total of 30 patients and 150 students were notified. [source] | Ohio University Hudson Health Center had a data breach in 2006, in Ohio. Names, birth dates, Social security numbers and medical information were accessed in records of students dating back to 2001, plus faculty, workers and regional campus students. [source] | |
Oilandgasjobsearch.com had a data breach in 2017, in Cheshire. [source] | Oklahoma Veterans Affairs Medical Center had a data breach in 2010, in Oklahoma. An employee noticed that some pages were missing from a laboratory log book on October 15. The pages may have contained the names, last four digits of Social Security numbers, appointment information and tests of 1,950 VAMC visitors. Veterans who visited between January 1 and October 8 may have been affected. The military believes the most likely cause of the loss is that the pages were shredded.UPDATE (12/2/10): An VA investigation determined that the information was most likely accidentally shredded. [source] | |
Oldendorf Medical Services had a data breach in 2012, in New York. An office burglary on or around January 18 resulted in the theft of two laptops. The laptops contained the records of about 640 patients and had been used for cardiac tests. Though the laptops contained minimal clinical data, they did contain some Social Security numbers and demographic information. [source] | Omni Hotels & Resorts had a data breach in 2016, in Texas. On May 30, 2016, we discovered we were the victim of malware attacks on our network affecting specific point of sale systems on-site at some Omni properties. The malware was designed to collect certain payment card information, including cardholder name, credit/debit card number, security code and expiration date. [source] | |
Omnicell, University of Michigan Health System had a data breach in 2012, in Michigan. An electronic device was stolen from an Omnicell employees car on November 14. The device was not encrypted and contained the medication, demographic, and health information of 4,000 patients from three hospitals in the University of Michigan Health System. UPDATE(1/2/2013): A total of 3,997 people who were treated between October 24 and November 13 at three hospitals in the University of Michigan Health System were affected. However, patients of at least 10 Sentara Healthcare and South Jersey Healthcare medical facilities were also affected. A total of 56,000 Sentara Healthcare patients from Sentara CarePlex, Sentara Leigh Hospital, Sentara Norfolk General Hospital, Sentara Obici Hospital, Sentara Princess Anne Hospital, Sentara Virginia Beach General Hospital, Sentara Williamsburg Regional Medical Center, Sentara Belle Harbour, Sentara Independence, and Sentara Port Warwick who were treated between October 18, 2012 and November 9, 2012 were affected. A total of 8,555 patients from South Jersey Healthcare who were either treated or scheduled for admission between June 1, 2012 and November 12, 2012 were affected. [source] | Onco360 and CareMed Speciality Pharmacy had a data breach in 2017, in Kentucky. [source] | |
Open Door Clinic of Greater Elgin had a data breach in 2010, in Illinois. According to a lawsuit, the clinic stores patient information, including Social Security numbers, addresses, telephone numbers, insurance information and medical history on a file-sharing network. That network is accessible to employeesí£ personal laptops and home computers. A spreadsheet with information of about 260 of its patients was leaked as a result of the installation and use of file sharing software on computers containing patientsí£ personally identifiable information. [source] | Open MRI of Chicago, Nation Wise Machine Buyers had a data breach in 2012, in Illinois. The improper disposal of paper documents resulted in the exposure of health and/or other personal information. The breach was discovered on September 6, 2011. [source] | |
Orange County Global Medical Center had a data breach in 2017, in California. [source] | Oregon Health and Science University Hospital (OHSU) had a data breach in 2012, in Oregon. The July 4 or 5 burglary of an OHSU empoyees home resulted in the theft of a briefcase, a thumb drive, and several other items. The thumb drive was used to back up data from OHSU computer systems and would normally be locked in a secure location on campus. Pediatric patient information such as name, date of birth, phone number, address, OHSU medical record number, patient medical condition code, or family medical history was exposed. A total of 702 patients had additional information exposed that was more sensitive. The thumb drive also contained a database of OHSU staff information that included names, Social Security numbers, addresses, and employment-related vaccination information of 195 OHSU employees. [source] | |
Oregon Health and Science University had a data breach in 2008, in Oregon. A laptop stolen in Chicago this week contained health records. It was stolen from a hotel while an OHSU employee was there on business. The data could include medical record numbers, names, telephone numbers, dates of birth, gender, Social Security numbers, addresses.medical diagnosis category and category of treatment - but not the specific treatments. [source] | Oregon Health and Science University had a data breach in 2009, in Oregon. A physicians laptop was stolen from a car parked at the doctors home. Patient names, treatment dates, short medical treatment summaries and medical record numbers were stored on the computer. There were no home addresses, billing information or Social Security numbers stored on the laptop.UPDATE (08/11/10): It seems that as many as 4,000 patients may have been affected and Social Security numbers were involved. [source] | |
Oregon Health and Science University had a data breach in 2013, in Oregon. [source] | Oregon State Hospital had a data breach in 2012, in Oregon. The theft of sensitive documents from an Oregon State Hospital supervisors car resulted in the exposure of patient information. On Friday, April 13, a printed list of 550 hospital patients that included names, treating physicians, hospital identification numbers, and geographic information was stolen. Additionally, progress notes for 20 patients were stolen that included patient dates of birth, diagnoses, and other information. It is not clear if patients who visited either the Salem Oregon State Hospital or the Portland Oregon State Hospital were affected by the breach. [source] | |
Orlando Health's Arnold Palmer Medical Center had a data breach in 2014, in Florida. A computer flash drive containing patient information on 586 children treated at Orlando Health's Arnold Palmer Medical Center is missing or reportedly been "misplaced" The information included last names, assigned medical record numbers, dates of birth, gestational ages, birth weights, dates of hospitalizations, and in some cases, transfer dates of children who were patients at Arnold Palmer Hospital for Children or Winnie Palmer Hospital for Women and Babies between 2009 and 2013. [source] | Orlantino Dyoco, M.D. had a data breach in 2015, in California. The information was breached via Network Server. [source] | |
OrthoMontana had a data breach in 2011, in Montana. The loss or theft of a laptop may have exposed the information of current and past patients.UPDATE(3/16/2011): About 37,000 patients had their information on the laptop. The types of patient information exposed were not reported, however the laptop did not contain financial information. [source] | Orthopaedic Specialty Institute Medical Group had a data breach in 2014, in California. The information was breached via Network Server. [source] | |
Orthopedic Physician Associates, Proliance Surgeons had a data breach in 2013, in Washington. An employees car was the target of an April 1 break-in. A company laptop and 10 patient files were taken during the car theft. The paper files were recovered, but the laptop also contained patient information. Names, Social Security numbers, addresses, telephone numbers, health insurance information, names of providers, and the reasons for patients appointments may have been included in emails stored on the laptop. [source] | Orthopedics and Adult Reconstructive Surgery, AssuranceMD had a data breach in 2013, in Texas. AssuranceMD lost a portable electronic device of their associate Orthopedics and Adult Reconstructive Surgery. The breach occurred between March 1 and March 15. [source] | |
Our Lady of Peace had a data breach in 2010, in Kentucky. A flash drive containing personal information on 24,600 patients is missing from Our Lady of Peace psychiatric hospital. The drive contained the following information on patients admitted since 2002: patient names, room numbers, insurance company names and admission and discharge dates. It didní£t include diagnoses or treatments, Social Security numbers, dates of birth, telephone numbers or addresses for these patients. The drive also included the following information on patients assessed since 2009 but never admitted: name, date of assessment, date of birth and the time they left the hospital. For these patients, the information on the drive didní£t include diagnoses or treatments, Social Security numbers, telephone numbers, addresses or insurance information. [source] | Pacific BioSciences of California Inc. had a data breach in 2014, in California. Name, dob, contact information, ssn, banking info, compensation info, insurance info were breached. [source] | |
Palo Alto Medical Foundation had a data breach in 2009, in California. A laptop computer recently stolen at the Palo Alto Medical Foundations Santa Cruz office contained personal and medical information of 1,000 Santa Cruz County patients. [source] | Palomar Health had a data breach in 2014, in California. The information was breached via Electronic Medical Record. [source] | |
Park Avenue Obstetrics and Gynecology, PC had a data breach in 2011, in Georgia. A portable electronic device was discovered stolen on March 25, 2011. It contained personal and health information. [source] | Parkland Memorial Hospital had a data breach in 2011, in Texas. [source] | |
Pathology Group had a data breach in 2007, in Tennessee. Someone broke into a locked office building, several computers with flat screen monitors were stolen. one of those computers had patient information on about 75,000 people. this information included names, addresses, Social Security number, even medical information [source] | Pathways Professional Counseling had a data breach in 2015, in Alabama. The information was breached via Desktop Computer. [source] | |
Patuxent River Naval Air Station had a data breach in 2010, in Maryland. A clinic employee and a co-conspirator used patient information to access financial accounts. The two people were charged with stealing from the Navy Federal Credit Union. The information was stolen between November of 2008 and May of 2009. [source] | PAX Labs, Inc. had a data breach in 2016, in California. On July 15, 2016, we discovered that an unauthorized party had gained access to one of our cloud-based website servers and installed unauthorized software. PAX removed this software on July 15, 2016. Subsequently, an unauthorized party added similar software on July 22, 2016, which PAX removed that same day. Our investigation revealed that the unauthorized party accessed personal payment card information of approximately 6,000 customers who had made purchases from either www.JUULvapor.com or www.PAXvapor.com between June 25, 2016, and July 22, 2016.The information compromised included payment card data including names, shipping and billing addresses, credit/debit card numbers, expiration dates, and security codes. [source] | |
Pediatric and Adult Allergy, PC had a data breach in 2010, in Iowa. Patients of Dr. George Caudill (retired), Dr. Veljko Zivkovich (retired) Dr. Robert Colman and Dr. Whitney Molis were notified that a backup tape with their personal information was lost on or around July 11. The patient information included name, address, phone number, date of birth, Social Security number, dates of service, services and diagnoses. Medical records and financial information were not on the backup tape. It appears that all patients with accounts created before July 10, 2010 were affected. [source] | Pediatric Sports and Spine Associates had a data breach in 2010, in Tennessee. A laptop was stolen from an employee on February 10. The theft occurred off-site. The laptop contained names, addresses, phone numbers, dates of birth, medical information and Social Security numbers. [source] | |
Peninsula Orthopaedic Associates had a data breach in 2009, in Maryland. As many as 100,000 patients of peninsula Orthopaedic Associates are being warned to protect themselves against identity theft after tapes containing patient information were stolen. Patients also were advised to keep an eye on benefits statements from their health insurance companies since they may also be at risk for medical identity theft. The records from Peninsula orthopaedic were stolen March 25 while in transport to an off-site storage facility. Patients personal information including their Social security numbers, employers and health insurance plan numbers may have been among the information stolen. [source] | Penn Highlands Brookville had a data breach in 2014, in Pennsylvania. Name, dob, ssn insurance info, medical info, gender were breached. [source] | |
Penn Medicine Rittenhouse had a data breach in 2014, in Pennsylvania. Penn Medicine had to announce a data breach involving receipts that were stolen last month from a locked office in Pennsylvania Hospital. The information on the receipts included combinations of patient names, dates of birth and the last four digits of credit card numbers. [source] | Penn Medicine had a data breach in 2017, in Pennsylvania. The information was breached via Laptop. [source] | |
Penn State Milton S. Hershey Medical Center had a data breach in 2014, in Pennsylvania. [source] | Penrose Hospital had a data breach in 2009, in Colorado. Officials at Penrose Hospital believe someone has stolen the personal information of 175 patients. The missing information consists of names, addresses, phone numbers, Social Security numbers and the reason for the patients visits. The information was stored on a computer print-out and kept in a binder stored in a cabinet. The print out has gone missing. [source] | |
Pension Fund of the Christian Church had a data breach in 2017, in Indiana. On Dec. 16, 2017, Pension Fund learned that a password protected employee laptop had been stolen that contained personal information for 10981 records, including SS numbers, as well as credit card or financial account information. [source] | Pentagon had a data breach in 2016, in District Of Columbia. An unclassified email system used by the Pentagon was compromised by Russian hackers in 2015, forcing security teams to take the entire network down in order to fix the breach.Martin Dempsey, who was at that time Chairman of the Joint Chiefs, told CBS that he was informed of the breach by the Director of the National Security Agency, Admiral Mike Rogers, revealing that in approximately one hour, hackers seized control of the entire email system.However, Dempsey explains that the email service was used by staff of the Pentagon’s Joint Chiefs staff, which involves some 3,500 military officers and civilians who work for the chairman, and included only unclassified emails that “had no real intelligence value.”According to Dempsey, hackers managed to obtain passwords and electronic signatures that he personally used to access the network, so taking the entire system offline was the only way to deal with the problem.Russia-backed attackersAs for the identity of the hackers, the United States officials believed they were Russians who were trying to fight back at the Pentagon after the US issued economic sanctions against their country for the conflict in Ukraine and the annexation of Crimea.The attack was launched with compromised severs from a West Coast university, which were used to send a total of 30,000 emails. Four of them were eventually forwarded to Joint Chiefs of Staff employees and included malicious files that infected computers when executed. At least one of them was opened by an employee and eventually compromised the system before spreading across the entire network. [source] | |
Pentair Aquatic Eco Systems, Inc. had a data breach in 2017, in Florida. Pentair Aquatic Eco Systems, Inc., suffered a hack on 12/19/2017 that resulted in the exposure of 239 records, which included names, credit card or financial account information and debit card numbers. [source] | Phoebe Putney Memorial Hospital had a data breach in 2012, in Georgia. On April 9, 2012, Phoebe Putney Home Health Care (PPMH) learned from law enforcement officials that a former employee had improperly accessed patient information with the intent to file fraudulent tax returns. The dishonest employee may have accessed the names, Social Security numbers, and dates of birth of patients some time between June 2010 and April 2012. Patients who were treated through PPMH between July 2005 and April 2012 may have been affected. [source] | |
Phoenix Cardiac Surgery, P.C. had a data breach in 2012, in Arizona. [source] | Physicians Skin and Weight Systems had a data breach in 2014, in California. On November 14, 2014 an employee laptop and hard drive were stolen when their car was broken into. According to the company the laptop was password protected.The information stored on the laptop included images taken during the course of treatment, names, banking, full routing numbers, credit card numbers, some financing applications that included Social Security Numbers, dates of birth, mailing address, email address, income, rent payments and employer names. [source] | |
Piedmont Behavioral Healthcare (PBH), Alamance-Caswell LME (AC LME) had a data breach in 2012, in North Carolina. A miscommunication caused AC LME to lose access to servers containing sensitive health information. An Alamance County employee mistakenly changed a lock on the facility that housed data servers for AC LME.It appears that AC LME forgot to inform the county that AC LME was extending a contract for server maintenance.Former consumers of AC LME, including those who became PBH consumers on October 1, 2011, may have had their personal health information stored on these servers. The servers are now in the possession of the county and could contain the names, Social Security numbers, medical record identification numbers, addresses, and diagnoses of AC LME consumers. LME officials have not had access to the server room without being monitored by a county employee or with the forensics team assigned to examine the servers. [source] | Pierre Fabre had a data breach in 2018, in California. On March 12, 2018, we discovered that information entered on some of our websites (aveneusa.com, renefurtererusa.com, kloraneusa.com, and glytone-usa.com (the “Websites”)) had been captured and potentially sent to unauthori zed third parties. Any information entered on any of the Websites between February 20, 2018 and March 15, 2 018 may have been exposed.Information affected included: name, credit or debit card information or other payment account information, phone number, email address, shipping address, billing address and/or Website account password. [source] | |
PinnacleHealth System, Gair Medical Transportation Services had a data breach in 2011, in Pennsylvania. New York based Pioneer Bank notified customers of a data breach when an employee laptop was stolen on January 26th, compromising their personal information. The information compromised the names, addresses, Social Security numbers, and account and debit card numbers. [source] | Pitt County Memorial Hospital had a data breach in 2009, in North Carolina. Patient names and Social Security numbers were placed onto a portable computer storage device, used to move the information between different computer systems. Employees have since discovered that USB flash drive is missing from where it was stored. [source] | |
Plastic Surgery Associates of South Dakota had a data breach in 2017, in South Dakota. A ransomware attack on Plastic Surgery Associates of South Dakota may have breached the data of 10,200 patients.The provider discovered on Feb. 12 that some of its systems were infected with ransomware. Officials said Plastic Surgery Associates immediately began to attempt removing the virus and decrypting the data. It also hired third-party experts.While the investigation found the hackers were unable to access the majority of Plastic Surgery Associates’ medical data, officials lost access to evidence during the cleanup efforts on April 24. As a result, officials can’t rule out whether the attackers were able to access some patient data.Social Security numbers, driver licenses, state identification numbers, credit/debit cards, medical conditions, dates of birth, lab results, diagnostic results and health insurance information may have been compromised. [source] | Platte Valley Medical Center (PVMC), Centura Health had a data breach in 2011, in Colorado. A contract nurse who was employed by PVMC between May of 2010 and January of 2011 misused patient information. At least 76 PVMC patients became victims of identity theft. The nurse was employed at multiple locations. The former employee may have accessed a total of 142 patient records while at PVMC, and 123 while working in the Centura Health system. He faces 90 felony counts related to illegally accessing patient files and identity theft. [source] | |
Pocatello Family Medicine, Idaho State University had a data breach in 2011, in Idaho. The firewall protecting computerized records was accidentally left inactive for nine months. It was disabled during maintenance in August of 2010, but was never restored. The problem was discovered when IT staff assisted an employee on May 18, 2011. It appears that an electronic medical record for the clinic that was stored on the server was never accessed during that time. Other information on the server included scanned images of drivers licenses and insurance cards. There is also no evidence that these records were accessed, downloaded or printed. It does appear that someone downloaded movies and a television program onto the site in order to use the storage space and illegally sell access to the material. UPDATE(05/22/2013): The information of 17,500 patients was exposed. The Department of Health and Human Services released a resolution agreement on May 21 for HIPAA violations related to the breach. [source] | Portal Healthcare Solutions, Glens Falls Hospital had a data breach in 2013, in New York. The information was breached via Network Server. [source] | |
Portland Veterans Affairs Medical Center had a data breach in 2011, in Oregon. Between 50 and 75 patient ID cards were lost in January. Social Security numbers, dates of birth and other personal information were on the cards. The cards had previously been mailed to the wrong addresses and were being stored in the hospitals enrollment office. [source] | Portsmouth Hospital had a data breach in 2011, in New Hampshire. A man tried to steal X-rays. Investigators believe he wanted the X-rays for the tiny amount of silver inside rather than the protected health information of patients. The incident may have been related to other thefts in the Massachusetts and New Hampshire areas. [source] | |
prAna had a data breach in 2017, in California. [source] | Pratap S. Kurra, M.D. had a data breach in 2016, in California. The information was breached via Paper/Films. [source] | |
Preferred Skin Solutions had a data breach in 2012, in Oklahoma. An office burglary that occurred on or around January 24 resulted in the loss of a laptop. The laptop held client records. The company sent a breach notification through Facebook and email. No financial information was on the laptop, but Preferred Skin Solutions still warned their clients about the risk of identity theft. [source] | Premier Healthcare, LLC had a data breach in 2016, in Indiana. The information was breached via Laptop. [source] | |
Presbyterian Anesthesia Associates had a data breach in 2013, in North Carolina. A hacker took advantage of a security flaw in Presbyterian Anesthesia Associates website and gained access to a database of patient information. Names, credit card numbers, dates of birth, and contact information may have been exposed. [source] | Presbyterian Health Care Services had a data breach in 2011, in New Mexico. Between May and June of 2008, a PHS pharmacy employee misused the names and identification information of customers. The former employee had fraudulent prescription reimbursement checks mailed to her friends and relatives, who then gave the proceeds back to the pharmacy employee. The employee allegedly generate 17 fraudulent checks for a total of $27,129.63. The woman was sentenced to two years in prison and four years of supervised release. She will also have to pay restitution to PHS and Medicaid. [source] | |
Presbyterian Intercommunity Hospital had a data breach in 2008, in California. About 5,000 past and current employees at Presbyterian Intercommunity Hospital had their private information stolen. The data included Social Security numbers, birth dates, full names and other records stored on a desktop computer that was stolen. [source] | Prime Home Care, LLC had a data breach in 2010, in Nebraska. Name, ssn, dob, and employee identification number were breached. [source] | |
Private Dental Practice had a data breach in 2010, in Missouri. A dentists laptop was stolen from his car in October. It contained the clinical information for patients who saw him at a St. Charles office. The dentist notified police immediately, but waited about a month to notify patients. [source] | Private Dental Practice had a data breach in 2010, in Texas. The office discovered a hacking incident after the computer system shut down on October 14. A hacker accessed the computer system and server. Patient names, Social Security numbers, addresses, dates of birth, dental care and X-ray records, dental insurance member numbers and health insurance member numbers may have been exposed. [source] | |
Private Dental Practice had a data breach in 2011, in Maryland. [source] | Private Medical Practice had a data breach in 2007, in New York. The information was breached via Email and Network Server. [source] | |
Private Medical Practice had a data breach in 2008, in Florida. Medical documents with Social Security numbers were found in a dumpster. [source] | Private Medical Practice had a data breach in 2010, in California. A desktop computer was stolen on or around August 17. [source] | |
Private Medical Practice had a data breach in 2010, in California. Confidential medical files were found in a dumpster near the medical office of the two doctors. The doctors were in the process of moving to a new location. [source] | Private Medical Practice had a data breach in 2010, in Kansas. [source] | |
Private Medical Practice had a data breach in 2010, in Virginia. A laptop was stolen from a doctors office on July 12. It is unknown if patient files were accessible on the laptop. The files would have contained names, dates of birth, diagnoses, treatments, and other personal information. [source] | Private Medical Practice had a data breach in 2011, in Kansas. An Attorney General who investigated the controversial Dr. Tiller is facing allegations that patient records were improperly stored. The AG admitted that sensitive patient records from the case had been temporarily stored in a former employees home at one point. [source] | |
Private Medical Practice had a data breach in 2011, in Oklahoma. A desktop computer, a portable electronic device, or both were discovered lost on November 24, 2010. It is unclear who the data belonged to and what kind of information was lost. [source] | Private Medical Practice had a data breach in 2011, in Texas. A man was linked to the theft of at least 100 medical records. A surgeon had taken old records home to be shredded; they were stolen from his garage. There were 34 names, 19 drivers license numbers and many dates of birth. The thief was caught attempting to sell the information for $250 in June of 2010. The man pleaded guilty to possessing numerous medical files. [source] | |
Private Practice in Medical Arts Building had a data breach in 2010, in Pennsylvania. [source] | Promedica Bay Park Hospital had a data breach in 2014, in Ohio. ProMedica Bay Park Hospital notified patients of a data breach when an employee of the facility accessed records of patients not directly under their care from April 1, 2013 to April 1, 2014.The information breached included each patient's full name, date of birth, diagnosis, attending physicians, and medications. Patients' Social Security numbers and financial information are not believed to have been accessed. The employee was immediately fired once the hospital learned of the privacy breach. [source] | |
ProMedica had a data breach in 2011, in Ohio. A mail sorting machine mistake caused sensitive information to be mailed to unintended patients. The breach was discovered when a patient opened a letter that contained her name and address, but the financial assistance application of a different patient. Names, addresses, dates of birth, phone numbers, and Social Security numbers were exposed. [source] | Prosthetic & Orthotic Care, Inc. had a data breach in 2016, in Missouri. [source] | |
Provena Covenant Medical Center had a data breach in 2011, in Illinois. An employee responsible for moving patients around Provena Covenant was sentenced to eight years in federal prison for identity theft. The former employee accessed patient names, Social Security numbers, dates of birth and other personal information by stealing patient wallets and through other methods. She also used at least one patients credit card information to pay for access to victims outside of Provena Covenant. At least 100 different names were found at the womans home. It is not clear if all of those names were related to the former employees misdeeds at Provena Covenant between 2007 and 2008. [source] | Providence Alaska Medical Center had a data breach in 2007, in Alaska. A laptop computer that contains the personal information of patients is missing. On the laptop there maybe names, medical record numbers, dates of birth, patient diagnoses, Social Security numbers and addresses. [source] | |
Providence Health had a data breach in 2009, in Oregon. [source] | Providence Hospital had a data breach in 2010, in Minnesota. The information was breached via Electronic Medical Record. [source] | |
Providence Medical Group- Gateway Clinics had a data breach in 2016, in Oregon. The information was breached via Electronic Medical Record . [source] | PSA HealthCare had a data breach in 2006, in Georgia. A company laptop was stolen from an employees vehicle in a public parking lot July 15. It contained names, addresses, SSNs, and medical diagnostic and treatment information used in reimbursement claims. [source] | |
Pure Med Spa, Brite Smile Brite Skin had a data breach in 2012, in Nevada. A woman alerted a local news station to a stash of improperly disposed information. Credit card applications, patient names, addresses, Social Security numbers, and possibly medical records were found sitting next to a dumpster in a parking lot. The paperwork came from multiple organizations. Among the organizations were two closed branches of Pure Med Spa and Brite Smile Brite Skin. [source] | Q Dental Group PC had a data breach in 2006, in New York. An employees car was stolen from the parking lot of a lab. A schedule of patients that included name, reason for visit, date of visit, doctor name and possibly phone number was in the car. The financial information of five patients and more detailed medical information of eight patients was also in the car. [source] | |
Quest Diagnostics had a data breach in 2012, in New Jersey. A dishonest employee was discovered to have forwarded emails that contained sensitive personal information in late July. The emails included names, Social Security numbers, addresses, dates of birth, drivers license numbers, financial account information, and medical/health insurance information. [source] | Radiology Regional Center, PA had a data breach in 2016, in Florida. Radiology Regional Center, PA, a physician-owned and managed diagnostic facility with nine locations in Florida, announced today that on December 19, 2015, Radiology Regional Center was informed by its records disposal vender, Lee County Solid Waste Division (“Lee County”), that, on that same date, paper records containing the personal information of Radiology Regional Center’s patients were released by Lee County on Fowler Street in Fort Myers, Florida. The records were released while Lee County was transporting the records to be incinerated. This release is being issued in accordance with guidelines from the Health Insurance Portability and Accountability Act (“HIPAA”). Impacted patients have already been notified in accordance with HIPAA. To the best of Radiology Regional Center’s knowledge, these records, which date from 2005-2012, may have contained patient names, addresses, phone numbers, social security numbers, dates of birth, health insurance numbers, and other medical status and assessment information as well as financial information gathered in the patient medical and financial records. [source] | |
Radiology Regional Center had a data breach in 2015, in Florida. Hundreds of medical records belonging to Radiology Regional Center were found scattered on the roads in Fort Myers Florida. The records included finacial information on accounts, old phone bills invoice and registration information typically given at the front desk. It appears that the container that the documents were in that were being collected for destruction by the county, opened and the papers flew out of the truck. [source] | Rady's Childrens Hospital had a data breach in 2014, in California. [source] | |
Rainbow Hospice and Palliative Care had a data breach in 2010, in Illinois. [source] | Rainier Surgical, Incorporated had a data breach in 2015, in Texas. OCR opened an investigation of the covered entity (CE), Rainier Surgical, Inc., after it reported that a file drawer with explanations of benefits containing the protected health information (PHI) of 4,290 individuals was stolen from a warehouse. The PHI included names, addresses, dates of birth, health insurance information, explanations of benefits, and in some cases, credit card numbers and social security numbers. Upon discovering the breach, the CE filed a police report. The CE provided substitute notice and media notification in the localities with greater than 500 individuals affected. The CE offered one year of free credit monitoring services to individuals whose social security numbers may have been compromised. Following this breach, the CE retrained employees, reviewed its policies and procedures, and began storing some PHI with an on-site third party secure storage vendor. OCR confirmed that the CE took the actions described above. [source] | |
Raleigh Orthopaedic Clinic had a data breach in 2013, in North Carolina. An office burglary was discovered on the morning of February 4. A server with patient personal and health information was among the stolen items. Patients who were seen by the dentists during the past 30 years were affected. The names of patients and patient guardians, home addresses and dates of birth for patients under 18 were on the server. Account holders who provided insurance information may have had their Social Security numbers and dates of birth on the server. Patients who used AllKids with Blue Cross & Blue Shield of Alabama may have had their Social Security number included in the exposed insurance information. An unspecified amount of customer credit card numbers were also stored on the server. [source] | Rancho Los Amigos National Rehabilitation Center had a data breach in 2011, in California. A stolen laptop contained patient information. Patient names, dates of birth and medical record numbers may have been exposed. The laptop was connected to diagnostic machinery. The laptop was stolen from the Center on or around February 24. [source] | |
Reading Hospital had a data breach in 2012, in Pennsylvania. A Reading Hospital employee made paper copies of sensitive information and used them for training purposes at an unaffiliated educational facility. The incident was discovered the next day and the employee was fired. Patient medical test results, diagnoses, prescribed medications, Social Security numbers, medical histories, and other personal information were exposed. [source] | Rebecca Minkoff had a data breach in 2016, in New York. On August 10, 2016, Rebecca Minkoff learned that there may have been unauthorized access to our website. We hired an outside forensic expert to determine whether the incident resulted in the unauthorized access to any personal information.The information compromised included names, website usernames and password, payment card information. [source] | |
Regional Medical Center had a data breach in 2013, in Tennessee. [source] | Reid Hospital had a data breach in 2011, in Connecticut. A computer was stolen from an employees home during an early April burglary. It may have contained information from patients who visited the hospital between 1999 and 2008. Patients covered under Medicaid or Medicare may have had their Social Security numbers as well as unspecified information contained in patient reports. [source] | |
Renal Treatment Centers Southeast, DaVita Inc. had a data breach in 2009, in Colorado. [source] | Renovate America had a data breach in 2017, in California. The information was breached via Portable Electronic Device. [source] | |
Rent the Runway had a data breach in 2017, in New York. It was discovered that your Rent the Runway account was accessed by an unknown party between December 25, 2016 and February 23, 2017.What Information Was InvolvedThe information that may have been accessed includes: email address, first name, last name,birthday and mailing address. We do not store credit cards, so your credit card information was not exposed. [source] | Revolution Partners, LLC had a data breach in 2017, in Tennessee. [source] | |
Rhinebeck Health Center, Center for Progressive Medicine had a data breach in 2012, in New York. On February 15, 2012, Rhinebeck learned that their unnamed computer vendor experienced a computer security breach. An unauthorized party or parties may have accessed any patient information between November 15, 2011 and December 14, 2011 that was on the Rhinebeck and Center for Progressive Medicine computer network. Patient full names, Social Security numbers, dates of birth, home addresses, phone numbers, account information, health insurance information, credit card information, laboratory tests, and diagnosis information may have been exposed. Anyone who visited either center between January 1, 2002 and December 22, 2011 may have been affected. [source] | River City Media had a data breach in 2017, in Oregon. One of the world's allegedly most prolific spamming operations inadvertently left backup databases accessible online, exposing upwards of 1.37 billion records and a raft of internal company information.Chris Vickery, a security researcher who works for the anti-virus company MacKeeper, discovered the databases, which belong to a US-based email and SMS marketing company called River City Media. In some cases, the records include the names, IP addresses, zip codes and physical addresses associated with the email addresses.The cause of the data exposure appears to be an oversight. The company used the rsync protocol to backup its MySQL databases. But those backup servers were not password-protected, Vickery says in an email to Information Security Media Group.The leak could be one of the largest of all time, but it's likely the databases contain duplicates. The databases, which were exposed for at least three months, have since been taken offline. [source] | |
River Falls Medical Clinic had a data breach in 2013, in Wisconsin. The information was breached via Email. [source] | Riverside County Regional Medical Center had a data breach in 2014, in California. [source] | |
Riverside County Regional Medical Center had a data breach in 2015, in California. The Riverside Regional Medical Center has notified patients of the loss of a laptop computer that contained personal patient information. The laptop went missing from a diagnostic services office in the hospital sometime between June 17, 2014 and June 18, 2014. The information on the missing laptop included names, dates of birth, medical record numbers and results of a nerve conduction study, and the names of the referring doctor and the doctor who performed the study. The hospital did communicate that no Social Security numbers, health insurance information or home addresses were stored on this particular laptop [source] | Riverside Mercy Hospital, Mercy Health Partners had a data breach in 2010, in Ohio. On December 5, 2017, a San Diego County office of Education employee inadvertently sent an employee retirement contribution spreadsheet to San Diego County Office of Education's retirement contribution contacts at forty-four (44) school districts throughout Southern California. The impact likely affected 1 Idaho resident. [source] | |
Robley Rex VA Medical Center had a data breach in 2012, in Kentucky. Documents with names, Social Security numbers, and discharge dates of veterans were discovered unattended in the lobby entrance of Robley Rex VA. An extensive review was conducted by VA officials and they concluded there was no reason to believe any information was misused or that any malicious activity was involved. Neither the reason for the breach nor the details of the breach discovery were revealed. [source] | Rod's True Western Living had a data breach in 2017, in Ohio. [source] | |
Ronald D. Garrett-Roe MD had a data breach in 2015, in Texas. Dr. Ronald D. Garrett-Roe notified patients of a data breach when hackers gained unauthorized access to two hard drives located on the desktop computers of the physicians office. The hard drive had been removed and all the files contained on the hard drive were copied. The hard drive was then formatted to erase all of the information on the computer system. No specific information was provided as to what patient information was compromised. [source] | Roudebush Veteran's Administration Medical Center had a data breach in 2007, in Indiana. [source] | |
Safe Harbor Med had a data breach in 2010, in California. Burglars stole client records, a suitcase and two bags of cookies from a medicinal marijuana referral office. Burglars also stole a computer hard drive that contained a client database, including Social Security numbers, ID numbers and other sensitive information. [source] | Sagebrush Medical Plaza/Kern Medical Center had a data breach in 2009, in California. The information was breached via Paper/Films. [source] | |
Saint Agnes Medical Center had a data breach in 2016, in California. Saint Agnes Medical Center was targeted by an isolated email phishing attack in which a scammer impersonated our Chief Executive Officer and requested that W-2 information be sent via email. There was no breach to any of our Sant Agnes systems and all patient information remains secure. Rather, we were a target of what is known as a BEC (Business Email Compromise/Correspondence) attack, which typically focuses on tax information that can be used to obtain fraudulent returns.The information compromised is the information you would find on a W2 form, including names, addresses, salary information, withholding information and Social Security numbers. [source] | Saint Barnabas Health Care Systems and Newark Beth Israel Medical Center had a data breach in 2010, in New Jersey. An employee of Saint Barnabas accounting partner KPMG lost an unencrypted flash drive. The flash drive had patient names and information about their health, but did not have Social Security numbers or financial information. The incident occurred in June and patients were notified in September. [source] | |
Saint Francis Broken Arrow (Broken Arrow Medical Center) had a data breach in 2011, in Oklahoma. A computer that had not been used since May of 2004 was stolen from a secured information systems room. Patient billing information and some employee records were exposed. The information would have included names, Social Security numbers, dates of birth, addresses and patient insurance and diagnostic information. [source] | Saint Mary's Hospital, Naugatuck Valley Community College had a data breach in 2012, in Connecticut. A Naugatuck Valley Community College instructor used patient X-rays from St. Marys Hospital to teach radiology technology. The instructor obtained the X-rays by using his Saint Marys employee login to access medical records. The X-rays were used without permission and contained patient names, dates of birth, and physician notes. The instructor told students not to disclose the practice. [source] | |
Saint Mary's Regional Medical Center had a data breach in 2008, in Nevada. An unauthorized person may have accessed the St. Marys database. The database, used for Saint Marys health education classes and wellness programs, contained personal information such as names and addresses, limited health information and some Social security numbers. The database did not contain medical records or credit card information. [source] | Salina Family Healthcare Center had a data breach in 2014, in Kansas. Salina Family Healthcare Center (SFHC) notified more than 500 patients of an unintentional transmission of unsecured personal patient protected health information after discovering the following event: On April 8, 2014, a staff member submitted a database to the National Commission for Quality Assurance (NCQA) for our involvement in a care coordination research study. The staff member responsible for our participation in the project inadvertently left a table in that database that included patients’ names, dates of birth, chart numbers and CPT codes associated with their care. Upon opening the email, the NCQA staff member who received the database immediately recognized the breach, deleted the database, and notified our staff member. [source] | |
Salina Regional Health Center had a data breach in 2007, in Kansas. A laptop was stolen from a Hospital office. It contained names, Social Security numbers and medical histories of patients. Only patients treated by the laptop user are at risk for identity theft. [source] | Samaritan Hospital, Rensselaer County Jail had a data breach in 2013, in New York. A nursing supervisor of Rensselaer County Jail was found to have misused credentials to access patient records without cause. The Rensselaer County Jail information is maintained by Samaritan Hospital. The hospital learned of the breach in November 2011, disabled the employees account, and notified the sheriffs office immediately. Subsequently, the Hospital may have delayed notifying patients because of the ongoing investigation. Notifications were sent out during the first week of March in 2013.UPDATE(04/01/2013): A total of 48 people have been notified. Patients from as far back as 2006 may have been affected. [source] | |
San Antonio Metropolitan Health District had a data breach in 2014, in Texas. San Antonio Metropolitan Health District announced a data breach involving vaccination records of 300 children when a laptop containing these records was stolen.The records included first and the last name of the patient, the patient's date of birth, an identifier for the patient's doctor, and the name of the immunizations. The laptop has since been recovered. [source] | San Diego Regional Center had a data breach in 2010, in California. A back-up tape created for the purpose of disaster recovery testing and training was lost during shipping to the California Department of Developmental Services by UPS. Consumers first and last names, Social Security numbers, contact, diagnostic and medical information may have been exposed. Extracting information from the tape requires sophisticated technology, according to the breach notice letter. [source] | |
San Jose Medical Group had a data breach in 2005, in California. The information was breached via Network Server. [source] | San Mateo Medical Center had a data breach in 2014, in California. Name, ssn, dln, passport number, email address, job titles were breached. [source] | |
Santa Cruz Biotechnology, Inc. had a data breach in 2017, in California. The information was breached via Paper/Films. [source] | Santa Rosa Memorial Hospital, Privacy Manager Breach had a data breach in 2014, in California. A thumb drive containing data pertaining to X-rays provided between February 2, 2009 and May 13, 2014, was believed to have been stolen from a staff member's locker during a burglary that occurred on June 2, 2014, at the Santa Rosa Memorial Imaging Center. The thumb drive contained information pertaining to X-rays provided by the Redwood Regional Medical Group and Santa Rosa Memorial Hospital. The types of electronic protected health information (ePHI) included in the breach included names, medical record numbers, dates of birth, genders, dates and times of service, body part(s) examined, names of technologists, and data related to the amount of radiation to produce the X-ray. The breach affected approximately 33,702 individuals. [source] | |
Schneck Medical Center had a data breach in 2013, in Indiana. A Schneck Medical Center employee gave a presentation that was later placed online. People who searched through the files from the presentation could find the names of 3,000 Schneck Medical Center patients. The presentation was removed from online and Google removed all cached information from the Internet. [source] | Schurman Retail Group had a data breach in 2017, in California. [source] | |
Scoppechio had a data breach in 2018, in Kentucky. [source] | Scott County Memorial Hospital had a data breach in 2011, in Indiana. A surgeon, had a palm pilot device stolen from his parked vehicle on or around the morning of July 13, 2011. It held patient names, dates of birth, surgical procedures, diagnoses, and anesthesia. Patients who had seen the surgeon between December 27, 2007 and June 24, 2011 were affected. [source] | |
Seattle Indian Health Board had a data breach in 2016, in Washington. The Seattle Indian Health Board experienced a security attack to an employee email account on August 10, 2016. Access to the account lasted approximately 4 hours before the Seattle Indian Health Board IT department shut down the email system. The information accessed may or may not have included patients’ names, date of birth, patient ID numbers, social security numbers or other protected health information. The security of patient data is extremely important to us and we are taking this attack seriously as well as informing our patients directly and notifying the public about this incident. [source] | Select Pain & Spine Dr. Christopher T. Sloan, D.P.M. had a data breach in 2016, in Missouri. [source] | |
Select Physical Therapy had a data breach in 2008, in Texas. The company dumped about 4,000 pieces of sensitive customer information in garbage containers behind its facility. The records included Social Security numbers, credit and debit card account numbers, names, addresses and telephone numbers. [source] | Sentara Heart Hospital had a data breach in 2015, in Virginia. [source] | |
Sentara Heart Hospital had a data breach in 2015, in Virginia. Sentara Heart Hospital notified patients of a data breach when two portable hard drives were stolen. According to authorities the theft occurred the weekend of August 14, 2015. The information on the hard drives included birthdates, names, diagnoses, types of procedures and other clinical notes. According to the clinic no Social Security numbers or addresses were on the portable drives. [source] | Sentara Virginia Beach General Hospital had a data breach in 2013, in Virginia. Two men claimed to be from a recycling company and stole over 200 pounds of x-ray film that contained sensitive patient information. The men transported the x-rays from the hospital without incident by using a moving truck. The breach occurred in 2012 and affected less than 500 patients. [source] | |
Seton Health System had a data breach in 2006, in New York. [source] | Seton Healthcare Family, HealthLOGIX had a data breach in 2012, in Texas. A computer mailing error caused Seton member Medicaid health plan cards to be sent to incorrect addresses. The cards were mailed by Setons vendor HealthLOGIX on March 9. Seton became aware of the breach when members began calling about receiving the incorrect cards a week after the mistake. Seton Health Plan members enrolled in the STAR/Medicaid plan were affected and may have had their names and dates of birth exposed. [source] | |
Seton Healthcare Network had a data breach in 2007, in Texas. A laptop with uninsured patients names, birth dates and Social Security numbers was stolen last week from the Seton hospital system. The uninsured patients had gone to Seton emergency rooms and city health clinics since July 1, 2005. [source] | Seton Northwest Hospital had a data breach in 2014, in Texas. A computer-like device was stolen from Seton Northwest Hospital that is used in the sleep lab. The device according to the hospital, is a Hewlett Packard desktop device that is used to capture and manipulate data from sleep studies. \"It does not function like a normal computer. The operator would need a password and access to Seton systems to get a hold of patient data\". Reportedly the data consists of names, dates of birth and Seton account numbers.The device was stored inside a locked storage area at Seton Northwest Hospital, where the device was stolen. [source] | |
Shands at UF had a data breach in 2010, in Florida. Shands at UF sent notification letters to about 12,500 people Monday warning them that a laptop containing their personal and medical information was stolen. An employee had uploaded the information onto his home laptop for work-related purposes. The laptop held information about patients referred to the gastroenterology clinical services department. Included were names, addresses, medical record numbers, and in the case of 650 patients, Social Security numbers. [source] | Sharper Future had a data breach in 2014, in California. The Sharper Future, a mental health facility in Los Angeles has informed clients of a data breach when their offices were burglarized and various electronic equipment that stored patient records which includes names, dates of birth, health and clinical histories, treatment records, CDCR identification numbers and Social Security numbers of their clients.The facility did report that the information on the stolen equipment was password-protected and did not include financial information. The incident is currently under investigation by authorities. [source] | |
Sheppard Air Force Base had a data breach in 2012, in Texas. I man found medical records stacked in a bag in a closet while checking for financial records in the home of his estranged wife. The records date from 2003 to 2007 and involve the information of patients of Sheppard Air Force Bases 82nd Medical Group. Names, Social Security numbers, addresses, phone numbers, and in some cases, patient diagnoses were on the documents. [source] | Sierra Plastic Surgery had a data breach in 2012, in Nevada. A computer system error caused sensitive information to be exposed. The breach occurred sometime between August 19, 2011 and September 20, 2011.UPDATE(11/28/2012): It appears that the breach was related to a terminated employee who could still access Sierra Plastic Surgerys network after leaving the company. The former employee accessed Social Security numbers, personal contact information, payment information, and other sensitive information in less than 50 instances. It also appears that some copies of patient surgery estimates were printed and subsequently surrendered by the former employee when the breach was discovered in August of 2012. The former employee was seeking information on compensation owed. [source] | |
Sierra View District Hospital had a data breach in 2013, in California. Credit card payment info was breached via email . [source] | Silver Creek Fitness & Physical Therapy had a data breach in 2016, in California. On September 11, 2016, we were notified by our billing and software companies that their Amazon “S3” storage account was vulnerable because it was accessible to persons outside their organization, and that a security researcher who works for a software company accessed and downloaded information from the account. This storage account contained, among other things, protected health information of certain Silver Creek Fitness & Physical Therapy, Silver Creek Physical Therapy Gilroy, Silver Creek Physical Therapy Sunnyvale, and Silver Creek Physical Therapy Los Gatos patients. The billing and software companies immediately took steps to secure the storage account and launched an investigation to determine whether any sensitive information was accessed or acquired. They determined that the storage account was vulnerable from May, 2016 to September 11, 2016. However, we have no indication that any fraud has resulted from this incident. While we have no indication that any fraud has resulted from this incident, we have confirmed that the data affected by this incident possibly included your name, Medicare number, prescription, date of birth, treatment location, treatment date, Social Security number, drivers license number, and progress notes. This information may have been downloaded by the security researcher on or around September 10, 2016 and may have been accessible to individuals who were able to access the “S3” account. [source] | |
Silver Cross Hospital had a data breach in 2017, in Illinois. A northeastern Illinois hospital has experienced a data breach that exposed patient information of up to 9,000 people.Officials of Silver Cross Hospital in New Lenox said there's no evidence showing any unauthorized people gained access to the data.Silver Cross Hospital recently learned that a vendor that manages parts of its website experienced a data incident that affected the information of certain Silver Cross patients and others, hospital officials said on its website.Names, Social Security numbers, health insurance information, addresses, birth dates were compromised [source] | Silverberg Surgical and Medical Group had a data breach in 2015, in California. The information was breached via Network Server. [source] | |
Sinai Medical Center of Jersey City LLC had a data breach in 2013, in New Jersey. A pediatrician misused patient information in order to defraud Medicaid of nearly one million dollars. The pediatrician owned Sinai Medical Center and billed Medicaid for wound repairs and other procedures that were never performed. Police arrested the dishonest pediatrician on January 16, 2013. [source] | Sisters of St. Francis Health Services via Advanced Receivables Strategy (ARS), a Perot Systems Company had a data breach in 2006, in Indiana. On July 28, 2006, a contractor working for Advanced Receivables Strategy, a medical billing records company, misplaced CDs containing the names and SSNs of 266,200 patients, employees, physicians, and board members of St. Francis hospitals in Indiana and Illinois. About260,000 patients and about 6,200 employees, board members and physicians were affected for a total of 266,200. Also affected were records of Greater Lafayette Health Services. The disks were inadvertently left in a laptop case that was returned to a store. The purchaser returned the disks. The records were not encrypted even though St. Francis and ARS policies require encryption. [source] | |
Sitka Wellness Center, EMR4Doctors.com had a data breach in 2011, in Alaska. A patient discovered their own personal information and that of 565 others online. Patient names, Social Security numbers, addresses, and dates of birth were exposed. A chiropractor from the Sitka Wellness Center claims that an electornic medical record software vendor known as EMR4Doctors.com stored the patient information for 9 months in 2008. The company stopped doing business in 2009. The information was removed from the Internet. [source] | Sky Lakes Medical Center, Verus Inc. had a data breach in 2007, in Oregon. On January 1st, the Syrian Electronic Army is reportedly taking credit for hacking into user accounts on Skype. The amount of users affected is unknown. Reportedly, the hackers infiltrated a users account and monitors the activity and sells the data. [source] | |
Skype breach had a data breach in 2014, in Washington. On January 1st, the Syrian Electronic Army is reportedly taking credit for hacking into user accounts on Skype. The amount of users affected is unknown. Reportedly, the hackers infiltrated a users account and monitors the activity and sells the data. [source] | Smile Designs had a data breach in 2012, in Florida. The theft of a computer on or aroudn December 1, 2011 resulted in the exposure of personal information. [source] | |
Snake River Farms had a data breach in 2017, in Idaho. Agri Beef Co. (“Agri Beef”) is writing to inform you of a data security incident that may have exposed some of your personally identifiable information (“PII”) submitted to our website snakeriverfarms.com (“Snake River Farms”). What Happened?Gorilla Group, a third-party partner that hosts Snake River Farms servers, advised us that a data security incident occurred during the window of November 22, 2016 to April 4, 2017, and Gorilla Group notified Agri Beef of the incident on April 5, 2017. During the window, a third party may have gained access to snakeriverfarms.com with the intent to obtain certain PII. The PII compromised includes: customer names, email addresses, billing addresses, telephone numbers, credit card/debit card numbers, credit card/debit card security codes and expiration dates, the credit card type, and the date of the transaction. After learning of the data breach on April 5, 2017, we have been working, with the aid of outside resources, to help you avoid and/or minimize as much as possible, any negative consequences. Our notification has not been delayed as a result of any law enforcement investigation. What Information Was Involved?The potentially compromised information relates to your transactions on the Snake River Farms website. As explained above, PII that may have been compromised includes: customer names, email addresses, billing addresses, telephone numbers, credit card/debit card numbers, credit card/debit card security codes and expiration dates, the credit card type, and the date of the transaction. Compromised information could be usedto attempt to fraudulently charge your credit or debit card. [source] | Sonoma Valley Hospital had a data breach in 2013, in California. An employee error caused patient information from surgeries to appear on the internet. Names, dates of service, procedures, surgeons, hospital charges, and names of insurance companies were accidentally uploaded. The breach occurred on February 14 and was discovered on April 17. [source] | |
South County Hospital had a data breach in 2007, in Rhode Island. The information was breached via Email. [source] | South Florida State Hospital, GEO Care LLC had a data breach in 2013, in Florida. A dishonest employee and his cousin pleaded not guilty to charges of conspiracy to commit identity theft, conspiracy to disclose individuals health information, access device fraud, wrongful disclosure of health information, and aggravated identity theft. The men are accused of stealing the names and Social Security numbers of patients to file fraudulent income tax returns between September of 2012 and April of 2013. [source] | |
South Miami Hospital, Baptist Health had a data breach in 2013, in Florida. A dishonest hospital employee misused patient records that were dated from June 2011 to February of 2012. Patients may have had their names, Social Security numbers, and dates of birth exposed.UPDATE(03/15/2013): A respiratory therapist provided Social Security numbers, dates of birth, patient names, and other patient data in exchange for payment. The patient data was then used to file fraudulent tax returns. The dishonest employee now faces charges for selling the information to two others.UPDATE(04/26/2013): Two women who purchased patient information from a Hospital employee were sentenced for their roles in the breach. One woman was sentenced to 26 years and five months in federal prison in addition to being ordered to pay over $1.9 million in restitution. She was convicted of 33 fraud and identity theft charges in January. The other was sentenced to 10 years and one month in prison after pleading guilty to conspiracy to defraud the government and aggravated identity theft. The fraud ring produced fraudulent income tax refunds totalling $11.7 million. [source] | South Shore Hospital, Active Data Solutions had a data breach in 2010, in Massachusetts. Computer files containing personal, health and financial information of volunteers, patients, vendors, business partners and employees from January 1996 through January 2010 may have been lost by a professional data management company. Depending on the persons association with the hospital, the information exposed could be full name, address, phone number, date of birth, Social Security number, drivers license number, medical record number, patient number, bank account information, credit card number, diagnoses and treatment.UPDATE (9/10/10): Archive Data Solutions (formerly Iron Mountain Data Products) was revealed to be the company responsible for disposing of South Shore Hospitals records. Archive Data Solutions subcontracted the process to Graham Magnetics, who then lost the tapes in shipping. The tapes may have also had patient information from Harbor Medical Associates and patient and vendor information from South Shore Physician Hospital Organization.After investigating the incident the hospital decided not to mail notices or offer credit monitoring and identity theft services to those who may have been affected by the loss. It was determined that the risk of the data being accessed was extremely low and that notifications inside the hospital, on websites, via email and in newspapers would be enough. In addition, the Attorney Generals office of Massachusetts has spoken out against the hospitals decision to skip precautions. [source] | |
South Sunflower County Hospital had a data breach in 2015, in Mississippi. A local merchant sent a package with shredded documents containing protected health information (PHI) from the covered entity (CE), South Sunflower County Hospital, used as packing material.The information compromised included dates of service, providers names, diagnoses, patient names, Social Security numbers, and dates of birth. [source] | Southern Perioperative Services, P.C. had a data breach in 2011, in Alabama. A device with protected health information of patients was stolen on or around November 17, 2010. [source] | |
Southwest Medical Association had a data breach in 2008, in Nevada. [source] | Southwest Seattle Orthopaedic and Sports Medicine had a data breach in 2010, in Washington. A hacking incident may have exposed the personal information of patients on September 4. [source] | |
Spartanburg Regional Hospital had a data breach in 2011, in South Carolina. The March 28 theft of a laptop resulted in the exposure of patient information. The laptop was stolen from an employees car on March 28. It contained patient names, Social Security numbers, addresses, dates of birth and medical billing codes. Spartanburg Regional has not revealed the number of affected patients.UPDATE(7/03/2011): Spartanburg Regional notified HHS that 400,000 patients were affected. [source] | Speare Memorial Hospital had a data breach in 2011, in Maryland. Dozens of boxes were found in an apartment complex dumpster. Hundreds of patient records, copies of Social Security cards and copies of drivers licenses were left exposed. [source] | |
Spectrum Family Medical had a data breach in 2008, in Nevada. Dozens of boxes were found in an apartment complex dumpster. Hundreds of patient records, copies of Social Security cards and copies of drivers licenses were left exposed. [source] | Spectrum Health Systems, Inc. had a data breach in 2011, in Massachusetts. The information was breached via Laptop. [source] | |
St. Anthony Central Hospital had a data breach in 2009, in Colorado. Boxes, filing cabinets and trash bags full of hundreds of U.S. passports, birth certificates, drivers licenses, Social Security cards and other documents - most stolen within the past two years were found in a storage unit. A hospital employee admitted to stealing the records. Also found were hospital records containing dates of birth, Social Security numbers and copies of the drivers licenses of 150 patients who had been admitted into the emergency room or general surgery. [source] | St. Catherine Medical Center had a data breach in 2012, in Pennsylvania. The information was breached via Electronic Medical Record. [source] | |
St. Charles Bend and Redmond had a data breach in 2011, in Oregon. A laptop was stolen from a St. Charles employees car in late October. It contained the personal information of 140 patients who were seen in the St. Charles Bend or St. Charles Redmond emergency room. The laptop was discovered in brush by an elementary school student in late November. After the laptop was returned on December 16, it was discovered that attempts to gain unauthorized access to its contents had failed. [source] | St. Elizabeth's Medical Center had a data breach in 2012, in Massachusetts. Name, address, phone number, email address, ssn were breached. [source] | |
St. Francis Hospita and Medical Centers had a data breach in 2014, in Connecticut. [source] | St. Francis Hospital had a data breach in 2010, in Oklahoma. A Sand Springs woman has been indicted on allegations that she used personal identifying information she copied from her then-employers computer system as part of a scheme involving fraudulent credit cards and stolen mail. The indictment was released Wednesday in federal court in Tulsa and states that the 45 year old woman exceeded her computer-access authority at St. Francis Hospital to obtain information such as Social Security numbers and dates of birth of at least 60 people.UPDATE(11/24/10): A second woman was sentenced for her role in the credit card fraud case. Both women had been employed at Saint Francis. Patient names, Social Security numbers and addresses obtained between August 6 and December 28 of 2009 were used to illegally obtain credit cards. [source] | |
St. Francis Hospital had a data breach in 2011, in Delaware. A doctor lost a thumb drive that contained the personal health care information of 474 maternity patients. It did not contain names, financial information or SSNs. The thumb drive was returned to the doctor on June 11 by an anonymous sender. The doctor had not realized it was missing and reported the incident to St. Francis on June 13. The doctor was authorized to remove the thumb drive from the Hospital, but it should have been encrypted and password protected. [source] | St. James Hospital and Health Centers had a data breach in 2010, in Illinois. The improper disposal of paper documents may have left the health information of patients of Saint James Hospital and Health Centers exposed. The incident occurred on or around August 10. [source] | |
St. John's Mercy Medical Group had a data breach in 2010, in Missouri. Patient files were found outside a doctors office. The doctor admitted to failing to shred the old papers and claimed that he ran out of space for the files. UPDATE (8/25/10): Reports state that 1,907 patients were notified. The patient files included contact and credit card information, Social Security numbers and dates of birth. [source] | St. Joseph Health System had a data breach in 2012, in California. Protected patient information may have been available on the internet for one year. A patients attorney contacted St. Jude officials to inform them that the information was available online. The patient health records included names, body mass index, blood pressure, lab results, smoking status, diagnoses lists, medication allergies, and demographic information such as gender, date of birth, language spoken, ethnicity, and race. The information was removed from online and co no longer be accessed by unauthorized parties. A total of 6,235 patients from Santa Rosa Memorial Hospital, two from Petaluma Valley Hospital, 4,263 from Queen of the Valley in Napa, and an unknown number of patients from St. Jude Medical Center in Fullerton, and Mission Hospitals in Laguna Beach and Mission Viejo were affected.UPDATE(07/10/2012): The California Department of Public Health was still investigating Queen of the Valley Medical Center as of July 10, 2012. Additionally, two patients who were treated at Santa Rosa Memorial Hospital, filed a class action lawsuit on behalf of the 31,800 patients who were affected. They seek $31.8 million, or $1,000 per patient. [source] | |
St. Joseph Medical Center, Baxter, Baker, Sidle, Conn & Jones had a data breach in 2011, in Maryland. A Baltimore law firm called Baxter, Baker, Sidle, Conn and Jones lost a hard drive with patient records. It contained patient names, Social Security numbers, medical records, addresses, dates of birth, and insurance information. The law firm was using the medical records of patients who were suing a cardiologist at St. Joseph Medical Center. The hard drive was lost by an employee during travel on August 4. Patients were informed in early October. [source] | St. Joseph Medical Center had a data breach in 2011, in Maryland. The information was breached via Email. [source] | |
St. Joseph's Hospital and Medical Center had a data breach in 2017, in Arizona. The information was breached via Electronic Medical Record . [source] | St. Joseph's Medical Center had a data breach in 2012, in California. A storeroom window at Saint Josephs HealthCare Clinical Laboratory (HCCL) was discovered broken on February 2, 2012. Two storage boxes containing HCCL lab requisition forms were missing from the center. People who received laboratory services betweenOctober 24, 2011 and November 18, 2011, betweenDecember 13, 2012 and January 5, 2012, and also between January 17, 2012 and January 31, 2012, may have had their names, Social Security numbers, phone numbers, addresses, and insurance information exposed.UPDATE(4/26/2012): At least 700 patients were affected. Two boxes were discovered missing immediately after the robbery and a third was discovered missing on March 16. [source] | |
St. Jude Heritage Medical Group had a data breach in 2010, in California. 20,000 patients may have had their personal information stolen after a break-in at the St. Jude Heritage Healthcare Clinical Management Services building in Fullerton. The thieves stole five computers. The stolen patient data included Social Security numbers, dates of birth and in some cases, health related information. [source] | St. Lukes Cornwall Hospital had a data breach in 2016, in New York. [source] | |
St. Mark's Medical Center had a data breach in 2013, in Texas. An employees computer was found to contain malware. The malware infection began on May 21, 2012 and was discovered on November 15, 2012. Files stored on the computer contained billing information with patient names, Social Security numbers, account numbers, medical record numbers, dates of birth, gender, treatment dates, insurance provider names, and account balances. [source] | St. Mark's Surgery Center had a data breach in 2017, in Florida. St. Mark’s Surgery Center was hit by a ransomware attack that may have impacted the personal health information of 33,877 patients.The Florida provider discovered a ransomware attack on May 8, although the attack occurred from April 13 until April 17. The installed virus prevented patient data from being accessed during that time.The impacted servers contained patient names, dates of birth, Social Security numbers and medical information. [source] | |
St. Marks Surgery Center had a data breach in 2017, in Florida. St. Mark’s Surgery Center was hit by a ransomware attack that may have impacted the personal health information of 33,877 patients.The Florida provider discovered a ransomware attack on May 8, although the attack occurred from April 13 until April 17. The installed virus prevented patient data from being accessed during that time.The impacted servers contained patient names, dates of birth, Social Security numbers and medical information. [source] | St. Mary and Elizabeth Hospital Women's Center had a data breach in 2010, in Kentucky. A hard drive was stolen from a locked area. Medical information such as biopsy images, patient names, and medical exams were on the stolen hard drive. [source] | |
St. Mary Medical Center had a data breach in 2012, in California. An unencrypted thumb drive was lost on May 7 and discovered missing on May 8. It contained the names, account numbers, diagnoses, dates of admission and discharge, physicians name, account numbers, and medical record numbers of patients. It is unclear if only one Saint Mary Medical Center in California was affected, and if so, which one. The incident was posted on the HHS website on June 8. [source] | St. Peter's Ambulatory Surgery Center LLC - d/b/a St. Peter's Surgery & Endoscopy Center had a data breach in 2018, in New York. The information was breached via Network Server . [source] | |
St. Peter's Hospital had a data breach in 2010, in New York. An East Greenbush man who worked as a medical records clerk at St. Peters Hospital is accused of stealing personal information from patients files to open credit card accounts. The man allegedly stole Social Security numbers and other personal information from patients records, then used the data to open credit card accounts for making personal purchases online. The man was charged April 12 with five counts of felony second-degree forgery, three counts of felony second-degree identity theft and three counts of misdemeanor second-degree criminal impersonation. [source] | St. Rita's Medical Center had a data breach in 2009, in Ohio. A home-health employee for St. ritas Medical Center had a bag stolen during an automobile break-in. the bag contained information on some patients, including names, dated of birth, addresses, phone numbers, patient identification numbers, and the names of case managers and physicians. In some cases it also included Social Security numbers and the type of treatment being provided, according to a letter given to the patients involved. [source] | |
St. Therese Medical Group had a data breach in 2012, in California. A July 22 Saint Therese office theft of a computer resulted in the exposure of patient information. The computer was unencrypted; however, it was password protected.Names, Social Security numbers, dates of birth, health insurer names, dates of treatment, amount billed, and account balances were exposed. Notifications were sent on September 17. [source] | St. Vincent Breast Center had a data breach in 2014, in Indiana. The information was breached via Laptop. [source] | |
St. Vincent Hospital (Saint Vincent) had a data breach in 2010, in Indiana. A computer was stolen from an employees home on July 25. The computer had patient Social Security numbers and other personal health information. Patients were notified in late September. [source] | St. Vincent Hospital, Verus, Inc. had a data breach in 2007, in Indiana. Saint Vincent used subcontractor Verus Inc. to set up an online bill payment for patients. For a brief period of time, personal information was left unprotected and available online. The security lapse compromised names, addresses and Social Security numbers. [source] | |
St. Vincent Hospital had a data breach in 2011, in Indiana. In November, Saint Vincent officials learned that several associate email accounts had been breached. A third party managed to obtain email logins. Patient names, dates of service and clinical information may have been accessed. [source] | St. Vincent Warrick had a data breach in 2017, in Indiana. St. Vincent learned of an inadvertent disclosure of 1 record on 12/15 2017, including name and social security number, and notified the consumer on 1/10/2018. [source] | |
Sta-Home Health & Hospice had a data breach in 2010, in Mississippi. A September 15 office burglary resulted in the theft of a desktop computer. The computer once held protected health information of people with state Medicaid claims. Some files included encoded names and diagnostic codes. Medicaid account numbers, financial information and Social Security numbers were not exposed. [source] | Stallcup & Associates, CPAs had a data breach in 2016, in California. The information was breached via Network Server. [source] | |
Stamford Podiatry Group PC had a data breach in 2016, in Connecticut. [source] | Stanford School of Medicine, Lucile Packard Children's Hospital had a data breach in 2013, in California. The January 9 theft of a laptop from a physicians car may have exposed sensitive information. The laptop may have contained some combination of patient names, dates of birth, and contact information.UPDATE(01/22/2013): A total of 57,000 patients are being notified. Medical information and medical record numbers were exposed. A limited number of patients had their contact information exposed. Most of the information on the laptop was from 2009. [source] | |
Stanford University Hospital and Clinics had a data breach in 2011, in California. [source] | Stanford University Medical Center, Stanford Hospital and Clinics, Stanford School of Medicine had a data breach in 2012, in California. A burglary sometime around July 15 resulted in the theft of a computer from a Stanford faculty members locked office.The computer contained patient information. No medical records or health histories were stored on the computer, but it may have held the Social security numbers of some patients. The computer was outfitted with security software that would detect when and where the computer connected to the internet.UPDATE(08/13/2012): The stolen computer was also password-protected. It may have contained medical record numbers, dates of service, and the names of providers and clinics relating to care provided at Stanford Hospital and Clinics or research conducted by the Stanford School of Medicine. [source] | |
Stanislaus Surgical Hospital had a data breach in 2015, in California. On April 4, 2015, two paper binders containing the protected health information (PHI) of up to 1,166 individuals were stolen from one of the covered entity’s (CE) facilities along with several other items that did not contain PHI. The type of PHI involved in the breach was financial information. The CE filed a formal police report and police identified two potential suspects. The CE provided breach notification to HHS, affected individuals, and the media and offered credit monitoring to all individuals affected. Following the breach, the CE improved physical security for the facility and the locked file cabinets that contain PHI and updated security procedures for employees’ access to the premises. It also converted its payment system to a paperless, all electronic system and implemented an encryption requirement for all information that is stored on a shared drive. The CE also trained all employees on the changes to its security policies and procedures. OCR obtained assurances that the CE implemented the corrective actions listed. [source] | State of California - Department of Corrections and Rehabilitations (CDCR) Parole Outpatient Clinic had a data breach in 2005, in California. The information was breached via Desktop Computer. [source] | |
State of Minnesota had a data breach in 2015, in Minnesota. Driver's license information of 18 St. Paul residents "were accessed after a password-protected portal was inadvertentlly opened online."According to officials a server update inadvertently removed the authentication processes in place when accessing the online portal system for drivers license information. According to these same officials, only two individuals utilized this portal 55 time from August 2, 2015 and August 24, 2015, showing 18 individuals information was accessed during this time frame. The information included pictures, names, addresses and dates of birth. [source] | Staten Island University Hospital had a data breach in 2008, in New York. Computer equipment stolen from an administrator contained personal information from patients. Social security numbers and health insurance numbers were contained in computer files on a desktop computer and the backup hard drive. [source] | |
Stevens Hospital Emergency Room via dishonest employee of billing company Med Data had a data breach in 2006, in Washington. A manager for the hospitals billing company, Med Data, stole patients credit card numbers. She gave them to her brother who bought $30,000 worth of clothes and gift cards over the Internet. The woman is scheduled for sentencing in nov. and her brothers trial is expected Jan. 2007. [source] | Stone Oak Urgent Care and Family Practice had a data breach in 2011, in Texas. A computer or laptop was discovered to have been lost or stolen on or around October 23, 2011.UPDATE (12/28/2011): A total of five computers containing medical and personal information were stolen from a physicians office during the breach. A thief had pried open an office door during the weekend of October 22-23. Patients were informed on December 5 that their names, Social Security numbers, dates of birth, account numbers, disability codes, and diagnoses were stored on the computers. [source] | |
Strong Memorial Hospital had a data breach in 2010, in New York. Around half of all patient medical bills were sent to the wrong address. The billing statements included patient names, name and address of the person responsible for paying the bill, description of services received and the dates of services, dollar amount owed, health insurance plan and subscriber number. Around 1,250 patients were affected. [source] | Summit Medical Group, Emory Family Practice, Fountain City Family Physicians, Office of Dr. Kenneth Reese had a data breach in 2011, in Tennessee. [source] | |
Sunglo Home Health Services had a data breach in 2015, in Texas. The information was breached via Laptop. [source] | Surgical Associates of Utica, Quanterion Solutions, Inc. had a data breach in 2012, in New York. The theft of a network server on or around September 18 may have resulted in the exposure of sensitive patient information. A notification was sent to the US Department of Health and Human Services (HHS) on November 16. [source] | |
Sutter Gould Medical Foundation (SGMF) had a data breach in 2011, in California. Around 1,200 patient records were misplaced on May 27 and were buried in a landfill. The box of records contained patient names, Social Security numbers, addresses, diagnostic test results, provider notes and correspondence, disability forms and insurance information. An unnamed SGMF vendor is responsible for displacing the box. [source] | Sutter Health's Alta Bates Summit Medical Center, Sutter Delta Medical Center, Eden Medical Center had a data breach in 2013, in California. [source] | |
Sutter Lakeside Hospital had a data breach in 2007, in California. A laptop computer containing personal and medical information of approximately 45,000 former patients, employees and physicians has been stolen from the residence of a contractor. [source] | Sutter Physicians Services (SPS) and Sutter Medical Foundation (SMF) had a data breach in 2011, in California. A company-issued password-protected unencrypted desktop computer was stolen from SMFs administrative offices during the weekend of October 15, 2011. Approximately 3.3 million patients whose health care provider is supported by SPS had their names, addresses, dates of birth, phone numbers, email addresses, medical record numbers and health insurance plan name exposed. The information dated from 1995 to January of 2011. An additional 934,000 SMF patients had dates of services and description of medical diagnoses and/or procedures used for business operations in addition the the previously listed information exposed. This information dated from January 2005 to January 2011. Patients will receive notification letters no later than December 5.UPDATE (11/23/2011): Two lawsuits have been filed against Sutter Health. One class-action suit alleges that Sutter Health was negligent in safeguarding its computers and data and then did not notify the millions of patients whose data went missing within the time required by state law. The suit seeks $1,000 for each member of the class and attorneys fees. [source] | |
SVR Tracking had a data breach in 2017, in California. [source] | Swedish Medical Center, Ballard Campus had a data breach in 2006, in Washington. An employee stole the names, birthdates, and Social Security numbers from patients who were hospitalized or had day-surgeries from June 22 to Sept 21. She used 3 patients information to open multiple credit accounts. [source] | |
Swedish Urology Group had a data breach in 2007, in Washington. [source] | SwedishAmerican Hospital had a data breach in 2012, in Illinois. Around 1,500 X-ray films were stolen from SwedishAmerican Hospital on May 31. Someone claiming to be the person responsible for picking up and destroying the films was able to steal them. Patient names, medical record numbers, dates of service, and dates of birth were exposed. Representatives believe the risk of identity theft is low since extracting the silver from X-ray films is usually the motive for similar thefts. [source] | |
Synergy Specialists Medical Group had a data breach in 2016, in California. The information was breached via Email. [source] | SynerMed, Inland Valleys IPA, Inland Empire Health Plan had a data breach in 2013, in California. The theft of an employees laptop resulted in the exposure of patient information. The theft occurred on the night of April 14 or the early morning of April 15 when a thief broke into the employees automobile. The laptop was password-protected and reported missing on the morning of the April 15. The laptops access to the SynerMed systems was eliminated on the morning of April 15 and the laptop contained member names, membership numbers, member addresses, CPT Codes, Diagnosis Codes, and dates of birth.UPDATE(06/07/2013): The laptop belonged to a group of independent California physicians managed by SynerMed, Inc. called Inland Valleys IPA.UPDATE(06/17/2013): There were no Social Security numbers on the laptop.UPDATE(06/21/2013): A total of 1,566 people were affected. [source] | |
Tallahassee Memorial HealthCare had a data breach in 2013, in Florida. A former Tallahassee Memorial HealthCare food service employee was indicted on 31 counts of filing false tax returns, wire fraud, false claims, and aggravated identity theft. He and two others are believed to have participated in a conspiracy that led to $818,000 in fraudulent claims. The employee worked for Tallahassee Memorial HealthCare for three years. He gathered patient names and dates of birth from food tray receipts when he delivered food to the rooms of patients in August of 2011 and stole emergency room data sheets from the trash. The information was then passed to the two others who participated in the conspiracy. [source] | Tampa General Hospital had a data breach in 2014, in Florida. The information was breached via Electronic Medical Record. [source] | |
Target America Inc., University of California, San Francisco (UCSF) had a data breach in 2008, in California. Information on UCSF patients was accessible on the Internet. The information accessible online included names and addresses of patients along with names of the departments where medical care was provided. Some patient medical record numbers and the names of the patients physicians also were available online. [source] | Tarleton Medical had a data breach in 2017, in California. Names, addresses, dates of birth, Social Security numbers, and data related to health care claims were breached. [source] | |
Tarleton Medical had a data breach in 2017, in Texas. Names, addresses, dates of birth, Social Security numbers, and data related to health care claims were breached via Website. [source] | Temple Community Hospital had a data breach in 2012, in California. The information was breached via Paper/Films. [source] | |
Tenet Healthcare Corporation had a data breach in 2008, in Texas. A ex-employee worked at a Frisco, texas, billing center for less than two years, and is confirmed to have stolen the names, Social Security numbers and other personal information of about 90 patients. The employee also had access to 37,000 other accounts. [source] | Terros Health had a data breach in 2018, in Arizona. The information was breached via Website. [source] | |
Texas Children's Hospital and Baylor College of Medicine had a data breach in 2010, in Texas. A physicians laptop was stolen from an office on May 13th. The laptop contained personal information on cardiology patients. Affected persons were notified that their names, dates of service, medical record numbers, diagnoses and dates of birth were on the password-protected laptop.UPDATE (9/2/10): Only 694 patients were affected. The original notice on the website stated that 1600 patients were at risk. [source] | Texas Health Arlington Memorial Hospital had a data breach in 2011, in Texas. Patient information was exposed during the process of converting information systems and processes to the same system as the other hospitals in the Texas Health group. A switch between Texas Health Arlington and SandlotConnect was turned on December 23, 2010. This allowed health information to go to SandlotConnect, a health information exchange, after patients signed an authorization form and the patients accounts were marked to permit the exchange of information. It was later determined that the SandlotConnect authorization form was not presented to patients at the time of registration since Texas Health Arlington employees were not aware that the switch had been turned on; registration employees were also marking patients accounts incorrectly. The switch was turned off and no further health information was sent after the breach was discovered on January 26, 2011. Each of the affected patients had their accounts marked as not participating in the health information exchange and Texas Health Arlington worked with Sandlot to shield the information from being further used or disclosed. Texas Health Arlington registration employees also received additional training on the Sandlot Connect health information exchange process. It appears that a majority of the accounts were accessed by Sandlot employees in order to shield the affected patients health information. Some SandlotConnect accounts were accessed by authorized health care providers for treatment purposes. [source] | |
Texas Health Harris Methodist Hospital Azle had a data breach in 2011, in Texas. [source] | Texas Health Presbyterian Hospital Flower Mound, Texas Health Partners had a data breach in 2011, in Texas. An employees company-issued laptop was stolen on June 21, 2011. The theft was reported immediately, but the laptop was not recovered. It contained 1) physical descriptions such as age, gender, weight, and height, 2) medical information such as date and time of admission, date and time of laboratory order, lab results, dates of service, diagnosis, discharge instruction and summary, name of physician, insurance, procedure, room number, medical history, and medical record number, and 3) personal information that included employer, marital status, phone number, name of account guarantor, and Social Security number for a small number of patients. [source] | |
Texas Tech University Health Sciences Center (TTUHSC) had a data breach in 2013, in Texas. An administrative error caused the billing statements of around 700 patients to be sent to the mailing addresses of other patients. Patient names, account numbers, invoice numbers, charge amounts, dates of service, department and provider names, adjustment amounts, payments from insurance companies, amounts due, and total account balances may have been exposed. [source] | The Brigham, Women's/Faulkner Hospital had a data breach in 2011, in Massachusetts. A physician who worked for both hospitals left an external hard drive in a piece of luggage. The luggage was lost in a cab on or around June 21. Information related to inpatient hospital stays from July 10, 2009, to January 28, 2011, may have been on the hard drive. The types of information that could have been on the device include patient names, medical record numbers, dates of admission, medications, and information about diagnosis and treatment. [source] | |
The Center for Neurosciences had a data breach in 2010, in Arizona. A visitor stole a laptop from an electromyogram and nerve conduction studies exam room on December 15, 2009. The computer contained names, dates of birth, referring physicians and reasons for neurophysiological tests. [source] | The Hand Care Center/Shoulder and Elbow Institute had a data breach in 2014, in California. The information was breached via Laptop. [source] | |
The Kent Center had a data breach in 2010, in Rhode Island. A briefcase with patient records was stolen from a clinicians car on July 13. The lost documents included client names, dates of birth and some clinical information. The patient records do not appear to have been the target of the theft since other cars were broken into during that night. [source] | The Lexington VA Medical Center had a data breach in 2011, in Kentucky. An employee took a laptop home without authorization. It contained patient names, dates of birth, the last four digits of patient Social Security numbers, and medical diagnoses. The employees actions were not believed to be intentionally malicious. [source] | |
The Lowell General Hospital had a data breach in 2017, in Massachusetts. The information was breached via Electronic Medical Record . [source] | The Medical Center had a data breach in 2010, in Kentucky. The information was breached via Desktop Computer. [source] | |
The Neighborhood Christian Clinic had a data breach in 2012, in Arizona. A portable electronic device was lost or discovered missing sometime around February 7, 2012. It contained sensitive information.The incident was reported on the HHS website. [source] | The Nemours Foundation had a data breach in 2011, in Delaware. The information was breached via Desktop Computer, Electronic Medical Record, Network Server, Other Portable Electronic Device, and Paper/Films. [source] | |
The Surgeons of Lake County, LLC had a data breach in 2012, in Illinois. A hacker or hackers accessed and encrypted the computer server of The Surgeons of Lake County. The incident occurred between June 22 and June 25 and was an attempt to force payment from The Surgeons of Lake County in exchange for the password needed to regain access to the server. The unauthorized user or users had access to names, Social Security numbers, addresses, credit card numbers, and medical information. [source] | The VA Caribbean Healthcare System had a data breach in 2011, in Puerto Rico. The information was breached via Electronic Medical Record and Network Server. [source] | |
The Washington State Liquor and Cannabis Board had a data breach in 2017, in Washington. The information was breached via Paper/Films. [source] | Thomas Jefferson University Hospitals (TJUH) had a data breach in 2012, in Pennsylvania. Law enforcement informed TJUH management that sensitive documents had been recovered during an investigation. Radiology registration documents with patient names, Social Security numbers, addresses, home phone numbers, work phone numbers, dates of birth, TJUH account numbers, TJUH medical record numbers, insurance information, emergency contact information, and special radiology studies performed had been stolen from TJUH. It is unclear when the theft occurred. Patients who received services between February 4 and March 22, 2005 were affected. [source] | |
Thomas Jefferson University Hospitals had a data breach in 2010, in Pennsylvania. A password-protected laptop was stolen from the office of an employee on June 14. The computer should not have contained protected health information, but did. It also contained the name, birth date, gender, ethnicity, diagnosis, Social Security number, insurance information, and hospital account number of approximately 24,000 patients. [source] | Titus Regional Medical Center (TRMC) had a data breach in 2012, in Texas. A nurse was fired after accessing patient medical records without cause. The unauthorized access exposed patient vital signs, diagnoses, and treatment notes. Patient Social Security numbers may have also been exposed. The breach was uncovered in November during an audit. [source] | |
Titus Regional Medical Center (TRMC) had a data breach in 2012, in Texas. The information was breached via Electronic Medical Record. [source] | Titus Regional Medical Center (TRMC) had a data breach in 2012, in Texas. The March 28, 2012 loss of a laptop during a routine patient transportation resulted in the exposure of protected health information. It was encrypted and password protected. The laptop was most likely let on the fender of an ambulance and lost during a route. Patient names, Social Security numbers, addresses, and medical data related to services provided by the EMS department may have been on the laptop. Notice of the breach was given on May 24. [source] | |
Tomah Memorial Hospital had a data breach in 2010, in Wisconsin. A nurse used patient names and account numbers to illegally obtain narcotics. The nurse was fired. [source] | Touchstone Medical Imaging had a data breach in 2014, in Tennessee. Name and credit card info were breached. [source] | |
TRICARE Management Activity had a data breach in 2011, in Colorado. Paper records with sensitive information were stolen on June 25, 2010. The types of information the paper records contained was not revealed. The breach does not appear to have been disclosed until May of 2011. [source] | Tri-City Medical Center had a data breach in 2010, in California. Employees shared patient information on Facebook. Differing reports leave it unclear if these employees were nurses, and whether or not they were fired. [source] | |
Trimont Real Estate Advisors had a data breach in 2018, in Georgia. From approximately January 30, 2018, through February 6, 2018, an unknown person, without authorization, had access to the business email account of a Trimont employee. Trimont first learned that the account was potentially compromised on February 6, 2018, and immediately terminated the intruder's access to the email account and launched an investigation. The investigation has determined that the compromise began with a phishing email sent by the unknown person to the employee on January 30, 2018. [source] | Trinity Medical Center (Montclair Baptist Medical Center) had a data breach in 2011, in Alabama. A former employee woman was caught stealing patient information for the purpose of identity theft. Hundreds of pages of information with patient names, Social Security numbers, dates of birth, and some medical information such as scheduled procedure were found at the employeeswomansresidential address. The information is from stolen surgery schedules and was taken between March 22 and April 1. The former employee woman was charged with violating the federal Health Insurance Portability and Accountability Act (HIPAA).UPDATE(2/01/2012): Additional details reveal that the woman was most likely not an employee of Trinity Medical Center and stole the logs of patient information while supposedly visiting a patient. The paper documents were stolen in a flamboyant way as the woman reportedly jumped over a counter to steal the logs. The files included information from people who had visited in 2006 when Trinity was known as Montclair Baptist Medical Center. The logs were recovered on April 8 through a USPS investigation.She pleaded guilty to the theft and was sentenced to 39 months in federal prison on February 1, 2012. She will also serve five years of supervised release after her prison time is served. [source] | |
Troy Regional Medical Center (TRMC), Southern Records Management Inc. had a data breach in 2011, in Alabama. TRMC discovered that someone had removed paper records that contained the information of approximately 880 patients. The unauthorized access and removal happened in early 2011 and was reported to TRMC by law enforcement on May 20, 2011. Affected patients had their names, Social Security numbers, addresses, dates of birth and medical record numbers exposed. It appears that some of the personal information was used to file fraudulent income tax returns with the IRS.UPDATE(06/13/2012): A woman was arrested on felony charges for allegedly conspiring with others to steal the information of 880 patients while she worked with Southern Records Management at TRMC. The 22-count felony indictment includes allegations of fraud against the U.S. government as part of a tax fraud scheme. [source] | Tuba City Regional Health Care Corporation had a data breach in 2011, in Arizona. [source] | |
Tumblr had a data breach in 2016, in New York. A third party accessed a set of Tumblr user email addresses with salted and hashed passwords.The credentials are from early 2013, prior to Tumblr's acquisition by Yahoo, officials said in a May 12 blog post. The site's security team investigated the matter as soon as it became aware of the incident. “Our analysis gives us no reason to believe that this information was used to access Tumblr accounts,” the blog said. Officials said in the blog that those affected will be required to set a new password as a precaution. Users are instructed to visit the sites security page for more information on how to keep their accounts secure". [source] | Tuolumne General Medical, PHNS (now under ConJoin Group) had a data breach in 2008, in California. Four laptop computers and one desktop computer were stolen from a Cerritos PHNS office. PHNS handles insurance-billing information for multiple medical centers. Up to 20,000 people may have been affected. Patients had their billing information, but not medical information, exposed. The other organizations affected by the PHNS breach were not reported, but were mostly in California. [source] | |
Turner Broadcasting Systems (Bleacher Report) had a data breach in 2016, in New York. On November 12, 2016, we became aware that an unauthorized party gained access to certain files containing limited Bleacher Report user information. We immediately began investigating the incident, and our investigation revealed that the unauthorized party accessed this user information sometime in or before early November 2016. We also reported the incident to law enforcement authorities.We concluded that the unauthorized party may have acquired the first name, last name, username (email address), and password for Bleacher Report's website and mobile application user accounts. The Bleacher Report website and mobile application do not collect credit card numbers or other sensitive personal information, such as Social Security numbers. [source] | Tween Brands, Inc. had a data breach in 2017, in Texas. [source] | |
Tx: Team Rehab, Inc. had a data breach in 2017, in Indiana. Tx:Team suffered a hack on 10/30/2017 that affected 6 records, including SS numbers as well as names and credit card or financial account information. [source] | U.S. Department of Defense had a data breach in 2006, in District Of Columbia. A hacker accessed a Tricare management Activity (TMA) public server containing personal information about military employees. TMA is used to provide health care services to military personnel and their families. [source] | |
U.S. Department of Veterans Affairs, VA Medical Center had a data breach in 2007, in Alabama. An employee reported a portable hard drive stolen or missing that might contain personal information about veterans including Social Security numbers. uPDATE (2/10/07): vA increases number of affected veterans to 535,000, included in the total below. uPDATE (2/12/07): vA reported that billing information for 1.3 million doctors was also exposed, including names and Medicare billing codes, not included in the total below. uPDATE (3/19/07): the VAs Security Operations Center has referred 250 incidents since july 2006 to its inspector general, which has led to 46 separate investigations. uPDATE (6/18/07):More than $20 million to respond to its latest data breach, the breach potentially puts the identities of nearly a million physicians and vA patients. [source] | U.S. Military Veterans had a data breach in 2009, in District Of Columbia. [source] | |
UC Irvine Medical Center had a data breach in 2015, in California. UC Irvine Medical Center has notified patients of a data breach when an employee reviewed patient records without authorization.The information this individual may have gained access to included names, dates of birth, gender, medical record numbers, height, weight, Medical Center account number, allergy informaton, home addresses, medical documentation, diagnoses, test orders/results, medications, employment status, and names of your health plan and employer. The medical center is providing those who were affected FraudStop free for one year. [source] | UCLA Health System had a data breach in 2011, in California. A September 6 home theft resulted in the loss of an external computer hard drive. It contained the first and last names, birth dates, medical record numbers, addresses, and other medical record information of patients. The information dated from July 2007 to July 2011 and belonged to an individual who maintained the information in order to fulfill job duties. Other items were taken during the theft, but none have been recovered.UPDATE (12/20/2011): A class action lawsuit was filed on December 14. It alleges that the UCLA Health System violated Californias Confidentiality of Medical Information Act. Since the act provides for statutory damages of $1,000 per person, the UCLA Health System could owe nearly $16.3 million to the 16,288 patients who were affected. UPDATE (12/22/2011): A total of 16,288 people had some type of information on the laptop, but 2,761 had enough information on the laptop to cause more than a minimal amount of financial, reputational, or other harm if accessed. [source] | |
UCLA Medical Center had a data breach in 2008, in California. UCLA Medical Center has moved to fire 13 employees and suspended six others for unauthorized access to confidential medical records. uPDATE (8/5/08): The latest report said 127 workers peeked into celebrities medical records without permission, leading to several firings, suspensions and warnings. The report also detailed the case of one employee who looked at the records of about 900 patients without any legitimate reason and viewed Social Security numbers, health insurance information and addresses, from April 2003 to May 2007. [source] | UCSF Family Medicine Center at Lakeshore had a data breach in 2014, in California. UCSF Family Medicine Center at Lakeshore notified patients of a theft of desktop computers that were unencrypted on or around January 11, 2014. An immediate analysis of what information the computers obtained. On March 6, 2014 UCSF determined that some of the computers stolen contained Social Security numbers, names, dates of birth and medical record numbers, some only contained names, medical record numbers and health information. [source] | |
UMASS Memorial Medical Center (UMMMC) had a data breach in 2014, in Massachusetts. [source] | UNC Health Care had a data breach in 2018, in North Carolina. The information was breached via Desktop Computer. [source] | |
Union Hospital had a data breach in 2016, in Indiana. Union Hospital suffered an inadvertent disclosure on approximately 1/18/16 that resulted in 1 record being exposed, which included social security numbers. [source] | Uniontown Hospital had a data breach in 2013, in Pennsylvania. [source] | |
Universal Medical Center had a data breach in 2011, in Arizona. Three staff members and one contract employee were fired for viewing sensitive patient information without cause. The electronic medical records of patients who were injured during a terrorist shooting spree may have intrigued the workers. There were no reports of confidential patient information being released to the public. [source] | University Community Hospital had a data breach in 2007, in Florida. A parent says his son should never have received bills in the mail for a pre-employment drug screening visit. Additionally, he received information about 17 others who were also tested, including Social Security numbers. [source] | |
University Health Care had a data breach in 2008, in Utah. A laptop and flash drive containing patient data were stolen after hours from a locked office. Data included patients names, addresses, and in some cases, medications, health insurance policy numbers, and Social Security numbers. [source] | University Hospital had a data breach in 2010, in Georgia. Two backup tapes containing personal information have gone missing. The hospital does not suspect theft and does believe that there is a very low probability that the personal information on the tapes can be misused. However, credit monitoring services are being offered to those who were affected. The hospital gave up looking for the tapes on May 7th and began notifying patients in late June. Per phone interview with University Hospital, Social Security number were involved but they are unaware of any financial data involved in this breach. [source] | |
University Hospitals had a data breach in 2014, in Ohio. The information was breached via Electronic Medical Record. [source] | University Medical Center had a data breach in 2009, in Nevada. Files containing Social Security numbers, phone numbers, patient names, and addresses were found in a trash bin outside of the clinic. A woman found the files and notified police after receiving an anonymous tip. [source] | |
University Medical Clinics had a data breach in 2010, in Florida. Files containing Social Security numbers, phone numbers, patient names, and addresses were found in a trash bin outside of the clinic. A woman found the files and notified police after receiving an anonymous tip. [source] | University MRI Diagnostic Center, Holy Cross Hospital, North Ridge Medical Center, and Oncology and Hematology Associates of West Broward had a data breach in 2010, in Florida. Two former employees of these organizations were involved in an identity theft scheme with at least three other partners. Thousands of victims have been confirmed. The employees had access to emergency room patient records such as names, dates of birth, Social Security numbers, Medicare numbers, and addresses. The stolen information was used by others to obtain Care Credit accounts and Chevron Visa credit cards. Victims lost a total of approximately $162,000. [source] | |
University of Arkansas for Medical Sciences (UAMS) had a data breach in 2012, in Arkansas. A former resident doctor kept the personal information of about 1,500 patients as part of a lawsuit she filed against UAMS. She also claimed to have kept the information for research purposes. UAMS became aware of the issue on October 9 when the former resident doctor used the documents as part of her lawsuit. UAMS learned that she kept additional documents on November 7 and had provided them to UAMS attorneys on June 25. Some patients had their names, addresses, dates of birth, medical record numbers, and dates of service exposed. Other patients had their ages, locations of care, dates of service, diagnoses, medications, surgical procedures, procedure names, and lab results exposed. [source] | University of Arkansas for Medical Sciences (UAMS) had a data breach in 2012, in Arkansas. A UAMS physician sent financial data to an individual who was not a member of UAMSs workforce in February of 2012. Patient identifiers had not been removed from the data and UAMS learned of the error on April 6. Patients of interventional radiology seen at UAMS between 2009 and 2011 had their names, UAMS account numbers, dates of service, interventional radiology procedures, diagnosis codes, charges, and payments exposed. [source] | |
University of Arkansas for Medical Sciences had a data breach in 2010, in Arkansas. A digital camera used for recording newborn information was stolen from an employee at the hospital. The information included newborn photos, mother names and contact information, dates of birth, insurance status and medical record numbers. The photos are taken as a security measure in case an infant is abducted. Infants born at the hospital between July and October were affected. [source] | University of California Davis (UCD) Medical Center had a data breach in 2010, in California. The information was breached via Email. [source] | |
University of California Los Angeles (UCLA) Health System had a data breach in 2012, in California. The UCLA Health System placed an audit report on billing practices online in May. It was later discovered that an employee had accidentally attached information containing the first name, last name, and five-digit billing code related to at least one patients emergency department visit in May of 2011. It is unclear how many people were affected and if others may have had additional information exposed. [source] | University of California, Irvine Medical Center had a data breach in 2007, in California. About 1,600 file boxes stored in an off-site university warehouse were discovered missing. Some of the files included patients names, addresses, Social Security numbers and medical record numbers. [source] | |
University of California, San Francisco (UCSF) School of Medicine had a data breach in 2010, in California. A laptop containing files with information on 4,400 patients was stolen from a uCSF School of Medicine employee. Information potentially exposed included name, medical record number, age and clinical information, but the stolen laptop did not contain any Social Security numbers or other financial data. The same laptop also contained data for approximately 2,900 patients at Beth Israel deaconess Medical Center in Boston [source] | University of Chicago Hospital had a data breach in 2005, in Illinois. The FBI launched an investigation into possible fraud by at least one hospital employee. As many as 85 patients may have been affected. The hospital contacted all affected patients. [source] | |
University of Colorado, Boulder had a data breach in 2005, in Colorado. Prospective students, current students, staff, faculty and University health care service recipients may have had their data exposed in a campus server breach. The information included names, Social Security numbers, addresses, student ID numbers, birth dates, and lab test information. The University mailed letters and sent emails to the individuals affected.UPDATE (08/20/2005) The number of students affected was increased from an estimate of 42,000 to 49,000. [source] | University of Connecticut Health Center had a data breach in 2013, in Connecticut. An employee accessed patient records for reasons unrelated to their job function. The Heath Center became aware of an unauthorized access in January of 2013. Patient names, addresses, dates of birth, and in some cases health information and Social Security numbers may have been exposed. [source] | |
University of Florida College of Medicine had a data breach in 2008, in Florida. A UF assistant professor of plastic surgery at the UF College of Medicine-Jacksonville, stored unsecured digital photographs of his patients and identifying information on a computer. He then gave the computer to a family. The information included names, dates of birth, Social Security numbers, and Medicare numbers. [source] | University of Florida had a data breach in 2013, in Florida. A dishonest employee working at University of Florida Health Pediatrics at Tower Square is suspected of participating in an identity theft ring. The former employee had access to pediatric patient records that included names, Social Security numbers, addresses, and dates of birth. The University of Florida learned about the issue on April 11. [source] | |
University of Kentucky HealthCare/Talyst had a data breach in 2014, in Kentucky. [source] | University of Kentucky HealthCare had a data breach in 2011, in Kentucky. An employees phone was lost or stolen on September 25, 2011. Patient health conditions, medical record numbers, and possibly even names could be accessed from the phone. [source] | |
University of Kentucky HealthCare had a data breach in 2012, in Kentucky. [source] | University of Louisville had a data breach in 2010, in Kentucky. A University of Louisville database of 708 names that included Social Security numbers and dialysis details was available on the Internet without password protection for nearly a year and a half. The Web site was disabled on May 17 when the university discovered the flaw. University officials said in a statement that accessing the database would not have been easy, and no direct links to the database were discovered. The information was available so long because the U of L doctor who set up the Web site thought the information was protected by a password and other precautions. U of L was finally notified when someone outside the university sent an e-mail about open access to the information. The Web site was shut down an hour later. [source] | |
University of Maine had a data breach in 2010, in Maine. Hackers compromised the personal information of 4,585 students who received services from the schools counseling center. The center provides students with support and mental health services. The information on the servers included names, Social Security numbers and clinical information on every student who sought counseling services from the center between August 8, 2002 and June 21 of this year. [source] | University of Maryland Medical Center had a data breach in 2011, in Maryland. A former employee of the University of Maryland Medical Center and three other people collaborated to steal the identities of patients. The former medical center employee allegedly stole the patient information of people who had paid for medical treatment between July 2009 and June 2011. His co-conspirators then used the information to open credit cards, obtain cash advances and make purchases in victims names. The four people were arrested and face a maximum sentence of 30 years in prison for conspiracy, in addition to charges related to bank fraud and aggravated identity theft.UPDATE (10/12/2012): A former employee was sentenced to six months of home detention and ordered to pay $22,000 in restitution. He claimed that he took the patient records home in order to conceal work that he had not completed and submit false reports. At least two other people used the patient records to commit fraud. [source] | |
University of Massachusetts - Amherst had a data breach in 2013, in Massachusetts. [source] | University of Massachusetts Amherst, University Health Services had a data breach in 2011, in Massachusetts. A workstation at the campus University Health Services (UHS) was infected with malware. The work station contained patient names, health insurance company names, medical record numbers, and prescription information from January 2, 2009 to November 17, 2009. There is no evidence that the data was copied from the workstation. The malware was on the computer from June 30, 2010 to October 28, 2010. Patients were notified in March. [source] | |
University of Massachusetts, Amherst had a data breach in 2008, in Massachusetts. Hackers breached the computer system used by UMass Amhersts Health Services, potentially gaining access to thousands of medical records. More than half of the student population at UMass Amherst are patients on record at the University health Services. [source] | University of Miami Health System had a data breach in 2012, in Florida. [source] | |
University of Miami Miller School of Medicine had a data breach in 2012, in Florida. A briefcase containing an unencrypted flash drive was stolen from the vehicle of a University of Miami Miller School of Medicine pathologist on November 24, 2011. It contained the names, medical record numbers, ages, sexes, diagnosis information, and treatment information of patients who had specimens reviewed by the department of pathology between 2005 and 2011. [source] | University of Miami had a data breach in 2008, in Florida. Computer tapes containing confidential information of Miami patients was stolen last month when thieves took a case out of a van used by a private off-site storage company. The data included names, addresses, Social Security numbers or health information. [source] | |
University of Michigan School of Nursing had a data breach in 2007, in Michigan. Backup tapes containing patient information like Social Security numbers, patient names and addresses were stolen from the School of Nursing two weeks ago. [source] | University of Minnesota Reproductive Medicine Center had a data breach in 2008, in Minnesota. A doctor at the fertility clinic lost a flash drive that was used to back up his computer. The drive held details of infertility treatments for 3,100 patients going back to 1999. The lost drive included names, birthdates, and in some cases, diagnostic information, details of treatments, whether or not patients had conceived, baby names, and birth weights -- but apparently no sSNs or financial information. [source] | |
University of Mississippi Medical Center (UMMC) had a data breach in 2013, in Mississippi. A laptop used by UMMC clinicians was discovered missing on January 22. The password-protected laptop contained information from patients who entered the hospital between 2008 and 2013. Patient names, Social Security numbers, addresses, diagnoses, medications, treatments, dates of birth, and other personal information may have been exposed.UPDATE(04/25/2013): The laptop may have been lost or stolen in November of 2012. [source] | University of Nevada had a data breach in 2010, in Nevada. [source] | |
University of Oklahoma's Urology Clinic had a data breach in 2015, in Oklahoma. [source] | University of Oklahoma-Tulsa Neurology Clinic, Neurology Services of Oklahoma, LLC had a data breach in 2010, in Oklahoma. Malware was discovered on a clinic computer on or around July 28. Patients who saw Dr. John Cattaneo at the clinic and at his former employer Neurology, LLC were notified of the breach. Patient names, Social Security numbers, phone numbers, addresses, dates of birth, medical record numbers, lab reports and dates of service were in documents that may have been accessed by the virus. [source] | |
University of Pittsburgh Medical Center Shadyside Hospital had a data breach in 2010, in Pennsylvania. In February of 2008, an employee disclosed the names, dates of birth and Social Security numbers of patients in exchange for personal gains. The patient information was eventually used to file false tax returns. The former employee was indicted on 14 counts.UPDATE(7/05/2011): A former employee has pleaded guilty to taking the names, Social Security numbers and dates of birth of 19 Shadyside patients. The employee gave the patient information to other people who then filed fraudulent 2008 tax returns.UPDATE (10/21/2011): The former employee was sentenced to one year of probation for disclosing the information of 19 UPMC patients. He claims he was intimidated into giving away the information and that the people who collected $84,190 in fraudulent tax returns returned to Zambia. [source] | University of Pittsburgh Medical Center, Squirrel Hill Family Medicine had a data breach in 2006, in Pennsylvania. An employee dishonestly took documents containing names and financial information. The employee was fired. [source] | |
University of Pittsburgh Medical Center had a data breach in 2007, in Pennsylvania. In February of 2008, an employee disclosed the names, dates of birth and Social Security numbers of patients in exchange for personal gains. The patient information was eventually used to file false tax returns. The former employee was indicted on 14 counts.UPDATE(7/05/2011): A former employee has pleaded guilty to taking the names, Social Security numbers and dates of birth of 19 Shadyside patients. The employee gave the patient information to other people who then filed fraudulent 2008 tax returns.UPDATE (10/21/2011): The former employee was sentenced to one year of probation for disclosing the information of 19 UPMC patients. He claims he was intimidated into giving away the information and that the people who collected $84,190 in fraudulent tax returns returned to Zambia. [source] | University of Pittsburgh Student Health Services had a data breach in 2010, in Pennsylvania. An employee dishonestly took documents containing names and financial information. The employee was fired. [source] | |
University of Rochester Medical Center (URMC) had a data breach in 2010, in New York. [source] | University of Rochester Medical Center had a data breach in 2013, in New York. The information was breached via Paper/Films. [source] | |
University of Tennessee Medical Center had a data breach in 2005, in Tennessee. A laptop was stolen from the Universitys medical billing office. Personal information lost included names, Social Security numbers and birth dates. Affected patients were not informed of the theft for nearly two months. [source] | University of Tennessee Medical Center had a data breach in 2010, in Tennessee. An administrative report that should have been shredded was accidentally thrown in the trash. Reports are usually left in a storage location for 45 days and then discarded properly. The Hospital became aware of the breach on October 4. Anyone looking through the report would find names, Social Security numbers and other patient information. [source] | |
University of Texas Arlington had a data breach in 2010, in Texas. [source] | University of Texas Health Science Center had a data breach in 2008, in Texas. About 2,000 medical bills were mailed last week with patients Social Security numbers visible on the envelope. [source] | |
University of Texas M.D. Anderson Cancer Center (M.D. Anderson) had a data breach in 2012, in Texas. A laptop with sensitive patient information was stolen from the home of an M.D. Anderson faculty member on April 30. The laptop was not encrypted and contained patient names, medical record numbers, treatment and/or research information, and in some instances Social Security numbers. Notifications were mailed to patients who were affected on June 28. [source] | University of Texas M.D. Anderson Cancer Center (M.D. Anderson) had a data breach in 2012, in Texas. An unencrypted flash drive was discovered missing. It had last been seen on an employee shuttle bus on July 13. It contained patient names, dates of birth, medical record number, diagnoses and treatment information, and research information. [source] | |
University of Texas M.D. Anderson Cancer Center had a data breach in 2006, in Texas. A laptop containing insurance information for patients was stolen from a PricewaterhouseCoopers employees home in November. Patients and patient families were notified in January that their private health information, policy numbers, dates of birth, ZIP codes and Social Security numbers may have been exposed. [source] | University of Texas Medical Branch had a data breach in 2010, in Texas. [source] | |
University of Texas Southwestern Medical Center had a data breach in 2010, in Texas. A former employee was arrested on patient information and identity theft. The stolen patient information includes names, Social Security numbers, birth dates, addresses, phone numbers and financial data. The employee allegedly sold the patient information of at least 200 people to an outside party for the purpose of creating bank accounts and misusing credit and loans. [source] | University of Utah Hospitals and Clinics had a data breach in 2008, in Utah. Billing records of 2.2 million patients at the University of Utah Hospitals and Clinics were stolen from a vehicle after a courier failed to immediately take the eight data tapes to a storage center. The records, contained Social Security numbers of 1.3 million people treated at the university over the last 16 years.UPDATE (2/5/09): The data tapes were found within a month after being stolen.UPDATE (6/9/10): An Englewood, Colo., insurance company has filed a federal lawsuit contending that it isnt responsible for reimbursing the University of Utah for $3.3 million in costs related to a 2008 data breach caused by a third-party service provider.The lawsuit filed in a Utah federal court by Colorado Casualty Insurance Co. contends that the insurer is not obligated to cover the costs sought by the University. Colorado Casualty was providing breach insurance to the University at the time of the breach.The nine-page complaint, which seeks a declaratory judgment from the court, offers little explanation as to why exactly the insurer believes it is not obligated to pay the breach-related costs sought by the University. [source] | |
University of Virginia Health System had a data breach in 2017, in Virginia. [source] | University of Virginia Medical Center, Continuum Home Infusion had a data breach in 2012, in Virginia. A handheld electronic devices used by Continuum pharmacists was discovered missing on October 5. The device was not encrypted and contained patient names, addresses, diagnoses, medications, and health insurance identification numbers. Some health insurance identification numbers were Social Security numbers or contained Social Security numbers. Patients who received services from Continuum during the month of September 2012 and potential patients who were referred to Continuum between August 2007 and September 2012. Notifications were sent on November 30. [source] | |
University of Washington Medical Center (UWMC) had a data breach in 2010, in Washington. The information was breached via Portable Electronic Device. [source] | University of Washington Medical Center had a data breach in 2006, in Washington. A hacker broke into the UW Medicine computer system in June of 2004. The incident was not discovered until December of 2005. The hacker may have accessed and copied patient and business records for 18 months. The goal of the hacker appears to have been to use the system for its computing power and data storage. [source] | |
University of Washington Medical Center had a data breach in 2006, in Washington. Laptops containing names, Social Security numbers, maiden names, birth dates, diagnoses and other personal data were stolen from a UW office. The information was password protected and the affected patients were notified. [source] | University Pittsburgh Medical Center had a data breach in 2014, in Pennsylvania. The University Pittsburgh Medical Center (UPMC) informed employees of a data breach that compromised employee's personal data, including their Social Security number and the potential for fraudulent tax returns being filed in their name. The number of employees affected was approximately 800. The full extent of the information exposed has not been communicated, however, due to the tax fraud, information such as names, addresses and Social Security numbers were assumed to be involved. UPMC was aware of the breach in February and thought that the breach included only 27 individuals, but soon became aware that the breach was much larger. An investigation is currently being conducted.UPDATE (4/21/2014): The extent of the data breach at UPMC thought to be around 800 employees, is much more extensive than originally believed. The current numbers are around 27,000 employees affected. UPMC is offering Lifelock for 12 months for those affected. [source] | |
Unknown had a data breach in 2016, in Indiana. An individual contacted a local TV station regarding records found in a dumpster outside a strip mall in Indianapolis Indiana. These documents were people's tax returns containing addresses, names and Social Security numbers. The amount of individuals affected or the company that prepared the tax returns is not yet known. [source] | UPMC Susquehanna had a data breach in 2017, in Pennsylvania. The information was breached via Email. [source] | |
Upper Valley Medical Center, Data Image had a data breach in 2012, in Ohio. A data breach of Data Images online billing system may have exposed the private information of Upper Valley Medical Center patients. Names, addresses, hospital account numbers, and balances owed could have been obtained during an 18-month period. Current and former patients were notified that the breach was discovered on March 21, 2012, but could have occurred as early as October 1, 2010. [source] | Upper Valley Medical Center had a data breach in 2012, in Ohio. [source] | |
Upstate University Hospital had a data breach in 2013, in New York. A portable electronic device was stolen from Upstate University Hospital on March 30 or 31. It contained the names, hospital medical record numbers, dates of birth, and diagnosis information of patients. [source] | US Army had a data breach in 2008, in District Of Columbia. A possible security breach regarding the personal information stored on a lost laptop computer may have affected more than 6,000 beneficiaries. Names, Social Security numbers and health information of at least 26 individuals were stored on the laptop. however, information on approximately 6,000 other patients also may have been on the missing computer. [source] | |
UT Southwestern Medical Center had a data breach in 2010, in Texas. UT Southwestern recently sent out a mass mailing to 10,000 of its patients, claiming that a former employee disclosed patients information to a third party that intended to use it for credit, loans and open bank accounts. UT southwestern representatives claim 200 patients were actually affected. [source] | V.A. Medical Center had a data breach in 2011, in South Carolina. A V.A. employee may have thrown the personal information of over 2,600 veterans into the trash. The breach was originally discovered over a month before the official notification and reported by a news channel. The V.A. admitted that appointment records with Social Security numbers, dates of birth and other information were accidentally thrown into the trash instead of being shredded. The records were from January 2010 through January 2011. All veterans from that period were contacted, but not all were affected. [source] | |
Valley Anesthesiology & Pain Consultants had a data breach in 2016, in Arizona. On June 13, 2016, we learned that a third party may have gained unauthorized access to the VAPC computer systems on March 30, 2016. Upon learning of the situation, we immediately began an investigation, including hiring a leading forensics firm to assist us, and notifying law enforcement. The forensics firm found no evidenc that the information on the computer systems was accessed, but was unable to definitively rul that out. The computer systems may ontain some of your information, such as your name, providers' names, date of service, place treatment, diagnosis and treatment codes, and your Medicare number, which may include your social security number. Your financial information was not included in these computer systems. [source] | Valley Plastic Surgery, P.C. had a data breach in 2012, in Virginia. The information was breached via Electronic Medical Record and Network Server. [source] | |
Verity Health System had a data breach in 2017, in California. The information was breached via Network Server. [source] | Verus Inc., Concord Hospital had a data breach in 2007. [source] | |
Veterans Administration Medical Center (Biloxi) had a data breach in 2011, in Mississippi. The VA believes an employees office at the Veterans Administration Medical Center in Biloxi was inappropriately accessed without proper authorization on July 21. A number of medical files with veteran names, Social Security numbers, dates of birth and other personal information like medical diagnoses were found spread on the office floor. The breach could affect veterans, deceased veterans and VA employees in seven counties in southern Mississippi, four counties in southern Alabama, and seven counties in the Florida Panhandle. [source] | Veterans Administration Medical Center had a data breach in 2011, in Florida. An employee was charged with selling the personal identities of disabled hospital patients. At least 22 military veterans who received services at the VA in Miami had their information sold. The employee was worked at the VA Travel Benefits Sections and had access to the names, Social Security numbers, addresses, and dates of birth of disabled veterans who had been reimbursed for travel expenses related to their medical treatment. The employee was caught late in 2010 after several veterans complained about unauthorized credit card accounts opened in their names. [source] | |
Veterans Affairs Hospital, South Dakota had a data breach in 2015, in South Dakota. The VA Hot Springs hospital notified patients of a data breach when files containing their Social Security numbers along with additional personal information were thrown in a trash bin without being shredded. The incident took place in May and the 1,100 patients that were affected were not notified until July 29, 2015. Reportedly, an employee discarded a box of patient files in a dumpster. The box of files was found two days later by another employee who removed them from the trash. [source] | Veterans Affairs Medical Center had a data breach in 2008, in Oregon. Name, address, SSN were breached. [source] | |
Vidant Pungo Hospital had a data breach in 2012, in North Carolina. Paper jackets that held radiology films were thrown away with office trash instead of being properly discarded. The paper jackets contained names, addresses, dates of birth, ages, sex, race, and information on dates and names of radiology procedures prior to May of 2012. The paper jackets are believed to have been picked up by a sanitation company and discarded in a landfill. [source] | Vidant Pungo Hospital had a data breach in 2012, in North Carolina. The information was breached via Email. [source] | |
Virginia Commonwealth University (VCU) Health System had a data breach in 2017, in Virginia. March 16, 2017 - Virginia Commonwealth University (VCU) Health System recently discovered a data breach potentially impacted over 2,700 patients, according to an announcement in the Richmond Times-Dispatch.On January 10, 2017, VCU Health System became aware of a data breach in which patient EHRs were vulnerable to unauthorized access over a three-year period between January 3, 2014 and January 10, 2017.Following an investigation, VCU Health System concluded employees of community physician groups, and an employee of a contracted vendor, had accessed patient records without proper justification. Officials maintain no information was used inappropriately.The employees involved in the incident have since been terminated.Employees may have viewed information including patient names, addresses, dates of birth, medical record numbers, health care providers, visit dates, health insurance information, and Social Security numbers.VCU Health System said it is providing concerned patients with one year of free credit monitoring to avoid further issues with identity theft and fraud.More Information: http://healthitsecurity.com/news/va-university-health-system-security-br... [source] | Virtual Radiological Professionals (vRad) had a data breach in 2011, in Minnesota. Name, address, phone number, health insurance info, dates of visit, health information were breached. [source] | |
Visiting Nurse Association of Southeastern Connecticut had a data breach in 2010, in Connecticut. Current and former patients received notification letters stating that their personal information was on a stolen laptop. The laptop was stolen from a nurses car while it was parked at her home on September 30. The laptop was used to store patient addresses, medical information and names. [source] | Visiting Nurse Service of New York (VNSNY) had a data breach in 2006, in New York. The information was breached via Desktop Computer. [source] | |
Visiting Nurse Service of New York (VNSNY) had a data breach in 2007, in New York. A tablet computer was stolen from a registered nurse. Patient Social Security numbers, names, addresses and telephone numbers were on the tablet. VNSNY warned patients that people might use the information and tablet to pose as VNSNY employees. [source] | Wake Forest Baptist Medical Center had a data breach in 2011, in South Carolina. A renter discovered that an employee had taken over 20 boxes of patient information home. The renter had been asked by the owner not to go into the basement of the home, but wanted to clean after a flood. He found the boxes, informed Wake Forest and the employee was fired. The medical records date back at least 10 years. They contained patient names, phone numbers, Medicaid numbers, medical record numbers, medical histories, diagnoses and medications. Wake Forest is filing a larceny report.UPDATE(6/4/2011): More boxes have been removed from three additional residential and storage units owned by the employee. The employee was fired on June 1 and has been cooperating with investigators. Wake Forest denied that Social Security numbers were found in the former employees home. Based on the response of the former employee and other observations, investigators believe that the former employee is a hoarder with no desire to misuse the information. Only 3-4% of the contents of the boxes were sensitive information.UPDATE(7/14/2011): A total of 136 patients and 221 medical center employees were affected. [source] | |
Wake Forest United Baptist Medical Center (WFUBMC) had a data breach in 2010, in North Carolina. A bag containing a document with the names and Social Security numbers of 554 patients was stolen from an employees locked car.UPDATE(6/2/2011): The theft occurred on February 15 at an outpatient clinic parking lot. [source] | Walter Reed Army Medical Center had a data breach in 2008, in District Of Columbia. The information was breached via Network Server. [source] | |
Washington Hospital Healthcare System had a data breach in 2016, in California. The information was breached via Email. [source] | Washington Redskins had a data breach in 2016, in Virginia. A laptop containing the medical records of thousands of NFL players was stolen from the car of a Washington Redskins trainer last month, the team said in a statement on Wednesday, confirming a story first reported by Deadspin.According to a letter from the NFLPA that was obtained by Deadspin, the stolen medical records were of every player who went through the NFL scouting combine from 2004 through 2016, as well as current Redskins players. The backpack also contained a zip drive and hard copies of the medical records, the letter said.[source] | |
Wayne Memorial Hospital had a data breach in 2013, in Pennsylvania. An unencrypted disc that contained patient information was lost in transit. The disc had names, Medicare account numbers, and outstanding account balances from patients who visited the Honesdale hospital between 2007 and 2012. A legal envelope that contained the disc was mailed on November 28 and arrived at Novitas Solutions in Pittsburgh in a cardboard box without the disc. [source] | WEI Mortgage had a data breach in 2017. [source] | |
Welk Resorts had a data breach in 2016, in California. [source] | Welk Resorts had a data breach in 2016, in California. On October 6, 2016, we learned that, late on October 5, a Welk team member’s home was burglarized, and the team member’s company laptop was stolen. Upon learning of the theft, we immediately launched an investigation to determine what information may have been involved in this incident. While our investigation is ongoing, we have determined that your information may have been stored on the stolen laptop. To date, we have no evidence to suggest that the data stored on the laptop has been accessed. Further, we have no evidence to date that there has been any attempted or actual misuse of data stored on the laptop. This incident has been reported to local police and, to our knowledge, there is an ongoing criminal investigation. The information contained on the stolen laptop may include your name, Social Security number, address, certain benefit plan participation information, and date of birth. [source] | |
West Dermatology had a data breach in 2012, in California. A theft that occurred sometime around April 22, 2012 resulted in the exposure of protected health information. The breach was posted on the HHS website on July 3. [source] | West Penn Allegheny Health System had a data breach in 2007, in Pennsylvania. [source] | |
WestCoast Children's Clinic had a data breach in 2012, in California. A referral document containing sensitive information was accidentally sent in an email to an unauthorized recipient. Patient names, Social Security numbers, dates of birth, addresses, and health concerns were sent to a county social worker. The county social worker deleted the sensitive email and any other existing copies of the document were securely deleted from the network. The WestCoast Childrens Clinic will not provide referral forms to outside agencies in order to protect against future inadvertent sharing of private information. Disciplinary actions will also be taken against the employees involved in the privacy breach. [source] | Westerly Hospital had a data breach in 2007, in Rhode Island. The information was breached via Network Server. [source] | |
Western Union had a data breach in 2016, in Colorado. The information was breached via Paper/Films. [source] | WESTMED Medical Group had a data breach in 2010, in New York. A laptop with patient information was stolen in August. [source] | |
Westside Park Elementary School Based Health Center had a data breach in 2012, in California. A burglary sometime around October 1 may have resulted in the exposure of patient names, Social Security numbers, phone numbers, addresses, dates of birth, health conditions, medications, and other health information. The information was in a locked room that was accessed, but it appears that none of the paper records were stolen. Thieves took a television and other items. [source] | White Blossom Care Center had a data breach in 2017, in California. The information was breached via Email. [source] | |
Wichita Radiological Group had a data breach in 2008, in Kansas. A former employee stole patient records before being fired from the Wichita Radiological Group. Tens of thousands of patient records were in the database could have been compromised. [source] | Wilcox Memorial Hospital had a data breach in 2005, in Hawaii. A backup computer data drive containing medical record numbers, addresses, names and Social Security numbers of current and former patients was lost. Letters have been sent to affected patients. [source] | |
William Jennings Bryan Dorn VA Medical Center had a data breach in 2013, in South Carolina. The February 11 theft of an unencrypted laptop from the respiratory department resulted in the exposure of patient information. Veterans who were patients may have had their name, Social Security number, age, race, weight, and medical test results on the laptop. The laptop was taken during regular clinic hours.UPDATE(05/01/2013): A lawsuit has been filed by two veterans on behalf of people who were affected by the breach. [source] | Wolf & Yun had a data breach in 2012, in Kentucky. [source] | |
Woman to Woman Healthcare had a data breach in 2011, in California. Medical records were improperly disposed of. Pro-Life Society found the records in a dumpster behind the office. [source] | Womancare Inc. had a data breach in 2009, in Michigan. Medical records were improperly disposed of. Pro-Life Society found the records in a dumpster behind the office. [source] | |
Women & Infants Hospital had a data breach in 2012, in Rhode Island. The information was breached via Desktop Computer and Network Server. [source] | Women's Health Care Group of Pennsylvania had a data breach in 2017, in Pennsylvania. The Women’s Health Care Group of Pennsylvania, with 45 offices throughout the state, has notified 300,000 of its patients that a ransomware attack has put their personal health information at risk.The health system discovered a server and workstation at one of its practices was infected by ransomware on May 16. Officials said the infected server and workstation were removed from the network, before officials launched an investigation by a computer forensics team.The investigation revealed the cybercriminals began hacking the system as early as January 2017, by leveraging a security vulnerability. Officials said the security flaw allowed limited access to patient information before it encrypted certain files.The health system couldn’t determine if patient information acquired or viewed. The data stolen by hackers included names, Social Security numbers, birth dates, pregnancy histories, blood type information, lab results, medical record numbers, insurance information and medical diagnoses. Officials said the encrypted files were restored from backups and didn’t disrupt patient care. [source] | |
Wonderful Center for Health Innovation had a data breach in 2017, in California. [source] | Wood County Hospital had a data breach in 2013, in Ohio. [source] | |
Woodwinds Hospital had a data breach in 2013, in Minnesota. An employee kept 200 pages of confidential information in an effort to prove that Woodwinds Hospital was trying to conceal evidence of medical misconduct. The employee was discharged in 2010 for reasons unrelated to removing the information. She claims to have taken them home after being ordered to destroy any information related to incidents that could damage Woodwinds Hospitals reputation. [source] | WorkCare Orem had a data breach in 2007, in Utah. A truck driver found medical documents containing personal information in his truck and on the ground while he picked up a load at a garbage transfer station. the documents contained names, addresses, telephone numbers, Social security numbers and birth dates. [source] | |
Wright State Physicians had a data breach in 2010, in Ohio. A password-protected laptop with patient information was accidentally thrown in the trash and lost for five days. Names, dates of service, and sometimes treatment description of patients treated for vascular conditions within the last four years were on the laptop. The laptop was thrown out on June 11 and found in a landfill on June 16. [source] | Wright-Patterson Air Force Base had a data breach in 2010, in Ohio. Name, address, ssn, financial account info were breached via Desktop Computer . [source] | |
Wright-Patterson Medical Center had a data breach in 2012, in Ohio. A notebook containing names and Social Security numbers was misplaced after a blood drive. It was left in a limited-use conference room late in the afternoon and recovered the next morning behind a chair. [source] | Wuesthoff Medical Center had a data breach in 2008, in Florida. Hundreds of people in Brevard County found out their personal information was stolen. Names, Social Security numbers and even personal medical information were posted on the Internet. [source] | |
Yale School of Medicine had a data breach in 2010, in Connecticut. A stolen laptop resulted in the exposure of patient clinical health information. [source] | Yale-New Haven Hospital had a data breach in 2016, in Connecticut. Federal investigators say two women orchestrated an identity theft ring that targeted at least 20 people. But it's how suspects Jamila Williams-Stevenson and Loretta Coburn are said to have gotten some of their victim's personal information that is most shocking.Authorities said several of the alleged victims had been patients at Yale-New Haven Hospital where Williams-Stevenson was working as a companion or sitter.According to a court affidavit, once the two changed their alleged victims addresses, they took control of their mail, then took control of their finances.[source] | |
Yuba Sutter Medical Center had a data breach in 2016, in California. On or about August 3, 2016, the Yuba-Sutter Medical Clinic's computer system came under a ransomware attack by hackers. Ransomware attacks are designed to deny access to certain portions of a computer systems until a ransom is paid.In such an attack, the risk is not usually to patient privacy. Instead it poses an operational risk to health systems in that it can result in patients being turned away due to an inability to provide care as a result of not having immediate access to records. [source] | Yuba Sutter Medical Center had a data breach in 2016, in California. The information was breached via Portable Electronic Device. [source] | |
Zarzamora Family Dental Care had a data breach in 2010, in Texas. The October 15 theft of a desktop computer affected 800 patients. [source] | ||