Documenting all the places
personal data goes.
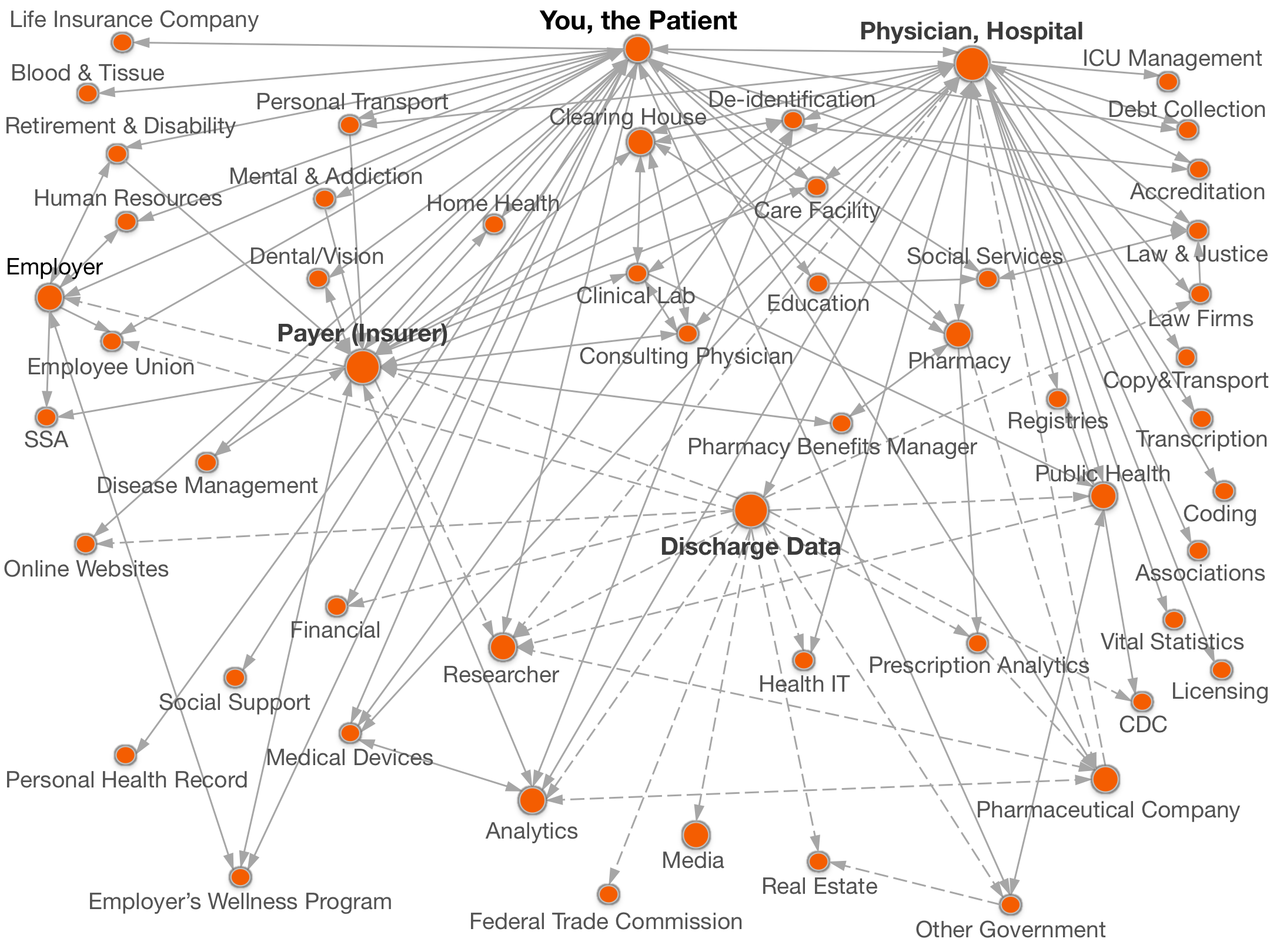
Legend:  with your name,
with your name, without your name.
without your name.
Click on a circle above for names of organizations and details of data shared.
Debt collection agencies are business that pursue payments of debts owed by individuals or businesses. They can be either a subsidiary of the creditor or a separate, third party company hired by the creditor. A debt collector working for a provider has information on medical charges they are trying to collect from you.
Examples
AccessLex Institute d/b/a Access Group had a data breach in 2018, in California. On March 28, 2018 AccessLex learned that on March 23, 2018, a vendor they use to help provide student loan processing services inadvert sently sent a copy of certain loan files, to another business that was not authorized to receive them. Shortly after they learned of the inadvertent file transfer, we contacted managers of the second business that received the files. The second business confirmed it had deleted the transferred files and agreed that the appropriate manager would sign a sworn statement confirming it had deleted the files and retained no copies.The information involved included names, driver’s license numbers, and Social Security numbers. [source] | Ameriprise Financial, Inc. had a data breach in 2017, in Minnesota. Ameriprise Financial suffered an inadvertent disclosure of 56 records, including SS numbers and names. [source] | |
Artarama N.C. Inc. had a data breach in 2016, in North Carolina. [source] | Central Collection Bureau had a data breach in 2008, in Indiana. A computer server containing Social security numbers and other personal information was stolen last month from a Southside debt-collection bureau. The information includes customer-billing records for Indiana businesses, including Citizens gas & Coke Utility, St. Vincent Health and Methodist Medical Group. (700,000 records involved) [source]. | |
EPN, Inc. had a data breach in 2012, in Utah. The FTC has fined EPN, Inc. for failing to implement reasonable security measures. The agency charged that the company did not have an appropriate information security plan, failed to assess risks to the consumer information it stored, did not adequately train employees, did not use reasonable measures to enforce compliance with its security policies, and did not use reasonable methods to prevent, detect and investigate unauthorized access to personal information on its networks. The FTC claims that this failure to implement reasonable and appropriate data security measures was an unfair act or practice and violated federal law. EPNs chief operating office installed peer-to-peer file-sharing software on EPNs computer system and left patient information vulnerable to unauthorized access. Hospital patient Social Security numbers, health insurance numbers, and medical diagnosis codes were accessible on any computer connected to the peer-to-peer network. EPN was barred from misrepresenting the privacy, security, confidentiality, and integrity of personal information they collected. EPN was also required to undergo data security audits and establish and maintain a comprehensive information security program. (3,800 records involved) [source]. | Far Niente Winery had a data breach in 2017, in California. On August 21, 2017, files on Far Niente’s computers were encrypted by an individual who gained unauthorized access to Far Niente’s computer network. The individual demanded a ransom in exchange for restoring access to the encrypted files. [source] | |
LeapLab had a data breach in 2014, in Arizona. LeapLab is being sued by the Federal Trade Commission for purchasing "payday loan applications of financially strapped consumers, and then sold that information to marketers whom it knew had no legitimate need for it". In another FTC case, Ideal Financial Solutions, used this information sold to them to withdraw millions of dollars from individual accounts without permission. [source] | Localblox had a data breach in 2018, in Washington. [source] | |
Logic Supply had a data breach in 2017, in Vermont. [source] | LV Financial Services had a data breach in 2010, in Florida. Dozens of boxes of files from medical offices that hired LV to collect unpaid bills were found in an Orlando public dumpster. The files contained names, addresses, Social Security numbers, drivers license copies and credit reports. The collection agency went out of business in 2005 and the location of the files prior to this incident is unknown. [source]. | |
Metro Credit Services had a data breach in 2007, in Texas. Thousands of files from the defunct bill collection company containing medical records, phone bills and Social Security numbers were found in a trash bin. [source]. | OneMain Financial had a data breach in 2018, in Maryland. An unauthorized individual apparently compromised the personal or work email accts of OneMain customers, & used the email accts to access certain customers OneMain online accts. Based on the review, it does not appear that OneMain was the source of or responsible for the apparent compromise of accts. The personal info involved may have included 1st & last name, phone #, OneMain loan acct #, OneMain rewards acct, & type of ins. purchased. [source] | |
The Trump Hotel Collection had a data breach in 2015, in New York. The information was breached via Email. [source] | Trump Hotels had a data breach in 2016, in New York. Trump Hotel has suffered a second data breach this year. The hotel chain is investigating a pattern of fraud with customer credit cards. The Trump Hotel Collection includes more than a dozen properties globally. Sources said they noticed a pattern of fraud on cards that were all used at multiple Trump hotel locations in the past two to three months, including at Trump International Hotel New York, Trump Hotel Waikiki in Honolulu, and the Trump International Hotel & Tower in Toronto. [source] | |
Virgin America had a data breach in 2017, in California. [source] | W.W Grainger Inc. had a data breach in 2015, in Illinois. Grainger has notified customers of a data breach when their IT team "recently identified a coding error in the Grainger.com mobile apps for iPhone and Android that resulted in the collection and storage of unsecured user names and passwords on the Grainger system." This particular data base could be accessed by unauthorized users. The company has implement a reset of users passwords to their Grainger.com system. [source] | |