Documenting all the places
personal data goes.
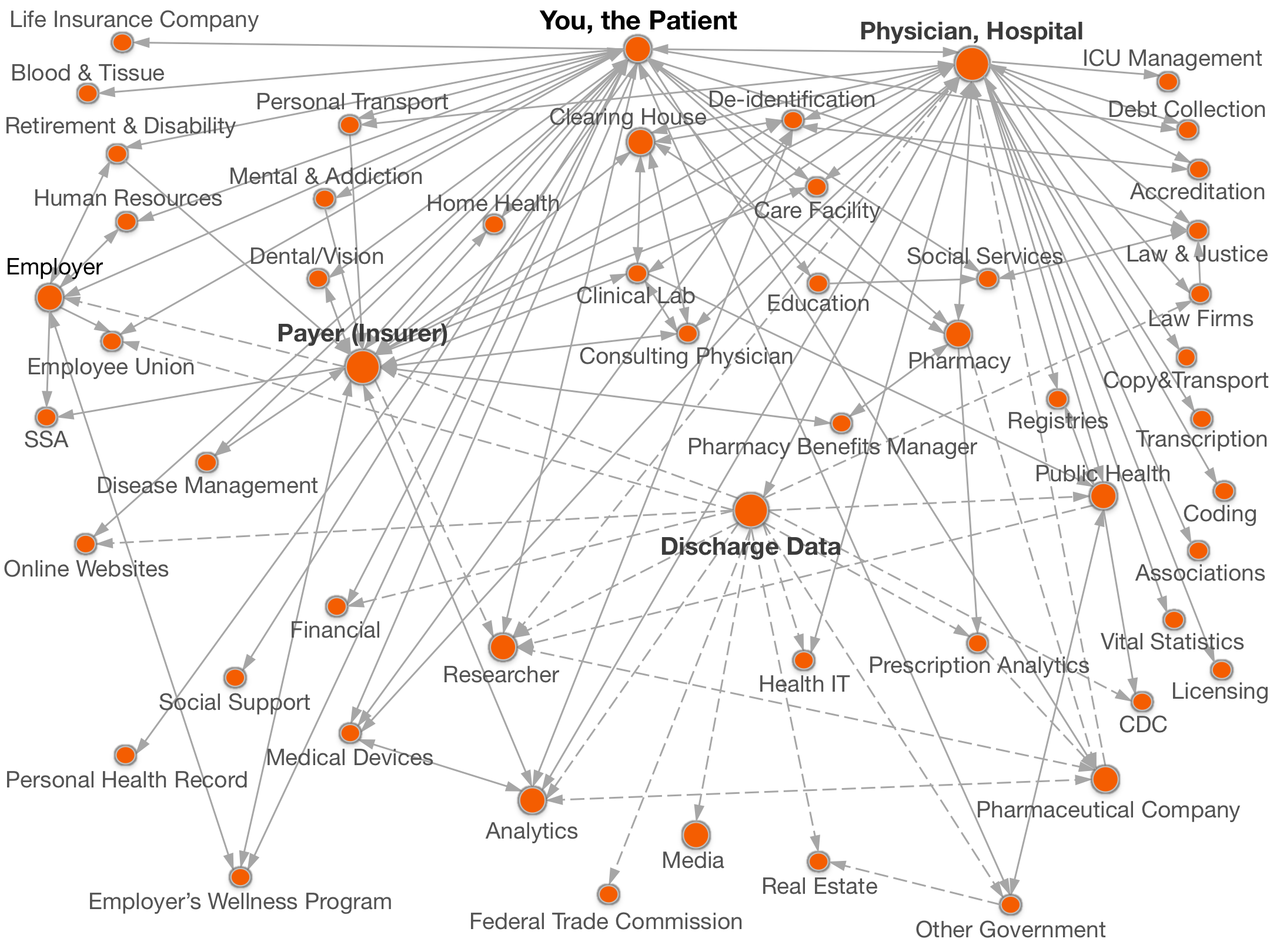
Legend:  with your name,
with your name, without your name.
without your name.
Click on a circle above for names of organizations and details of data shared.
Public Health Agencies receive health information from state discharge data holders, other government agencies, vital statistics offices and providers (hospital, physician). Data they receive is often required by reporting laws. They provide data to the CDC, other government entities, and researchers.
Examples
Arkansas Department of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Alabama Department of Public Health had a data breach in 2007, in Alabama. The personal information, including the names, ages and Social Security numbers of families enrolled in the states ALL Kids health care coverage program, were accidentally sent to the wrong families last week. 1,554 affected families were alerted that some of their confidential information might have been released. (1,554 records involved) [source]. | |
Delaware Health Statistics Center, Division of Public Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Alaska Department of Health and Social Services (DHSS) had a data breach in 2009, in Alaska. A portable electronic device that may have contained protected health information was stolen from the vehicle of a DHSS employee on or around October 12, 2009. The Health and Human Services (HHS) Office for Civil Rights (OCR) began an investigation after the incident. OCR found evidence that DHSS did not have adequate policies and procedures in place to safeguard ePHI. DHSS was also found to have not completed a risk analysis, implemented sufficient risk management measures, completed security training for its workforce members, implemented device and media controls, or addressed device and media encryption as required by the HIPAA Security Rule. Alaska DHSS agreed to pay a $1,700,000 settlement. [source]. | |
Illinois Department of Public Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | American Cancer Society (ACS) had a data breach in 2006, in Kentucky. An unspecified number of laptop computers were stolen from the Louisville offices of the american Cancer Society. It is not clear what personal information was exposed, if any. [source]. | |
Mississippi Dept of Health, Office of Health Informatics collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Baltimore County Department of Health had a data breach in 2007, in Maryland. A laptop containing personal information including names, date of birth, Social Security numbers, telephone numbers and emergency contact information of patients who were seen at the clinic between Jan. 1, 2004 and April 12 was stolen. (6000 records involved) [source]. | |
Missouri Department of Health and Senior Services collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Cabinet for Health and Family Services had a data breach in 2012, in Kentucky. An employee was the victim of a phishing attack via email sent by a hacker. The employees account was then compromised. Unauthorized activity was identified on the account within half an hour and the account was immediately disabled. [source]. | |
New Hampshire Department of Health & Human Services collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | California Department of Health Services had a data breach in 2007, in California. Benefit notification letters containing names addresses, Medicare Part D plan names and premium payment amounts of some individuals enrolled in the California aIDS Drug Assistance Program (ADAP) were erroneously mailed to another enrollee. (54 records involved) [source]. | |
New Jersey Department of Health & Senior Services collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | California Department of Public Health had a data breach in 2010, in California. A magnetic tape was lost during shipping between West Covina and Sacremento on or around September 27. The health care facility staff and residents who were determined to have been affected were notified on November 23. Employee emails, employee background reports, investigative reports, names and diagnosis information on health care facility residents and Social Security numbers for CDPH workers were on the tape. [source]. | |
New Mexico Department of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | California Department of Public Health (CDPH) had a data breach in 2013, in California. A reel containing images of 2,000 State of California Birth Records from May through September of 1974 was found in a publicly accessible location. Names, Social Security numbers, addresses, and certain types of medical information were in the birth record images. People in Santa Clara, Santa Cruz, Shasta, Siskiyou, Solano, Sonoma, Stanislaus, Sutter, or Tehama counties and who were born or had a child born in 1974 between May and September were affected. (2,000 records involved) [source]. | |
New York State Dept of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | California Department of Public Health, Bakersfield Memorial Hospital had a data breach in 2012, in California. The theft of a binder from an employees car resulted in the exposure of sensitive patient information. The binder was stolen on or around May 7 and had information from a survey conducted at the Bakersfield Memorial Hospital. Patient names, dates of birth, ages, medications, room numbers, and medical record numbers were exposed. [source]. | |
North Dakota Department of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Colorado Health Department had a data breach in 2005, in Colorado. A laptop containing Social Security numbers, medical records, family medical history, and addresses was stolen from an employees car. The State Health Department is not monitoring the affected group and has only contacted some of the families involved. (1,600 records involved) [source]. | |
Oklahoma State Department of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Department of Medical Assistance Services, Affiliated Computer Services (ACS), Inc. had a data breach in 2012, in Virginia. The unauthorized disclosure of paper records may have resulted in the exposure of the protected health information of people associated with Department of Medical Assistance Services (DMAS). The incident related to DMASs relationship with Affiliated Computer Services (ACS) and occurred sometime between November 2, 2011 and November 16, 2011. [source]. | |
Rhode Island Department of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Department of Social and Health Services had a data breach in 2013, in Washington. A private contractor working for the Department of Social and Health Services discovered that their laptop had been stolen on February 4. The laptop was recovered in a pawn shop on February 14. It contained the names, ID numbers, psychological evaluations, dates of birth, diagnoses, dates of services, addresses, and last four digits of Social Security numbers of clients. (652 records involved) [source]. | |
Office of Health Statistics, Tennessee Department of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Detroits Health Department had a data breach in 2009, in Michigan. Police are investigating two incidents in which patients medical records -- including social security numbers -- were stolen from the citys health department. The first theft occurred in late October when a flash drive was stolen from a health department employees car. It contained files with birth certificate information for babies born in 2008 and the first half of 2009 whose parents reside in the 48202 and 48205 zip codes. Also a part of the files were information on the mothers names and health conditions, the fathers names, addresses, Medicaid numbers and social security numbers. The second incident happened over the Thanksgiving break when five computers were stolen from the immunization program at the departments Herman Kiefer Health Complex. One of the computers contained Medicare and Medicaid seasonal flu billing information for 2008. (5,000 records involved) [source]. | |
Texas Health Care Information Collection, Center for Health Statistics, Texas Department of State Health Services collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Florida Department of Children and Families had a data breach in 2008, in Florida. Social Security numbers, birth dates and other information about day-care workers in Orange, Seminole and Osceola counties were among the data on five laptop computers that were stolen from the DCF office near Orlando. (1,200 records involved) [source]. | |
Office of Health Care Statistics, Utah Department of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Florida Department of Health had a data breach in 2013, in Florida. Information on personal drug prescriptions from the Florida Department of Health somehow ended up in the hands of prosecution lawyers. Names, addresses, phone numbers, pharmacies, and drug dosages were obtained by lawyers involved in six prescription-drug fraud cases. The American Civil Liberties Union of Florida began an investigation into how the records were exposed. [source]. | |
Washington State Department of Health collects, sells or gives away statewide, person-specific information about hospital discharges [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Georgia Division of Public Health had a data breach in 2007, in Georgia. The GA Dept. of Human Resources notified parents of infants born between 4/1/06 and 3/16/07 that paper records containing parents SSNs and medical histories -- but not names or addresses -- were discarded without shredding. (140000 records involved) [source]. | |
Alameda County Public Health Department purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Gila County Health and Emergency Services (Payson WIC Office) had a data breach in 2012, in Arizona. A woman found thousands of applications for Women, infants, and Children (WIC) support in a dumpster.Around 1,000 documents were originally reported in the dumpster. Additional documents were discovered when a local news team joined the woman at the dumpster a few days later.The applications included copies of drivers licenses, Social Security numbers, medical information, and many other types of sensitive information. An employee of the state agency said that the forms would normally be properly shredded, but were thrown out in a hurry without being checked. (1000 records involved) [source]. | |
Anne Arundel County Health Department purchases statewide personal hospital discharge data from at least MD [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Green River District Health Department, Fox Technology Group (now part of Intergranetics) had a data breach in 2011, in Kentucky. The personal information of people who visited Green River District Health Department was accidentally placed online by Fox Technology. A resident notified the Department after discovering personal information online. Many visitor names were given with dates of birth; around half included Social Security information as well. The information was exposed sometime in October of 2010 or before. The problem was fixed soon after the Department was notified.UPDATE(3/16/2011): There were 18,871 visitors who were affected, not 9,986. [source]. | |
Austin/Travis County Health and Human Services Department (HHSD) purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Hillsborough Health Department had a data breach in 2012, in Florida. An employee printed and removed sensitive client information for unknown purposes. The employee was dismissed and steps were taken to reduce the risk of similar employee thefts occurring. The employee removed the documents on February 15, 2012 and was not discovered until Hillsborough County Health Department was notified on May 25. Client names, Social Security numbers, dates of birth, phone numbers, patient identification numbers, type of visit, and other protected health information were exposed. (291 records involved) [source]. | |
Broward Regional Health Planning Council purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Human Services Agency of San Francisco had a data breach in 2011, in California. A former city employee emailed the information of her caseload to her personal computer, two attorneys and two union representatives. The former employee wanted proof that she was fired for low performance because she had been given an unusually high number of cases. Certain MediCal recipients in San Francisco had their names, Social Security numbers and other personal information exposed. (2400 records involved) [source]. | |
Ca Dept Of Public Health purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Illinois Department of Healthcare and Family Services had a data breach in 2012, in Illinois. The August 31 theft of a briefcase from the home of a contractor resulted in the exposure of nursing home residents. The briefcase contained names, Social Security numbers, Medicaid recipient numbers, and dates of birth. (508 records involved) [source]. | |
California Department Of Healthcare Services purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Kanawha-Charleston Health Department had a data breach in 2009, in West Virginia. People who received flu shots from the agency since October are being warned that their personal information may have been stolen by a former department temporary worker. Information included their names, Social Security numbers, addresses and other personal information. (11000 records involved) [source]. | |
Cdph Child And Adolescent Health purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Montana Public Health and Human Services Department had a data breach in 2006, in Montana. A state government computer was stolen from the office of a drug dependency program during a 4th of July break-in. It was not known if sensitive information such as SSNs was compromised. [source]. | |
Center For Community Health, Monroe Cnty Doh purchases statewide personal hospital discharge data from at least NY [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | New Hampshire Department of Health and Human Services had a data breach in 2008, in New Hampshire. Health and Human Services mistakenly released the Social Security numbers and other personal information of Medicare Part D recipients. The information was mistakenly attached to an e-mail to health care organizations including nursing homes. (9300 records involved) [source]. | |
County Of La- Dept Of Health Services purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | New Jersey Department of Health had a data breach in 2012, in New Jersey. Over 480 registered medical marijuana patients received an email from the New Jersey Department of Health. The email instructed them not to call New Jersey or the dispensary in Montclair to make an appointment. The email did not hide the email addresses of the recipients. [source]. | |
County Of San Bernardino Public Health purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | North Carolina Department of Health and Human Services had a data breach in 2011, in North Carolina. A set of computer disks may have been accidentally discarded during an office renovation. The disks contained data from the Division of Services for the Deaf and Hard of Hearing and would have been taken to a landfill if they were accidentally discarded. Those who applied for services from the Divisions Equipment Distribution Service between January of 2005 and December of 2008 may have had their information exposed. [source]. | |
Department Of Public Health purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | North Carolina Dept. of Health and Human Services had a data breach in 2008, in North Carolina. A laptop computer belonging to a Division of Aging and Adult Services employee was stolen. The computer contained information about people receiving home and community services. [source]. | |
DHMH purchases statewide personal hospital discharge data from at least MD [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Office of the New York City Public Advocate had a data breach in 2011, in New York. The group Anonymous claimed responsibility for hacking and publishing a data base. The database consisted of names, addresses, telephone numbers, email addresses, medical conditions, domestic violence and abuse reports, descriptions of financial hardship, complaints about residential issues, and other very personal details of people who submitted this information via the public advocates website. The submissions for assistance date from April 2010.UPDATE(12/28/2011): The NYC Office of the Public Advocate released a public notice. [source]. | |
Department of Health FL purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Palm Beach County Health Department had a data breach in 2013, in Florida. A senior desk clerk was arrested for obtaining and releasing patient information for identity theft purposes. The dishonest employee took home client lists with names, Social Security numbers, and dates of birth. Patients born between 1991 and 1996 may have had their personal information misused. (2800 records involved) [source]. | |
Department of Health FL, Bureau Of Environmental Public Health Medicine purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Palm Beach County Health Department had a data breach in 2012, in Florida. An employee was fired in May for creating and attempting to mail a list of names and Social Security numbers for purposes of identity fraud. It is unclear if the dishonest employee disclosed the information of other people before being caught. Some patients had already experienced fraudulent activity. People who may have been a patient in one of the Health Department Health Centers could have been affected. UPDATE(01/09/2013): The employee worked as a records clerk and was arrested on January 5, 2013. She had worked for Palm Beach County Health Department since 2006 and was charged with several counts of fraud. (86 records involved) [source]. | |
Department of Health, Childrens Medical Services purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Pennsylvania Public Welfare Department had a data breach in 2007, in Pennsylvania. Two computers containing the mental health histories of more than 300,000 medical-assistance recipients were stolen. The computer work stations were taken during an overnight break-in at an office. The mental health information on the computers identified people by codes and not by name. The information also was protected by multiple passwords, but full names and Social security numbers of nearly 2,000 people were also on the computers. (2,000 records involved) [source]. | |
Doh, Office Of Trauma purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Pima County Health Department had a data breach in 2006, in Arizona. Vaccination records on 2,500 clients had been left in the trunk of a car that was stolen Sept. 12. The car and records have since been recovered. Records included names, dates of birth and ZIP codes, but no SSNs or addresses. [source]. | |
Dshs-Adult Chronic Disease purchases statewide personal hospital discharge data from at least TX [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Public Health - Seattle and King County had a data breach in 2013, in Washington. A custodian improperly disposed of client medical information on March 7. The records were from the Refugee Screening, WIC, and Needle Exchange programs. Patient names, dates of birth, phone numbers, addresses, medical record numbers, appointment dates, and medical condition or treatment may have been accessed. [source]. | |
Florida Department Of Health purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Skagit County Health Department had a data breach in 2011, in Washington. A student ran a Google search on her own name in mid-September and discovered some of her private information online. Skagit County Health Department was notified. People who used services at other county departments also had information exposed. The types of information did not include credit card numbers, Social Security numbers, dates of birth, or addresses, but did include information from receipts for department services. [source]. | |
Governors Office of Health Care Policy and Finance ME purchases statewide personal hospital discharge data from at least ME [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Tennessee Department of Human Services had a data breach in 2009, in Tennessee. Doctors offices in Tennessee have been accidentally sending patient information, including Social security numbers and medical histories, to an Indiana businessmans fax machine for the past three years. The sensitive medical information was supposed to be sent to the Tennessee Department of Human Services, but the owner of SunRise Solar Inc. in Indiana, says hundreds of confidential medical faxes having been coming to him. [source]. | |
Health Planning Council Of Northeast Florida purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Texas Department of Health and Human Services had a data breach in 2008, in Texas. Information, including Social security numbers that could be used to steal Medicaid clients identity may have been stored on two computers stolen during a burglary. Computers could have contained personal information only on e-mails. The e-mails, however, would normally contain only an individuals case number. it is unlikely those e-mails would have listed Social Security numbers. [source]. | |
Humboldt County Hhs-Phb purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Texas Health and Human Services had a data breach in 2011, in Texas. The theft of a laptop from a nurses car may have exposed names, dates of birth, genders, Medicaid client identification numbers, procedure codes, diagnoses codes, and other health information. The theft took place on March 10, 2011, but it was not until August that the risk to patient privacy was discovered. A notice was sent on September 9. [source]. | |
Kern County Health purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Utah Department of Health, Goold Health Systems had a data breach in 2013, in Utah. An employee of Goold Health Systems lost an unencrypted USB memory stick that contained the information of around 6,000 Medicaid recipients in Utah. Goold Health Systems is a contractor for the Utah Department of Health. Medicaid recipient names, Medicaid identification numbers, ages, and recent prescription drug use were on the memory stick. The memory stick was lost during travel between Salt Lake City, Denver, and Washington. The loss was confirmed on Tuesday, January 15. [source]. | |
King County Communicable Disease purchases statewide personal hospital discharge data from at least WA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Wellesley Health Department had a data breach in 2008, in Massachusetts. Information in an envelope that had been mailed by the towns health department to a Medicare office in Boston say when the envelope arrived, it was open and the contents were missing. The material included social security numbers, addresses and dates of birth of seniors who had received flu shots from the town last fall. (480 records involved) [source]. | |
La County Department Of Public Health purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Wisconsin Department of Health and Family Services had a data breach in 2008, in Wisconsin. Social Security numbers were printed on about 260,000 informational brochures sent by a vendor hired by the state, Electronic Data Systems Inc. (EDS), to recipients of SeniorCare, badgerCare and Medicaid. The company agreed to pay $250,000 to the state for the mistake, as well as paying for an identity theft monitoring service for the affected individuals, for a total of about $1 million. (260,000 records involved) [source]. | |
La County Dept Of Health Svcs purchases statewide personal hospital discharge data from at least CA [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Yates County Public Health had a data breach in 2006, in New York. A laptop computer used for Child Health Plus, Medicaid and Family Health Plus plans was stolen from a vehicle on October 20. It contained application information which included name, Social Security number, date of birth, drivers license number, bank account and personal checking information and employer information. At least 68 New York residents were affected, but the total number of affected individuals nationwide was not revealed. (68 records involved) [source]. | |
Leon County Health & Human Services purchases statewide personal hospital discharge data from at least FL [source]. See more information about the fields of data shared, an example of matching real names to the records in statewide discharge data, and which states use standards less than the HIPAA standard. | Yuba County Health and Human Services had a data breach in 2007, in California. A laptop stolen from a building contained personally identifiable information of individuals whose cases were opened before May 2001. The laptop was being used as a backup system for the countys computer system. The data include social Security numbers, birth dates, drivers license numbers and other private information. (70,000 records involved) [source]. | |
101 Family Medical Group, Privacy Manager Breach had a data breach in 2014, in California. A laptop computer owned by Phressia, Inc., a business associate (BA) of the covered entity (CE), Family Medical Group, was stolen from the parked car of a Phreesia workforce member. In violation of the BA’s policies and procedures, both the hard drive of the laptop, and the workforce member’s Dropbox account, which was accessible through the laptop, contained the electronic protected health information (ePHI) of approximately 2,500 patients. The types of PHI involved in the breach included patients’ names, addresses, identification numbers, phone numbers, email addresses, dates of birth, social security numbers, and insurance identification numbers. Following the breach, the BA sanctioned the responsible workforce member and retrained workforce members on its privacy and security policies and procedures. The CE provided breach notification HHS, affected individuals, and the media. In response to OCR's investigation, the BA updated its policies and procedures on device and media controls and employee sanctions. [source] | Advance Rehabilitation & Consulting LTD had a data breach in 2015, in Georgia. [source] | |
Agency of Human Services had a data breach in 2014, in Vermont. Vermont Agency of Human Services notified individuals of a data breach containing names and Social Security numbers of individuals. The email distribution list inadvertently included all AHS employees and some contractors. According to the agency, the email was opened by numerous AHS employees, a subsequent email was promptly sent that instructed recipients of the email to "hard delete" it so it did not remain in their email delete box. [source] | Alaska Department of Health and Social Services had a data breach in 2017, in Alaska. Two computers of the Alaska Department of Health and Social Services were hit by malware attacks, which potentially breached the records of some of its patients.A Trojan horse virus was found on the two computers on July 5 and July 8. Trojan malware is masked as legitimate software and are used by hackers as leverage into a network.Data compromised included Children's Services information, medical information and observation, family case files, and other personal information. [source] | |
Allina Health had a data breach in 2015, in Minnesota. [source] | Amedisys had a data breach in 2015, in Louisiana. [source] | |
Apria Healthcare had a data breach in 2016, in California. s reported by Health and Human Services unauthorized access/disclosures. No specific information as to what information was compromised as provided by health and human services. [source] | Arizona State Board of Elections had a data breach in 2016, in Arizona. Hackers have breached databases for election systems in Illinois and Arizona, according to state election systems in Illinois and Arizona, according to state election and law enforcement officials.In Illinois, hackers accessed a database for the Illinois Board of Elections, compromising up to 200,000 personal voter records according to Ken Menzel, General Counsel for the board.According to Matthew Roberts, director of communications for the Arizona secretary of state, in late May, Arizona officials took the statewide voting registration system offline after the FBI alerted the Arizona Department of Administration that there was a credible cyber threat to the voter registration system. Although the Washington Post reported that Roberts attributed the database breach directly to a Russian hacker, when pressed by CNN, he said that the Arizona secretary of state's office learned of Russian involvement from internal IT and cyber security staff.The information compromised included names, addresses, sex and birthdays, plus voter's social security number or drivers' license numbers. The database that was compromised had information going back 10 years and most likely included outdated information which was never purged. [source] | |
Arkansas Department of Medicaid had a data breach in 2017, in Arkansas. The confidentiality of more than 26,000 Medicaid recipients' medical information was broken earlier this year, state officials said Friday as they prepared to notify those individuals about the breach.The information -- including names, medical procedure codes, birth dates, diagnoses and Medicaid identification numbers -- was sent to a fired Department of Human Services employee's personal email account, a department spokesman said Friday.The department discovered the information in an email on Aug. 7 while conducting research for its defense of a federal lawsuit filed by Yolanda Farrar over her dismissal from her job as a payment integrity coding analyst, spokesman Amy Webb said.The email was sent to Farrar's personal account on March 23 within minutes of a discussion over issues that led to Farrar's firing the next day, Webb said. [source] | Asante had a data breach in 2016, in Oregon. [source] | |
Aspire Indiana Inc. had a data breach in 2015, in Indiana. According to Health and Human Services Aspire Indiana Inc. suffered a data breach when a laptop was stolen from their facitlity. They did not report as to what specific personal information was on the laptop. [source] | Aventura Hospital and Medical Center had a data breach in 2015, in Florida. [source] | |
Backcountry Gear had a data breach in 2014, in Maryland. Customer names, email addresses, billing and mailing addresses, purchase information, credit card or debit card numbers, the card expiration date and security code on the back of the cards were breached via payment card system . [source] | Baltimore School of Massage Therapy had a data breach in 2014, in Maryland. Name, ssn, phone number, address, and student ID number were breached via email. [source] | |
Baxter Regional Medical Center- Home Health Facility had a data breach in 2016, in Arkansas. On August 5, 2016, intruders broke into the covered entity (CE), Baxter Regional Medical Center, potentially breaching the protected health information (PHI) of approximately 2,124 individuals. The intruders broke into locked offices which contained PHI in paper-based patient files although nothing appeared to be missing. Following the breach, the CE improved physical security. Additionally, it moved all non-current patient records to a secure, off-site storage facility and trained employees on its HIPAA practices. The CE provided breach notification to HHS, affected individuals, and the media. During OCR’s investigation, OCR reviewed the notification to HHS and provided technical assistance regarding the Breach Notification Rule. Location of breached information: Other Business associate present: No [source] | Baystate Health, Inc. had a data breach in 2016, in Massachusetts. [source] | |
Bedford County Board of Education had a data breach in 2016, in Tennessee. [source] | Bizmatics, Inc. had a data breach in 2016, in California. A healthcare provider in Colorado, Vincent Vein Center, is the latest organization to notify the U.S. Department of Health and Human Services (HHS) Office of Civil Rights (OCR) about a breach of protected health information stemming from a malicious hacker attacking Bizmatics’ data servers. Bizmatics provides ambulatory software and electronic health records serving 15,000 healthcare providers.Each customer/provider is reporting the specific numbers to Health and Human Services. We will be reporting the specific provider records breached as they are reported by HHS. [source] | |
CA Department of Developmental Services had a data breach in 2018, in California. The information was breached via Paper/Films . [source] | California Correctional Health Care Services had a data breach in 2017, in California. On January26, 2017, California Correctional Health Care Services (CCHCS) was informed that on January 23, 2017,a CCHCS staff member inadvertently sent an email containing your personal information to a staff member at another California State department.What Information Was InvolvedThe personal information contained in the email included your name, CDCR number, CDCR housing information, mental health related information, and health care provider names. [source] | |
California Department of Business Oversight had a data breach in 2015, in California. The California Department of Business Oversight notified both registered investment advisers and broker-dealers that some of their personally identifying informatino was accidentally disclosed when typical procedure to redact the information either failed or was neglected. The information exposed included Social Security numbers of these individuals. The DBO did not mention the other information exposed on the forms. [source] | California Pacific Medical Center had a data breach in 2015, in California. On or about October 15, 2014, during a routine review of workforce members’ use of electronic protected health information (ePHI), the covered entity (CE), California Pacific Medical Center, discovered that a workforce member in the pharmacy department had impermissibly accessed the medical records of 13 coworkers. A subsequent audit showed that from October 2013 to October 2014, the workforce member had impermissibly used the medical records of a total of 845 individuals. The ePHI accessed included patient demographics, last four digits of social security numbers, clinical information about diagnoses, clinical notes, physician order information, laboratory and radiological data, and prescription information. OCR verified that the CE applied employee sanctions pursuant to its policy and procedure, provided breach notification to HHS, affected individuals, and the media, and retrained employees on relevant HIPAA policies and procedures. [source] | |
Cardiology Associates of Jonesboro, Inc. had a data breach in 2016, in Arkansas. [source] | Cathrine Steinborn, DDS had a data breach in 2015, in California. [source] | |
Cathrine Steinborn, DDS had a data breach in 2015, in California. The covered entity (CE) reported a breach of 3,224 individuals’ electronic protected health information (ePHI), as a result of an office burglary on January 5, 2015. The stolen server contained names, addresses, dates of birth, telephone numbers, social security numbers, insurance information, medical information, and billing information. The CE provided OCR with evidence that it responded to the security incident and undertook steps to prevent the risk of future security incidents by implementing physical and technical security safeguards; updating security analysis, and training the entire workforce. OCR provided technical assistance regarding the HIPAA Security Rule. Location of breached information: Network Server Business associate present: No [source] | CCHI Insurance Services had a data breach in 2017, in California. The information was breached via Desktop Computer, Electronic Medical Record, Email, Network Server . [source] | |
Cefalu Eye-Tech of Green, Inc. had a data breach in 2016, in Ohio. An employee of Cefalu Eye-Tech of Green, Inc. (Cefalu) photographed computer screens containing the protected health information (PHI) of approximately 850 individuals, including names, addresses, email addresses, and codes for diagnosis and conditions. Following the breach, Cefalu investigated the breach and provided breach notification to HHS and the affected individuals. OCR determined that the reporting entity is no longer a covered entity. OCR obtained documentation supporting its finding that Cefalu is no longer a covered entity. Location of breached information: Electronic Medical Record Business associate present: No [source] | Center for Minimally Invasive Bariatric and General Surgery had a data breach in 2016, in Pennsylvania. [source] | |
Children's Medical Clinics of East Texas had a data breach in 2015, in Texas. The information was breached via Desktop Computer . [source] | City of Alexandria Fire Department had a data breach in 2014, in Virginia. Name, dob, ssn, record identifier were breached via Desktop Computer . [source] | |
City of Crossville, Tennessee had a data breach in 2014, in Maryland. Name, bank numbers, were breached via Website . [source] | City of Hope had a data breach in 2016, in California. The information was breached via Laptop. [source] | |
Colorado Community Health Alliance (CCHA)/Physicians Health Partners had a data breach in 2014, in Colorado. On January 2, 2014, the covered entity (CE), Colorado Department of Health Care Policy and Financing, reported a breach by its business associate (BA), Colorado Community Health Alliance. On November 21, 2013, a temporary employee working for the BA’s subcontractor, Aerotek, sent a list via unencrypted email containing the electronic protected health information (ePHI) of 1,918 individuals to her personal email account. The ePHI included patients’ names, addresses, dates of birth, Medicaid identification numbers, and health conditions. The BA detected the email through its auditing program. The CE provided breach notification to HHS and the BA provided breach notification to affected individuals and the media and posted substitute notice. After the incident, the BA developed and implemented a policy requiring that emails containing ePHI be encrypted to prevent a similar incident from occurring in the future, and trained its workforce members accordingly. OCR provided substantial technical assistance to the BA, which implemented additional procedures and technical safeguards and provided written assurance that it will complete an enterprise-wide risk analysis.[source] | Community Technology Alliance had a data breach in 2014, in California. Community Technology Alliance (CTA) is notifying individuals of a potential compromise of their personal information, when an employee's laptop was stolen on July 28, 2014. CTA is a non-profit organization that administers the Bay Area Homeless Management Information Systems (HMIS) and helps hundreds of partner agencies. The information in HMIS can include names and Social Security Numbers, and various other pieces of personal information. If services were being received from an HMIS Partner Agency in Santa Cruz California, those individuals are the ones at risk. The partner agencies include the following: Community Action Board, Families in Transition, Homeless Services Center, Salvation Army of Watsonville, Pajaro Valley Shelter Services, Housing Authority of the County of Santa Cruz, Encompass, Front Street Housing, Inc., Mountain Community Resource Center, Catholic Charities, Veterans Resource Center, Santa Cruz County Office of Education, Santa Cruz County Health and Human Services Agency, Housing Services Center, Pajaro Rescue Mission, and New Life Community Services. [source] | |
County of Los Angeles had a data breach in 2016, in California. [source] | Darlington had a data breach in 2016, in Georgia. [source] | |
David E. Hansen DDS PS had a data breach in 2015, in Washington. David E. Hansen DDS PS notified patients of a data breach when a portable electronic device was stolen.Specifics on what information was compromised was not provided. [source] | Department of Health and Human Services had a data breach in 2015, in North Carolina. The Department of Health and Human Services (DHHS) in Granville County North Carolina notified patients of a data breach when an employee inadvertently sent an email to the Granville County Health Department when the file was not encrypted. The information compromised included first and last names, Medicaid identification numbers, provider names, provider ID numbers, and other Medicaid related services. [source] | |
Department of Homeland Security had a data breach in 2017, in District Of Columbia. A data breach at the Department of Homeland Security has exposed the personal information of more than 240,000 current and former DHS employees, such as their social security numbers, dates of birth, positions, grades, and duty stations, the agency said. On January 3, 2018, select DHS employees received notification letters that they may have been impacted by a privacy incident related to the DHS Office of Inspector General (OIG) Case Management System. The privacy incident did not stem from a cyber-attack by external actors, and the evidence indicates that affected individual’s personal information was not the primary target of the unauthorized unauthorized transfer of data.What we know: The department said the breach was not carried out as part of a "cyber-attack by external actors." Instead, the data was discovered in the possession of a former employee of the agency's Office of Inspector General during an ongoing criminal investigation last MayGo deeper with the department's full memo. [source] | Department of Human Services' Office of Behavioral Health, Denver had a data breach in 2014, in Colorado. The Department of Human Services' Office of Behavioral Health in Denver Colorado notified individuals of a data breach when a postcard mailing went out to individuals as part of a survey. The cards were specifically addressed to individuals receiving behavioral health services through DHS office and mailed in post-card format. This information is considered to be protected health information. According to the DHS no Social Security numbers or financial information was on the cards. [source] | |
Department of Resources, Recycling and Recovery had a data breach in 2014, in California. [source] | Dr. Anthony T.R. Green DDS had a data breach in 2015, in New York. [source] | |
Dr. Dennis T. Myers, D.D.S, P.A. had a data breach in 2016, in Missouri. [source] | Dr. Melissa D. Selke had a data breach in 2016, in New Jersey. [source] | |
Dr. Q Pain and Spine d/b/a Arkansas Spine and Pain had a data breach in 2016, in Arkansas. [source] | Ebay had a data breach in 2014, in California. [source] | |
Ecolab Health and Welfare Benefits Plan had a data breach in 2016, in Minnesota. [source] | Edward G. Myers, D.O. Inc. had a data breach in 2016, in Ohio. [source] | |
Edwin Shaw Rehabilitation had a data breach in 2016, in Ohio. [source] | Einstein Healthcare Network had a data breach in 2016, in Pennsylvania. [source] | |
Elite Imaging had a data breach in 2016, in Florida. A log book (sign-in book) containing information about the covered entity’s (CE) patients was stolen from its offices and returned anonymously with a letter. The log-book contained the patients’ full names and the name of the procedure conducted for each patient. The breach affected 1,457 patients. The CE provided breach notification to HHS, affected individuals, and the media. The CE conducted a full review of the incident and filed a police report. It also reviewed and modified its safeguards policies and internal procedures, implemented a new log in procedure, updated its software, and re-trained all staff received on its new policies. The CE’s shredding vendor securely disposed of the log books. OCR obtained assurances that the CE implemented the corrective actions listed above. Location of breached information: Paper/Films Business associate present: No [source] | Elliot J Martin Chiropractic PC had a data breach in 2016, in New York. The information was breached via Desktop Computer. [source] | |
Emergency Room Associates dba- Emergency Medicine Associates had a data breach in 2016, in Arizona. [source] | Employee Benefits Division had a data breach in 2016, in Arkansas. [source] | |
ENT & Allergy Center had a data breach in 2016, in Arkansas. [source] | Excel Plus Home Health, Inc. had a data breach in 2016, in Texas. The information was breached via Network Server. [source] | |
EyeCare of Bartlesville had a data breach in 2015, in Oklahoma. [source] | Family & Children's Services of Mid-Michigan had a data breach in 2016, in Michigan. [source] | |
Family Medicine of Weston had a data breach in 2016, in Florida. The information was breached via Network Server. [source] | Fellicia Lewis, M.D. had a data breach in 2016, in Texas. [source] | |
Fidelis Care had a data breach in 2016, in New York. [source] | Florida Department of Agriculture had a data breach in 2017, in Florida. The names of thousands of concealed carry permit holders in Florida may have been leaked as the result of a recent data breach, state officials said. An online payment system utilized by the Florida Department of Agriculture and Consumer Services (FDACS) was compromised about two weeks ago, the office acknowledged Monday, in turn exposing the Social Security numbers of 469 customers as well as the names of 16,190 concealed weapon licensees. The breach appears to have originated overseas and is currently the subject of an investigation undertaken by the Florida Department of Law Enforcement, FDACS said in a statement. No financial information was obtained in the breach, and any additional records possibly compromised were already publicly available and pose “no risk of identity theft,” the announcement said. “The social security numbers that may have been obtained had been entered in an online field where either a social security number or Federal Employer Identification Number could be entered,” the statement said. [source] | |
Florida Hospital Medical Group had a data breach in 2016, in Florida. The information was breached via Paper/Films. [source] | Florida Medical Clinic had a data breach in 2016, in Florida. The information was breached via Electronic Medical Record. [source] | |
Fred's Stores of Tennessee had a data breach in 2016, in Tennessee. [source] | Freeport Memorial Hospital had a data breach in 2016, in Illinois. [source] | |
Friedman & Perry, CPAs had a data breach in 2017, in California. Name, date of birth, telephone number(s), address, social security number, employment (W-2) information, and 1099 information were breached via Website. [source] | Gallant Risk & Insurance Services, Inc. had a data breach in 2015, in California. On April 4, 2015, laptop computers belonging to the business associate (BA), Gallant Risk & Insurance Services, Inc., were stolen due to an office break-in. The breach affected 995 individuals’ protected health information (PHI), including a combination of individuals’ names, addresses, dates of birth, social security numbers, group policy numbers, and insurance identification numbers. The BA reported the incident to local law enforcement and to the affected covered entities. In response to OCR’s investigation, the BA ensured the proper breach notifications were provided, increased physical security, increased technical safeguards for electronic PHI (such as utilizing additional encryption), and adopted HIPAA policies and procedures. OCR obtained documented assurances that the BA implemented these corrective steps.. Location of breached information: Laptop Business associate present: Yes [source] | |
Genesis Physical Therapy, Inc. had a data breach in 2016, in California. [source] | Georgia Department of Behavioral Health and Developmental Disabilities (DBHDD) had a data breach in 2014, in Georgia. [source] | |
Georgia Department of Community Health had a data breach in 2015, in Georgia. The information was breached via Network Server . [source] | Georgia Department of Community Health had a data breach in 2015, in Georgia. [source] | |
Gibson Insurance Agency, Inc. had a data breach in 2016, in Indiana. [source] | Glendale Adventist Medical Center had a data breach in 2016, in California. [source] | |
Grace Primary Care, PC had a data breach in 2016, in Tennessee. [source] | Grapevine Police Departments had a data breach in 2015, in Texas. A group demanding the dashcam video of a shooting be released to the public, hacked the database of the Grapevine Police Department posting a video demanding this release. The police department is currently investigating the hacking of their system.More Information: www.thescoopblog,dallasnews.com/2015/04/anonymous-hacker-group-demands-police-video-of-shooting-of-mexican-immigrant-by-grapevine-cop,html/ [source] | |
Group Health Incorporated had a data breach in 2017, in New York. [source] | Group Health had a data breach in 2016, in Washington. [source] | |
Group Life Hospital and Medical Program had a data breach in 2016, in Connecticut. [source] | Grx Holdings LLC dba Medicap Pharmacy had a data breach in 2016, in Iowa. Grx Holdings, LLC dba Medicap Pharmacy notified Health and Human Services of a data breach when they suffered a loss of information. There are no specifics as to what kind of loss it was or what type of information was compromised. [source] | |
Haley Chiropractic Clinic had a data breach in 2014, in Washington. [source] | Harry Barker had a data breach in 2014, in Maryland. Name, address, phone number, email address, credit card number were breached via Website. [source] | |
Hawaii Medical Service Association had a data breach in 2016, in Hawaii. [source] | Health and Human Services Agency, Napa had a data breach in 2014, in California. [source] | |
Health Incent, LLC had a data breach in 2016, in Tennessee. [source] | HealthSouth Rehabilitation Hospital of Round Rock had a data breach in 2015, in Texas. [source] | |
Heart Center of Southern Maryland, L.L.P. had a data breach in 2016, in Maryland. [source] | Henry County Health Department had a data breach in 2016, in Ohio. [source] | |
Henry County Health Department had a data breach in 2016, in Ohio. The information was breached via Electronic Medical Record, Email, Laptop, Paper/Films. [source] | Heritage Medical Partners, LLC had a data breach in 2016, in South Carolina. [source] | |
Hill Country Memorial Hospital had a data breach in 2017, in Texas. The computer network used by Democratic presidential candidate Hillary Clinton's campaign was hacked as part of a broad cyber attack on Democratic political organizations, people familiar with the matter told Reuters.The latest attack, which was disclosed to Reuters on Friday, follows reports of two other hacks on the Democratic National Committee and the party's fundraising committee for candidates for the U.S. House of Representatives.The U.S. Department of Justice national security division is investigating whether cyber hacking attacks on Democratic political organizations threatened U.S. security, sources familiar with the matter said on Friday.The involvement of the Justice Department's national security division is a sign that the Obama administration has concluded that the hacking was state sponsored, individuals with knowledge of the investigation said.In a comment, the Clinton campaign said the data program maintained by the DNC and used by its campaign and other entities was accessed as part of the DNC hack. It added that its computer system has been under review by outside cyber security experts. To date, the outside experts have found no evidence that the campaign's internal systems have been compromised. [source] | Hillsborough County Aging Services Department had a data breach in 2017, in Florida. The information was breached via Paper/Films . [source] | |
Hospital fo Special Surgery had a data breach in 2016, in New York. The information was breached via Email. [source] | Howard R. Jarvis, D.M.D., L.L.C. dba Southwest Portland Dental had a data breach in 2016, in Oregon. [source] | |
Idaho Transportation Department had a data breach in 2017, in Idaho. On Jan. 2, 2018, the Idaho Transportation Department's Cyber Security Unit discovered an internal email account was compromised through a phishing attack. The Division of Motor Vehicles employee account was accessible from Nov. 11, 2017 through Dec. 7, 2017. The email account contained personal identifiable and payment card information for eight individuals. [source] | Illinois Valley Podiatry Group had a data breach in 2016, in Illinois. The Illinois Valley Podiatry Group, 3322 W. Willow Knolls Drive, has announced that it has became aware of unauthorized access to its computer records, believed to have taken place last year.The names, addresses and Social Security numbers of patients may have been viewed, according to the medical office. [source] | |
Indian Health Service Northern Navajo Medical Center had a data breach in 2016, in New Mexico. The information was breached via Paper/Films. [source] | Indiana State Medical Association had a data breach in 2015, in Indiana. [source] | |
Integrated Health Solutions PC had a data breach in 2016, in Pennsylvania. [source] | Iowa Department of Human Services had a data breach in 2017, in Iowa. The information was breached via Email . [source] | |
Iowa Dept. of Human Services had a data breach in 2014, in Iowa. The information was breached via Email. [source] | JASACare had a data breach in 2016, in New York. [source] | |
Jeffrey D. Rice had a data breach in 2017, in Ohio. [source] | Jennie Stuart Medical Center had a data breach in 2016, in Kentucky. [source] | |
Juame Francisco D.O. had a data breach in 2016, in Arizona. [source] | Kaiser Foundation Health Plan, Inc. had a data breach in 2016, in California. [source] | |
Kansas Department for Aging and Disability Services (KDADS) had a data breach in 2018, in Kansas. The Kansas Department for Aging and Disability Services (KDADS) has begun to notify individual consumers about a recent incident in which personal or protected health information was disseminated to a specific group of KDADS business associates.On February 23, 2018, KDADS became aware of a potential breach of personal or protected health information after an employee sent an unauthorized email containing personal or protected health information to a group of current KDADS business associates. . . The email contained an attachment which included consumer names, addresses, dates of birth, Social Security numbers, gender, in-home services program participation information and Medicaid identification numbers. No banking, credit card or driver license information was included.All involved consumers identified by KDADS will be sent an individual letter explaining the situation. [source] | Kansas Department for Aging and Disability Services had a data breach in 2018, in Kansas. The information was breached via Desktop Computer . [source] | |
Kansas Department of Commerce had a data breach in 2017, in Kansas. Hackers who breached a Kansas Department of Commerce data system used by multiple states gained access to more than 5.5 million Social Security Numbers and put the agency on the hook to pay for credit monitoring services for all victims.The number of SSNs exposed across the 10 states whose data was accessed has not been previously reported. The Kansas News Service, a collaboration of KCUR, Kansas Public Radio, KMUW and High Plains Public Radio, obtained the information through an open records request.More than half a million of the SSNs were from Kansas, according to the Department of Commerce.The data is from websites that help connect people to jobs, such as Kansasworks.com, where members of the public seeking employment can post their resumes and search job openings. Kansas was managing data for 16 states at the time of the hack, but not all were affected.In addition to the 5.5 million personal user accounts that included SSNs, about 805,000 more accounts that did not contain SSNs were also exposed. [source] | Karmanos Cancer Center had a data breach in 2016, in Michigan. [source] | |
Kern County Mental Health had a data breach in 2016, in California. [source] | KidsPeace had a data breach in 2016, in Pennsylvania. [source] | |
King of Prussia Dental Associates had a data breach in 2016, in Pennsylvania. [source] | Laborers Fund Administrative Office of Northern California, Inc. had a data breach in 2016, in California. [source] | |
Lafayette Pain Care PC had a data breach in 2016, in Indiana. The information was breached via Network Server. [source] | Lake Pulmonary Critical Care PA had a data breach in 2016, in Florida. [source] | |
Lasair Aesthetic Health P.C. had a data breach in 2016, in Colorado. [source] | Laser & Dermatologic Surgery Center had a data breach in 2016, in Missouri. [source] | |
Lasko Group, Inc. had a data breach in 2014, in Maryland. Name, email address, phone number, credit card info were breached via email. [source] | Lebanon Cardilogy Associates, PC had a data breach in 2016, in Pennsylvania. [source] | |
Lee Rice D.O. Medical Corp DBA Lifewellness Institute had a data breach in 2016, in California. [source] | Linda J White, DDS, PC had a data breach in 2016, in Virginia. [source] | |
Lindsay House Surgery Center, LLC had a data breach in 2016, in New York. The information was breached via Paper/Films. [source] | Livongo Health Inc. had a data breach in 2016, in Illinois. Per Health and Human Services Livongo Health suffered a breach when paper files/films were breached. There is no information as to what type of information was compromised in the breach. [source] | |
Locust Fork Pharmacy had a data breach in 2016, in Alabama. [source] | Los Angeles County Department of Health/Sutherland Healthcare Solutions had a data breach in 2014, in California. The information was breached via Laptop. [source] | |
Los Angeles County Department of Mental Health had a data breach in 2017, in California. On October 24, 2017, a LACDMH employee sent an email to candidates who responded to a job posting for a position within LACDMH. Inadvertently attached to that email was a spreadsheet that contained the PII of candidates, including you.What Information Was Involved?The information that may have been compromised included your name, promulgation date, email address, and Social Security Number. [source] | Louisiana Health Cooperative, Inc. in Rehabilitation had a data breach in 2016, in Louisiana. [source] | |
Louisiana Healthcare Connections had a data breach in 2016, in Louisiana. [source] | LSU Health Care Services Division had a data breach in 2017, in Louisiana. A business associate was not present. [source] | |
M&T Bank (Identity Theft) had a data breach in 2014, in Maryland. Name, address, telephone number, social security number, and account numberswere breached. [source] | Man Alive, Inc.and Lane Treatment Center, LLC had a data breach in 2016, in Maryland. [source] | |
Managed Health Services had a data breach in 2016, in Indiana. [source] | Marin Healthcare District had a data breach in 2016, in California. [source] | |
Mark Anthony Quintero M.D, LLC had a data breach in 2016, in Florida. [source] | Marketing Clique had a data breach in 2015, in Texas. [source] | |
Martin Army Community Hospital had a data breach in 2016, in Georgia. [source] | Maryland Department Of Health And Mental Hygiene had a data breach in 2014, in Maryland. Name and ssn were breached via email. [source] | |
Massachusetts Department of Public Health - Tewksbury Hospital had a data breach in 2017, in Massachusetts. The information was breached via Electronic Medical Record . [source] | Mayfield Clinic Inc. had a data breach in 2016, in Ohio. [source] | |
McLaren Greater Lansing Cardiovascular Group had a data breach in 2016, in Michigan. [source] | mdlNR LLC had a data breach in 2015, in Florida. As reported through Health and Human Services, mdlNR LLC a healthcare provider in Jacksonville Florida had unauthorized access in emails.Additional specific information as to what personal information was compromised was not available. [source] | |
Medical College of Wisconsin had a data breach in 2016, in Wisconsin. [source] | Medical Management, LLC (MML) had a data breach in 2015, in North Carolina. [source] | |
Melanie Witte (counsel for Berkeley Endocrine Clinic) had a data breach in 2016, in California. [source] | Memorial Hermann Health System had a data breach in 2016, in Texas. [source] | |
MetroPlus Health Plan had a data breach in 2017, in New York. [source] | Metropolitan Jewish Health System, Inc. d/b/a MJHS had a data breach in 2016, in New York. [source] | |
Michael Benjamin, M.D. Inc. had a data breach in 2015, in California. [source] | Mid Atlantic Professionals, Inc. DBA SSI had a data breach in 2014, in Maryland. [source] | |
Midland County Hospital District dba. Midland Memorial Hospital had a data breach in 2016, in Texas. [source] | Midland Women's Clinic had a data breach in 2016, in Texas. [source] | |
Mind Springs Health had a data breach in 2016, in Colorado. [source] | Mississippi Division of Medicaid had a data breach in 2017, in Mississippi. The information was breached via Email . [source] | |
Mississippi State Department of Health had a data breach in 2018, in Mississippi. The information was breached via Email . [source] | Montana Department of Public Health & Human Services had a data breach in 2014, in Montana. The information was breached via Network Server . [source] | |
Montana Department of Public Health and Human Service had a data breach in 2014, in Maryland. The information was breached via Website. [source] | Montana Health Department had a data breach in 2014, in Montana. [source] | |
Morton Medical Center had a data breach in 2016, in Washington. [source] | Mosaic Sales SOlutions US Operating Co. LLC had a data breach in 2014, in Maryland. Name, dob, ssn, email address, employee id number, phone number, address were breached via Laptop. [source] | |
Muir Medical Group, IPA. Inc. had a data breach in 2017, in California. On March 7, 2018, Muir discovered that a former employee of Muir IPA took with her certain information in the possession of Muir IPA before her employment ended with Muir IPA in December 2017. [source] | My Pediatrician had a data breach in 2016, in Florida. [source] | |
National Counseling Group had a data breach in 2016, in Virginia. The information was breached via Email. [source] | Nationstar Mortgage LLC had a data breach in 2014, in Maryland. Name, address, mortgage loan numbers were breached via email. [source] | |
NCO Financial Systems, Inc. had a data breach in 2014, in Maryland. NEAs former public website was compromised by a hacker or hackers on July 12, 2011. People who previously registered with the website in order to use the websites special functions may have had their email addresses and user name and password combinations exposed. Some individuals also had their names, addresses, and dates of birth compromised. Since passwords may have been obtained, individuals who may have been affected should not use their NEA website password for any other accounts. [source] | Neurology Physicians LLC had a data breach in 2016, in Maryland. [source] | |
New Jersey Spine Center had a data breach in 2016, in New Jersey. [source] | New West Health Services dba New West Medicare had a data breach in 2016, in Montana. The information was breached via Paper/Films. [source] | |
New York City Human Resources Administration/Department of Social Services had a data breach in 2018, in New York. The information was breached via Paper/Films . [source] | New York State Office of Mental Health had a data breach in 2016, in New York. [source] | |
Nintendo of America, Inc. had a data breach in 2016, in Washington. [source] | North Carolina Department of Health and Human Services had a data breach in 2014, in North Carolina. A business associate was present. [source] | |
North Dakota Department of Human Services had a data breach in 2017, in North Dakota. The information was breached via Paper/Films . [source] | North Texas Heart Center, P.A. had a data breach in 2016, in Texas. The information was breached via Desktop Computer, Laptop, and Network Server. [source] | |
North Texas Medical Center had a data breach in 2018, in Texas. A business associate was not present. [source] | Northstar Healthcare Acquisitions LLC had a data breach in 2016, in Texas. The information was breached via Portable Electronic Device. [source] | |
Northwest Community Healthcare had a data breach in 2016, in Illinois. [source] | Northwest Oncology & Hematology, S.C. had a data breach in 2016, in Illinois. The information was breached via Email. [source] | |
Oakland Family Services had a data breach in 2015, in Michigan. The information was breached via Email . [source] | Office of the New York City Public Advocate had a data breach in 2011, in New York. The information was breached via Desktop Computer, Email, Laptop, Network Server, and Other Portable Electronic Device. [source] | |
Ohio Department of Mental Health and Addiction Services had a data breach in 2016, in Ohio. [source] | Ohio Department of Mental Health and Addiction Services had a data breach in 2016, in Ohio. A business associate was not present. [source] | |
Oklahoma Department of Human Services had a data breach in 2017, in Oklahoma. The information was breached via Network Server . [source] | Oneida Tribe of Indians of Wisconsin had a data breach in 2016, in Wisconsin. [source] | |
OptumRx, Inc. had a data breach in 2016, in California. [source] | Orchid MPS Holdings, LLC/Welfare Benefit Plan had a data breach in 2016, in Missouri. [source] | |
Oregon Employment Department/WorkSource Oregon had a data breach in 2014, in Oregon. The Oregon Employment Department, specifically WorkSource Oregon, discovered a data breach of a data base that contained personal information of individuals searching for jobs when an anonymous tip came in alerting officials of the breach. Social Security numbers of more than 850,000 individuals were compromised in the breach. Officials shut down the website and were investigating the breach. [source] | Oregon's Health CO-OP had a data breach in 2015, in Oregon. A personal laptop belonging to an Oregon Health CO-OP's employee was stolen from his unattended, locked car. The laptop was unencrypted and contained the electronic protected health information (ePHI) of approximately 14,000 individuals. The e-PHI involved in the breach was demographic information and included names, addresses, social security numbers, dates of birth, health plan identification numbers, and health plan numbers. Following the breach, the covered entity (CE) sanctioned the employee, implemented additional technical safeguards to prevent the downloading of e-PHI onto a personal electronic device, and trained its employees on these technical safeguards. OCR provided the CE with technical assistance regarding risk analysis and risk management implementation. Location of breached information: Laptop Business associate present: No [source] | |
Orleans Medical Clinic had a data breach in 2016, in Massachusetts. [source] | OsteoMed LP had a data breach in 2015, in Texas. Name, debit/credit card info were breached. [source] | |
Pacific Gas and Electric had a data breach in 2016, in California. [source] | Pain Treatment Centers of America/Interventional Surgery Institute had a data breach in 2016, in Arkansas. [source] | |
PathGroup had a data breach in 2016, in Tennessee. [source] | Pathway to Hope had a data breach in 2016, in Florida. [source] | |
Peabody Retirement Community had a data breach in 2016, in Indiana. [source] | Pedes Orange County, Inc. had a data breach in 2018, in California. The information was breached via Electronic Medical Record. [source] | |
Pennsylvania Revenue Department had a data breach in 2016. [source] | Phoenix Dental Care had a data breach in 2016, in Tennessee. [source] | |
Pittman Family Dental had a data breach in 2016, in Ohio. [source] | Planned Parenthood of Greater Washington and North Idaho had a data breach in 2016, in Washington. [source] | |
Planned Parenthood of the Heartland had a data breach in 2016, in Iowa. [source] | Pointe Medical Services, Inc. had a data breach in 2016, in Florida. [source] | |
Polk County Health Services, Inc had a data breach in 2018, in Iowa. The information was breached via Email . [source] | Pratap S. Kurra, M.D had a data breach in 2016, in California. [source] | |
Premier Family Care I, Inc. had a data breach in 2016, in Texas. [source] | Preventice Services, LLC had a data breach in 2016, in Texas. [source] | |
Prima Medical Foundation had a data breach in 2016, in California. [source] | PrimeWest Health had a data breach in 2016, in Minnesota. [source] | |
Prince George's County Public Schools had a data breach in 2014, in Maryland. Name, ssn, dob employee identification number were breached via Email. [source] | PRN Medical Services, LLC dba Symbius Medical, LLC had a data breach in 2014, in Arizona. The information was breached via Email and Network Server . [source] | |
Professional Dermatology Care, P.C. had a data breach in 2016, in Virginia. [source] | Providence Saint John's Health Center had a data breach in 2017, in California. [source] | |
Pruitt Health Hospice Beaufort had a data breach in 2016, in South Carolina. [source] | Pruitt Home Health had a data breach in 2016, in South Carolina. [source] | |
Public Education Employees' Health Insurance Plan had a data breach in 2016, in Alabama. [source] | Public Health Trust of Miami-Dade County Florida had a data breach in 2016, in Florida. [source] | |
Public Health Trust of Miami-Dade County, Florida had a data breach in 2016, in Florida. The information was breached via Electronic Medical Record . [source] | Puerto Rico Department of Heatlh - Medicaid Program had a data breach in 2015. [source] | |
Pulaski County Special School District-Employee Benefits Division had a data breach in 2016, in Arkansas. The information was breached via Email . [source] | Pulte Mortgage LLC had a data breach in 2014, in Maryland. Name, address, phone or email, ssn, financial account numbers were breached via Laptop. [source] | |
Quarles & Brady, LLP had a data breach in 2016, in Wisconsin. The information was breached via Laptop. [source] | Rainbow Children's Clinic had a data breach in 2016, in Texas. [source] | |
Raymond Mark Turner, M.D. had a data breach in 2015, in Nevada. One unencrypted laptop computer was stolen during business hours wile the office of Dr. Robert Mark Turner was in the process of updating and encrypting its computers. A file on the stolen laptop contained the electronic protected health information (ePI) of 2,153 individuals which included names, addresss, dates of birth, Social Security numbers, drivers license numbers, health insurance information, and records of medical treatment. The covered entity (CE) provided breach notifications to HHS, affected individuals, and the media and provided credit monitoring and identity theft protection to affected individuals. In response to the breach, the CE improved physical safeguards and enhanced technical safeguards by implementig an encryption management program for all computer syystems. OCR reviewed the CE's HIPAA risk assessment and provided technical assistance on the required elements of a risk analysis and risk management plan. [source] | RealTruck, Inc. had a data breach in 2017, in North Dakota. Name, social security number, driver’s license number, date of birth, and bank account number were breached. [source] | |
RGH Enterprises, Inc. had a data breach in 2014, in Ohio. Computer hackers installed malware that intercepted the electronic protected health information (ePHI) of approximately 4,230 individuals using the covered entity's (CE's) website. The ePHI included names, dates of birth, phone numbers, shipping and billing addresses, email addresses, credit card issuers, expiration dates, the last 4 digits of credit card numbers, account numbers, primary physicians, diagnoses, order histories, and health insurers. Following the breach, the CE removed the malware from the affected computer servers, migrated the website to non-compromised Location of breached information: Network Server Business associate present: No [source] | Rhode Island Executive Office of Health and Human Services had a data breach in 2018, in Rhode Island. A business associate was not present. [source] | |
Rhode Island Executive Office of Health and Human Services had a data breach in 2018, in Rhode Island. The information was breached via Paper/Films . [source] | Rite Aid, New York had a data breach in 2016, in New York. [source] | |
Riverside Health System had a data breach in 2016, in California. [source] | Riverside Health System had a data breach in 2016, in Virginia. An employee authorized to work from home failed to return paper records to the physician practice. Her ex-husband discovered the records and returned them to the physician practice. The breach included the protected health information (PHI) of 578 individuals. The PHI involved in the breach included demographic information, dates of birth, social security numbers, medical records numbers, and clinical information. Following the breach, the covered entity re-educated all employees. OCR reviewed the CE's risk analysis to ensure compliance with the HIPAA Privacy and Security Rules. Location of breached information: Paper/Films Business associate present: No [source] | |
RMA Medical Centers of Florida had a data breach in 2016, in Florida. [source] | Roark's Pharmacy had a data breach in 2016, in Tennessee. [source] | |
Sacred Heart Health System, Inc. had a data breach in 2015, in Florida. [source] | Sacred Heart Health System, Inc. had a data breach in 2016, in Florida. [source] | |
Saint Louis County Department of Health had a data breach in 2015, in Missouri. On November 18, 2014, an employee of the covered entity (CE), Saint Louis County Department of Health, resigned her position and then impermissibly emailed her personal email account a spreadsheet that was used to reconcile bills for medical services provided to the CE's patients. The types of protected health information (PHI) contained in the spreadsheet included the names, social security numbers, and dates of service of approximately 4,000 patients, along with the names of the medical providers. The CE provided breach notification to HHS, affected individuals, and the media, and also filed a police report. The CE terminated the former employee’s access to its patient database and retrained employees on its HIPAA policies and procedures regarding HIPAA. OCR obtained assurances that the CE implemented the corrective actions listed. [source] | Saint Mary and Elizabeth Hospital had a data breach in 2016, in Kentucky. [source] | |
San Francisco Department of Public Health/Sutherland Healthcare Solutions had a data breach in 2014, in California. On November 7, 2016, we learned that an SJECCD employee had inadvertently uploaded a file containing the personal information of certain SJECCD students to a publicly accessible folder on the SJECCD website. The file was temporarily stored on the webserver and could be retrieved in search results. Upon learning this, we promptly removed the file from the website and began an investigation into the incident. Our investigation indicates that the incident was an accident, and not the result of any kind of malicious attack.What Information Was Involved?The personal information contained in the file may have included your name, date of birth, and Social Security number. Although we are not aware at this time of any third party misusing your personal information, we take privacy and security very seriously and wanted to inform you about this situation, the steps we are taking to protect your information, and steps you may take to help protect yourself. [source] | San Francisco General Hospital and Trauma Center had a data breach in 2015, in California. [source] | |
San Juan County New Mexico had a data breach in 2016, in New Mexico. [source] | San Juan Oncology Associates had a data breach in 2016, in New Mexico. [source] | |
Santa Cruz County Health Services Agency had a data breach in 2016, in California. [source] | Santa Cruz County Health Services Agency had a data breach in 2016, in California. The information was breached via Paper/Films. [source] | |
Santa Fe Medical Group had a data breach in 2014, in New Mexico. On behalf of our client, SAS Safety Corporation (the Company), we write to advise you of an incident involving the unauthorized introduction of maiware onto the Company's website,www.sassafety.com. This malware resulted in the possible compromise of personal information of Company customers residing in Maryland. Based upon the Company's investigation, the maiware was present from September 23, 2015 to December 8, 2013 and potentially exposed certain personal information of three residents that was inputted by those customers. The personal information that was potentially affected by the incident includes: customer name, address, credit or debit card number, payment card expiration date and the card's CVV security number. Additionally, the customer's logon identification and password for the website may have been affected. The Company does not collect customers' social security or driver's license numbers and that data was in no way affected by the incident. [source] | SAY San Diego had a data breach in 2017, in California. On October 27, 2017, SAY San Diego was notified by the County of San Diego Health & Human Services Agency (“HHSA”) that a citizen had returned some paper files to their office that were found in a filing cabinet purchased from a salvage store. The files were reviewed and assessed by our team on October 30, 2017 at which time we confirmed the documents in the files related to participants in SAY San Diego’s Dual Diagnosis youth program from January through June 2013. However, the files from March and April of 2013 were not returned, and have not been recovered to date. While we currently have no evidence that the information was subject to misuse, we have confirmed that the files contained the name, case number, dates and length of service, location of service, and provider name. The files did not contain any Social Security numbers, dates of birth, or Driver’s License numbers or financial account information. [source] | |
SEC had a data breach in 2017, in District Of Columbia. Companies that took advantage of the chance to practice filing sensitive information with the U.S. Securities and Exchange Commission might wish they hadn’t.While the SEC is providing few details, the regulator did say the hack of its online database of corporate filings targeted what the agency calls its test Edgar system. It lets startups unfamiliar with filling out SEC forms get comfortable with the process without publicly blasting out market-moving announcements.Now an initiative that was grounded in good intentions is causing the SEC headaches. The agency disclosed Wednesday that not only had cybercriminals breached Edgar, but they may have stolen corporate secrets that they profited from. The SEC blamed the 2016 intrusion -- which it was slow to reveal -- on a software vulnerability in its test system.Edgar houses millions of filings on disclosures ranging from corporate earnings to statements on mergers and acquisitions. Infiltrating it to review announcements before they are released publicly would serve as a virtual treasure trove for a hacker seeking to make easy money. SEC Chairman Jay Clayton said the agency’s review of the breach is ongoing and that it’s “coordinating with the appropriate authorities.” [source] | Secretary of State Brian Kemp had a data breach in 2015, in Georgia. The Georgia Secretary of State, Brian Kemps office is being sued by two Georgia women who claim that the Secretary's office released personal information that involves 6 million Georgia voters. Mr. Kemps office has communicated that his office released information to media, political parties and other paying subscribers who legally buy voter information from the state, but due to what they are calling a "clerical" error, individual voters personal information was included in these files.12 separate entities received the files that contained 6 million Georgia voters and inadvertently included drivers license information, Social Security numbers and dates of birth. It is legal for the state to release public voter information, but the information is only supposed to include voter's name, residential or mailing address, race, gender, registration date and last voting date. According to the lawsuit, Mr. Kemps office never notified individuals regarding the breach, nor did they contact the consumer reporting agencies. [source] | |
SEIM Johnson LLP had a data breach in 2016, in Nevada. A business associate (BA), Seim Johnson, LLP, reported on behalf of 10 health care provider clients that its health care auditor took his firm-issued laptop computer on a non-business weekend trip. When the employee arrived home from this trip, he discovered the backpack containing the laptop was missing. The laptop contained the protected health information (PHI) of 30,972 individuals and included demographic, clinical, and financial information. The BA provided breach notification to HHS, affected individuals, and the media. After investigating this incident, the BA determined that the laptop may not have been effectively encrypted. Following the breach, the BA sanctioned the involved employee and its security officer, retrained employees on security risks involving portable devices, and implemented new policies and procedures. OCR obtained assurances that the BA implemented the corrective actions listed above. [source] | Senior Health Partners had a data breach in 2015, in New York. Health and Human Services reported a breach with Senior Health Partners when a portable device was stolen. [source] | |
Sequin Dermatology, Office of Robert J Magnon, MD had a data breach in 2016, in Texas. [source] | Sharon J. Jones M.D. had a data breach in 2015, in California. [source] | |
Sisters of Charity of Leavenworth Health System Health Benefits had a data breach in 2016, in Colorado. [source] | Sorenson Communications and CaptionCall had a data breach in 2014, in Utah. On March 7 it was discovered that there was an unauthorized access to Sorenson Communications employee data via the payroll vendor utilized for both Sorenson Communications and CaptionCall employees. The personal information breached includes both the employee, beneficiaries, dependents, and emergency contacts, or anyone listed in the employees HR account with the company. The information includes names, dates of birth, addresses, Sorenson income histories, Social Security Numbers, W-2 information, and emergency contact data and appeared to have happened between February 20, 2014 through March 3, 2014.The FBI has been contacted and is investigating the breach. An email was sent to all those affected on March 11th with instructions on how to enroll in the company-provided credit monitoring services. If an email was not received they are requesting those individuals contact the Human Resources Department at hrsupport@sorenson.com to obtain the information. [source] | |
South Carolina Department of Employment and Workforce had a data breach in 2014, in South Carolina. [source] | ST Psychotherapy, LLC had a data breach in 2015, in Wisconsin. [source] | |
St. Mary's Health had a data breach in 2015, in Indiana. [source] | St. Peter's Health Parnters had a data breach in 2015, in New York. [source] | |
St. Vincent Hospital and Health Care Center Inc. had a data breach in 2015, in Indiana. [source] | StarCare Specialty Health System had a data breach in 2016, in Texas. [source] | |
State Long Term Care Ombudsmans Office, Michigan Department of Community Health had a data breach in 2014, in Michigan. The information was breached via Other Portable Electronic Device . [source] | State of Alaska Department of Health and Social Services had a data breach in 2017, in Alaska. The information was breached via Desktop Computer . [source] | |
State of New Hampshire, Department of Health and Human Services had a data breach in 2016, in New Hampshire. The information was breached via Desktop Computer . [source] | Summit Medical Group, In. dba St. Elizabeth Physicians had a data breach in 2016, in Kentucky. [source] | |
Sunbury Plaza Dental had a data breach in 2016, in Ohio. [source] | Sunshine State Health Plan, Inc. had a data breach in 2016, in Florida. [source] | |
Surgical Care Affiliates had a data breach in 2016, in Alabama. [source] | Susan M. Hughes Center had a data breach in 2016, in New Jersey. [source] | |
Tallahassee Memorial HealthCare, Inc had a data breach in 2016, in Florida. [source] | Target Corporation Health Plan had a data breach in 2016, in Minnesota. [source] | |
Tennessee Rural Health Improvement Association had a data breach in 2015, in California. Children's Eyewear Sight notified individuals of a data breach when a desktop computer was stolen containing individuals personal information. What specific personal information was contained in the computers was not communicated. [source] | Texas Children's Health Plan had a data breach in 2017, in Texas. The information was breached via Email . [source] | |
Texas Health and Human Services Commission had a data breach in 2016, in Texas. [source] | Texas Health and Human Services Commission had a data breach in 2016, in Texas. Between April 19, 2016 and May 10, 2016, Iron Mountain, a business associate (BA) of the covered entity (CE), Texas Health and Human Services Commission, was unable to locate sixteen cartons of records containing protected health information (PHI). The types of PHI involved in the breach included the names, addresses, social security numbers, social security claim numbers, dates of birth, medical record numbers, Medicaid/individual numbers, case numbers, and bank account numbers for over 500 individuals. The CE provided breach notification to HHS, affected individuals, and the media. Following the incident, the CE ensured that the BA retrained its workforce members on privacy and appropriate storage and tracking procedures. Additionally, the CE initiated a change to its procedure for reconciling file inventories and verifying file box destruction. OCR obtained assurances that the CE implemented the corrective actions noted above. [source] | |
Texas Health Physicians Group had a data breach in 2018, in Texas. The information was breached via Email . [source] | Texas Wellness Incentives and Navigation (WIN) Project- University of Florida and Texas Health and Human Services Commission had a data breach in 2014, in Florida. [source] | |
The Ambulatory Surgery Center at St. Mary had a data breach in 2016, in Pennsylvania. [source] | The Carle Foundation had a data breach in 2016, in Illinois. [source] | |
The County of Hertford County, North Carolina had a data breach in 2014, in Maryland. Name and ssn were breached via Website. [source] | The Department of Aging and Disability Services had a data breach in 2015, in Texas. The information was breached via Network Server . [source] | |
The Finley Center had a data breach in 2016, in Nevada. [source] | The North Carolina Department of Health and Human Services had a data breach in 2017, in North Carolina. The information was breached via Email. [source] | |
The University of New Mexico had a data breach in 2016, in New Mexico. [source] | The University of Texas System Administration had a data breach in 2016, in Texas. [source] | |
The Vein Doctor had a data breach in 2016, in Missouri. [source] | Thomasville Eye Center had a data breach in 2016, in Georgia. [source] | |
Triple S Advantage, Inc had a data breach in 2015, in Puerto Rico. The information was breached via Paper/Films. [source] | Tulare County Health and Human Services had a data breach in 2015, in California. The Tulare County Health and Human Services Agency notified individuals of a breach of their personal information when an HHSA employee emailed approximately 845 patients from the Visalia and Farmersville clinics exposing information to access their medical portal. The agency disabled all patient portal accounts and are asking individuals to change their email addresses, re-register through the portal and change the PIN to login to the patient portal. The agency did not disclose specifically what personal information may have been viewable. [source] | |
U.S HealthWorks had a data breach in 2016, in California. [source] | U.S. Department of Health and Human Services had a data breach in 2016, in District Of Columbia. The top watchdogs in the House demanded to know Tuesday why a personal laptop taken from a federal building in Washington state was used to conduct child-support audits, especially because it and other stolen hard drives may have contained millions of names and Social Security numbers.The letter by the House government oversight panel's Republican chairman and senior Democrat to Health and Human Services Secretary Sylvia Burwell comes about a week after GOP investigators began looking into the breach in Olympia, Washington, which authorities say affected as many as five million people.Your staff acknowledged that the use of personal equipment is a clear violation of HHS privacy and security policy, Utah Republican Jason Chaffetz and Maryland Democrat Elijah Cummings wrote in the letter obtained by The Associated Press. The break-ins occurred in early February at the federal Office of Child Support Enforcement.Chaffetz's committee has been critical of data breaches under the Obama administration, including when the U.S. Office of Personnel Management said last year hackers committed an unprecedented theft of private data for millions of federal workers. [source] | |
UHHS Geauga Medical Center had a data breach in 2016, in Ohio. [source] | UIL Holdings Corporation had a data breach in 2014, in Maryland. Names, Social Security Numbers, addresses, earnings data, and/or dates of birth. were breached via Laptop. [source] | |
Uncommon Care, P.A. had a data breach in 2016, in North Carolina. [source] | United Community & Famiy Services had a data breach in 2016, in Connecticut. [source] | |
UnitedHealthcare Group Single Affiliated Covered Entity had a data breach in 2016, in Minnesota. [source] | Unity Point Health had a data breach in 2016, in Iowa. [source] | |
University of Wisconsin Hospitals and Clinics had a data breach in 2016, in Wisconsin. [source] | Urgent Care Clinic of Oxford had a data breach in 2016, in Mississippi. [source] | |
US State Department had a data breach in 2014, in District Of Columbia. Name, address, ssn, member account number, and financial info. [source] | Vail Clinic, Inc. dba Vail Valley Medical Center and dbs Howard Head Sports Medicine had a data breach in 2016, in Colorado. [source] | |
Val Verde Regional Medical Center had a data breach in 2016, in Texas. [source] | Valley Community Healthcare had a data breach in 2015, in California. [source] | |
Valley Hope Association had a data breach in 2016, in Kansas. [source] | Ventura County Health Care Agency had a data breach in 2016, in California. [source] | |
Vertiv Co. Health & Welfare Plan had a data breach in 2017, in Ohio. [source] | Vibrant Body Wellness had a data breach in 2016, in California. [source] | |
Vidant Health had a data breach in 2016, in North Carolina. [source] | Village of Oak Park had a data breach in 2016, in Illinois. [source] | |
Vincent Vein Center had a data breach in 2016, in Colorado. The covered entity (CE), Vincent Vein Center, reported that its business associate (BA), Bizmatics, had owned data servers containing the CE's patient information that were accessed by unauthorized persons. Approximately 2,250 of the CE's patients were affected by the breach. The electronic protected health information (ePHI) involved in the breach included patients' names, addresses, social security numbers, and health visit information. The CE provided breach notification to affected individuals, HHS, and the media. Following the breach, the CE began evaluating the use of alternate electronic medical record and practice management software. As a result of OCR’s investigation and technical assistance, the CE provided written assurances that it will revise and/or implement its relevant breach notification and BA contract policies and procedures in compliance with HIPAA. OCR opened a separate investigation of the BA. [source] | Virginia Department of Human Resources Management had a data breach in 2015, in Virginia. The information was breached via Network Server. [source] | |
Virginia Department of Medical Assistance Services (VA-DMAS) had a data breach in 2015, in Virginia. The information was breached via Network Server . [source] | Virginia Department of Medical Assistance Services had a data breach in 2015, in Virginia. [source] | |
Virginia Premier Health Plan (VPHP) had a data breach in 2014, in Virginia. Virginia Premier Health Plan, a business associate (BA) of the covered entity (CE), Virginia Department of Medical Assistance Services (VA-DMAS), mailed incorrect postcards to Virginia Medicaid members. The breach included 13,357 postcards that were mailed to the wrong address and 12,156 postcards that contained incorrect services information. The information did not include social security numbers or financial information. The BA provided breach notification to HHS, the media, and to affected individuals in English and Spanish. Following this breach, the BA improved safeguards by retraining employees on safeguards for protected health information, updating procedures for mailings, and implementing additional quality control checks. OCR obtained assurances that the BA implemented the corrective action listed above. [source] | Virtua Medical Group had a data breach in 2016, in New Jersey. [source] | |
W. Christopher Bryant DDS PC had a data breach in 2016, in Michigan. On April 10, 2018, Grainger as notified by [24]7.ai that [24]7.ai was involved in a cyber incident, during which time, credit card information of those conducting business with certain [24]7.ai clients, including Grainger, may have been accessed. Customers who used guest check out and manually entered credit card information on Grainger.com or its app were potentially affected. Information includes credit card numbers, security codes, card expiration dates, names and addresses. [source] | Waiting Room Solutions Limited Liability Limited Partnership had a data breach in 2016, in New York. [source] | |
Walgreen Co. had a data breach in 2016, in Illinois. [source] | Walmart Stores, Inc. had a data breach in 2016, in Arkansas. [source] | |
Warren Clinic had a data breach in 2016, in Oklahoma. [source] | Washington DC VA Medical Center had a data breach in 2016, in District Of Columbia. [source] | |
Washington State Health Authority (HCA) had a data breach in 2016, in District Of Columbia. The Washington State Health Authority (HCA) said Tuesday that an employee mishandled the Social Security numbers, dates of birth, Apple Health client ID numbers and private health information of 91,000 Apple Health (Medicaid) clients.The employees involved worked at two different state agencies and they exchanged files of clients which violates HIPAA. They are not clear if any of the files were disseminated beyond the two employees who exchanged the files. [source] | WellSpan Health had a data breach in 2017, in Pennsylvania. [source] | |
White Glove Health had a data breach in 2015, in Texas. [source] | Willis North America Inc. Medical Expense Benefit Plan had a data breach in 2014, in Maryland. Name, dob, ssn, employee ID number were breached via email. [source] | |
Willow Bend Dental had a data breach in 2016, in Texas. [source] | Wisconsin Department of Health Services had a data breach in 2018, in Wisconsin. The information was breached via Laptop . [source] | |
Worldwide Services Insurance Agency, LLC had a data breach in 2018. [source] | Wyoming Medical Center had a data breach in 2016, in Wyoming. The information was breached via Network Server. [source] | |
You and Your Health Family Care, Inc. had a data breach in 2016, in Florida. [source] | Young Adult Institute, Inc. had a data breach in 2016, in New York. [source] | |